- ARM驱动学习之4小结
JT灬新一
嵌入式C++arm开发学习linux
ARM驱动学习之4小结#include#include#include#include#include#defineDEVICE_NAME"hello_ctl123"MODULE_LICENSE("DualBSD/GPL");MODULE_AUTHOR("TOPEET");staticlonghello_ioctl(structfile*file,unsignedintcmd,unsignedlo
- SpringBlade dict-biz/list 接口 SQL 注入漏洞
文章永久免费只为良心
oracle数据库
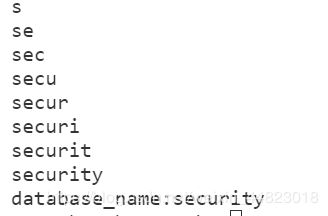
SpringBladedict-biz/list接口SQL注入漏洞POC:构造请求包查看返回包你的网址/api/blade-system/dict-biz/list?updatexml(1,concat(0x7e,md5(1),0x7e),1)=1漏洞概述在SpringBlade框架中,如果dict-biz/list接口的后台处理逻辑没有正确地对用户输入进行过滤或参数化查询(PreparedSta
- react-intl——react国际化使用方案
苹果酱0567
面试题汇总与解析java开发语言中间件springboot后端
国际化介绍i18n:internationalization国家化简称,首字母+首尾字母间隔的字母个数+尾字母,类似的还有k8s(Kubernetes)React-intl是React中最受欢迎的库。使用步骤安装#usenpmnpminstallreact-intl-D#useyarn项目入口文件配置//index.tsximportReactfrom"react";importReactDOMf
- Linux CTF逆向入门
蚁景网络安全
linux运维CTF
1.ELF格式我们先来看看ELF文件头,如果想详细了解,可以查看ELF的manpage文档。关于ELF更详细的说明:e_shoff:节头表的文件偏移量(字节)。如果文件没有节头表,则此成员值为零。sh_offset:表示了该section(节)离开文件头部位置的距离+-------------------+|ELFheader|---++--------->+-------------------
- Windows安装ciphey编码工具,附一道ciscn编码题例
im-Miclelson
CTF工具网络安全
TA是什么一款智能化的编码分析解码工具,对于CTF中复杂性编码类题目可以快速攻破。编码自动分析解码的神器。如何安装Windows环境Python3.864位(最新的版本不兼容,32位的也不行)PIP直接安装pipinstallciphey-ihttps://pypi.mirrors.ustc.edu.cn/simple/安装后若是出现报错请根据错误代码行数找到对应文件,r修改成rb即可。使用标准语
- Web安全:Web体系架构存在的安全问题和解决方室
程序员-张师傅
前端安全web安全前端
Web体系架构在提供丰富功能和高效服务的同时,也面临着诸多安全问题。这些问题可能涉及数据泄露、服务中断、系统被控制等多个方面,对企业和个人造成不可估量的损失。以下是对Web体系架构中存在的安全问题及解决方案的详细分析:Web体系架构存在的安全问题注入攻击SQL注入:攻击者通过在输入字段中插入恶意SQL代码,操控后台数据库,窃取、篡改或删除数据。OS命令注入:攻击者通过输入字段插入恶意代码,执行系统
- 2005年高考英语北京卷 - 阅读理解C
让文字更美
Howcouldwepossiblythinkthatkeepinganimalsincagesinunnaturalenvironments-mostlyforentertainmentpurposes-isfairandrespectful?我们怎么可能认为把动物关在非自然环境的笼子里——主要是为了娱乐目的——是公平和尊重的呢?Zooofficialssaytheyareconcernedab
