Hyperledger Fabric 1.0 快速搭建 -------- 多机部署 Fabric CA节点服务
前言
在这里我推荐两位大神的博客,可以参考或者直接跟着这两位大神学习,我是阅读这两位大神的博客和《深度探索区块链Hyperledger技术与应用》一书部署的
《深度探索区块链Hyperledger技术与应用》作者:张增骏、董宁、朱轩彤、陈剑雄 著。
深蓝大大:https://www.cnblogs.com/studyzy/category/1024666.html
Aberic大神:https://www.cnblogs.com/aberic/category/1148898.html
Fabric CA服务是官方提供的数字证书管理的一个默认实现,Fabric CA是超级账本的数字证书认证中心,提供了以下功能:
用户信息的注册;
数字证书的发行;
数字证书的延期与吊销
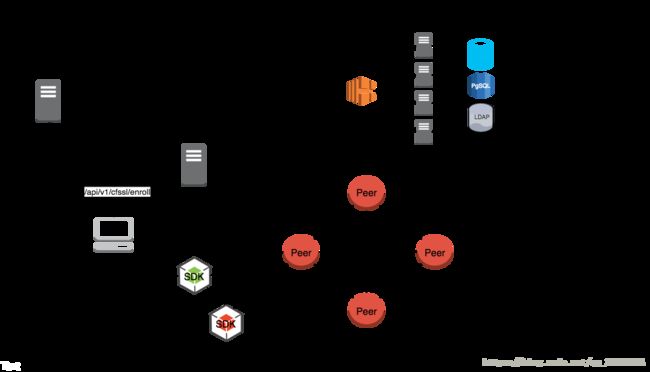
Fabric CA 服务端提供用户登记和注册数字证书管理功能,数据存储后端可以是Mysql、PostgreSQL、LDAP等,如果配置了LDAP,用户信息存在于LDAP中,而不是存放在Mysql或者PostgreSQL,通过数据存储和业务逻辑的分离,Fabric CA服务能够采用无状态的集群部署。通过HAProxy等软件实现负载均衡功能,实现服务的高可用。
图片来自官网,阐述了Fabric CA在整个超级账本中的作用
有人说CA就是MSP的具体实现,之前用户的MSP证书是通过平台特定二进制文件来生成的,现在我们是通过访问CA服务来实现证书的发行,和用户的注册。CA服务还提供了数字证书的延期和吊销。
而能给别人发放证书的有两种,一种是根证书(root),一种是tls根证书,被这两种根证书发行的证书叫做 ”中间CA证书“ 发行的证书有私钥和公钥(cert证书,我这样写不严谨,只是我自己理解的,希望不要误导)。
所以这次我部署了两个CA服务,一个放的是tlsCA根证书,一个是CA根证书,tlsCA服务可以不用部署,视情况可定,我需要所以部署了。TlsCA和CA的部署顺序与配置是大部分一样的,没有本质上的区别,都是CA服务器,只是证书文件(ca-cert.pem,ca-key.pem)用的不一样,tlsCA服务器用的是tls根证书,CA服务器用的是CA根证书,把这两个分清楚就可以了,这两个CA节点分别在不同的服务器节点上部署即可。
关于CA更详细的可以参考官网文档:https://hyperledger-fabric-ca.readthedocs.io/en/latest/
还有一个博文应该是根据官网写的笔记:https://blog.csdn.net/baidu_39649815/article/details/76259031
开始
1.配置文件与证书文件
CA服务在node6机器上进行操作
1.1因为我们选择使用的是PostgreSQL数据库来存储,所以在启动CA之前一定要先启动数据库容器
[root@node6 ~]# mkdir -p /u01/data/postgresql
[root@node6 ~]# docker run --name mypostgres1 -e POSTGRES_PASSWORD=postgres -e POSTGRES_USER=postgres -p 5432:5432 -v /u01/data/postgresql:/var/lib/postgresql/data -d postgres -c 'shared_buffers=256MB' -c 'max_connections=500'1.2.配置CA 服务fabric-ca-server-config.yaml文件 这个文件会在启动CA容器的时候默认在你映射的目录下寻找,如果没有这个文件,CA服务会自动生成一个,设置什么的都是默认的,在这里我们手动创建一个fabric-ca-server-config.yaml
