- Redis教程(二十一):Redis怎么保证缓存一致性
ThatMonth
缓存redis数据库
传送门:Redis教程汇总篇,让你从入门到精通Redis的缓存一致性Redis的缓存一致性是指在使用Redis作为缓存层时,保证缓存中的数据与数据库中的数据保持一致的状态。在分布式系统中,数据一致性是一个重要的问题,因为可能存在多个客户端同时读写同一数据,或者数据在不同节点间需要同步更新。在涉及缓存的场景中,保持缓存一致性面临以下挑战:数据更新:当数据库中的数据被修改后,相关联的缓存数据需要被相应
- V2X通信协议测试
软件测试车载测试协议测试
引言随着智能网联汽车的发展,V2X(Vehicle-to-Everything)通信技术成为提升道路安全和交通效率的关键。V2X包括车与车(V2V)、车与基础设施(V2I)、车与行人(V2P)以及车与网络(V2N)的通信。为了确保V2X的可靠性和安全性,通信协议的测试至关重要。本文将介绍V2X通信协议的关键技术、测试方法及挑战。一、V2X通信协议概述目前V2X通信主要基于两种技术:DSRC(Ded
- 智能推送系统的敏感词过滤功能:合规防线与用户体验的守护者
大数据
在信息爆炸与监管趋严的双重挑战下,APP企业正面临前所未有的内容安全压力。一次不当推送可能引发用户投诉、应用下架甚至法律诉讼。MobPush智能推送系统的敏感词过滤功能,通过技术手段在推送内容发布前自动拦截违规信息,已成为企业规避风险、维护品牌声誉的核心工具。数据显示,引入该功能后,APP的违规内容投诉率平均下降75%,人工审核成本减少60%。本文将从技术逻辑、业务价值及典型案例三个维度,解析这一
- 智能推送系统的敏感词过滤功能:合规防线与用户体验的守护者
大数据
在信息爆炸与监管趋严的双重挑战下,APP企业正面临前所未有的内容安全压力。一次不当推送可能引发用户投诉、应用下架甚至法律诉讼。MobPush智能推送系统的敏感词过滤功能,通过技术手段在推送内容发布前自动拦截违规信息,已成为企业规避风险、维护品牌声誉的核心工具。数据显示,引入该功能后,APP的违规内容投诉率平均下降75%,人工审核成本减少60%。本文将从技术逻辑、业务价值及典型案例三个维度,解析这一
- 从云端到私有:智慧任务管理工具的私有化转型之路
项目管理软件
智慧任务管理工具私有化是指将智慧任务管理工具部署在组织内部的私有服务器或云环境中,以确保数据的安全性、隐私性和完全控制权。以下是对智慧任务管理工具私有化的详细解析:一、私有化的优势●数据安全:私有化部署确保所有数据存储在组织内部的服务器或私有云中,避免数据泄露或被第三方访问,特别适合处理敏感信息或需要遵守数据保护法规(如GDPR、HIPAA等)的组织。●定制化开发:组织可以完全控制系统的配置、更新
- 构建专属工作流:私有化部署下的数据安全与效率双赢
项目管理软件
工作流管理软件私有化是指将工作流管理软件部署在组织内部的私有服务器或专有云环境中,以确保数据的安全性、隐私性和组织的完全控制权。以下是对工作流管理软件私有化的详细分析:一、私有化的优势数据安全:○私有化部署确保所有数据存储在组织内部的服务器或私有云中,避免了数据泄露或被第三方访问的风险。○特别适合处理敏感信息或需要遵守数据保护法规(如GDPR、HIPAA等)的组织。定制化开发:○组织可以完全控制系
- redisCluster集群相关查询结果详解
ghostp
redisredis
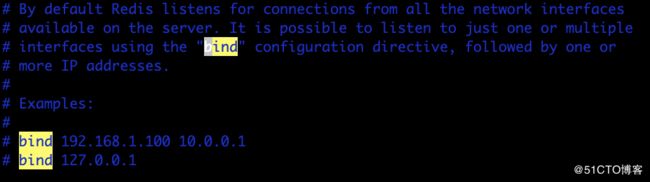
redisCluster集群相关查询结果详解进入redis进群查看集群信息CLUSTERINFO命令CLUSTERNODES命令info命令infoCommandstats命令查询服务器相关key的大小单个key查询某些前缀key批量查询进入redis进群在安装redis的机器上,找到安装目录的bin文件夹,使用以下命令来进入集群:[root@localhostbin]#./redis-cli-c
- 什么是通配符证书
ssl证书数字证书
