http://en.wikipedia.org/wiki/Intel_Active_Management_Technology
Intel Active Management Technology
Intel Active Management Technology (AMT) is hardware-based technology for remotely managing and securing PCs out-of-band.[1][2][3][4][5] Currently, Intel AMT is available in desktops, servers, ultrabooks, tablets, and laptops with Intel Core vPro processor family, including Intel Core i3, i5, i7, and Intel Xeon processor E3-1200 product family.[1][6][7][8]
Contents
[hide]- 1 Overview of Intel AMT
- 1.1 Hardware-based management and software-based management
- 1.2 Benefits of Intel AMT hardware-based management
- 2 Intel AMT features
- 2.1 Hardware-based AMT features in laptop and desktop PCs
- 2.2 Additional AMT features in laptop PCs
- 2.3 Intel vPro platform features
- 3 Using Intel AMT
- 3.1 VNC-based KVM remote control
- 4 Out-of-band (OOB) communication with AMT
- 4.1 AMT out-of-band (OOB) communication for wired vs. wireless PCs
- 4.2 AMT out-of-band (OOB) secure communication outside the corporate firewall
- 4.2.1 How it works
- 5 Intel AMT security measures
- 5.1 Using AMT in a secure network environment
- 5.1.1 Intel AMT in a secured network environment: how it works
- 5.1.2 Security postures supported by Intel AMT versions
- 5.2 Intel AMT security technologies and methodologies
- 5.1 Using AMT in a secure network environment
- 6 Versions
- 7 Management Engine firmware modules
- 8 Provisioning and integration of Intel AMT
- 8.1 Intel vPro PCs can be sold with AMT enabled or disabled
- 8.2 Disabling and re-enabling Intel AMT
- 8.2.1 Disabling Intel AMT
- 8.2.2 Re-enabling Intel AMT
- 8.2.3 Returning AMT to factory default
- 8.3 Setup and integration tools
- 8.4 Implementation
- 9 Attacks
- 10 See also
- 11 References
- 12 External links
Overview of Intel AMT[edit]
Intel AMT is hardware and firmware technology that builds certain functionality into business PCs in order to monitor, maintain, update, upgrade, and repair PCs.[1] Intel AMT is part of the Intel Management Engine, which is built into PCs with Intel vPro technology.[2] Intel AMT is designed into a secondary (service) processor located on the motherboard. Intel AMT has moved towards increasing support for DMTF Desktop and mobile Architecture for System Hardware (DASH)standards and AMT Release 5.1 and later releases are an implementation of DASH version 1.0/1.1 standards for out-of-band management.[9] AMT provides similar functionality to IPMI, although AMT is designed for client computing systems as compared with the typically server-based IPMI.
AMT is not intended to be used by itself; it is intended to be used with a software management application.[1] It gives a management application (and thus, the system administrator who uses it) better access to the PC down the wire, in order to remotely and securely do tasks that are difficult or sometimes impossible when working on a PC that does not have remote functionalities built into it.[1][3][10][11]
Hardware-based management and software-based management[edit]
Hardware-based (or out-of-band) management is different from software-based (or in-band) management and software management agents.[1][2] Hardware-based management works at a different level than software applications, uses a communication channel (through the TCP/IP stack) that is different from software-based communication (which is through the software stack in the operating system). Hardware-based management does not depend on the presence of an OS or locally installed management agent.
Benefits of Intel AMT hardware-based management[edit]
Hardware-based management has been available on Intel/AMD based computers in the past, but it has largely been limited to auto-configuration using DHCP or BOOTPfor dynamic IP allocation and diskless workstations, as well as Wake-on-LAN (WOL) for remotely powering on systems.[12]
Intel AMT uses TLS-secured communication and strong encryption, to provide additional security.[2]
Intel AMT features[edit]
Intel AMT includes hardware-based remote management, security, power-management, and remote-configuration features.[1][13] These features allow an IT technician to access an AMT featured PC remotely.[10]
Intel AMT relies on a hardware-based out-of-band (OOB) communication channel[1] that operates below the OS level, the channel is independent of the state of the OS (present, missing, corrupted, down). The communication channel is also independent of the PC's power state, the presence of a management agent, and the state of many hardware components (such as hard disk drives and memory).