[root@node6 ~]# mkdir -p /u01/ca
[root@node6 ~]# cd -p /u01/ca
[root@node6 ~]# vi fabric-ca-server-config.yaml
#
# COMMAND LINE ARGUMENTS AND ENVIRONMENT VARIABLES
# ------------------------------------------------
# Each configuration element can be overridden via command line
# arguments or environment variables. The precedence for determining
# the value of each element is as follows:
# 1) command line argument
# Examples:
# a) --port 443
# To set the listening port
# b) --ca-keyfile ../mykey.pem
# To set the "keyfile" element in the "ca" section below;
# note the '-' separator character.
# 2) environment variable
# Examples:
# a) FABRIC_CA_SERVER_PORT=443
# To set the listening port
# b) FABRIC_CA_SERVER_CA_KEYFILE="../mykey.pem"
# To set the "keyfile" element in the "ca" section below;
# note the '_' separator character.
# 3) configuration file
# 4) default value (if there is one)
# All default values are shown beside each element below.
#
# FILE NAME ELEMENTS
# ------------------
# The value of all fields whose name ends with "file" or "files" are
# name or names of other files.
# For example, see "tls.certfile" and "tls.clientauth.certfiles".
# The value of each of these fields can be a simple filename, a
# relative path, or an absolute path. If the value is not an
# absolute path, it is interpretted as being relative to the location
# of this configuration file.
#
#############################################################################
# Server's listening port (default: 7054) 默认的端口
port: 7054
# Enables debug logging (default: false)
# 日志的级别默认是false不开启 开启后会有更多的信息打印在控制台
debug: true
# Size limit of an acceptable CRL in bytes (default: 512000)
crlsizelimit: 512000
#############################################################################
# TLS section for the server's listening port
#
# The following types are supported for client authentication: NoClientCert,
# RequestClientCert, RequireAnyClientCert, VerifyClientCertIfGiven,
# and RequireAndVerifyClientCert.
#
# Certfiles is a list of root certificate authorities that the server uses
# when verifying client certificates.
#############################################################################
#是否在服务端启用TLS,如果启用TLS后进行身份验证的证书和签名的私钥
tls:
# Enable TLS (default: false)
enabled: false
# TLS for the server's listening port
certfile: server.crt #如果开启后tls的证书就要把你用的哪个节点的tls证书和私钥放在 /u01/ca下
keyfile: server.key
clientauth:
type: noclientcert
certfiles: ca.crt
#############################################################################
# The CA section contains information related to the Certificate Authority
# including the name of the CA, which should be unique for all members
# of a blockchain network. It also includes the key and certificate files
# used when issuing enrollment certificates (ECerts) and transaction
# certificates (TCerts).
# The chainfile (if it exists) contains the certificate chain which
# should be trusted for this CA, where the 1st in the chain is always the
# root CA certificate.
#############################################################################
# 包括实例的名称、签名私钥文件、身份验证证书和证书链文件乖;这些私钥和证书文件会用来作为生成ECert、TCert的根证书
ca:
# Name of this CA CA服务名称. 可以支持多个服务
name: userca
# Key file (default: ca-key.pem) 密钥文件(默认: ca-key.pem)
keyfile: ca-key.pem
# Certificate file (default: ca-cert.pem) 证书文件(默认: ca-cert.pem)
certfile: ca-cert.pem
# Chain file (default: chain-cert.pem) 证书链文件(默认: chain-cert.pem)
chainfile: ca-chain.pem
#其实上面的证书名字写什么都无所谓,这里写什么,在/u01/ca下的ca证书要跟这里写的一样
#############################################################################
# The registry section controls how the fabric-ca-server does two things:
# 1) authenticates enrollment requests which contain a username and password
# (also known as an enrollment ID and secret).
# 2) once authenticated, retrieves the identity's attribute names and
# values which the fabric-ca-server optionally puts into TCerts
# which it issues for transacting on the Hyperledger Fabric blockchain.
# These attributes are useful for making access control decisions in
# chaincode.
# There are two main configuration options:
# 1) The fabric-ca-server is the registry.
# This is true if "ldap.enabled" in the ldap section below is false.
# 2) An LDAP server is the registry, in which case the fabric-ca-server
# calls the LDAP server to perform these tasks.
# This is true if "ldap.enabled" in the ldap section below is true,
# which means this "registry" section is ignored.
#############################################################################
#当fabric-ca-server自身提供用户的注册管理时使用, 此情况下需要禁用LDAP功能, 否则fabric-ca-server将会把注册管理数据转发到LDAP进行查询
registry:
# Maximum number of times a password/secret can be reused for enrollment
# (default: -1, which means there is no limit)
# 允许同一个用户名和密码进行enrollment的最大次数, -1为无限制, 0为不支持登记
maxenrollments: -1
# Contains identity information which is used when LDAP is disabled
identities: # 注册的实体信息, 可以进行enroll. 只有当LDAP未启用时起作用
- name: ywhtest
pass: ywh123456
type: client
affiliation: ""
maxenrollments: -1
attrs:
hf.Registrar.Roles: "client,user,peer,validator,auditor"
hf.Registrar.DelegateRoles: "client,user,validator,auditor"
hf.Revoker: true
hf.IntermediateCA: true
#############################################################################
# Database section
# Supported types are: "sqlite3", "postgres", and "mysql".
# The datasource value depends on the type.
# If the type is "sqlite3", the datasource value is a file name to use
# as the database store. Since "sqlite3" is an embedded database, it
# may not be used if you want to run the fabric-ca-server in a cluster.
# To run the fabric-ca-server in a cluster, you must choose "postgres"
# or "mysql".
#############################################################################
#数据库支持SQLite3、MySQL、Postgres. 默认为SQLite3类型的本地数据库. 如果要配置集群, 则需要选用MySQL或Postgres后端数据库, 并在前端部署负载均衡器(如Nginx或HAProxy)
db:
type: postgres
datasource: host=172.31.145.194 port=5432 user=postgres password=postgres dbname=ca #host一定要写本机的内网地址,不要写127.0.0.1 sslmode=disable
tls:
enabled: false #是否启用TLS来连接到数据库
certfiles: #PEM格式的数据库服务器的TLS根证书, 可以指定多个, 用逗号隔开
- db-server-cert.pem
client:
certfile: db-client-cert.pem # PEM格式的客户端证书文件
keyfile: db-client-key.pem # PEM格式的客户端证书私钥文件
#############################################################################
# LDAP section
# If LDAP is enabled, the fabric-ca-server calls LDAP to:
# 1) authenticate enrollment ID and secret (i.e. username and password)
# for enrollment requests;
# 2) To retrieve identity attributes
#############################################################################
# 配置使用远端的LDAP来进行注册管理, 认证enrollment的用户和密码, 并获取用户属性信息. 此时, 服务端将按照指定的usrfilter从LDAP获取对应的用户, 利用其唯一识别名(distinguidhed name)和给定的密码进行验证.