在网络安全领域,SSL证书是保障数据传输安全的重要工具,而通配符证书是其中一种特殊类型的证书,下面我们就来详细了解一下它。一、通配符证书的定义通配符证书是一种SSL/TLS证书,其特点在于可以保护一个主域名及其所有的子域名。简单来说,当你拥有一个通配符证书时,它能够为诸如主域名下的等任意子域名提供安全加密保护。证书中使用通配符“*”来表示匹配该主域名下的所有子域名,这使得它在管理多个子域名的安全时
- redis架构系列——Cluster集群模式详解
庄隐
#组件redis架构
设计的主要特点和基本原理Redis集群目标高性能和线性可扩展性,最多可达1000个节点。没有代理,使用异步复制,并且不对值执行合并操作。可接受的写入安全程度:系统尝试(尽最大努力)保留来自与大多数主节点连接的客户端的所有写入。通常,有一些小窗口可能会丢失确认的写入。当客户端位于少数分区中时,丢失确认写入的窗口会更大。可用性:Redis集群能够在大多数主节点可访问的分区中继续存在,并且每个主节点至少
- 七个合法学习黑客技术的平台,让你从萌新成为大佬
黑客白帽子黑爷
学习php开发语言web安全网络
1、HackThisSite提供在线IRC聊天和论坛,让用户交流更加方便。网站涵盖多种主题,包括密码破解、网络侦察、漏洞利用、社会工程学等。非常适用于个人提高网络安全技能2、HackaDay涵盖多个领域,包括黑客技术、科技、工程和DIY等内容,站内提供大量有趣的文章、视频、教程和新闻,帮助用户掌握黑客技术和DIY精神。3、OffensiveSecurity一个专门提供网络安全培训和认证的公司,课程
- 【2025年】全国CTF夺旗赛-从零基础入门到竞赛,看这一篇就稳了!
白帽黑客鹏哥
web安全CTF网络安全大赛pythonLinux
基于入门网络安全/黑客打造的:黑客&网络安全入门&进阶学习资源包目录一、CTF简介二、CTF竞赛模式三、CTF各大题型简介四、CTF学习路线4.1、初期1、html+css+js(2-3天)2、apache+php(4-5天)3、mysql(2-3天)4、python(2-3天)5、burpsuite(1-2天)4.2、中期1、SQL注入(7-8天)2、文件上传(7-8天)3、其他漏洞(14-15
- Redis Cluster集群详解
高冷小伙
redis数据库缓存
数据分片(Sharding)哈希槽(HashSlot)机制:集群将数据划分为16384个哈希槽,每个键通过CRC16(key)%16384计算归属的槽。槽分配给多个主节点,每个节点负责一部分槽(例如:3节点集群中,每个节点可能管理约5461个槽)。动态槽分配:节点增减时,槽可动态迁移,支持在线扩容/缩容(如CLUSTERADDSLOTS命令)。跨槽操作限制:事务、Lua脚本需确保所有键在同一槽(可
- dynamic_cast和static_cast和const_cast
zjkzjk7711
服务器linux运维
dynamic_cast在C++中的作用dynamic_cast是C++运行时类型转换(RTTI,Run-TimeTypeIdentification)的一部分,主要用于:安全的多态类型转换检查类型的有效性向下转换(Downcasting)跨类层次的指针或引用转换它只能用于带有虚函数的类,否则dynamic_cast将无法工作。1.dynamic_cast的作用1.1向下转换(Downcastin
- 后端开发技巧:提升代码质量与系统性能
wenbin_java
javaspringbootmavenmybatis
引言后端开发是构建高效、稳定应用的核心环节。无论是处理复杂的业务逻辑,还是优化系统性能,后端开发者都需要掌握一系列技巧和最佳实践。本文将分享一些实用的后端开发技巧,帮助你提升代码质量、优化系统性能并确保应用的安全性。1.提升代码质量的技巧1.1遵循编码规范统一风格:使用工具(如Checkstyle、ESLint)确保代码风格一致。命名规范:变量、函数、类名应具有描述性,避免使用缩写。1.2模块化与
- 【面试实战】Spring基础、IoC、AOP、MVC、Mybatis、Spring Boot
Sivan_Xin
技术实战专栏(已上云)面试mvcspring