Most AMT features are available OOB, regardless of PC power state.[1] Other features require the PC to be powered up (such as console redirection via serial over LAN (SOL), agent presence checking, and network traffic filtering).[1] Intel AMT has remote power-up capability.
Hardware-based features can be combined with scripting to automate maintenance and service.[1]
Hardware-based AMT features in laptop and desktop PCs[edit]
Hardware-based AMT features include:
- Encrypted, remote communication channel for network traffic between the IT console and Intel AMT.[1][2]
- Ability for a wired PC (physically connected to the network) outside the company's firewall on an open LAN to establish a secure communication tunnel (via AMT) back to the IT console.[1][2] Examples of an open LAN include a wired laptop at home or at an SMB site that does not have a proxy server.
- Remote power up / power down / power cycle through encrypted WOL.[1][2]
- Remote boot, via integrated device electronics redirect (IDE-R).[1][2]
- Console redirection, via serial over LAN (SOL).[1]
- Keyboard, video, mouse (KVM) over network.
- Hardware-based filters for monitoring packet headers in inbound and outbound network traffic for known threats (based on programmable timers), and for monitoring known / unknown threats based on time-based heuristics. Laptops and desktop PCs have filters to monitor packet headers. Desktop PCs have packet-header filters and time-based filters.[1][2][14]
- Isolation circuitry (previously and unofficially called "circuit breaker" by Intel) to port-block, rate-limit, or fully isolate a PC that might be compromised or infected.[1][2][14]
- Agent presence checking, via hardware-based, policy-based programmable timers. A "miss" generates an event; you can specify that the event generate an alert.[1][2][14]
- OOB alerting.[1][2]
- Persistent event log, stored in protected memory (not on the hard drive).[1][2]
- Access (preboot) the PC's universal unique identifier (UUID).[1][2]
- Access (preboot) hardware asset information, such as a component's manufacturer and model, which is updated every time the system goes through power-on self-test (POST).[1][2]
- Access (preboot) to third-party data store (TPDS), a protected memory area that software vendors can use, in which to version information, .DAT files, and other information.[1][2]
- Remote configuration options, including certificate-based zero-touch remote configuration, USB key configuration (light-touch), and manual configuration.[1][2][15]
- Protected Audio/Video Pathway for playback protection of DRM-protected media.
Additional AMT features in laptop PCs[edit]
Laptops with AMT also include wireless technologies:
- Support for IEEE 802.11 a/g/n wireless protocols[1][6][16][17]
- Cisco-compatible extensions for Voice over WLAN[1][6][16][17]
Intel vPro platform features[edit]
Intel AMT is security and management technology that is built into PCs with Intel vPro technology.[1][12] PCs with Intel vPro include many other "platform" (general PC features) technologies and features.
Using Intel AMT[edit]
Almost all AMT features are available even if PC power is off, the OS is crashed, the software agent is missing, or hardware (such as a hard drive or memory) has failed.[1][2] The console-redirection feature (SOL), agent presence checking, and network traffic filters are available after the PC is powered up.[1][2]
Intel AMT supports these management tasks:
- Remotely power up, power down, power cycle, and power reset the computer.[1]
- Remote boot the PC by remotely redirecting the PC’s boot process, causing it to boot from a different image, such as a network share, bootable CD-ROM orDVD, remediation drive, or other boot device.[1][10] This feature supports remote booting a PC that has a corrupted or missing OS.
- Remotely redirect the system’s I/O via console redirection through serial over LAN (SOL).[1] This feature supports remote troubleshooting, remote repair, software upgrades, and similar processes.
- Access and change BIOS settings remotely.[1] This feature is available even if PC power is off, the OS is down, or hardware has failed. This feature is designed to allow remote updates and corrections of configuration settings. This feature supports full BIOS updates, not just changes to specific settings.
- Detect suspicious network traffic.[1][14] In laptop and desktop PCs, this feature allows a sys-admin to define the events that might indicate an inbound or outbound threat in a network packet header. In desktop PCs, this feature also supports detection of known and/or unknown threats (including slow- and fast-moving computer worms) in network traffic via time-based, heuristics-based filters. Network traffic is checked before it reaches the OS, so it is also checked before the OS and software applications load, and after they shut down (a traditionally vulnerable period for PCs[citation needed]).