# 当LDAP功能启用时, registry中的配置将被忽略
ldap:
# Enables or disables the LDAP client (default: false)
# If this is set to true, the "registry" section is ignored.
enabled: false # 是否启用LDAP, 默认不启用
# The URL of the LDAP server
url: ldap://:@:/
# Automatically generate non-default CAs. The names of these
# additional CAs are "ca1", "ca2", ... "caN", where "N" is
# This is particularly useful in a development environment to quickly set up
# multiple CAs.
#
# 2) --cafiles
# For each CA config file in the list, generate a separate signing CA. Each CA
# config file in this list MAY contain all of the same elements as are found in
# the server config file except port, debug, and tls sections.
#
# Examples:
# fabric-ca-server start -b admin:adminpw --cacount 2
#
# fabric-ca-server start -b admin:adminpw --cafiles ca/ca1/fabric-ca-server-config.yaml
# --cafiles ca/ca2/fabric-ca-server-config.yaml
#
#############################################################################
cacount:
cafiles:
#############################################################################
# Intermediate CA section
#
# The relationship between servers and CAs is as follows:
# 1) A single server process may contain or function as one or more CAs.
# This is configured by the "Multi CA section" above.
# 2) Each CA is either a root CA or an intermediate CA.
# 3) Each intermediate CA has a parent CA which is either a root CA or another intermediate CA.
#
# This section pertains to configuration of #2 and #3.
# If the "intermediate.parentserver.url" property is set,
# then this is an intermediate CA with the specified parent
# CA.
#
# parentserver section
# url - The URL of the parent server
# caname - Name of the CA to enroll within the server
#
# enrollment section used to enroll intermediate CA with parent CA
# profile - Name of the signing profile to use in issuing the certificate
# label - Label to use in HSM operations
#
# tls section for secure socket connection
# certfiles - PEM-encoded list of trusted root certificate files
# client:
# certfile - PEM-encoded certificate file for when client authentication
# is enabled on server
# keyfile - PEM-encoded key file for when client authentication
# is enabled on server
#############################################################################
intermediate:
parentserver:
url:
caname:
enrollment:
hosts:
profile:
label:
tls:
certfiles:
client:
certfile:
keyfile:
1.3.编写启动配置文件ca.yaml文件
[root@node6 ~]# mkdir -p /u01/chainConfig/configfile/ca
[root@node6 ~]# cd /u01/chainConfig/configfile/ca
[root@node6 ~]# vi ca.yaml
vi ca.yaml
version: '2'
services:
ca:
image: hyperledger/fabric-ca:x86_64-1.0.1
ports:
- "7054:7054"
command: sh -c "fabric-ca-server start -b admin:adminpw -d"
environment:
- FABRIC_CA_HOME=/etc/hyperledger/fabric-ca-server
volumes:
- /u01/ca:/etc/hyperledger/fabric-ca-server
1.4 在启动CA服务之前,我们要选择一个组织作为CA节点的根,也就说用哪个组织的根证书去发行证书,在前几篇博文中我们配置了五个org,我这里选择org1作为发行证书的根,把ca下的证书复制并重新命名,新的名字是根据fabric-ca-server-config.yaml文件中设置的名字一样。
[root@node6 ~]# cp /u01/chainConfig/crypto-config/peerOrganizations/ywhOrg1.example.com/ca/ca.ywhOrg1.example.com-cert /u01/ca/ca-cert.pem
[root@node6 ~]# cd /u01/chainConfig/crypto-config/peerOrganizations/ywhOrg2.example.com/ca/*_sk /u01/ca/ca-key.pem
#如果在fabric-ca-server-config.yaml文件中关闭了tls 这个命令就可以不用运行
[root@node6 ~]# mv /u01/chainConfig/crypto-config/peerOrganizations/ywhOrg1.example.com/users/User1\@ywhOrg1.example.com/tls/* /u01/ca1.5 在把配置文件和我们所需要的证书都完成后,启动CA服务就可以了
[root@node6 ~]# docker-compose -f /u01/chainConfig/configfile/ca/ca.yaml up -d2.申请用户
2.1 CA启动以后我们要使用CA服务来测试能否申请用户,并发行证书,使用脚本申请用户的时候可以先把tls通讯关闭,否则会报通讯的错误。
关于fabric-ca-client命令可以上网查询一下,这个命令在之前下载的平台特定二进制文件中没有,需要自己另外下载并放到bin目录下
下载地址:https://nexus.hyperledger.org/content/repositories/releases/org/hyperledger/fabric-ca/
