基于Centos7.2的自选域名配置实现正向和反向解析以及部署并测试缓存DNS服务器
自选域名配置实现正向和反向解析
(注:下文中 IP 192.168.200.101为我的虚拟机IP,涉及上述“192.168.200.101”以及“192.168.200”的内容,请根据实际情况自行修改)
安装 BIND 服务器软件并启动
[root@chuang ~]# rpm -qa |grep bind
bind-license-9.9.4-29.el7.noarch
bind-libs-lite-9.9.4-29.el7.x86_64
#这里使用在线yum源安装
[root@chuang ~]# yum –y install bind bind-utils
Loaded plugins: fastestmirror
#这个地方报错,无法安装,经过后面使用离线yum源分析得出:问题由系统安装bind这类的rpm包冲突引起,查找安装的是那些包,直接卸载:
[root@chuang ~]# rpm -qa |grep bind
bind-license-9.9.4-29.el7.noarch
bind-libs-lite-9.9.4-29.el7.x86_64
[root@chuang ~]# yum -y remove bind-libs-lite bind-license-9.9.4
重新安装Bind服务器软件并启动,这里直接安装 bind 和 bind-utils
若无法安装,尝试 # yum clean all,清除缓存再安装
[root@chuang ~]# yum -y install bind bind-utils
[root@chuang ~]# systemctl start named.service // 启动服务
[root@chuang ~]# systemctl enable named // 设为开机启动查看named进程是否正常启动
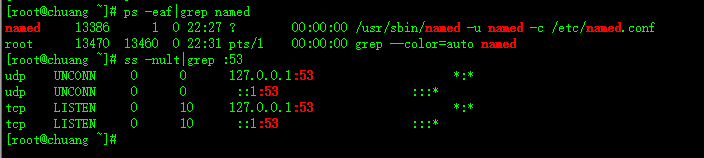
[root@chuang ~]# ps -eaf|grep named // 检查进程
named 12052 1 0 20:56 ? 00:00:00 /usr/sbin/named -u named -c /etc/named.conf
root 12087 12073 0 20:58 pts/1 00:00:00 grep --color=auto named
[root@chuang ~]# ss -nult|grep :53 // 检查监听端口
udp UNCONN 0 0 127.0.0.1:53 *:*
udp UNCONN 0 0 ::1:53 :::*
tcp LISTEN 0 10 127.0.0.1:53 *:*
tcp LISTEN 0 10 ::1:53 :::*
[root@chuang ~]# //开放 TCP 和 UDP 的 53 端口(若防火墙已关闭,则直接无视)
firewall-cmd --permanent --add-port=53/tcp
firewall-cmd --permanent --add-port=53/udp
firewall-cmd --reload // 重新加载防火墙配置,让配置生效//使用getenforce命令查看selinux是否已被禁用,若显示内容非disabled,则vi /etc/selinux/config,修改SELINUX=disabled,重启系统 reboot(若已显示disabled,则无视)
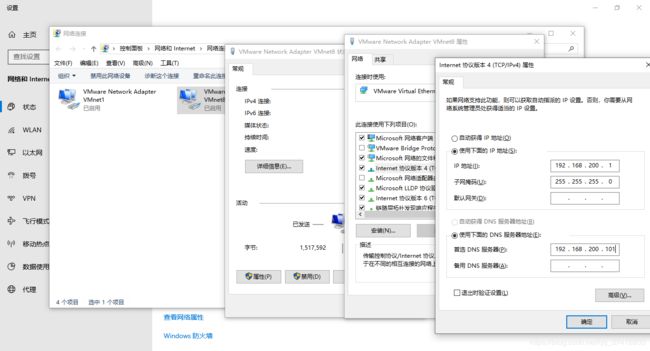
打开与centos虚拟机双机互通的windows客户端网络配置
将虚拟网卡VMnet8的dns设置为与虚拟机IP相同,我的虚拟机IP为192.168.200.101,即DNS设置为192.168.200.101
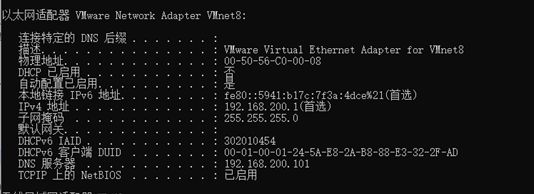
验证(win+R,进入cmd,使用ipconfig /all)如图:
DNS 服务的相关配置文件