version:1.0文章目录SpringSpring基础/IoC♂️面试官:举例Spring的模块?♂️面试官:Spring、SpringMVC、SpringBoot关系?♂️面试官:说说对SpringIoC的了解?♂️面试官:什么是SpringBean?♂️面试官:Bean的作用域?♂️面试官:Bean的生命周期?♂️面试官:单例Bean的线程安全问题了解吗?♂️面试官:@Co
- 自动化脚本在Xshell中的应用
这多冒昧啊
运维githubgit运维自动化自动化脚本脚本
Xshell是一款功能强大的终端模拟软件,主要用于远程连接和管理服务器。它支持多种协议,包括SSH、Telnet、SFTP等,使用户能够通过命令行界面对远程服务器进行操作。Xshell提供了丰富的功能和特点,使其成为系统管理员、开发人员和网络工程师的得力工具。目录一、概述二、自动化脚本在Xshell中的应用案例案例一:自动化系统更新与维护案例二:自动化备份与恢复案例三:自动化网络安全检查三、总结一
- 解释SQL和NoSQL数据库的区别,各自的适用场景是什么?
破碎的天堂鸟
学习教程nosql数据库
SQL与NoSQL数据库的深度对比及适用场景分析一、核心定义与数据模型差异1:SQL数据库结构化数据模型:基于关系型模型,数据以表格(行和列)形式存储,表之间通过外键建立关联。例如,客户表与订单表通过客户ID关联,形成严格的逻辑结构。预定义模式(Schema):需提前定义表结构(字段类型、主键、外键等),修改结构需通过ALTER等命令,灵活性较低。标准化查询语言:使用SQL(StructuredQ
- 网络安全工具 AWVS 与 Nmap:原理、使用及代码示例
阿贾克斯的黎明
网络安全安全web安全网络
目录网络安全工具AWVS与Nmap:原理、使用及代码示例AWVS:Web漏洞扫描的利器1.工具概述2.工作原理3.使用方法4.代码示例(Python调用AWVSAPI进行扫描)Nmap:网络探测与端口扫描的神器1.工具概述2.工作原理3.使用方法4.代码示例(Python调用Nmap进行扫描)总结在网络安全领域,AWVS(AcunetixWebVulnerabilityScanner)和Nmap是
- 深入剖析 Java 反序列化:FASTjson 漏洞与 Shiro 漏洞
阿贾克斯的黎明
网络安全phpweb安全开发语言
目录深入剖析Java反序列化:FASTjson漏洞与Shiro漏洞引言Java反序列化原理示例代码FASTjson漏洞分析漏洞成因示例代码防护措施Shiro漏洞分析漏洞成因示例代码(模拟攻击场景)防护措施总结引言在Java应用开发中,反序列化是一项重要的技术,但同时也隐藏着巨大的安全风险。FASTjson和Shiro作为Java开发中常用的工具和框架,其反序列化漏洞曾引发了广泛关注。本文将深入探讨
- 第14天:C++异常处理实战指南 - 构建安全的文件解析系统
JuicyActiveGilbert
C++教程c++安全开发语言
第14天:C++异常处理实战指南-构建安全的文件解析系统一、今日学习目标掌握C++异常处理的核心语法与流程️理解RAII在资源管理中的关键作用创建自定义文件解析异常体系实现安全的文件解析器原型二、C++异常处理核心机制1.异常处理基础语法#include#include#includevoidparseConfiguration(conststd::string&path){std::ifstre
- Composer如何通过GitHub Personal Access Token安装私有包:完整教程
lihuang319
composergithubphp
使用Composer安全管理您的PHP私有依赖包一、前言在PHP开发中,我们经常需要将内部工具包托管为私有仓库。传统的账号密码验证方式存在安全隐患,而GitHubPersonalAccessToken(PAT)提供了一种更安全的鉴权方案。本文将通过4个核心步骤+3个避坑指南,手把手教您在Composer中优雅地使用PAT安装私有包。二、为什么要用PAT?安全性:细粒度权限控制(可设置过期时间/单仓