- Block or rate-limit network traffic to and from systems suspected of being infected or compromised by computer viruses, computer worms, or other threats.[1][14] This feature uses Intel AMT hardware-based isolation circuitry that can be triggered manually (remotely, by the sys-admin) or automatically, based on IT policy (a specific event).
- Manage hardware packet filters in the on-board network adapter.[1][14]
- Automatically send OOB communication to the IT console when a critical software agent misses its assigned check in with the programmable, policy-based hardware-based timer.[1][14] A "miss" indicates a potential problem. This feature can be combined with OOB alerting so that the IT console is notified only when a potential problem occurs (helps keep the network from being flooded by unnecessary "positive" event notifications).
- Receive Platform Event Trap (PET) events out-of-band from the AMT subsystem (for example, events indicating that the OS is hung or crashed, or that apassword attack has been attempted).[1] You can alert on an event (such as falling out of compliance, in combination with agent presence checking) or on a threshold (such as reaching a particular fan speed).
- Access a persistent event log, stored in protected memory.[1] The event log is available OOB, even if the OS is down or the hardware has already failed.
- Discover an AMT system independently of the PC's power state or OS state.[1] Discovery (preboot access to the UUID) is available if the system is powered down, its OS is compromised or down, hardware (such as a hard drive or memory) has failed, or management agents are missing.
- Perform a software inventory or access information about software on the PC.[1] This feature allows a third-party software vendor to store software asset or version information for local applications in the Intel AMT protected memory. (This is the protected third party data store, which is different from the protected AMT memory for hardware component information and other system information). The third-party data store can be accessed OOB by the sys-admin. For example, an antivirus program could store version information in the protected memory that is available for third-party data. A computer script could use this feature to identify PCs that need to be updated.
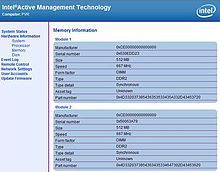
- Perform a hardware inventory by uploading the remote PC's hardware asset list (platform, baseboard management controller, BIOS, processor, memory, disks, portable batteries, field replaceable units, and other information).[1] Hardware asset information is updated every time the system runs through power-on self-test (POST).
VNC-based KVM remote control[edit]
From major version 6, Intel AMT embeds a proprietary VNC server, so you can connect out-of-band using dedicated VNC-compatible viewer technology, and have full KVM (Keyboard, Video, Mouse) capability throughout the power cycle - including uninterrupted control of the desktop when an operating system loads. Clients such as VNC Viewer Plus from RealVNC also provide additional functionality that might make it easier to perform (and watch) certain Intel AMT operations, such as powering the computer off and on, configuring the BIOS, and mounting a remote image (IDER).
Out-of-band (OOB) communication with AMT[edit]
Intel AMT is part of the Intel Management Engine. All access to the Intel AMT features is through the Intel Management Engine in the PC’s hardware and firmware.[1] AMT communication depends on the state of the Management Engine, not the state of the PC’s OS.
As part of the Intel Management Engine, the AMT OOB communication channel is based on the TCP/IP firmware stack designed into system hardware.[1] Because it is based on the TCP/IP stack, remote communication with AMT occurs via the network data path before communication is passed to the OS.
AMT out-of-band (OOB) communication for wired vs. wireless PCs[edit]
Intel AMT supports wired and wireless networks.[1][6][16][18] For wireless notebooks on battery power, OOB communication is available when the system is awake and connected to the corporate network, even if the OS is down. OOB communication is also available for wireless or wired notebooks connected to the corporate network over a host OS-based virtual private network (VPN) when notebooks are awake and working properly.
AMT out-of-band (OOB) secure communication outside the corporate firewall[edit]
AMT version 4.0 and higher can establish a secure communication tunnel between a wired PC and an IT console outside the corporate firewall.[1][19] In this scheme, a management presence server (Intel calls this a "vPro-enabled gateway") authenticates the PC, opens a secure TLS tunnel between the IT console and the PC, and mediates communication.[1][20] The scheme is intended to help the user or PC itself request maintenance or service when at satellite offices or similar places where there is no on-site proxy server or management appliance.
