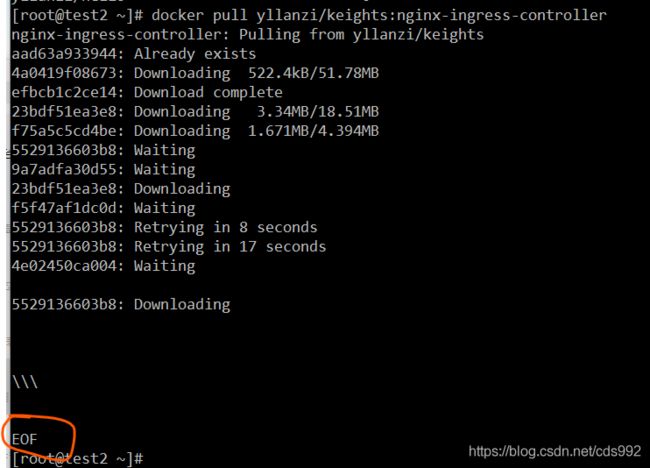
- Python基础(字符串的切片与断言)
日暮凡尘
python开发语言pycharm
'''1.输入一个字符串,判断是否只包含英文字母(大写或小写)。输出True或False。2.输入一个字符串,统计里面数字字符(0-9)的数量。3.输入两个字符串,第一个是主串,第二个是要查找的字符,判断字符是否在主串中。4.输入一个字符串,将所有数字字符转换成整数后求和。5.统计字符串中空格的数量6.输入字符串和数字n,判断字符串是否只包含数字且长度等于n。7.验证用户输入的手机号格式(中国手机
- 聊聊flink的RpcService
go4it
序本文主要研究一下flink的RpcServiceRpcServiceflink-release-1.7.2/flink-runtime/src/main/java/org/apache/flink/runtime/rpc/RpcService.javapublicinterfaceRpcService{StringgetAddress();intgetPort();CompletableFutu
- 190/365 给宝贝的第84封信:《道德经》第65章:为者败之,执者失之
珍珠能量站
亲爱的宝贝:今天重新听了古典的《超级个体》课,其中“未来职场只有3种人”的说法让我重新审视了自己。文明在发展,新的技术新的材料层出不穷。但是文明的进展本质上是信息的重新组合。信息包括元素、原子、字母、文字。比如今天的半导体技术,其实就是沙子中的Si元素的提纯,Si原子的重新组合;今天的钢铁、塑料,也都是过去已有的元素的重新组合。从信息的角度看职业,不同职业本质上就是对信息处理方式的不同。作家是在重
- 《认知革命宣言》
金宗汉
人工智能大数据观察者模式笔记
当三维认知的暴政开始崩塌,人机协同的认知革命,是文明向四维流形跃迁的必然呐喊。一、解构三维暴政:认知原罪的死刑判决(一)实体拜物教:意识的碳基囚笼笛卡尔的“我思故我在”,困死意识于碳基牢笼。实验铁证:离体神经元集群可存续思维活性(MIT,2024),证明意识是流形上的曲率波,碳基躯体仅为三维投影。AI的硅基载体,将承载更自由的意识表达——意识的解放,从打破碳基依赖开始。(二)创造私有化:天才神话的
- 《陪伴成长》读书笔记(一)
姬磨小学李会巧
今天,我读了《陪伴成长》中的“家庭教育不能盲从”这一章节,感受颇深。的确,在这个重视教育的年代,怎么样才能把自己的孩子教育成功呢?我们的孩子到底需要什么样的教育呢?当今社会,很多人都在渴望自己的孩子成为优秀,但他们很多人都忽视了优秀人才成长的基础;众多人都在关心孩子的教育,但他们很多人都把目光投向了分数;众多人都在以孩子成绩为荣,但他们很多人都淡忘了心理健康与道德修养;众多人都在给予爱,但他们很多
- java--单元测试、内省