- redis集群迅速搭建(个人学习和测试用)
yinhezhanshen
redis学习java
笔者使用ubuntu操作系统下载redis地址:Indexof/releases/,选择最新的版本下载。解压后进入目录,直接make就可以编译。编译成功后在src目录下会生成redis-server和redis-cli可执行文件。进入redis目录下的utils/create-cluster目录,执行./create-clusterstart,快速启动6个实例zy@zy-VirtualBox:~/
- 硬盘数据恢复操作全攻略
AR新视野
本文还有配套的精品资源,点击获取简介:硬盘数据恢复是一项需要精确操作的技术活动,主要针对丢失、误删或损坏的文件进行恢复。本教程通过深入探讨数据恢复的基础知识和步骤,指导用户如何安全有效地执行数据恢复。教程强调了在硬盘故障发生时的正确处理方式,包括避免在受损硬盘上直接操作、使用保护卡或克隆技术复制数据,以及选择合适的数据恢复软件等。教程还提供了数据恢复的基本步骤,并告诫用户在数据非常关键或硬件问题复
- 网络安全加密python代码
黑客Ash
web安全安全
点击文末小卡片,免费获取网络安全全套资料,资料在手,涨薪更快网络信息安全中遇到的各种攻击是防不胜防的,采取适当的防护措施就能有效地保护网络信息的安全,包括防火墙、入侵检测系统、漏洞扫描技术以及加密技术等多种防护措施。而信息安全的本质就是要保护信息本身和信息系统在存储、传输中的完整性和保密性,保障不被攻击和篡改,上述的主动攻击、被动攻击和病毒袭击都会造成信息的破坏和泄密,我们以信息安全中的基础理论出
- 网络安全尹毅 《网络安全》
黑客Ash
web安全网络安全
点击文末小卡片,免费获取网络安全全套资料,资料在手,涨薪更快一网络安全基本概念1.网络安全定义安全在字典中的定义是为了防范间谍活动或蓄意破坏、犯罪、攻击而采取的措施。网络安全就是为了防范计算机网络硬件、软件、数据被偶然或蓄意破坏、篡改、窃听、假冒、泄露、非法访问以及保护网络系统持续有效工作的措施总和。网络安全保护范围:密码安全、计算机系统安全、网络安全、信息安全。2.网络安全目标可靠性(relia
- 一个基于 React + SpringBoot 的在线多功能问卷系统(附源码)
程序员-李旭亮
Java项目源码react.jsspringboot前端
简介:一个基于React+SpringBoot的在线多功能问卷系统前端技术栈:React、React-Router、Webpack、Antd、Zustand、Echarts、DnDKit后端技术栈:SpringBoot、MySQL、MyBatisPlus、Redis项目源码下载链接:https://pan.quark.cn/s/2e32786e0c61部分页面静态预览:主要前端业务需求与技术突破:
- b s架构 网络安全 网络安全架构分析
黑客Ash
web安全架构网络
目录文章目录目录网络安全逻辑架构微分段(Micro-segmentation)防火墙即服务(FirewallasaService,FWaaS)安全网络网关(Securewebgateway)净化域名系统(SanitizedDomainNameSystem,S-DNS)网络安全策略管理(NetworkSecurityPolicyManagement,NSPM)网络防火墙(Networkfirewal
- IoT安全软件:Tenable二次开发_TenableIoT数据处理与分析
chenlz2007
物联网物联网自动化运维网络协议网络
TenableIoT数据处理与分析在上一节中,我们介绍了如何使用TenableIoT进行资产发现和漏洞扫描。接下来,我们将深入探讨如何处理和分析TenableIoT生成的数据,以便更好地理解网络中的安全态势,并采取适当的措施来保护我们的IoT设备。1.数据导出与格式转换在处理TenableIoT数据之前,首先需要将数据从TenableIoT平台导出,并转换为适合进一步分析的格式。TenableIo
- 什么是SSL?什么是TLS?SSL与TLS 区别
HOLD ON!