Technology that secures communications outside a corporate firewall is relatively new. It also requires that an infrastructure be in place, including support from IT consoles and firewalls.
How it works[edit]
An AMT PC stores system configuration information in protected memory. For PCs version 4.0 and higher, this information can include the name(s) of appropriate "whitelist" management servers for the company. When a user tries to initiate a remote session between the wired PC and a company server from an open LAN, AMT sends the stored information to a management presence server (MPS) in the "demilitarized zone" ("DMZ") that exists between the corporate firewall and client (the user PC's) firewalls. The MPS uses that information to help authenticate the PC. The MPS then mediates communication between the laptop and the company’s management servers.[1]
Because communication is authenticated, a secure communication tunnel can then be opened using TLS encryption. Once secure communications are established between the IT console and Intel AMT on the user's PC, a sys-admin can use the typical AMT features to remotely diagnose, repair, maintain, or update the PC.[1]
Intel AMT security measures[edit]
Because AMT allows access to the PC below the OS level, security for the AMT features is a key concern.
Security for communications between Intel AMT and the provisioning service and/or management console can be established in different ways depending on the network environment. Security can be established via certificates and keys (TLS public key infrastructure, or TLS-PKI), pre-shared keys (TLS-PSK), or administrator password.[1][2]
Security technologies that protect access to the AMT features are built into the hardware and firmware. As with other hardware-based features of AMT, the security technologies are active even if the PC is powered off, the OS is crashed, software agents are missing, or hardware (such as a hard drive or memory) has failed.[1][2][21]
Using AMT in a secure network environment[edit]
Because in-band remote management does not usually occur over a secured network communication channel, businesses have typically had to choose between having asecure network or allowing IT to use remote management applications without secure communications to maintain and service PCs.[1]
Modern security technologies and hardware designs allow remote management even in more secure environments. For example, Intel AMT supports IEEE 802.1x, Preboot Execution Environment (PXE), Cisco SDN, and Microsoft NAP.[1]
All AMT features are available in a secure network environment. With Intel AMT in the secure network environment:
- The network can verify the security posture of an AMT-enabled PC and authenticate the PC before the OS loads and before the PC is allowed access to the network.
- PXE boot can be used while maintaining network security. In other words, an IT administrator can use an existing PXE infrastructure in an IEEE 802.1x, CiscoSDN, or Microsoft NAP network.
Intel AMT in a secured network environment: how it works[edit]
Intel AMT can embed network security credentials in the hardware, via the Intel AMT Embedded Trust Agent and an AMT posture plug-in.[1][2] The plug-in collects security posture information, such as firmware configuration and security parameters from third-party software (such as antivirus software and antispyware),BIOS, and protected memory. The plug-in and trust agent can store the security profile(s) in AMT's protected, nonvolatile memory, which is not on the hard disk drive.
Because AMT has an out-of-band communication channel, AMT can present the PC's security posture to the network even if the PC's OS or security software is compromised. Since AMT presents the posture out-of-band, the network can also authenticate the PC out-of-band, before the OS or applications load and before they try to access the network. If the security posture is not correct, a system administrator can push an update OOB (via Intel AMT) or reinstall critical security software before letting the PC access the network.
Security postures supported by Intel AMT versions[edit]
Support for different security postures depends on the AMT release:
- Support for IEEE 802.1x and Cisco SDN requires AMT version 2.6 or higher for laptops, and AMT version 3.0 or higher for desktop PCs.[1][22][23]
- Support for Microsoft NAP requires AMT version 4.0 or higher.[1]
- Support for PXE boot with full network security requires AMT version 3.2 or higher for desktop PCs.[1]
Intel AMT security technologies and methodologies[edit]
AMT includes several security schemes, technologies, and methodologies to secure access to the AMT features during deployment and during remote management.[1][2][21] AMT security technologies and methodologies include:
- Transport Layer Security, including pre-shared key TLS (TLS-PSK)
- HTTP authentication
- Single sign-on to Intel AMT with Microsoft Windows domain authentication, based on Microsoft Active Directory and Kerberos
- Digitally signed firmware
- Pseudo-random number generator (PRNG) which generates session keys
- Protected memory (not on the hard disk drive) for critical system data, such as the UUID, hardware asset information, and BIOS configuration settings
- Access control lists (ACL)
As with other aspects of Intel AMT, the security technologies and methodologies are built into the chipset.
