K8S关于Dashboard浏览器访问填坑
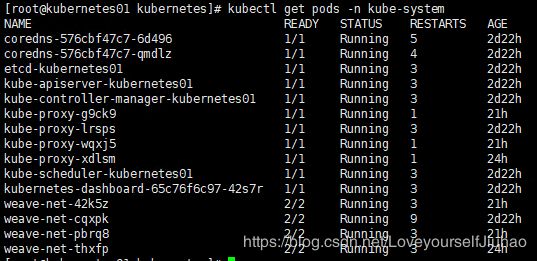
1安装K8S集群完成,包括kubernetes-dashboard-65c...可视化界面,运行一切状态正常
2关于问题点关于dashboard可视化界面
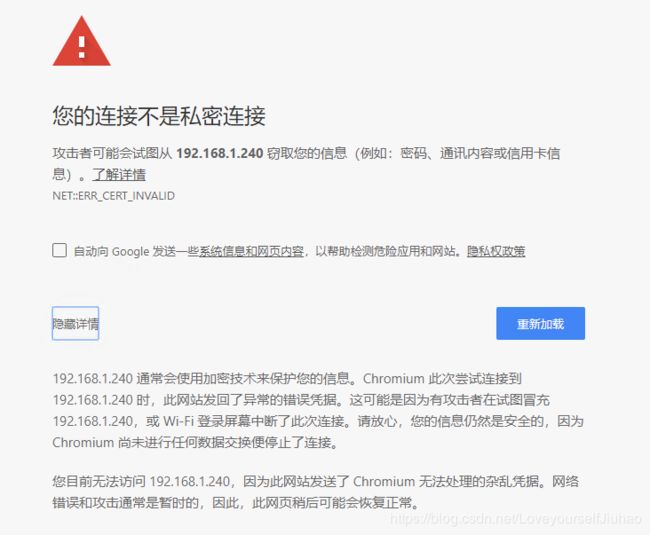
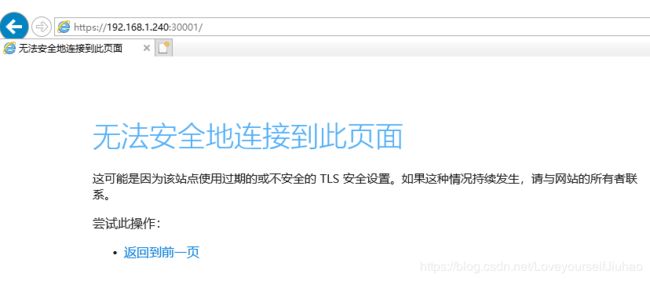
然而Goole浏览器访问失败,IE也是如如此。。。
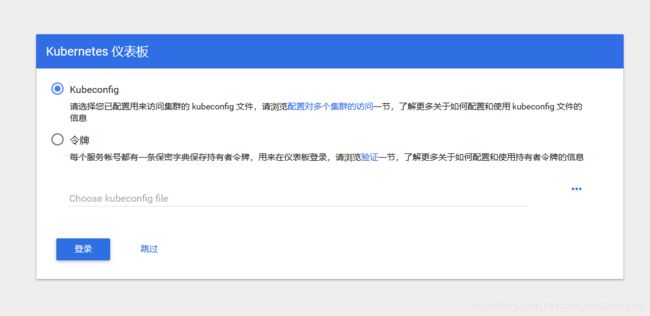
还好火狐有不安全访问模式,点击进入,瞬间感觉眼前一亮,不过kubeconfig、令牌什么鬼。。。
按照搜罗网上方法,敲两条命令获取token粘贴复制到令牌,点击登录
kubectl get secret -n kube-system|grep dashboard-token
kubectl describe secret kubernetes-dashboard-token-c7bp9 -n kube-system
虽然登录成功了,怎么跟跳过显示的一样啊,全空的。。。
注意:有人直接粘贴复制token并不能登录成功,提示验证失败请重试(出现原因是你一些小细节没注意到)
把token字符串粘贴到txt文本后,发现字符串为两行,只需按一下删除,把回车去掉,两行变一行就可以顺利登录了,有没有人踩坑半天感觉就是登录不进去啊,哈哈
3解决Dashboard可视化问题
其实进入刚才可视化一堆提示的画面,所有功能都实现了,为什么集群信息没有显示呢,是因为权限不够,简单说就是登录token字符串命令,并没有查看集群信息的权限,我们要做的是创建一个可以访问集群全部权限的token,或者说某个用户是超级管理员使用这个用户的token.