计算机网络
什么是SSL?什么是TLS?SSL与TLS区别chunqianpo7385一、什么是ssl?什么是tls?SSL:(SecureSocketLayer,安全套接字层),位于可靠的面向连接的网络层协议和应用层协议之间的一种协议层。SSL通过互相认证、使用数字签名确保完整性、使用加密确保私密性,以实现客户端和服务器之间的安全通讯。SSL协议可分为两层:SSL记录协议(SSLRecordProtocol
- 一个方法被多个线程同时调用,确保同样参数的调用只能有一个线程执行,不同参数的调用则可以多个线程同时执行
carcarrot
.Netlock同步锁相同参数同步锁
我们知道通过lock一个固定静态object给代码段加同步锁,可以让多个线程的同时调用以同步执行,因此可以利用字典来给不同参数分配不同的静态对象,方法中不同的参数调用锁住各自不同的静态对象即可实现不同参数不加锁,相同参数才加锁的需求,而多线程更新操作的字典需要用到线程安全的ConcurrentDictionary防止争用,因此这里的静态加锁对象字典类型为ConcurrentDictionary。比
- Spring的注解积累
yijiesuifeng
spring注解
用注解来向Spring容器注册Bean。
需要在applicationContext.xml中注册:
<context:component-scan base-package=”pagkage1[,pagkage2,…,pagkageN]”/>。
如:在base-package指明一个包
<context:component-sc
- 传感器
百合不是茶
android传感器
android传感器的作用主要就是来获取数据,根据得到的数据来触发某种事件
下面就以重力传感器为例;
1,在onCreate中获得传感器服务
private SensorManager sm;// 获得系统的服务
private Sensor sensor;// 创建传感器实例
@Override
protected void
- [光磁与探测]金吕玉衣的意义
comsci
这是一个古代人的秘密:现在告诉大家
信不信由你们:
穿上金律玉衣的人,如果处于灵魂出窍的状态,可以飞到宇宙中去看星星
这就是为什么古代
- 精简的反序打印某个数
沐刃青蛟
打印
以前看到一些让求反序打印某个数的程序。
比如:输入123,输出321。
记得以前是告诉你是几位数的,当时就抓耳挠腮,完全没有思路。
似乎最后是用到%和/方法解决的。
而今突然想到一个简短的方法,就可以实现任意位数的反序打印(但是如果是首位数或者尾位数为0时就没有打印出来了)
代码如下:
long num, num1=0;
- PHP:6种方法获取文件的扩展名
IT独行者
PHP扩展名
PHP:6种方法获取文件的扩展名
1、字符串查找和截取的方法
1
$extension
=
substr
(
strrchr
(
$file
,
'.'
), 1);
2、字符串查找和截取的方法二
1
$extension
=
substr
- 面试111
文强chu
面试
1事务隔离级别有那些 ,事务特性是什么(问到一次)
2 spring aop 如何管理事务的,如何实现的。动态代理如何实现,jdk怎么实现动态代理的,ioc是怎么实现的,spring是单例还是多例,有那些初始化bean的方式,各有什么区别(经常问)
3 struts默认提供了那些拦截器 (一次)
4 过滤器和拦截器的区别 (频率也挺高)
5 final,finally final
- XML的四种解析方式
小桔子
domjdomdom4jsax
在平时工作中,难免会遇到把 XML 作为数据存储格式。面对目前种类繁多的解决方案,哪个最适合我们呢?在这篇文章中,我对这四种主流方案做一个不完全评测,仅仅针对遍历 XML 这块来测试,因为遍历 XML 是工作中使用最多的(至少我认为)。 预 备 测试环境: AMD 毒龙1.4G OC 1.5G、256M DDR333、Windows2000 Server
- wordpress中常见的操作
aichenglong
中文注册wordpress移除菜单
1 wordpress中使用中文名注册解决办法
1)使用插件
2)修改wp源代码
进入到wp-include/formatting.php文件中找到
function sanitize_user( $username, $strict = false
- 小飞飞学管理-1
alafqq
管理
项目管理的下午题,其实就在提出问题(挑刺),分析问题,解决问题。
今天我随意看下10年上半年的第一题。主要就是项目经理的提拨和培养。
结合我自己经历写下心得
对于公司选拔和培养项目经理的制度有什么毛病呢?