Versions[edit]
Intel AMT versions can be updated in software to the next minor version. New major releases of Intel AMT are built into a new chipset, and are updated through new hardware.[2]
Management Engine firmware modules[edit]
- Active Management Technology (AMT)
- Alert Standard Format (ASF)
- Quiet System Technology (QST), formerly Advanced Fan Speed Control (AFSC)
- Trusted Platform Module (TPM)
Provisioning and integration of Intel AMT[edit]
AMT supports certificate-based or PSK-based remote provisioning (full remote deployment), USB key-based provisioning (“one-touch” provisioning), manual provisioning[1] and provisioning using an agent on the local host ("Host Based Provisioning"). An OEM can also pre-provision AMT.[15]
The current version of AMT supports remote deployment on both laptop and desktop PCs. (Remote deployment was one of the key features missing from earlier versions of AMT and which delayed acceptance of AMT in the market.)[10] Remote deployment, until recently, was only possible within a corporate network.[24]Remote deployment lets a sys-admin deploy PCs without “touching” the systems physically.[1] It also allows a sys-admin to delay deployments and put PCs into use for a period of time before making AMT features available to the IT console.[25] As delivery and deployment models evolve, AMT can now be deployed over the Internet, using both "Zero-Touch" and Host-Based methods.[26]
Intel vPro PCs can be sold with AMT enabled or disabled[edit]
PCs with Intel AMT can be sold with AMT enabled or disabled. The OEM determines whether to ship AMT with the capabilities ready for setup (enabled) or disabled. Your setup and configuration process will vary, depending on the OEM build.[15]
Intel AMT includes a Privacy Icon application, called IMSS,[27] that notifies the system's user if AMT is enabled. It is up to the OEM to decide whether they want to display the icon or not.
Disabling and re-enabling Intel AMT[edit]
Intel AMT supports different methods for disabling the management and security technology, as well as different methods for reenabling the technology.[1][25][28][29]
Disabling Intel AMT[edit]
AMT can be partially unprovisioned using the Configuration Settings, or fully unprovisioned by erasing all configuration settings, security credentials, and operational and networking settings; or by resemotherboard.[30]
A partial unprovisioning leaves the PC in the setup state. In this state, the PC can self-initiate its automated, remote configuration process. A full unprovisioning erases the configuration profile as well as the security credentials and operational / networking settings required to communicate with the Intel Management Engine. A full unprovisioning returns Intel AMT to its factory default state.
Re-enabling Intel AMT[edit]
Once AMT is disabled, in order to enable AMT again, an authorized sys-admin can reestablish the security credentials required to perform remote configuration by either:
- Using the remote configuration process (full automated, remote config via certificates and keys).[1] This probably means that AMT is always listening to open ports to the wild and cannot be disabled at all.
- Physically accessing the PC to restore security credentials, either by USB key or by entering the credentials and MEBx parameters manually.[1]
Returning AMT to factory default[edit]
There is a way to totally reset AMT and return in to factory defaults. This can be done in two ways:
- Setting the appropriate value in the BIOS.
- Clearing the CMOS memory and/or NVRAM.
Setup and integration tools[edit]
Setup and integration of Intel AMT is supported by a setup and configuration service (for automated setup), an AMT Webserver tool (included with Intel AMT), and AMT Commander, an unsupported and free, proprietary application available from the Intel website.
Implementation[edit]
The management controller for AMT is embedded in the northbridge of the motherboard for recent versions, or network card for AMT 1.0 (as compared with e.g. typical IPMI implementations where the management controller is a discrete part). On current Intel chipsets, an ARC4 RISC microcontroller running the Nucleus RTOS is used as the service processor.