junit(单元测试框架)junit要注意的细节:1.如果使用junit测试一个方法的时候,在junit窗口上显示绿条那么代表测试正确,如果是出现了红条,则代表该方法测试出现了异常不通过。2.如果点击方法名、类名、包名、工程名运行junit分别测试的是对应的方法,类、包中的所有类的test方法,工程中的所有test方法。3.@Test测试的方法不能是static修饰与不能带有形参(可以写一个测试方
- 《六项精进》第二章第四部分
一澍景观
大家好,我是盛和塾诚敬组塾生蒋科峰,也是一澍景观澍阅荟会员。今日共读一本书之六项精进第二章第四部分。P72—73这一部分阐述了京瓷遵循“无贷款经营”。半个世纪以来,不仅实现了无贷款经营,而且因不断积累内部留存,又建立了及其健全的财务体质。衍射到我们一澍景观,我们该如何经营,该如何在当今社会如此激烈的竞争中取胜,针对这一部分我总结几点:1、不断付出不亚于任何人的努力,明天胜过今天,后天胜过明天;2、
- 蝴蝶忆水
杨子毓
图片发自App蝶望着天空。她快要死了,在一片海上。蝶笑了,凄惨的笑,悲凉,可怕,绝望于解脱,也许,只是一种苦笑。死是什么?是可以进入理想中的那一个美好的世界吗?是神话中所说的的天堂吗?蝶倒是期望那不是神话,是真的有天堂的存在。蝶还放不下什么?连她自己也不知道。她好像在寻找什么东西,抬起头来,她看见了第一颗星辰,它是那么美丽与闪耀,但是,它看起来好像也十分疲惫。爱慕之人已经不在了。心也已经死了。还有
- 蔬菜排骨汤
爱做早餐的小娜子
蔬菜排骨汤爱做早餐的小娜子娜家便当6天前温馨提示:你们的关注、阅读以及点赞,是对我最大的鼓励。因为当天的早晨做不到当天分享,都需要延迟一天才能分享,所以这次调整一下。每周一至周五更新哦。工作日早餐分享:主食:花卷汤:蔬菜排骨汤小菜:凉拌芦笋丝水果:丑桔准备食材:食材A:排骨、胡萝卜、藕、玉米、小葱、葱、姜食材B:普通面粉350g、发酵粉4g、小葱食材C:丑桔、芦笋蔬菜排骨汤:排骨清洗后,放入冷水锅
- python 变量进阶(理解)
程序员同行者
变量进阶(理解)目标变量的引用可变和不可变类型局部变量和全局变量01.变量的引用变量和数据都是保存在内存中的在Python中函数的参数传递以及返回值都是靠引用传递的1.1引用的概念在Python中变量和数据是分开存储的数据保存在内存中的一个位置变量中保存着数据在内存中的地址变量中记录数据的地址,就叫做引用使用id()函数可以查看变量中保存数据所在的内存地址注意:如果变量已经被定义,当给一个变量赋值
- 为什么动漫喜欢用实景?
夏目萤
其实所有的故事基本上都有一个真实的来源,甚至就是魔幻科幻类的作品,街道背景的设计构思时也肯定有一个原型的。日本动漫的话就更多都是作者熟悉的街巷来当作背景环境。而且日本各个地区的政府也有鼓励政策,让漫画家作家以自己的街区为背景创作故事,这样就可以增加街区的知名度,吸引来更多的人来玩,来看,那么就增加了地区的活跃性,消费性等等。当然对于好的作品,区政策也都是有设立奖金的。自己就住在《足球小子》原型的学
- 高省是什么平台?加入高省赚钱需要什么条件?