- CTF-bugku-crypto-[7+1+0]-base64解码之后做偏移
沧海一粟日尽其用
算法安全python
CTF-bugku-crypto-[7+1+0]-base64解码之后做偏移1.题目2.解题思路2.1base64编码原理2.2解题思路2.2.1base64解码找规律2.2.2破解思路3.解题脚本4.flag5.附EASCII码表1.题目提示信息:7+1+0?格式bugku{xxxxx}密文:4nXna/V7t2LpdLI44mn0fQ==要求:破解密文获得flag2.解题思路2.1base64
- CTF常见编码及加解密(超全)第二篇
不会代码的小徐
编码密码网络安全密码学预编码
HTML实体编码简述:字符实体是用一个编号写入HTML代码中来代替一个字符,在使用浏览器访问网页时会将这个编号解析还原为字符以供阅读。举例:highlighter-HTML明文:hello,world.十进制:hello,world.十六进制:hel
- 2021国家开放大学计算机网络安全技术形成性考核五
chaoliang.top
国开试题网络安全网络安全
本人还会继续更新其他国家开放大学的试题,请大家多多关注,如果有什么建议,还希望大家提出来,本人也好完善本人在测试答案的时候发现,本章考试回顾结果中明明选对了答案,但是提示错误的情况,并且该题没有提示正确答案,这种情况应该是国开试题出现bug导致,请大家不要担心,如果有追求完美的同学,多答几次,可能就会避开这种题,因为出题是随机的。1.SQL注入一般可通过网页表单直接输入选择多项:对错正确答案:对2
- CTF——web方向学习攻略
一则孤庸
CTF网络安全CTF
1计算机基础操作系统:熟悉Linux命令,方便使用Kali。网络技术:HCNA、CCNA。编程能力:拔高项,有更好。2web应用HTTP协议:必须掌握web开发框架web安全测试3数据库数据库基本操作SQL语句数据库优化4刷题
- CTF——web总结
oliveira-time
ctfweb安全
解题思路做题先看源码关注可下载的资源(zip压缩包)抓包寻找可能存在的加密信息(base64)不管三七二十一先扫描目录再说ps:正常的应该是先扫描目录,然后发现后台进行爆破,发现爆破困难,然后去社工找其他信息。CTF——web个人总结_ctfweb-CSDN博客
- VueTreeselect el-tree-select 多选
小小并不小
Vueelementjsvue.jsjavascript
1、VueTreeselect是一个多选组件npminstall--save@riophae/vue-treeselect全部代码//importthecomponentimportTreeselectfrom'@riophae/vue-treeselect'//importthestylesimport'@riophae/vue-treeselect/dist/vue-treeselect.cs
- ctf逆向解题——Bomb二进制炸弹
Funkypantss
BombPhase1在输入阶段将由文件输入的字符存储在input中,在phase1,该阶段将原字符串存储到rdi中,调用pases_1函数进行字符串比较。image进入phase1函数,该函数将原字符串rdi与预先设定的字符串“BorderrelationswithCanadahaveneverbeenbetter.”(存储在rsi中)进行比较,用于比较的函数是strings_not_equal,
- 【CTF】MISC常用工具集锦/使用方法简介
不会代码的小徐
misc网络安全测试工具
前言#MISC题型多变而且工具繁杂,因此自己花时间整理了一份工具列表,以便日后参考用流畅地阅读这篇博客,你可能需要:Python2.7.18+Python3.8+任何一个更高版本的Python,使用conda管理Linux虚拟机,kali即可流畅访问Google/GitHub等站点的网络通用工具#PuzzleSolver#专为misc手打造的瑞士军刀(?),整合了多种脚本(base,字频分析,pn
- 网络安全的相关比赛有哪些?需要掌握哪些必备技能?