token令牌认证登录
(1)创建serviceaccount
[root@kubernetes01 pki]# kubectl create serviceaccount dashboard-admin -n kube-system
serviceaccount/dashboard-admin created
[root@kubernetes01 pki]# kubectl get sa -n kube-system
NAME SECRETS AGE
。。。。。。
dashboard-admin 1 17s
。。。。。。(2)把serviceaccount绑定在clusteradmin,授权serviceaccount用户具有整个集群的访问管理权限
[root@kubernetes01 pki]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created(3)获取serviceaccount的secret信息,可得到token(令牌)的信息
[root@kubernetes01 pki]# kubectl get secret -n kube-system|grep dash
dashboard-admin-token-kk862 kubernetes.io/service-account-token 3 120m
kubernetes-dashboard-certs Opaque 0 2d21h
kubernetes-dashboard-key-holder Opaque 2 2d21h
kubernetes-dashboard-token-c7bp9
注意使用新创建token:dashboard-admin-token-kk862
[root@kubernetes01 pki]# kubectl describe secret dashboard-admin-token-kk862 -n kube-system
Name: dashboard-admin-token-kk862
Namespace: kube-system
Labels:
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: 82852e2f-880f-11e9-88a2-000c294b5dd3
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4ta2s4NjIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiODI4NTJlMmYtODgwZi0xMWU5LTg4YTItMDAwYzI5NGI1ZGQzIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.Rfy-OPBcHO7A4dPYKBigX59gWaXUOeILHfOw7lk8f-5pSOznO6rVHOGvKMT2Uh8QuXY0iwQnjdjUgxtoTDbeI7WiHZR6CET-ezDjmxfPSzDqYTEnIhs11e8922dSb7zSNPHv4Z8W7esqnHV0Wic1yBEDqIvKBkKY4Cl9YcJmr6m5RJaXsfSiRzR180_uUkvBFXEsJ4cWH9eFgRoq_JnFWjB8rVl5a17c-CjxlW6i8hcW5Zd8JuvgCIOSISfoz1JvLtzRkZJr10gHTqkWwKx-hL27MUyT1JXDU_l97OcGp2p6ImbLMdNAOByDYVCJh02_YchoWc9EVib7IHi3Xyc-5A
(4)通过patch暴露端口
[root@kubernetes01 pki]# kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kube-system
service/kubernetes-dashboard patched (no change)
[root@kubernetes01 pki]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 53/UDP,53/TCP 2d20h
kubernetes-dashboard NodePort 10.103.203.46 443:30001/TCP 2d20h
(5)浏览器访问登录,把token粘贴进去登录即可
2 kubeconfig配置文件登录
创建一个只能对default名称空间有权限的serviceaccount
[root@kubernetes01 pki]# kubectl create serviceaccount def-ns-admin -n default
serviceaccount/def-ns-admin created
[root@kubernetes01 pki]# kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin
rolebinding.rbac.authorization.k8s.io/def-ns-admin created
[root@kubernetes01 pki]# kubectl get secret
NAME TYPE DATA AGE
admin-token-bwrbg kubernetes.io/service-account-token 3 5d1h
def-ns-admin-token-xdvx5 kubernetes.io/service-account-token 3 2m9s
default-token-87nlt kubernetes.io/service-account-token 3 49d
tomcat-ingress-secret kubernetes.io/tls 2 21d
[root@master1 pki]# kubectl describe secret def-ns-admin-token-xdvx5
Name: def-ns-admin-token-xdvx5
Namespace: default
Labels:
Annotations: kubernetes.io/service-account.name: def-ns-admin
kubernetes.io/service-account.uid: 928bbca1-245c-11e9-81cc-000c291e37c2
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi14ZHZ4NSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI5MjhiYmNhMS0yNDVjLTExZTktODFjYy0wMDBjMjkxZTM3YzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.EzUF13MElI8b-kuQNh_u1hGQpxgoffm4LdTVoeORKUBTADwqHEtW2arj76oZuI-wQyy5P0v5VvOoefr6h3NpIgbAze8Lqyrpg9wO0Crfi30IE1kZ2wUPYU9P_5inMxmCPLttppyPyc8mQKDkOOB1xFUmEebC63my-dG4CZljsd8zwNU6eXnhaThSUUn12UTvRsbSBLD-dvau1OY6YgDL6mgFl3cVqzCPd7ELpEyNYWCh3x5rcRfCcjcHGfUOrWY2NvdW50Iiwia3ViZXJpby9-CI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2
这种情况下的权限较小,用token登陆后只能对default名称空间有权限
[root@kubernetes01 pki]# kubectl config set-cluster kubernetes --certificate-authority=./ca.crt --server="https://10.0.0.100:6443" --embed-certs=true --kubeconfig=/root/def-ns-admin.conf
Cluster "kubernetes" set.