我下载的是liunx-adm64的
[root@node6 ~]# mkdir -p /u01/users/
[root@node6 ~]# cd /u01/users/
[root@node6 ~]# vi createUser.sh
#!/bin/bash
USERNAME=test
CALOCATION=47.104.255.180:7054
#修改为当前CA的IP和端口
#
# enroll admin, after enroll admin, the msp files will store in the default msp directory.
# if the msp directory doesn't exist, we need to enroll an new pair of cert and prikey
#
#
enrollAdmin () {
echo enroll admin
fabric-ca-client enroll -u http://lianpai:lianpai888@${CALOCATION}
}
#
# create new user,
#
createUser () {
echo
echo
echo Createuser ${USERNAME}----#########################################################
fabric-ca-client register --id.name ${USERNAME} --id.type peer --id.affiliation lianpai.baochain \
--id.attrs hf.Revoker=true --id.attrs '"hf.Registrar.Roles=user,peer,client,validator,auditor"' \
--id.attrs hf.IntermediateCA=true --id.attrs '"hf.Registrar.DelegateRoles=user,peer,client,validator,auditor"' \
--id.secret ${USERNAME}pw
fabric-ca-client enroll --csr.hosts ${USERNAME} -u http://${USERNAME}:${USERNAME}pw@${CALOCATION} --mspdir /$(pwd)/${USERNAME}/msp/
}
start () {
export PATH=$PATH:/u01/chainConfig/bin
sleep 0.001
enrollAdmin
sleep 0.001
createUser
}
USERNAME=$1
echo --------------------------------------------------------
echo ----------create msp files for $USERNAME ----------------
echo --------------------------------------------------------
start
[root@node6 ~]# sh createUser.sh test #如果没有关闭tls的话 就会跟下面一样,有个错误
[root@node7 users]# sh createUser.sh test
--------------------------------------------------------
----------create msp files for test ----------------
--------------------------------------------------------
enroll admin
2018/09/30 15:46:41 [INFO] User provided config file: /root/.fabric-ca-client/fabric-ca-client-config.yaml
2018/09/30 15:46:41 [INFO] generating key: &{A:ecdsa S:256}
2018/09/30 15:46:41 [INFO] encoded CSR
Error: POST failure [Post http://172.31.145.195:7054/enroll: malformed HTTP response "\x15\x03\x01\x00\x02\x02\x16"]; not sending
POST http://172.31.145.195:7054/enroll
Authorization: Basic c3l0ZXN0OnN5MTIzNDU2
{"hosts":["node7"],"certificate_request":"-----BEGIN CERTIFICATE REQUEST-----\nMIIBOzCB4wIBADBeMQswCQYDVQQGEwJVUzEXMBUGA1UECBMOTm9ydGggQ2Fyb2xp\nbmExFDASBgNVBAoTC0h5cGVybGVkZ2VyMQ8wDQYDVQQLEwZGYWJyaWMxDzANBgNV\nBAMTBnN5dGVzdDBZMBMGByqGSM49AgEGCCqGSM49AwEHA0IABDW+oKepIc235APE\n/z1OxDtcpO+5ICywf9vAd+93/Jxe3fv7DpPDxtZB0OR62iuaZoiki9v3i887s4Hz\nye9WO/igIzAhBgkqhkiG9w0BCQ4xFDASMBAGA1UdEQQJMAeCBW5vZGU3MAoGCCqG\nSM49BAMCA0cAMEQCIH7A6bgBoqMYZGWDyV1GGCczWeeQuwCmbODfwaDDoOFqAiA1\nDA9NT741Po5PngxujcenjFiGqJ0GcAtbZttD4dupDQ==\n-----END CERTIFICATE REQUEST-----\n","profile":"","crl_override":"","label":"","CAName":""}
