Linux PAM 开发
简介
可插拔验证模块 (Pluggable authentication module, PAM) 为系统登录应用程序提供了验证和相关的安全服务。PAM是一种提供给应用程序通用的身份鉴别与认证,每一种应用程序可以通过编写PAM模块为自己设置访问控制规则。PAM的应用很好的解决了两个问题,一是避免了每一种应用程序都编写自己的访问控制模块,大量减少了重复开发,更重要的是将访问控制与应用程序本身相分离,这样即使以后发现控制算法有问题,也不用重新改写应用程序,只将PAM模块更新替换即可。
PAM作为一种可插拔的模块,实现了认证与操作系统以及应用程序的分离,十分灵活,并且开发方便。并且PAM提供了API接口,应用程序可以方便的调用他们。
体系结构
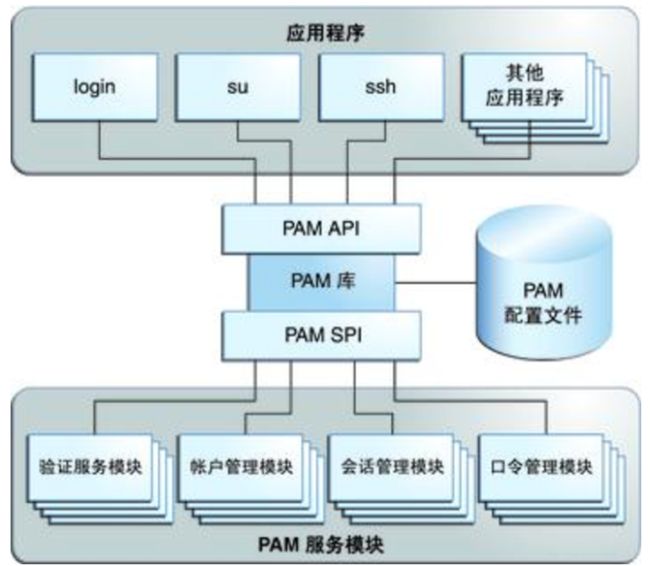
整个PAM分为三部分,最上层是应用程序,如sshd,login等系统自带的程序都已经支持PAM,我们也可以编写自己的应用程序。最下层是PAM额认证模块,总共有四种服务。模块中有编写好的PAM SPI,封装了具体的认证逻辑。中间的PAM库为应用程序提供了PAM API可以供应用程序调用,并向下提供了一种PAM API到PAM SPI的映射,以及PAM配置文件的加载。
编写PAM应用程序分为三部分,应用程序,会话函数,底层服务模块。应用程序就是我们希望对外提供的程序如linux的sshd,sudo等,会话函数是连接应用程序与服务模块的桥梁,负责两者之间的对话。
服务模块开发
服务模块开发是最常用的,也非常简单。linux的服务模块都位于/lib64/security/目录下,包含了pam_unix.so,pam_env.so等,我们模块开发完成编译为.so以后放到此目录即可。
以sshd auth模块开发为例,我们获取ssh远程的token以后,希望实现我们自己的验证,简单代码如下。编写完成以后,执行
gcc pam_test.c -fPIC -shared -o pam_test.so将pam_test.so 文件拷贝到/lib64/security/下,然后在/etc/pam.d/sshd文件下加入
auth sufficient pam_test.so这是自己编译的pam模块已经能起到作用,加入配置文件的时候注意加入的位置,看好不同关键字sufficient,include,optional的含义。
sshd加入PAM模块一定要谨慎,搞不好就跟着机器永远拜拜了。在改PAM的时候记住留一个session不要关,如果sshs的PAM搞混乱,先将sshd_config文件的USE PAM功能关掉,再慢慢的解决问题。
#include 会话函数开发
pam模块已经提编译好的会话函数,我们可以直接调用产生会话,如Google验证码提示输入pin。
struct pam_conv {
int (*conv)(int num_msg, const struct pam_message **msg,
struct pam_response **resp, void *appdata_ptr);
void *appdata_ptr;
};上面是会话函数所处于的结构体,第一个参数就是回函函数,第二个参数是会话的上下文。该函数在PAM源码的/pamlib/misc_conv.c中。
int misc_conv(int num_msg, const struct pam_message **msgm,
struct pam_response **response, void *appdata_ptr)在PAM服务模块中对话的使用方式如下:
#include 会话函数基本实现方式:
/*
* Copyright 2005 Sun Microsystems, Inc. All rights reserved.
* Use is subject to license terms.
*/
#pragma ident "@(#)pam_tty_conv.c 1.4 05/02/12 SMI"
#define __EXTENSIONS__ /* to expose flockfile and friends in stdio.h */
#include 上述总结中对以后进行了引用,感谢。
http://docs.oracle.com/cd/E24847_01/html/E22200/pam-01.html#scrolltoc
https://www.freebsd.org/doc/fr_FR.ISO8859-1/articles/pam/pam-sample-module.html