[root@kubernetes01 pki]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.0.0.100:6443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
[root@kubernetes01 pki]# kubectl get secret
NAME TYPE DATA AGE
def-ns-admin-token-xdvx5 kubernetes.io/service-account-token 3 5d
[root@kubernetes01 pki]# kubectl describe secret def-ns-admin-token-xdvx5
Name: def-ns-admin-token-xdvx5
Namespace: default
Labels:
Annotations: kubernetes.io/service-account.name: def-ns-admin
kubernetes.io/service-account.uid: 928bbca1-245c-11e9-81cc-000c291e37c2
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi14ZHZ4NSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI5MjhiYmNhMS0yNDVjLTExZTktODFjYy0wMDBjMjkxZTM3YzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.EzUF13MElI8b-kuQNh_u1hGQpxgoffm4LdTVoeORKUBTADwqHEtW2arj76oZuI-wQyy5P0v5VvOoefr6h3NpIgbAze8Lqyrpg9wO0Crfi30IE1kZ2wUPYU9P_5inMxmCPLttppyPyc8mQKDkOOB1xFUmEebC63my-dG4CZljsd8zwNU6eXnhaThSUUn12UTvRsbSBLD-dvau1OY6YgDL6mgFl3cVqzCPd7ELpEyNYWCh3x5rcRfCcjcHGfUOrWY2NvdW50Iiwia3ViZXJpby9-CI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2
[root@master1 pki]# kubectl config set-credentials def-ns-admin --token=eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi14ZHZ4NSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI5MjhiYmNhMS0yNDVjLTExZTktODFjYy0wMDBjMjkxZTM3YzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.EzUF13MElI8b-kuQNh_u1hGQpxgoffm4LdTVoeORKUBTADwqHEtW2arj76oZuI-wQyy5P0v5VvOoefr6h3NpIgbAze8Lqyrpg9wO0Crfi30IE1kZ2wUPYU9P_5inMxmCPLttppyPyc8mQKDkOOB1xFUmEebC63my-dG4CZljsd8zwNU6eXnhaThSUUn12UTvRsbSBLD-dvau1OY6YgDL6mgFl3cVqzCPd7ELpEyNYWCh3x5rcRfCcjcHGfUOrWY2NvdW50Iiwia3ViZXJpby9-CI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2 --kubeconfig=/root/def-ns-admin.conf
User "def-ns-admin" set.
# 设置context
[root@kubernetes01 pki]# kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf
Context "def-ns-admin@kubernetes" created.
# use-context
[root@kubernetes01 pki]# kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf
Switched to context "def-ns-admin@kubernetes".
# 查看conf文件,此时已经完整了
[root@kubernetes01 pki]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.0.0.100:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: def-ns-admin
name: def-ns-admin@kubernetes
current-context: def-ns-admin@kubernetes
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi14ZHZ4NSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI5MjhiYmNhMS0yNDVjLTExZTktODFjYy0wMDBjMjkxZTM3YzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.EzUF13MElI8b-kuQNh_u1hGQpxgoffm4LdTVoeORKUBTADwqHEtW2arj76oZuI-wQyy5P0v5VvOoefr6h3NpIgbAze8Lqyrpg9wO0Crfi30IE1kZ2wUPYU9P_5inMxmCPLttppyPyc8mQKDkOOB1xFUmEebC63my-dG4CZljsd8zwNU6eXnhaThSUUn12UTvRsbSBLD-dvau1OY6YgDL6mgFl3cVqzCPd7ELpEyNYWCh3x5rcRfCcjcHGfUOrWY2NvdW50Iiwia3ViZXJpby9-CI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2