网安学习
web安全安全网络安全的相关比赛有哪
01、CTF(夺旗赛)这是一种最常见的网络安全竞技形式,要求参赛者在限定时间内解决一系列涉及密码学、逆向工程、漏洞利用、取证分析等领域的挑战,获取标志(flag)并提交得分。通过举办CTF来培养网络安全人才,已经发展成为了国际网络安全圈的共识。CTF赛事可以分为线上赛和线下赛,线上赛通常是解题模式(Jeopardy),线下赛通常是攻防模式(Attack-Defense)。CTF赛事的代表性线下赛事
- 第四部分:1---文件内核对象,文件描述符,输出重定向
S+叮当猫
LinuxCentOS算法linux服务器
目录structfile内核对象:如何读写文件?文件描述符在文件描述符表中的分配规则:输出重定向初步解析:dup2实现复制文件描述符:structfile内核对象:structfile是在内核空间中创建的用于描述文件的结构体,每当一个文件被打开时,内核会为该文件创建一个对应的structfile结构体,并在文件描述符表中为其分配一个文件描述符。基于文件的定义(文件=内容+属性),structfil
- 最新网络安全(黑客)——自学篇
黑客小雨
web安全安全
*需要的小伙伴关注我第一阶段:基础操作入门,学习基础知识入门的第一步是学习一些当下主流的安全工具课程并配套基础原理的书籍,一般来说这个过程在1个月左右比较合适。在这个阶段,你已经对网络安全有了基本的了解。如果你学完了第一步,相信你已经在理论上明白了上面是sql注入,什么是xss攻击,对burp、msf、cs等安全工具也掌握了基础操作。这个时候最重要的就是开始打地基!所谓的“打地基”其实就是系统化的
- 网络攻防WEB入门指南
youhao108
网络攻防web渗透测试网络安全网络攻防
网络攻防WEB入门指南(大佬绕路)文章目录前言学习网络攻防该如何入门前言我对网络攻防的理解,分为比赛和实战两个部分,两者所学习的知识虽有共通之处,但还是有很大区别,我也在向实战的状态转换,不过二者入门所要掌握的知识差别不大。下面主要从网络攻防竞赛角度,也就是知名的CTF夺旗赛,来谈谈网络攻防知识如何入门。学习网络攻防该如何入门常规CTF比赛主要分为线上做题,以及线下AWD攻防(AttackWith
- 软考 - 系统架构设计师 - 设计模式
小林想被监督学习
系统架构设计师系统架构设计模式
目录概念创建型设计模式抽象工厂模式(AbstractFactoryPattern)优点缺点应用场景总结构建器模式(BuilderPattern)优点缺点应用场景工厂方法模式(factorymethod)优点缺点应用场景原型模式(prototype)优点缺点应用场景单例模式(Singleton)优点缺点应用场景结构型设计模式适配器模式(Adapter)优点缺点应用场景桥接模式(Bridge)优点缺点
- Spring Interceptor
Draper
Spring中使用Interceptor拦截器与Servlet的listener比较相似,同样是监听请求,同样需要配置,一个是在web.xml中,Spring拦截器是在Spring配置文件中拦截未登录用户访问某些连接拦截日志信息拦截SQL注入执行顺序是preHandle->controller->postHandle->afterCompletionSpringInterceptor属于链式调用,
- HP 应用程序如何防止 SQL 注入攻击提高程序安全稳定性?