Createuser test----#########################################################
2018/09/30 15:46:41 [INFO] User provided config file: /root/.fabric-ca-client/fabric-ca-client-config.yaml
2018/09/30 15:46:41 [INFO] Configuration file location: /root/.fabric-ca-client/fabric-ca-client-config.yaml
Error: POST failure [Post http://172.31.145.195:7054/register: malformed HTTP response "\x15\x03\x01\x00\x02\x02\x16"]; not sending
POST http://172.31.145.195:7054/register
Authorization: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNZRENDQWdhZ0F3SUJBZ0lVVW9vQ1E1cVJKcHZ6MHBnZmN2UGNBMzdCSUdnd0NnWUlLb1pJemowRUF3SXcKZ1lFeEN6QUpCZ05WQkFZVEFsVlRNUk13RVFZRFZRUUlFd3BEWVd4cFptOXlibWxoTVJZd0ZBWURWUVFIRXcxVApZVzRnUm5KaGJtTnBjMk52TVNBd0hnWURWUVFLRXhkemVURnZjbWN1YzNsMFpYTjBZMmhoYVc0dVkyeDFZakVqCk1DRUdBMVVFQXhNYVkyRXVjM2t4YjNKbkxuTjVkR1Z6ZEdOb1lXbHVMbU5zZFdJd0hoY05NVGd3T1RFNE1EZ3oKT1RBd1doY05NVGt3T1RFNE1EZ3pPVEF3V2pCZU1Rc3dDUVlEVlFRR0V3SlZVekVYTUJVR0ExVUVDQk1PVG05eQpkR2dnUTJGeWIyeHBibUV4RkRBU0JnTlZCQW9UQzBoNWNHVnliR1ZrWjJWeU1ROHdEUVlEVlFRTEV3WkdZV0p5CmFXTXhEekFOQmdOVkJBTVRCbk41ZEdWemREQlpNQk1HQnlxR1NNNDlBZ0VHQ0NxR1NNNDlBd0VIQTBJQUJHM2EKTE1NU1hadjdLdWtFSWV1OW8rWVVNcGFQQkR6aWFKREhjUFVPL3daK2RSUEtaVngyakk0TFVHUEhMbndCUXBXdgp6eFNVWXB3bTZOdVpTWmk0cjBtamZqQjhNQTRHQTFVZER3RUIvd1FFQXdJSGdEQU1CZ05WSFJNQkFmOEVBakFBCk1CMEdBMVVkRGdRV0JCUkd6bG1lQ1NIMGdhSWtmM2w3VmhYb3RwRlN4VEFyQmdOVkhTTUVKREFpZ0NDRkxZTloKOUVIQjFlU3lRZnQxUUo3eDh1Vkc0dytIYkZab21KeWpNSmsyU0RBUUJnTlZIUkVFQ1RBSGdnVnViMlJsTnpBSwpCZ2dxaGtqT1BRUURBZ05JQURCRkFpRUE5ajBKMVQxVzk3TDNFTVJ1aUcyelpwWnhRWk1OUWlwUlZjbUdxM21jClBBVUNJQkNtYk9JRTdTNGR3a2Q5cTVQL1dwSm82ZHZTOHBZREp6Z0NmY1VUTUJqbgotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==.MEQCICKAJNRJCWfrViXKcWDGA5206751TSL9fISOOdg8rxO0AiBJaNjsF6HCYSSAMEp+e7qLR0zg2lRaIGky8ngkzFwWgQ==
{"id":"test","type":"peer","secret":"testpw","max_enrollments":-1,"affiliation":"sytest.sy123456","attrs":[{"name":"hf.Revoker","value":"true"},{"name":"hf.Registrar.Roles","value":"user,peer,client,validator,auditor"},{"name":"hf.IntermediateCA","value":"true"},{"name":"hf.Registrar.DelegateRoles","value":"user,peer,client,validator,auditor"}]}
2018/09/30 15:46:41 [INFO] User provided config file: /root/.fabric-ca-client/fabric-ca-client-config.yaml