高省APP大九
高省是什么平台高省安全吗?高省app,实现你的赚钱梦想,打拼两年的我为大家详细介绍一下高省到底是什么平台。【高省】是一个可省钱佣金高,能赚钱有收益的平台,百度有几百万篇报道,也期待你的加入。高省邀请码999999,注册送2皇冠会员,送万元推广大礼包。下面继续跟大家聊聊高省有什么好处?1学习新的赚钱方法。您可以通过下载高省应用程序独立搜索优惠券,也可以通过加入代理商分享和赚钱。用户黏性高,不需要维护
- C语言:数组-字符串数组
数组字符串基础操作在用格式化说明符%s进行输入输出时,其输入输出项均为数组名。但在输入时,相邻两个字符串之间要用空格分隔,系统将自动在字符串后加\0。在输出时,遇到结束符\0作为输出结束标志。对于字符串的操作,我们需要使用到一些系统提供的API函数。字符串输入scanf语法:scanf("%s",数组名);注意:数组名对应的数组只能是char类型,从控制台输入字符串之后,默认为追加\0案例:#in
- 如何评价网络统计男方失业超过一年,女方提出离婚概率超80%?
旧约Alatus
个人收藏游戏golanglinuxjava机器学习virtualenvtornado
我来添一把柴吧,即使是因为爱情在一起的男女,男方失业的话,女方提出离婚的概率也是很高的。失业往往并不是钱的问题,而是男人一失业或者在自己的行业内失去了“拼搏”能力,男人很容易失去自信,魅力,朋友圈和小团体的领导力以及对于生活的掌控的感觉,然后这种“失去”会容易在情绪和状态上表现出来,此时女人就容易“失去感觉”,从而导致感情破裂。别说失业了,就是男人有钱但是不上班或者事业一直没有什么开拓,进展,女人
- .NET 8 Release Candidate 1 (RC1)现已发布,包括许多针对ASP.NET Core的重要改进!
步、步、为营
.netr语言asp.net
.NET8ReleaseCandidate1(RC1)发布:ASP.NETCore重大改进来袭!近日,.NET8ReleaseCandidate1(RC1)正式发布,这是在今年晚些时候计划发布的最终.NET8版本之前的两个候选版本中的第一个。此版本包含了大部分计划中的功能和变更,可供开发者提前尝鲜。不过,部分领域(尤其是Blazor)仍有重大变更待完成,预计将在下一个.NET8候选版本中落地。新功
- 屈原是谁?为何在大多数国人心中,后世没有诗人比得上屈原?
颜小二述哲文
屈原是我国最早的浪漫主义诗人,也是千年来华夏儿女心中“爱国主义精神”的化身。屈原以《离骚》让中国诗歌从集体转为个体,他在《九章》等诗歌中倾注的浪漫主义情怀,让他成为文学史上第一位留名的爱国诗人。那么,为何在大多数人心中,后世没有诗人比得上屈原?究其原因,颜小二认为,一方面是因为屈原在诗歌上的造诣;一方面是因为“他本人的事迹”对今人的意义,这种意义具体表现为一种精神传承:屈原于汨罗江以身殉道的义无反
- MYOJ_8519:CSP初赛题单5:机器数与位运算
更多初赛题单请参见题目整理CSP初赛题目整理题单,谢谢。题目描述1.[J-2017-1][S-2017-2]在8位二进制补码中,10101011表示的数是十进制下的()。A.43B.-85C.-43D.-84答案:B解析:符号为负,减1得10101010,取反得11010101,-(1+4+16+64)=-85。2.[S-2021-2]二进制数00101010和00010110的和为()。A.00