xiaohuojian1
android
在PHP应用程序中,防止SQL注入攻击是确保程序安全和稳定的关键步骤。SQL注入攻击可以让恶意用户通过操控SQL查询来访问、修改或删除数据库中的数据,严重时甚至可能导致系统的完全控制。以下是防止SQL注入攻击的有效策略和最佳实践,以帮助提高PHP应用程序的安全性和稳定性。一、使用预处理语句和参数化查询1.预处理语句https://github.com/xhj2/p/issues/7预处理语句是防止
- ctfshow web入门 ssrf web351~web360
kikkeve
ctfshowphpweb安全安全
目录SSRF基础web351web352、353web354web355web356web357web358web359web360SSRF基础SSRF(Server-SideRequestForgery:服务器端请求伪造)就是让服务器去请求服务器的资源,因为我们远程请求不到。curl_init():初始curl会话curl_setopt():会话设置curl_exec():执行curl会话,获取
- flutter 一键打出不同包名、应用名、版本名、签名、应用图标、版本号的安装包
Sindyue
flutter
1.build.gradle文件中配置不同的应用信息flavorDimensions"app"productFlavors{app1{//配置包名manifestPlaceholders=[str:"releaseStr",package_name:"com.example.demo1"]applicationId"com.example.demo1"versionCode1versionName
- CTF 竞赛密码学方向学习路径规划
David Max
CTF学习笔记密码学ctf信息安全
目录计算机科学基础计算机科学概念的引入、兴趣的引导开发环境的配置与常用工具的安装WattToolkit(Steam++)、机场代理Scoop(Windows用户可选)常用Python库SageMathLinux小工具yafuOpenSSLMarkdown编程基础Python其他编程语言、算法与数据结构(可选)数学基础离散数学与抽象代数复杂性分析密码学的正式学习兴趣的培养做题小技巧系统学习需要了解并
- Web应用防火墙
Smile灬凉城666
网络安全WAF安全
一、定义与目的WAF是一种特殊类型的防火墙,专门设计用于监视、过滤和阻挡进出Web应用的HTTP流量。其主要目的是保护Web应用免受如XSS(跨站脚本)、SQL注入、会话劫持等网络攻击。二、工作原理WAF工作在应用层,即OSI模型的第七层。它通过对HTTP/HTTPS请求进行解析、协议检测、攻击识别和恶意行为阻断等步骤来保护Web应用。具体来说,WAF会解析进入Web应用的HTTP/HTTPS请求
- MySQL8.0新特性~最左前缀匹配原则被打破了
进击的CJR
mysqlmysql
测试在MySQL8.0.25和mysql5.7.33中创建如下CREATETABLEt1(f1INTNOTNULL,f2INTNOTNULL,PRIMARYKEY(f1,f2));INSERTINTOt1VALUES(1,1),(1,2),(1,3),(1,4),(1,5),(2,1),(2,2),(2,3),(2,4),(2,5);INSERTINTOt1SELECTf1,f2+5FROMt1;
- Web安全与网络安全:SQL漏洞注入
hong161688
web安全sqloracle
Web安全与网络安全:SQL漏洞注入引言在Web安全领域,SQL注入漏洞(SQLInjectionVulnerability)是一种极具破坏性的安全威胁。它允许攻击者通过向Web应用程序的输入字段中插入或“注入”恶意的SQL代码片段,从而操纵后台数据库系统,执行未授权的数据库查询,甚至可能获取数据库管理权限,进而对整个系统造成严重的安全损害。本文将从SQL注入的原理、分类、危害及防御策略等方面进行
- Web安全与网络安全:SQL漏洞注入
bigbig猩猩
typescriptvue.js前端
Web安全与网络安全:SQL漏洞注入引言在Web安全领域,SQL注入漏洞(SQLInjectionVulnerability)是一种极具破坏性的安全威胁。它允许攻击者通过向Web应用程序的输入字段中插入或“注入”恶意的SQL代码片段,从而操纵后台数据库系统,执行未授权的数据库查询,甚至可能获取数据库管理权限,进而对整个系统造成严重的安全损害。本文将从SQL注入的原理、分类、危害及防御策略等方面进行