See also[edit]
- Relationships between Intel vPro, AMT, Intel Centrino 2, and Intel Core 2
- Intel AMT versions
- Intel vPro
- Intel Core 2
- Intel Centrino 2
- Distributed Management Task Force (DMTF)
- Alert Standard Format (ASF)
- Desktop and mobile Architecture for System Hardware (DASH)
- Intelligent Platform Management Interface (IPMI)
- Baseboard management controller (BMC)
- Host Embedded Controller Interface (HECI)
- Trusted Platform Module (TPM)
- Northbridge (computing) (NB)
- Southbridge (computing) (SB)
- I/O Controller Hub (ICH)
- Out-of-band management
- Lights out management
- HP Integrated Lights-Out (HP/Compaq specific)
- Intel CIRA
|
||||||||||||||
http://en.wikipedia.org/wiki/Intel_AMT_versions
Intel AMT versions
Intel Active Management Technology (AMT) is hardware-based technology built into PCs with Intel vPro technology. AMT is designed to help sys-admins remotely manage and secure PCs out-of-band when PC power is off, the operating system (OS) is unavailable (hung, crashed, corrupted, missing), software management agents are missing, or hardware (such as a hard disk drive or memory) has failed.[1][2][3][4][5]
Contents
[hide]- 1 Versions
- 1.1 Comparison of AMT versions
- 2 See also
- 3 Notes
- 4 External links
Versions[edit]
Intel AMT is built into a small secondary processor located on the motherboard. This OOB controller has embedded firmware that runs on the Manageability Engine (ME), a separate small ARC architecture processor built into the northbridge (or network card for AMT 1.0) of the motherboard. The AMT firmware is stored in the same SPI flash memory component used to store the BIOS and is generally updated along with the BIOS. FWH (Firmware Hub) or LPC firmware storage is not supported for AMT.[2]
In general, an AMT version can be updated in software to the next minor version. New major releases of Intel AMT are built into a new chipset, and are updated through new hardware.
- Intel AMT 9.0 — Intel 8 Series chipset (Lynx Point). SOAP(EOI) protocol removed.
- Intel AMT 8.0 — Intel Q75 and Q77 (Maho Bay: Panther Point) chipset, mobile QM77 and QS77 (Chief River: Panther Point) chipset.
- Intel AMT 7.0 — Intel Q67 (Sugar Bay: Cougar Point) chipset, mobile QM67 and QS67 (Huron River: Cougar Point) chipset.
- Intel AMT 6.0 — Intel Core i5/7 vPro desktop platforms based on the Q57 (Piketon: Ibex Peak) chipset, Core i5/7 vPro mobile platforms based on the QM57 and QS57 (Calpella: Ibex Peak) chipset, and Xeon 3400 series/Core i5 vPro entry workstation platforms based on the 3450 chipset.
- Intel AMT 5.0 — Intel Core 2 vPro desktop platforms (launched September 22, 2008) based on the Intel Q45 (McCreary: Eaglelake-Q, ICH10) chipsets.[6]
- Intel AMT 4.1 — Intel AMT 4.0 + Intel Anti-Theft Technology. Supported on same mobile platforms as Intel AMT 4.0, and based on the GM45 (Montevina, ICH9M) chipset.[7]
- Intel AMT 4.0 — Mobile platforms with Intel Centrino 2 with vPro based on the GM45 or 47/PM45 (Montevina: Cantiga, ICH9M) chipsets.[1][5][8][9]
- Intel AMT 3.2 — Intel AMT 3.0 + extra DASH 1.0 (simplified configuration) support and bug fixes (supported on same desktop platforms as Intel AMT 3.1 and Intel AMT 3.0).[1][9]
- Intel AMT 3.1 — Intel AMT 3.0 + Linux (Red Hat and SUSE) support (supported on same desktop platforms as Intel AMT 3.0; uses same firmware).[1][9]
- Intel AMT 3.0 — Intel vPro desktop platforms based on the Intel Q35 (Weybridge: Bearlake-Q, ICH9) chipsets, e.g., the Intel DQ35MP motherboard.[1][4]
- Intel AMT 2.6 — Intel AMT 2.5 + Remote Configuration and bug fixes (supported on same platforms as Intel AMT 2.5).[10]
- Intel AMT 2.5 — Intel Centrino Pro mobile platforms based on the GM965/PM965 (Santa Rosa: Crestline, ICH8M) chipsets.[4][10]
- Intel AMT 2.2 — Intel AMT 2.1 + Remote Configuration and bug fixes (supported on same platforms as Intel AMT 2.1 and Intel AMT 2.0).[10]
- Intel AMT 2.1 — Intel AMT 2.0 + AMT Power Savings (Intel Management Engine Wake on LAN) and bug fixes (supported on same platforms as Intel AMT 2.0).[10]
- Intel AMT 2.0 — Intel vPro desktop platforms based on the Intel Q963/Q965 (Broadwater-Q, ICH8) chipsets, e.g., the Intel DQ965GF motherboard.[10]
- Intel AMT 1.0 — Intel platforms based on the Intel 82573E (Tekoa; usually 945, ICH7) Gigabit Ethernet Controller, e.g., the Intel D975XBX2 motherboard. This version provides basic NVRAM, hardware asset, event log and other basic features. It does not provide Intel System Defense network filters.