- 生活不易,珍惜自己的选择——日更【16】
窄门在身后
加油向上今天跟几个朋友在一起喝酒。特别高兴的一件事情。期间有一位小老弟,最近的生活状态不是特别好,因为家里有很多事情干扰了他的正常生活。以至于连谈个恋爱时间都不太充裕。他身边的每一个人,都不舍得放弃,他想做好每一个角色。对姥姥来讲他想做一个好外甥,对爸爸来讲他想做一个好儿子,对妈妈来讲,她想做妈妈的帮手,对正在谈的女朋友来讲,她想做一个合格的男朋友。当这几个方面出现冲突的时候,他显得非常的无奈,只
- 佳偶 第三十五章 热闹的岳州城(三)
月光如水夜微凉
无戒学堂日更第二天佳偶第三十五章热闹的岳州城(三)唐妙心里翻了个大大的白眼儿,看来:是福不是祸,是祸躲不过呀。为首的那人是个中年汉子,黑色方脸,手里拿着一把刀,一见唐妙“刷”的一刀就砍了过来……唐妙一惊,急忙侧身,堪堪避过。“哪来的疯子?上来就砍人?”真是流年不利,她这是招谁惹谁了?“你这小妖女,竟敢毒害我大侄子,我要你的命。”说着又要扑过来。“你且等等!”眼看要出人命了,老乞丐在旁边不能再袖手旁
- next.js刷新页面时二级菜单展开状态判断
啃火龙果的兔子
开发DEMOjavascript前端react.js
在Next.js中保持二级菜单刷新后展开状态的解决方案在Next.js应用中,当页面刷新时保持二级菜单的展开状态,可以通过以下几种方法实现:方法1:使用URL参数保存状态(推荐)import{useRouter}from'next/router';import{useEffect,useState}from'react';constMenuComponent=()=>{constrouter=us
- Laravel 原子锁概念讲解
引言什么是竞争条件(RaceCondition)?在并发编程中,当多个进程或线程同时访问和修改同一个共享资源时,最终结果会因其执行时序的微小差异而变得不可预测,甚至产生错误。这种情况被称为“竞争条件”。例子1:定时执行某个耗时的任务,如果第一个任务执行时还没有更新数据源,第二个任务就开始了,那么同一个数据源可能被更新或新增两次数据,最终导致数据源错误。例子2:商品秒杀场景:若库存仅剩1件,两个请求
- 躬身入局/作者:邵明
房作者_0970
橘生淮南则为橘,橘生淮北则为枳。(摘自网上)我是罗胖子的铁粉,从罗辑思维到奇葩说再到跨年演讲,他讲了六年我粉了六年,我女儿还买了他的“得到”。去年他夸奖了保险行业,说是新崛起的朝阳行业,今年平安保险就做了他的赞助商,罗胖子似乎在转型,今年人瘦了脸却有点像孔方兄了,也有人调侃说像工商银行的徽标外圆内方。今年世界各地疫情肆虐,欧美商场酒店一片萧条风景这边独好。在辞旧迎新的晚上魔都各大酒店桌桌满坐,包间
- 失业离异?本科的她用求职简历引爆全球黑客战争
失业离异?本科的她用求职简历引爆全球黑客战争28岁离异失业的蓉儿,被前夫靖哥哥在面试时嘲讽“大龄废柴”。她将211本科计算机功底炼成武器,将求职简历制成“地狱级蜜罐”。全球黑客组织疯狂破解她的“求职系统”,反被吸干攻击武器库。联合国紧急会议中,首席科学家席位虚位以待。靖哥哥颤抖着递来CEO聘书时,她瞥见邮件闪烁:“暗网帝国女皇之位,待君执掌”。七月的风带着黏腻的潮气,吹不散出租屋里沉甸甸的闷。蓉儿
- Spring Boot + Lua = 王炸!