- hackcon ctf 2018 | pwn wp
fantasy_learner
BOF漏洞点:栈溢出利用过程栈溢出跳转callMeMaybe函数获得flagexpSheSellsSeaShells90流程分析:给出了输入的栈地址有一个栈溢出点没有nx利用过程:根据以上三点,得出可以使用ret2shellcode使用shellcraft生成shellcode利用栈溢出,输入并跳转到shellcodeexpSimpleYetElegent150这道题目做了最久,卡在了能否根据_d
- 项目中 枚举与注解的结合使用
飞翔的马甲
javaenumannotation
前言:版本兼容,一直是迭代开发头疼的事,最近新版本加上了支持新题型,如果新创建一份问卷包含了新题型,那旧版本客户端就不支持,如果新创建的问卷不包含新题型,那么新旧客户端都支持。这里面我们通过给问卷类型枚举增加自定义注解的方式完成。顺便巩固下枚举与注解。
一、枚举
1.在创建枚举类的时候,该类已继承java.lang.Enum类,所以自定义枚举类无法继承别的类,但可以实现接口。
- 【Scala十七】Scala核心十一:下划线_的用法
bit1129
scala
下划线_在Scala中广泛应用,_的基本含义是作为占位符使用。_在使用时是出问题非常多的地方,本文将不断完善_的使用场景以及所表达的含义
1. 在高阶函数中使用
scala> val list = List(-3,8,7,9)
list: List[Int] = List(-3, 8, 7, 9)
scala> list.filter(_ > 7)
r
- web缓存基础:术语、http报头和缓存策略
dalan_123
Web
对于很多人来说,去访问某一个站点,若是该站点能够提供智能化的内容缓存来提高用户体验,那么最终该站点的访问者将络绎不绝。缓存或者对之前的请求临时存储,是http协议实现中最核心的内容分发策略之一。分发路径中的组件均可以缓存内容来加速后续的请求,这是受控于对该内容所声明的缓存策略。接下来将讨web内容缓存策略的基本概念,具体包括如如何选择缓存策略以保证互联网范围内的缓存能够正确处理的您的内容,并谈论下
- crontab 问题
周凡杨
linuxcrontabunix
一: 0481-079 Reached a symbol that is not expected.
背景:
*/5 * * * * /usr/IBMIHS/rsync.sh
- 让tomcat支持2级域名共享session
g21121
session
tomcat默认情况下是不支持2级域名共享session的,所有有些情况下登陆后从主域名跳转到子域名会发生链接session不相同的情况,但是只需修改几处配置就可以了。
打开tomcat下conf下context.xml文件
找到Context标签,修改为如下内容
如果你的域名是www.test.com
<Context sessionCookiePath="/path&q
- web报表工具FineReport常用函数的用法总结(数学和三角函数)
老A不折腾
Webfinereport总结
ABS
ABS(number):返回指定数字的绝对值。绝对值是指没有正负符号的数值。
Number:需要求出绝对值的任意实数。
示例:
ABS(-1.5)等于1.5。
ABS(0)等于0。
ABS(2.5)等于2.5。
ACOS
ACOS(number):返回指定数值的反余弦值。反余弦值为一个角度,返回角度以弧度形式表示。
Number:需要返回角
- linux 启动java进程 sh文件
墙头上一根草
linuxshelljar
#!/bin/bash
#初始化服务器的进程PId变量
user_pid=0;
robot_pid=0;
loadlort_pid=0;
gateway_pid=0;
#########
#检查相关服务器是否启动成功
#说明:
#使用JDK自带的JPS命令及grep命令组合,准确查找pid
#jps 加 l 参数,表示显示java的完整包路径
#使用awk,分割出pid
- 我的spring学习笔记5-如何使用ApplicationContext替换BeanFactory
aijuans
Spring 3 系列
如何使用ApplicationContext替换BeanFactory?