1,公司考察,选拔项目经理,只关注技术能力,而很少或没有关注管理方面的经验,能力。
2,公司对项目经理缺乏必要的项目管理知识和技能方面的培训。
3,公司对项目经理的工作缺乏进行指
- IO输入输出部分探讨
百合不是茶
IO
//文件处理 在处理文件输入输出时要引入java.IO这个包;
/*
1,运用File类对文件目录和属性进行操作
2,理解流,理解输入输出流的概念
3,使用字节/符流对文件进行读/写操作
4,了解标准的I/O
5,了解对象序列化
*/
//1,运用File类对文件目录和属性进行操作
//在工程中线创建一个text.txt
- getElementById的用法
bijian1013
element
getElementById是通过Id来设置/返回HTML标签的属性及调用其事件与方法。用这个方法基本上可以控制页面所有标签,条件很简单,就是给每个标签分配一个ID号。
返回具有指定ID属性值的第一个对象的一个引用。
语法:
&n
- 励志经典语录
bijian1013
励志人生
经典语录1:
哈佛有一个著名的理论:人的差别在于业余时间,而一个人的命运决定于晚上8点到10点之间。每晚抽出2个小时的时间用来阅读、进修、思考或参加有意的演讲、讨论,你会发现,你的人生正在发生改变,坚持数年之后,成功会向你招手。不要每天抱着QQ/MSN/游戏/电影/肥皂剧……奋斗到12点都舍不得休息,看就看一些励志的影视或者文章,不要当作消遣;学会思考人生,学会感悟人生
- [MongoDB学习笔记三]MongoDB分片
bit1129
mongodb
MongoDB的副本集(Replica Set)一方面解决了数据的备份和数据的可靠性问题,另一方面也提升了数据的读写性能。MongoDB分片(Sharding)则解决了数据的扩容问题,MongoDB作为云计算时代的分布式数据库,大容量数据存储,高效并发的数据存取,自动容错等是MongoDB的关键指标。
本篇介绍MongoDB的切片(Sharding)
1.何时需要分片
&nbs
- 【Spark八十三】BlockManager在Spark中的使用场景
bit1129
manager
1. Broadcast变量的存储,在HttpBroadcast类中可以知道
2. RDD通过CacheManager存储RDD中的数据,CacheManager也是通过BlockManager进行存储的
3. ShuffleMapTask得到的结果数据,是通过FileShuffleBlockManager进行管理的,而FileShuffleBlockManager最终也是使用BlockMan
- yum方式部署zabbix
ronin47
yum方式部署zabbix
安装网络yum库#rpm -ivh http://repo.zabbix.com/zabbix/2.4/rhel/6/x86_64/zabbix-release-2.4-1.el6.noarch.rpm 通过yum装mysql和zabbix调用的插件还有agent代理#yum install zabbix-server-mysql zabbix-web-mysql mysql-
- Hibernate4和MySQL5.5自动创建表失败问题解决方法
byalias
J2EEHibernate4
今天初学Hibernate4,了解了使用Hibernate的过程。大体分为4个步骤:
①创建hibernate.cfg.xml文件
②创建持久化对象
③创建*.hbm.xml映射文件
④编写hibernate相应代码
在第四步中,进行了单元测试,测试预期结果是hibernate自动帮助在数据库中创建数据表,结果JUnit单元测试没有问题,在控制台打印了创建数据表的SQL语句,但在数据库中
- Netty源码学习-FrameDecoder
bylijinnan
javanetty
Netty 3.x的user guide里FrameDecoder的例子,有几个疑问:
1.文档说:FrameDecoder calls decode method with an internally maintained cumulative buffer whenever new data is received.
为什么每次有新数据到达时,都会调用decode方法?