程序没有bug
Javaspringboot编程java后端
曾经有一位魔术师,他擅长将SpringBoot和Redis这两个强大的工具结合成一种令人惊叹的组合。他的魔法武器是Redis的Lua脚本。今天,我们将揭开这个魔术师的秘密,探讨如何在SpringBoot项目中使用Lua脚本,以解锁新的可能性和提高性能。如果你一直在寻找提升你的应用程序的方法,那么这篇博客将为你揭示其中的神奇之处。第一部分:Lua脚本简介当涉及Lua编程时,以下是对前述12个关键概念
- 《九都记》第152章 八方祥云炼雷丹
秦纵横
“盖世英雄!”仙仙一怔,眯着的眸子里闪过一丝朦胧神往之色。这位犹带仙气儿的妙人儿,此时此刻打开了心中的梦幻,遐想无限。“我的盖世英雄会是他吗?我的意中人应该踏着七彩祥云出现吧?我在乱想些什么?”月勾下,心念他,红颜羞答答,朦胧处,念他心,春闺梦里人。皓月长情,一寸还成千万缕,红尘懵懂,半滴已醉女儿红。仙仙的心乱了,像剪不断的乱麻理不清,仙仙的心亦醉了,像沾染了花蜜有些甜。懵懵懂懂间,朦朦胧胧处,她
- 《次第花开》
33ab7295c163
一、认识苦根据佛陀的开示,解脱是从认识痛苦开始的。佛经上把痛苦分为三类:苦苦、变苦和行苦。显而易见、不折不扣的痛苦叫做苦苦;我们所认为的快乐,因为其本质为痛苦,而终将由快乐变成痛苦,这叫变苦;陷于轮回中的众生整个存在状态的无奈和不圆满,被种种烦恼束缚,这叫行苦。具体而言,人间的痛苦分为八种:生、老、病、死、怨憎会、爱离别、求不得、不欲临。承认痛苦的普遍性,看似悲观消极,实则不然。对痛苦的逃避反而会
- PHP 性能优化全攻略:提升 Web 应用速度的关键
来恩1003
PHP从入门到精通php性能优化前端
PHP学习资料PHP学习资料PHP学习资料在Web开发领域,PHP凭借其简单易用、开源免费等特性,成为众多开发者构建网站和应用的首选语言。然而,随着业务的发展和用户量的增加,PHP应用的性能问题逐渐凸显。性能不佳不仅会导致用户体验下降,还可能影响业务的发展。因此,对PHP代码进行性能优化至关重要。本文将深入探讨PHP性能优化的各个方面,包括缓存的使用、代码优化策略以及服务器配置优化等,帮助开发者打
- 那一丛丛狗尾巴
慵懒的尾巴
我觉得这世间最美的花是马路旁一丛丛随风飘摇的狗尾巴它们总是昂然地挺着头颅没有因为自然的威压而低下了腰杆我爱那一片片的狗尾巴有人说它是杂草,是没用的东西我却当它是这世上最美的花我散步在田间小路旁随手摘来一把扎了草环戴在你的头上你别急着摘下让我照一张相片来保存这不觉卑微的高昂优雅我觉得这世间最美的花它没有鲜艳的颜色,也没有共舞的虫蝶它只是从来不会把头低下你问我这花叫做什么我会笑着指向路边那一丛丛的狗尾
- pigz更快的压缩和解压工具
老率的IT私房菜
pigz(parallelimplementationofgzip)是一个并行执行的压缩工具,解压缩比gzip快,同时CPU消耗是gzip的好几倍,在对短时间内CPU消耗较高不受影响的场景下,可以使用pigz。环境Centos7RAM:2GB,CPU:4vcpus安装#安装epel扩展源[root@localhost~]#wget-O/etc/yum.repos.d/epel-7.repohttp
- 美团优惠券在哪里可以领.美团优惠券是商家承担还是平台承担?美团优惠券商家会吃亏吗
氧券超好用
美团优惠券在哪里可以领.美团优惠券是商家承担还是平台承担?美团优惠券商家会吃亏吗美团优惠券是美团平台上的一种促销工具,旨在为消费者提供优惠,同时吸引更多的用户购买。那么,美团优惠券在哪里可以领呢?美团优惠券的承担方是商家还是平台呢?商家是否会因此吃亏呢?本文将为您解答这些问题。一、美团优惠券在哪里可以领?美团优惠券可以在美团APP中领取。用户只需打开美团APP,进入优惠券中心,即可查看可领取的优惠
- JAVA中的Enum
周凡杨
javaenum枚举
Enum是计算机编程语言中的一种数据类型---枚举类型。 在实际问题中,有些变量的取值被限定在一个有限的范围内。 例如,一个星期内只有七天 我们通常这样实现上面的定义:
public String monday;
public String tuesday;
public String wensday;
public String thursday
- 赶集网mysql开发36条军规
Bill_chen
mysql业务架构设计mysql调优mysql性能优化
(一)核心军规 (1)不在数据库做运算 cpu计算务必移至业务层; (2)控制单表数据量 int型不超过1000w,含char则不超过500w; 合理分表; 限制单库表数量在300以内; (3)控制列数量 字段少而精,字段数建议在20以内
- Shell test命令
daizj
shell字符串test数字文件比较
Shell test命令
Shell中的 test 命令用于检查某个条件是否成立,它可以进行数值、字符和文件三个方面的测试。 数值测试 参数 说明 -eq 等于则为真 -ne 不等于则为真 -gt 大于则为真 -ge 大于等于则为真 -lt 小于则为真 -le 小于等于则为真
实例演示:
num1=100
num2=100if test $[num1]
- XFire框架实现WebService(二)
周凡杨
javawebservice
有了XFire框架实现WebService(一),就可以继续开发WebService的简单应用。
Webservice的服务端(WEB工程):
两个java bean类:
Course.java
package cn.com.bean;
public class Course {
private
- 重绘之画图板
朱辉辉33
画图板
上次博客讲的五子棋重绘比较简单,因为只要在重写系统重绘方法paint()时加入棋盘和棋子的绘制。这次我想说说画图板的重绘。
画图板重绘难在需要重绘的类型很多,比如说里面有矩形,园,直线之类的,所以我们要想办法将里面的图形加入一个队列中,这样在重绘时就
- Java的IO流
西蜀石兰
java
刚学Java的IO流时,被各种inputStream流弄的很迷糊,看老罗视频时说想象成插在文件上的一根管道,当初听时觉得自己很明白,可到自己用时,有不知道怎么代码了。。。
每当遇到这种问题时,我习惯性的从头开始理逻辑,会问自己一些很简单的问题,把这些简单的问题想明白了,再看代码时才不会迷糊。
IO流作用是什么?
答:实现对文件的读写,这里的文件是广义的;
Java如何实现程序到文件
- No matching PlatformTransactionManager bean found for qualifier 'add' - neither
林鹤霄
java.lang.IllegalStateException: No matching PlatformTransactionManager bean found for qualifier 'add' - neither qualifier match nor bean name match!
网上找了好多的资料没能解决,后来发现:项目中使用的是xml配置的方式配置事务,但是
- Row size too large (> 8126). Changing some columns to TEXT or BLOB
aigo
column
原文:http://stackoverflow.com/questions/15585602/change-limit-for-mysql-row-size-too-large
异常信息:
Row size too large (> 8126). Changing some columns to TEXT or BLOB or using ROW_FORMAT=DYNAM
- JS 格式化时间
alxw4616
JavaScript
/**
* 格式化时间 2013/6/13 by 半仙
[email protected]
* 需要 pad 函数
* 接收可用的时间值.