Comparison of AMT versions[edit]
The following is a comparison of the various features supported by each version of Intel AMT[11][12][13]
| Feature | AMT 1.0 (Desktop) |
AMT 2.0/2.1 (Desktop) |
AMT 2.5/2.6 (Mobile) |
AMT 3.0 (Desktop) |
AMT 4.0 (Mobile) |
AMT 5.0 (Desktop) |
6.0 (Desktop & Mobile) |
7.0 & 8.0 (Desktop & Mobile) |
9.0 (Desktop & Mobile) |
|---|---|---|---|---|---|---|---|---|---|
| Hardware Inventory | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Persistent ID | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Remote Power On/Off | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| SOL/IDER[note 1] | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Event Management | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Third-party Data Storage | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Built-in web server | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Flash Protection | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Firmware Update | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| TCP/IP, SOAP XML/EOI | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No[note 2] | No[note 2] |
| HTTP Digest/TLS | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Static and dynamic IP | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| System Defense | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Agent Presence | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Power Policies | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Mutual Authentication | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Kerberos | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| TLS-PSK | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Privacy Icon | No | 2.1 and up | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| ME Wake-on-LAN | No | 2.1 and up | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Remote Configuration | No | 2.2 and up | 2.6 and up | Yes | Yes | Yes | Yes | Yes | Yes |
| Wireless Configuration | No | No | Yes | No | Yes | No | Yes | Yes | Yes |
| Endpoint Access Control (EAC) 802.1 | No | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Power Packages | No | No | Yes | No | Yes | No | Yes | Yes | Yes |
| Environment Detection | No | No | Yes | No | Yes | No | Yes | Yes | Yes |
| Event Log Reader Realm | No | No | 2.6 and up | Yes | Yes | Yes | Yes | Yes | Yes |
| System Defense Heuristics | No | No | No | Yes | No | Yes | Yes | Yes | Yes |
| WS-Management interface | No | No | No | Yes | Yes | Yes | Yes | Yes | Yes |
| VLAN settings for Intel AMT network interfaces | No | No | No | Yes | No | Yes | Yes | Yes | Yes |
| Fast Call For Help (CIRA) | No | No | No | No | Yes | Yes | Yes | Yes | Yes |
| Access Monitor | No | No | No | No | Yes | Yes | Yes | Yes | Yes |
| MS NAP support | No | No | No | No | Yes | Yes | Yes | Yes | Yes |
| Virtualization Support for Agent Presence | No | No | No | No | No | Yes | Yes | Yes | Yes |
| PC Alarm Clock | No | No | No | No | No | 5.1 and up | Yes | Yes | Yes |
| KVM Remote Control | No | No | No | No | No | No | Yes | Yes | Yes |
| Wireless Profile Synchronization | No | No | No | No | No | No | Yes | Yes | Yes |
| Support for IPv6 | No | No | No | No | No | No | Yes | Yes | Yes |
| Host-based Provisioning | No | No | No | No | No | No | No | Yes | Yes |
| Host-based over the Internet Provisioning | No | No | No | No | Yes | Yes | Yes | Yes | Yes |
| Zero-touch over the Internet Provisioning | No | No | No | No | Yes | Yes | Yes | Yes | Yes |
| Gracefull Shutdown | No | No | No | No | No | No | No | No | Yes |
- Jump up^ Serial Over LAN/IDE-Redirection is an Intel AMT protocol that allows the host computer to access the floppy disk or CD drive of the connecting computer[14]
- ^ Jump up to:a b SOAP (EOI) was deprecated from AMT 6.0 onwards in favour of WS-MAN, AMT 9.0 is WS-MAN only[15]
vPro hardware requirements[edit]
The first release of Intel vPro was built with an Intel Core 2 Duo processor.[4] The current versions of Intel vPro are built into systems with 22 nm Intel 4th Generation Core i5 & i7 processors.