修改主要文件 /etc/named.conf
修改前先备份: cp -p /etc/named.conf /etc/named.conf.bak // 参数-p表示备份文件与源文件的属性一致。
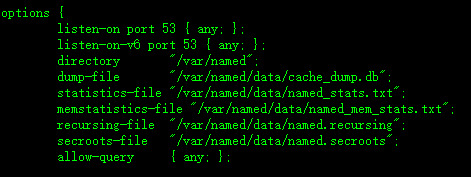
修改配置:vi /etc/named.conf ,(一共三处需要改为any) 配置内容如下:
options {
listen-on port 53 { any; }; //此处修改为any
listen-on-v6 port 53 { any; }; //此处修改为any
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; }; //此处修改为any
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};检查named.conf是否有语法问题
[root@chuang ~]# named-checkconf // 检查named.conf是否有语法问题
[root@chuang ~]# 配置正向解析和反向解析
修改/etc/named.rfc1912.zones
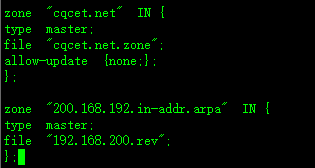
(zone "200.168.192.in-addr.arpa" 里面的IP是从右往左写的,一定要记得修改)
在文件末行添加配置: vi /etc/named.rfc1912.zones , 配置内容如下:
zone "cqcet.net" IN {
type master;
file "cqcet.net.zone";
allow-update {none;};
};
zone "200.168.192.in-addr.arpa" IN {
type master;
file "192.168.200.rev";
};添加正向解析域
基于 name.localhost 模板,创建配置文件:
# cp -p /var/named/named.localhost /var/named/cqcet.net.zone
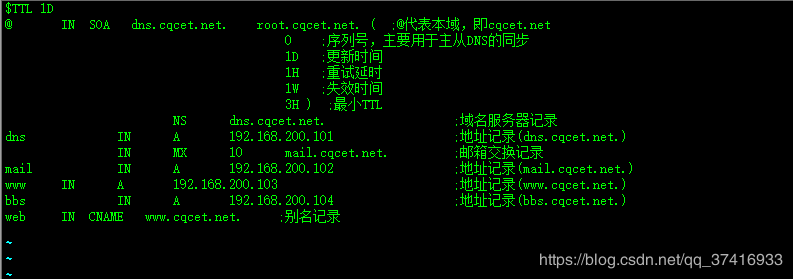
配置正向域名解析文件 cqcet.net.zone : vi /var/named/cqcet.net.zone ,配置内容如下:
$TTL 1D
@ IN SOA dns.cqcet.net. root.cqcet.net. ( ;
0 ;
1D ;
1H ;
1W ;
3H ) ;
NS dns.cqcet.net. ;
dns IN A 192.168.200.101 ;
IN MX 10 mail.cqcet.net. ;
mail IN A 192.168.200.102 ;
www IN A 192.168.200.103 ;
bbs IN A 192.168.200.104 ;
web IN CNAME www.cqcet.net. ;
下图的中文是注释,不需要加上
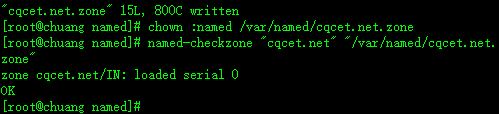
授权 named 用户 chown :named /var/named/cqcet.net.zone
检查区域文件是否正确 named-checkzone "cqcet.net" "/var/named/cqcet.net.zone" ,如图:
添加反向解析域
基于 name.localhost 模板,创建配置文件: cp -p /var/named/named.localhost /var/named/192.168.200.rev
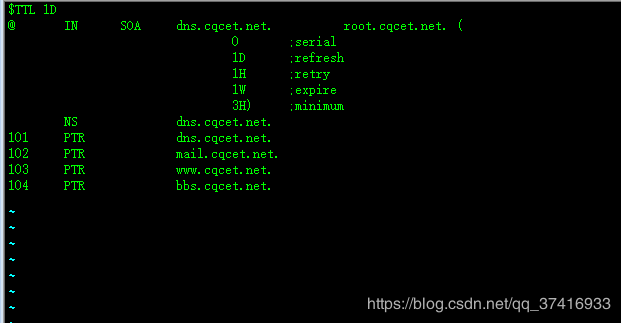
配置反向域名解析文件 192.168.200.rev :#
$TTL 1D
@ IN SOA dns.cqcet.net. root.cqcet.net. (
0 ;serial
1D ;refresh
1H ;retry
1W ;expire
3H) ;minimum
NS dns.cqcet.net.