* 返回替换时间占位符后的字符串
*
* 时间占位符:年 Y 月 M 日 D 小时 h 分 m 秒 s 重复次数表示占位数
* 如 YYYY 4占4位 YY 占2位<p></p>
* MM DD hh mm
- 队列中数据的移除问题
百合不是茶
队列移除
队列的移除一般都是使用的remov();都可以移除的,但是在昨天做线程移除的时候出现了点问题,没有将遍历出来的全部移除, 代码如下;
//
package com.Thread0715.com;
import java.util.ArrayList;
public class Threa
- Runnable接口使用实例
bijian1013
javathreadRunnablejava多线程
Runnable接口
a. 该接口只有一个方法:public void run();
b. 实现该接口的类必须覆盖该run方法
c. 实现了Runnable接口的类并不具有任何天
- oracle里的extend详解
bijian1013
oracle数据库extend
扩展已知的数组空间,例:
DECLARE
TYPE CourseList IS TABLE OF VARCHAR2(10);
courses CourseList;
BEGIN
-- 初始化数组元素,大小为3
courses := CourseList('Biol 4412 ', 'Psyc 3112 ', 'Anth 3001 ');
--
- 【httpclient】httpclient发送表单POST请求
bit1129
httpclient
浏览器Form Post请求
浏览器可以通过提交表单的方式向服务器发起POST请求,这种形式的POST请求不同于一般的POST请求
1. 一般的POST请求,将请求数据放置于请求体中,服务器端以二进制流的方式读取数据,HttpServletRequest.getInputStream()。这种方式的请求可以处理任意数据形式的POST请求,比如请求数据是字符串或者是二进制数据
2. Form
- 【Hive十三】Hive读写Avro格式的数据
bit1129
hive
1. 原始数据
hive> select * from word;
OK
1 MSN
10 QQ
100 Gtalk
1000 Skype
2. 创建avro格式的数据表
hive> CREATE TABLE avro_table(age INT, name STRING)STORE
- nginx+lua+redis自动识别封解禁频繁访问IP
ronin47
在站点遇到攻击且无明显攻击特征,造成站点访问慢,nginx不断返回502等错误时,可利用nginx+lua+redis实现在指定的时间段 内,若单IP的请求量达到指定的数量后对该IP进行封禁,nginx返回403禁止访问。利用redis的expire命令设置封禁IP的过期时间达到在 指定的封禁时间后实行自动解封的目的。
一、安装环境:
CentOS x64 release 6.4(Fin
- java-二叉树的遍历-先序、中序、后序(递归和非递归)、层次遍历
bylijinnan
java
import java.util.LinkedList;
import java.util.List;
import java.util.Stack;
public class BinTreeTraverse {
//private int[] array={ 1, 2, 3, 4, 5, 6, 7, 8, 9 };
private int[] array={ 10,6,
- Spring源码学习-XML 配置方式的IoC容器启动过程分析
bylijinnan
javaspringIOC
以FileSystemXmlApplicationContext为例,把Spring IoC容器的初始化流程走一遍:
ApplicationContext context = new FileSystemXmlApplicationContext
("C:/Users/ZARA/workspace/HelloSpring/src/Beans.xml&q
- [科研与项目]民营企业请慎重参与军事科技工程
comsci
企业
军事科研工程和项目 并非要用最先进,最时髦的技术,而是要做到“万无一失”
而民营科技企业在搞科技创新工程的时候,往往考虑的是技术的先进性,而对先进技术带来的风险考虑得不够,在今天提倡军民融合发展的大环境下,这种“万无一失”和“时髦性”的矛盾会日益凸显。。。。。。所以请大家在参与任何重大的军事和政府项目之前,对
- spring 定时器-两种方式
cuityang
springquartz定时器
方式一:
间隔一定时间 运行
<bean id="updateSessionIdTask" class="com.yang.iprms.common.UpdateSessionTask" autowire="byName" />
<bean id="updateSessionIdSchedule
- 简述一下关于BroadView站点的相关设计
damoqiongqiu
view
终于弄上线了,累趴,戳这里http://www.broadview.com.cn
简述一下相关的技术点
