Jarvis OJ (逆向):DD - Hello
文件类型 Mach-O:
核心函数:
int sub_100000CE0()
{
int result; // eax
signed int v1; // [rsp+1Ch] [rbp-14h]
int v2; // [rsp+24h] [rbp-Ch]
v2 = ((unsigned __int64)((char *)start - (char *)sub_100000C90) >> 2) ^ byte_100001040[0];// 地址相减
result = sub_100000DE0();
if ( !(result & 1) )
{
v1 = 0;
while ( v1 < 55 )
{
byte_100001040[v1] -= 2;
byte_100001040[v1] ^= v2;
++v1;
++v2;
}
result = printf("\nFinal output is %s\n", &byte_100001040[1]);
}
return result;
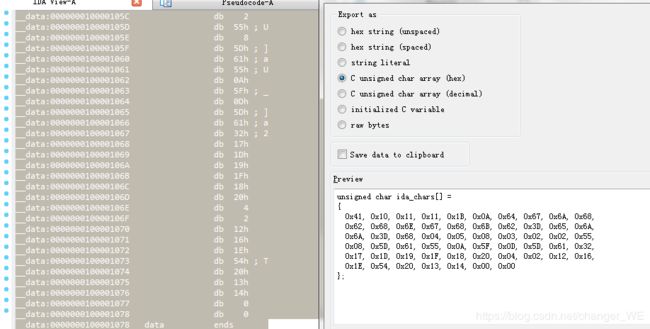
}获取byte_100001040数值:
写个脚本:
start = 0x0000000100000CB0
sub_100000C90 = 0x0000000100000C90
v2 = (start - sub_100000C90)>>2 ^ 0x41
flag = ""
print(v2)
byte_100001040 = [
0x41, 0x10, 0x11, 0x11, 0x1B, 0x0A, 0x64, 0x67, 0x6A, 0x68,
0x62, 0x68, 0x6E, 0x67, 0x68, 0x6B, 0x62, 0x3D, 0x65, 0x6A,
0x6A, 0x3D, 0x68, 0x04, 0x05, 0x08, 0x03, 0x02, 0x02, 0x55,
0x08, 0x5D, 0x61, 0x55, 0x0A, 0x5F, 0x0D, 0x5D, 0x61, 0x32,
0x17, 0x1D, 0x19, 0x1F, 0x18, 0x20, 0x04, 0x02, 0x12, 0x16,
0x1E, 0x54, 0x20, 0x13, 0x14, 0x00, 0x00
]
for i in range(0,55,1):
byte_100001040[i] -= 2
byte_100001040[i] ^= v2
v2 += 1
flag += chr(byte_100001040[i])
print(flag)flag要去掉前面的 'v':
Mach-O
https://www.jianshu.com/p/bcc7ba20f900