2018/09/30 15:46:41 [INFO] generating key: &{A:ecdsa S:256}
2018/09/30 15:46:41 [INFO] encoded CSR
Error: POST failure [Post http://172.31.145.195:7054/enroll: malformed HTTP response "\x15\x03\x01\x00\x02\x02\x16"]; not sending
POST http://172.31.145.195:7054/enroll
Authorization: Basic dGVzdDp0ZXN0cHc=
{"hosts":["test"],"certificate_request":"-----BEGIN CERTIFICATE REQUEST-----\nMIIBOTCB4AIBADBcMQswCQYDVQQGEwJVUzEXMBUGA1UECBMOTm9ydGggQ2Fyb2xp\nbmExFDASBgNVBAoTC0h5cGVybGVkZ2VyMQ8wDQYDVQQLEwZGYWJyaWMxDTALBgNV\nBAMTBHRlc3QwWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAATkRbdsh6KRGFDjob2N\nn9vU1+HMWIIrUFJpYxVNMXu7ZJ8MaiOCgvSCRtR9tyQZ6WXpkk6pa5nWoMV1HrYy\nKqpDoCIwIAYJKoZIhvcNAQkOMRMwETAPBgNVHREECDAGggR0ZXN0MAoGCCqGSM49\nBAMCA0gAMEUCIQDkooKJY7vBP8lhXG7qPOFHRQS6cAcU6nB5vn3RjGN14gIgawX2\n0Hb5Tb8bTS21MHGE26t9tLz8+MIX5jFX2RsMnGo=\n-----END CERTIFICATE REQUEST-----\n","profile":"","crl_override":"","label":"","CAName":""}
[root@node7 users]# sh createUser.sh test1 #这是没有开启tls的,成功注册了一个用户 密码是testpw
--------------------------------------------------------
----------create msp files for test1 ----------------
--------------------------------------------------------
enroll admin
2018/09/30 15:49:59 [INFO] User provided config file: /root/.fabric-ca-client/fabric-ca-client-config.yaml
2018/09/30 15:49:59 [INFO] generating key: &{A:ecdsa S:256}
2018/09/30 15:49:59 [INFO] encoded CSR
2018/09/30 15:49:59 [INFO] Stored client certificate at /root/.fabric-ca-client/msp/signcerts/cert.pem
2018/09/30 15:49:59 [INFO] Stored CA root certificate at /root/.fabric-ca-client/msp/cacerts/172-31-145-195-7054.pem
Createuser test1----#########################################################
2018/09/30 15:49:59 [INFO] User provided config file: /root/.fabric-ca-client/fabric-ca-client-config.yaml
2018/09/30 15:49:59 [INFO] Configuration file location: /root/.fabric-ca-client/fabric-ca-client-config.yaml
Password: test1pw
2018/09/30 15:49:59 [INFO] User provided config file: /root/.fabric-ca-client/fabric-ca-client-config.yaml
2018/09/30 15:49:59 [INFO] generating key: &{A:ecdsa S:256}
2018/09/30 15:49:59 [INFO] encoded CSR
2018/09/30 15:49:59 [INFO] Stored client certificate at /u01/users/test1/msp/signcerts/cert.pem
2018/09/30 15:49:59 [INFO] Stored CA root certificate at /u01/users/test1/msp/cacerts/172-31-145-195-7054.pem
相应的在/u01/users文件夹中也出现了test和test1两个文件夹,一个失败的和一个成功的,可以对比一下两个文件夹下的东西。
上面部署的是CA服务,tls的跟上面唯一区别就是证书用的不同,一个用的是ca文件夹下的,一个是用的tlsca文件夹下的
走到这里,CA服务的申请用户基本完成了。