package onlyfun.caterpillar.device;
import org.springframework.beans.factory.BeanFactory;
import org.springframework.beans.factory.xml.XmlBeanFactory;
import
- Linux 内存使用方法详细解析
annan211
linux内存Linux内存解析
来源 http://blog.jobbole.com/45748/
我是一名程序员,那么我在这里以一个程序员的角度来讲解Linux内存的使用。
一提到内存管理,我们头脑中闪出的两个概念,就是虚拟内存,与物理内存。这两个概念主要来自于linux内核的支持。
Linux在内存管理上份为两级,一级是线性区,类似于00c73000-00c88000,对应于虚拟内存,它实际上不占用
- 数据库的单表查询常用命令及使用方法(-)
百合不是茶
oracle函数单表查询
创建数据库;
--建表
create table bloguser(username varchar2(20),userage number(10),usersex char(2));
创建bloguser表,里面有三个字段
&nbs
- 多线程基础知识
bijian1013
java多线程threadjava多线程
一.进程和线程
进程就是一个在内存中独立运行的程序,有自己的地址空间。如正在运行的写字板程序就是一个进程。
“多任务”:指操作系统能同时运行多个进程(程序)。如WINDOWS系统可以同时运行写字板程序、画图程序、WORD、Eclipse等。
线程:是进程内部单一的一个顺序控制流。
线程和进程
a. 每个进程都有独立的
- fastjson简单使用实例
bijian1013
fastjson
一.简介
阿里巴巴fastjson是一个Java语言编写的高性能功能完善的JSON库。它采用一种“假定有序快速匹配”的算法,把JSON Parse的性能提升到极致,是目前Java语言中最快的JSON库;包括“序列化”和“反序列化”两部分,它具备如下特征:
- 【RPC框架Burlap】Spring集成Burlap
bit1129
spring
Burlap和Hessian同属于codehaus的RPC调用框架,但是Burlap已经几年不更新,所以Spring在4.0里已经将Burlap的支持置为Deprecated,所以在选择RPC框架时,不应该考虑Burlap了。
这篇文章还是记录下Burlap的用法吧,主要是复制粘贴了Hessian与Spring集成一文,【RPC框架Hessian四】Hessian与Spring集成
- 【Mahout一】基于Mahout 命令参数含义
bit1129
Mahout
1. mahout seqdirectory
$ mahout seqdirectory
--input (-i) input Path to job input directory(原始文本文件).
--output (-o) output The directory pathna
- linux使用flock文件锁解决脚本重复执行问题
ronin47
linux lock 重复执行
linux的crontab命令,可以定时执行操作,最小周期是每分钟执行一次。关于crontab实现每秒执行可参考我之前的文章《linux crontab 实现每秒执行》现在有个问题,如果设定了任务每分钟执行一次,但有可能一分钟内任务并没有执行完成,这时系统会再执行任务。导致两个相同的任务在执行。
例如:
<?
//
test
.php
- java-74-数组中有一个数字出现的次数超过了数组长度的一半,找出这个数字
bylijinnan
java
public class OcuppyMoreThanHalf {
/**
* Q74 数组中有一个数字出现的次数超过了数组长度的一半,找出这个数字
* two solutions:
* 1.O(n)
* see <beauty of coding>--每次删除两个不同的数字,不改变数组的特性
* 2.O(nlogn)
* 排序。中间
- linux 系统相关命令
candiio
linux
系统参数
cat /proc/cpuinfo cpu相关参数
cat /proc/meminfo 内存相关参数
cat /proc/loadavg 负载情况
性能参数
1)top
M:按内存使用排序
P:按CPU占用排序
1:显示各CPU的使用情况
k:kill进程
o:更多排序规则
回车:刷新数据
2)ulimit
ulimit -a:显示本用户的系统限制参
- [经营与资产]保持独立性和稳定性对于软件开发的重要意义
comsci
软件开发
一个软件的架构从诞生到成熟,中间要经过很多次的修正和改造
如果在这个过程中,外界的其它行业的资本不断的介入这种软件架构的升级过程中
那么软件开发者原有的设计思想和开发路线
- 在CentOS5.5上编译OpenJDK6
Cwind
linuxOpenJDK
几番周折终于在自己的CentOS5.5上编译成功了OpenJDK6,将编译过程和遇到的问题作一简要记录,备查。
0. OpenJDK介绍
OpenJDK是Sun(现Oracle)公司发布的基于GPL许可的Java平台的实现。其优点:
1、它的核心代码与同时期Sun(-> Oracle)的产品版基本上是一样的,血统纯正,不用担心性能问题,也基本上没什么兼容性问题;(代码上最主要的差异是
- java乱码问题