101 PTR dns.cqcet.net.
102 PTR mail.cqcet.net.
103 PTR www.cqcet.net.
104 PTR bbs.cqcet.net.
授权 named 用户 chown :named /var/named/192.168.200.rev
检查区域文件是否正确 named-checkzone "200.168.192.in-addr.arpa" "/var/named/192.168.200.rev" ,
[root@chuang named]# chown :named /var/named/192.168.200.rev
[root@chuang named]# named-checkzone "200.168.192.in-addr.arpa" "/var/named/192.168.200.rev"
zone 200.168.192.in-addr.arpa/IN: loaded serial 0
OK
[root@chuang named]# 如图:
重启 named 服务,让配置生效
重启 named 服务,让配置生效 systemctl restart named
在 Linux 下的 DNS 客户端的设置及测试
注册域名解析服务器到配置文件
配置 ifcfg-xxxx
# vi /etc/sysconfig/network-scripts/ifcfg-eno16777736 , 具体内容如下:
TYPE=Ethernet
BOOTPROTO=static
DEFROUTE=yes
PEERDNS=yes
PEERROUTES=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_PEERDNS=yes
IPV6_PEERROUTES=yes
IPV6_FAILURE_FATAL=no
NAME=eno16777736
UUID=20f71f51-c409-48a7-8ac1-c1ab84ac31e9
DEVICE=eno16777736
IPADDR=192.168.200.101
PREFIX=24
GATEWAY=192.168.200.2
DNS1=192.168.200.101 // 新增,本机就是域名解析服务器
DNS2=8.8.8.8
ONBOOT=yes如图:
重启网络服务,让配置生效
systemctl restart network.service使用 nslookup 测试
bind-utils 软件包本身提供了测试工具 nslookup
正向域名解析测试
nslookup dns.cqcet.net
反向域名解析测试
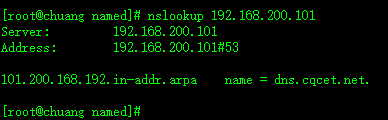
nslookup 192.168.200.101
多次验证(可选)
部署并测试缓存DNS服务器(注:基于上面的步骤)
首先编辑主配置文件, /etc/named.conf
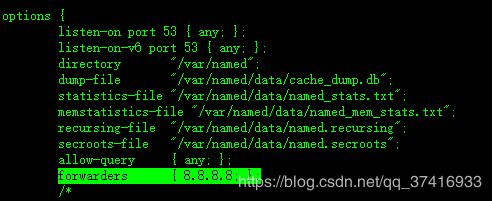
[root@chuang ~]# vi /etc/named.conf在options中配置真实的DNS服务器地址,编辑如下:
forwarders { 8.8.8.8; };
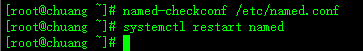
检查主配置配置(named-checkconf /etc/named.conf),并重启named服务(systemctl restart named )
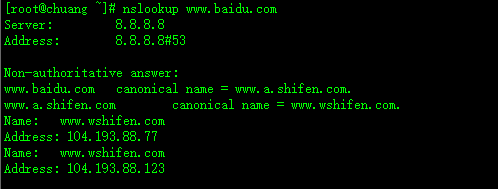
进行测试如下:nslookup www.baidu.com