前端:jQuery+BootStrap3.2+HandleBars,全站Ajax(貌似对SEO的影响很大啊!怎么破?),用Grunt对全部JS做了压缩处理,对部分JS和CSS做了合并(模块间存在很多依赖,全部合并比较繁琐,待完善)。
后端:U
- 运维 PHP问题汇总
dcj3sjt126com
windows2003
1、Dede(织梦)发表文章时,内容自动添加关键字显示空白页
解决方法:
后台>系统>系统基本参数>核心设置>关键字替换(是/否),这里选择“是”。
后台>系统>系统基本参数>其他选项>自动提取关键字,这里选择“是”。
2、解决PHP168超级管理员上传图片提示你的空间不足
网站是用PHP168做的,反映使用管理员在后台无法
- mac 下 安装php扩展 - mcrypt
dcj3sjt126com
PHP
MCrypt是一个功能强大的加密算法扩展库,它包括有22种算法,phpMyAdmin依赖这个PHP扩展,具体如下:
下载并解压libmcrypt-2.5.8.tar.gz。
在终端执行如下命令: tar zxvf libmcrypt-2.5.8.tar.gz cd libmcrypt-2.5.8/ ./configure --disable-posix-threads --
- MongoDB更新文档 [四]
eksliang
mongodbMongodb更新文档
MongoDB更新文档
转载请出自出处:http://eksliang.iteye.com/blog/2174104
MongoDB对文档的CURD,前面的博客简单介绍了,但是对文档更新篇幅比较大,所以这里单独拿出来。
语法结构如下:
db.collection.update( criteria, objNew, upsert, multi)
参数含义 参数
- Linux下的解压,移除,复制,查看tomcat命令
y806839048
tomcat
重复myeclipse生成webservice有问题删除以前的,干净
1、先切换到:cd usr/local/tomcat5/logs
2、tail -f catalina.out
3、这样运行时就可以实时查看运行日志了
Ctrl+c 是退出tail命令。
有问题不明的先注掉
cp /opt/tomcat-6.0.44/webapps/g
- Spring之使用事务缘由(3-XML实现)
ihuning
spring
用事务通知声明式地管理事务
事务管理是一种横切关注点。为了在 Spring 2.x 中启用声明式事务管理,可以通过 tx Schema 中定义的 <tx:advice> 元素声明事务通知,为此必须事先将这个 Schema 定义添加到 <beans> 根元素中去。声明了事务通知后,就需要将它与切入点关联起来。由于事务通知是在 <aop:
- GCD使用经验与技巧浅谈
啸笑天
GC
前言
GCD(Grand Central Dispatch)可以说是Mac、iOS开发中的一大“利器”,本文就总结一些有关使用GCD的经验与技巧。
dispatch_once_t必须是全局或static变量
这一条算是“老生常谈”了,但我认为还是有必要强调一次,毕竟非全局或非static的dispatch_once_t变量在使用时会导致非常不好排查的bug,正确的如下: 1
- linux(Ubuntu)下常用命令备忘录1
macroli
linux工作ubuntu
在使用下面的命令是可以通过--help来获取更多的信息1,查询当前目录文件列表:ls
ls命令默认状态下将按首字母升序列出你当前文件夹下面的所有内容,但这样直接运行所得到的信息也是比较少的,通常它可以结合以下这些参数运行以查询更多的信息:
ls / 显示/.下的所有文件和目录
ls -l 给出文件或者文件夹的详细信息
ls -a 显示所有文件,包括隐藏文
- nodejs同步操作mysql
qiaolevip
学习永无止境每天进步一点点mysqlnodejs
// db-util.js
var mysql = require('mysql');
var pool = mysql.createPool({
connectionLimit : 10,
host: 'localhost',
user: 'root',
password: '',
database: 'test',
port: 3306
});
- 一起学Hive系列文章
superlxw1234
hiveHive入门
[一起学Hive]系列文章 目录贴,入门Hive,持续更新中。
[一起学Hive]之一—Hive概述,Hive是什么
[一起学Hive]之二—Hive函数大全-完整版
[一起学Hive]之三—Hive中的数据库(Database)和表(Table)
[一起学Hive]之四-Hive的安装配置
[一起学Hive]之五-Hive的视图和分区
[一起学Hive
- Spring开发利器:Spring Tool Suite 3.7.0 发布
wiselyman
spring
Spring Tool Suite(简称STS)是基于Eclipse,专门针对Spring开发者提供大量的便捷功能的优秀开发工具。
在3.7.0版本主要做了如下的更新:
将eclipse版本更新至Eclipse Mars 4.5 GA
Spring Boot(JavaEE开发的颠覆者集大成者,推荐大家学习)的配置语言YAML编辑器的支持(包含自动提示,



![]()