dashuaifu
java乱码问题js中文乱码
swfupload上传文件参数值为中文传递到后台接收中文乱码 在js中用setPostParams({"tag" : encodeURI( document.getElementByIdx_x("filetag").value,"utf-8")});
然后在servlet中String t
- cygwin很多命令显示command not found的解决办法
dcj3sjt126com
cygwin
cygwin很多命令显示command not found的解决办法
修改cygwin.BAT文件如下
@echo off
D:
set CYGWIN=tty notitle glob
set PATH=%PATH%;d:\cygwin\bin;d:\cygwin\sbin;d:\cygwin\usr\bin;d:\cygwin\usr\sbin;d:\cygwin\us
- [介绍]从 Yii 1.1 升级
dcj3sjt126com
PHPyii2
2.0 版框架是完全重写的,在 1.1 和 2.0 两个版本之间存在相当多差异。因此从 1.1 版升级并不像小版本间的跨越那么简单,通过本指南你将会了解两个版本间主要的不同之处。
如果你之前没有用过 Yii 1.1,可以跳过本章,直接从"入门篇"开始读起。
请注意,Yii 2.0 引入了很多本章并没有涉及到的新功能。强烈建议你通读整部权威指南来了解所有新特性。这样有可能会发
- Linux SSH免登录配置总结
eksliang
ssh-keygenLinux SSH免登录认证Linux SSH互信
转载请出自出处:http://eksliang.iteye.com/blog/2187265 一、原理
我们使用ssh-keygen在ServerA上生成私钥跟公钥,将生成的公钥拷贝到远程机器ServerB上后,就可以使用ssh命令无需密码登录到另外一台机器ServerB上。
生成公钥与私钥有两种加密方式,第一种是
- 手势滑动销毁Activity
gundumw100
android
老是效仿ios,做android的真悲催!
有需求:需要手势滑动销毁一个Activity
怎么办尼?自己写?
不用~,网上先问一下百度。
结果:
http://blog.csdn.net/xiaanming/article/details/20934541
首先将你需要的Activity继承SwipeBackActivity,它会在你的布局根目录新增一层SwipeBackLay
- JavaScript变换表格边框颜色
ini
JavaScripthtmlWebhtml5css
效果查看:http://hovertree.com/texiao/js/2.htm代码如下,保存到HTML文件也可以查看效果:
<html>
<head>
<meta charset="utf-8">
<title>表格边框变换颜色代码-何问起</title>
</head>
<body&
- Kafka Rest : Confluent
kane_xie
kafkaRESTconfluent
最近拿到一个kafka rest的需求,但kafka暂时还没有提供rest api(应该是有在开发中,毕竟rest这么火),上网搜了一下,找到一个Confluent Platform,本文简单介绍一下安装。
这里插一句,给大家推荐一个九尾搜索,原名叫谷粉SOSO,不想fanqiang谷歌的可以用这个。以前在外企用谷歌用习惯了,出来之后用度娘搜技术问题,那匹配度简直感人。
环境声明:Ubu
- Calender不是单例
men4661273
单例Calender
在我们使用Calender的时候,使用过Calendar.getInstance()来获取一个日期类的对象,这种方式跟单例的获取方式一样,那么它到底是不是单例呢,如果是单例的话,一个对象修改内容之后,另外一个线程中的数据不久乱套了吗?从试验以及源码中可以得出,Calendar不是单例。
测试:
Calendar c1 =
- 线程内存和主内存之间联系
qifeifei
java thread
1, java多线程共享主内存中变量的时候,一共会经过几个阶段,
lock:将主内存中的变量锁定,为一个线程所独占。
unclock:将lock加的锁定解除,此时其它的线程可以有机会访问此变量。
read:将主内存中的变量值读到工作内存当中。
load:将read读取的值保存到工作内存中的变量副本中。
- schedule和scheduleAtFixedRate
tangqi609567707
javatimerschedule
原文地址:http://blog.csdn.net/weidan1121/article/details/527307
import java.util.Timer;import java.util.TimerTask;import java.util.Date;
/** * @author vincent */public class TimerTest {
- erlang 部署
wudixiaotie
erlang
1.如果在启动节点的时候报这个错 :
{"init terminating in do_boot",{'cannot load',elf_format,get_files}}
则需要在reltool.config中加入
{app, hipe, [{incl_cond, exclude}]},
2.当generate时,遇到:
ERROR