2.Dec
- SQL行列转换方法
chicony
行列转换
create table tb(终端名称 varchar(10) , CEI分值 varchar(10) , 终端数量 int)
insert into tb values('三星' , '0-5' , 74)
insert into tb values('三星' , '10-15' , 83)
insert into tb values('苹果' , '0-5' , 93)
- 中文编码测试
ctrain
编码
循环打印转换编码
String[] codes = {
"iso-8859-1",
"utf-8",
"gbk",
"unicode"
};
for (int i = 0; i < codes.length; i++) {
for (int j
- hive 客户端查询报堆内存溢出解决方法
daizj
hive堆内存溢出
hive> select * from t_test where ds=20150323 limit 2;
OK
Exception in thread "main" java.lang.OutOfMemoryError: Java heap space
问题原因: hive堆内存默认为256M
这个问题的解决方法为:
修改/us
- 人有多大懒,才有多大闲 (评论『卓有成效的程序员』)
dcj3sjt126com
程序员
卓有成效的程序员给我的震撼很大,程序员作为特殊的群体,有的人可以这么懒, 懒到事情都交给机器去做 ,而有的人又可以那么勤奋,每天都孜孜不倦得做着重复单调的工作。
在看这本书之前,我属于勤奋的人,而看完这本书以后,我要努力变成懒惰的人。
不要在去庞大的开始菜单里面一项一项搜索自己的应用程序,也不要在自己的桌面上放置眼花缭乱的快捷图标
- Eclipse简单有用的配置
dcj3sjt126com
eclipse
1、显示行号 Window -- Prefences -- General -- Editors -- Text Editors -- show line numbers
2、代码提示字符 Window ->Perferences,并依次展开 Java -> Editor -> Content Assist,最下面一栏 auto-Activation
- 在tomcat上面安装solr4.8.0全过程
eksliang
Solrsolr4.0后的版本安装solr4.8.0安装
转载请出自出处:
http://eksliang.iteye.com/blog/2096478
首先solr是一个基于java的web的应用,所以安装solr之前必须先安装JDK和tomcat,我这里就先省略安装tomcat和jdk了
第一步:当然是下载去官网上下载最新的solr版本,下载地址
- Android APP通用型拒绝服务、漏洞分析报告
gg163
漏洞androidAPP分析
点评:记得曾经有段时间很多SRC平台被刷了大量APP本地拒绝服务漏洞,移动安全团队爱内测(ineice.com)发现了一个安卓客户端的通用型拒绝服务漏洞,来看看他们的详细分析吧。
0xr0ot和Xbalien交流所有可能导致应用拒绝服务的异常类型时,发现了一处通用的本地拒绝服务漏洞。该通用型本地拒绝服务可以造成大面积的app拒绝服务。
针对序列化对象而出现的拒绝服务主要
- HoverTree项目已经实现分层
hvt
编程.netWebC#ASP.ENT
HoverTree项目已经初步实现分层,源代码已经上传到 http://hovertree.codeplex.com请到SOURCE CODE查看。在本地用SQL Server 2008 数据库测试成功。数据库和表请参考:http://keleyi.com/a/bjae/ue6stb42.htmHoverTree是一个ASP.NET 开源项目,希望对你学习ASP.NET或者C#语言有帮助,如果你对
- Google Maps API v3: Remove Markers 移除标记
天梯梦
google maps api
Simply do the following:
I. Declare a global variable:
var markersArray = [];
II. Define a function:
function clearOverlays() {
for (var i = 0; i < markersArray.length; i++ )
- jQuery选择器总结
lq38366
jquery选择器
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40
- 基础数据结构和算法六:Quick sort
sunwinner
AlgorithmQuicksort
Quick sort is probably used more widely than any other. It is popular because it is not difficult to implement, works well for a variety of different kinds of input data, and is substantially faster t
- 如何让Flash不遮挡HTML div元素的技巧_HTML/Xhtml_网页制作
刘星宇
htmlWeb
今天在写一个flash广告代码的时候,因为flash自带的链接,容易被当成弹出广告,所以做了一个div层放到flash上面,这样链接都是a触发的不会被拦截,但发现flash一直处于div层上面,原来flash需要加个参数才可以。
让flash置于DIV层之下的方法,让flash不挡住飘浮层或下拉菜单,让Flash不档住浮动对象或层的关键参数:wmode=opaque。
方法如下:
- Mybatis实用Mapper SQL汇总示例
wdmcygah
sqlmysqlmybatis实用
Mybatis作为一个非常好用的持久层框架,相关资料真的是少得可怜,所幸的是官方文档还算详细。本博文主要列举一些个人感觉比较常用的场景及相应的Mapper SQL写法,希望能够对大家有所帮助。
不少持久层框架对动态SQL的支持不足,在SQL需要动态拼接时非常苦恼,而Mybatis很好地解决了这个问题,算是框架的一大亮点。对于常见的场景,例如:批量插入/更新/删除,模糊查询,多条件查询,联表查询,