PCs with Intel vPro require specific chipsets. Intel vPro releases are usually identified by their AMT version.[1][4]
Laptop PC requirements[edit]
Laptops with Intel vPro require:
- For Intel AMT release 9.0 (4th Generation Intel Core i5 and Core i7):
- 22 nm Intel 4th Generation Core i7 Mobile Processors.[30]
- 22 nm Intel 4th Generation Core i5 Mobile Processors.[31]
- Mobile QM87 Chipsets [32]
- For Intel AMT release 8.0 (3rd Generation Intel Core i5 and Core i7):
- 32 & 45 nm Intel 3rd Generation Core i7 Mobile Processors.[33]
- 32 & 45 nm Intel 3rd Generation Core i5 Mobile Processors.[34]
- Mobile QM77 & Q77 Chipsets [32]
- For Intel AMT release 4.1 (Intel Centrino 2 with vPro technology):[35]
- 45 nm Intel Core2 Duo processor T, P sequence 8400, 8600, 9400, 9500, 9600; small form factor P, L, U sequence 9300 and 9400, and Quad processor Q9100.
- Mobile 45 nm Intel GS45, GM47, GM45 and PM45 Express Chipsets (Montevina with Intel Anti-Theft Technology) with 1066 FSB, 6 MB L2 cache, ICH10M-enhanced.
- For Intel AMT release 4.0 (Intel Centrino 2 with vPro technology):[1][5]
- 45 nm Intel Core2 Duo processor T, P sequence 8400, 8600, 9400, 9500, 9600; small form factor P, L, U sequence 9300 and 9400, and Quad processor Q9100.
- Mobile 45 nm Intel GS45, GM47, GM45 and PM45 Express Chipsets (Montevina) with 1066 FSB, 6 MB L2 cache, ICH9M-enhanced.
- For Intel AMT release 2.5 and 2.6 (Intel Centrino with vPro technology):[4][6][36]
- Intel Core2 Duo processor T, L, and U 7000 sequence3, 45 nm Intel Core2 Duo processor T8000 and T9000
- Mobile Intel 965 (Broadwater-Q) Express Chipset with ICH8M-enhanced.
Note that AMT release 2.5 for wired/wireless laptops and AMT release 3.0 for desktop PCs are concurrent releases.
Desktop PC requirements[edit]
Desktop PCs with vPro (called "Intel Core 2 with vPro technology") require:
- For AMT release 5.0:[37]
- Intel Core2 Duo processor E8600, E8500, and E8400 ; 45 nm Intel Core2 Quad processor Q9650, Q9550, and Q9400.
- Intel Q45 (Eaglelake-Q) Express Chipset with ICH10DO.
- For AMT release 3.0, 3.1, and 3.2:[1][4][5]
- Intel Core2 Duo processor E6550, E6750, and E6850; 45 nm Intel Core2 Duo processor E8500, E8400, E8300 and E8200; 45 nm Intel Core2 Quad processor Q9550, Q9450 and Q9300.
- Intel Q35 (Bearlake-Q) Express Chipset with ICH9DO.
Note that AMT release 2.5 for wired/wireless laptops and AMT release 3.0 for desktop PCs are concurrent releases.
- For AMT release 2.0, 2.1 and 2.2:[4][6][36]
- Intel Core 2 Duo processor E6300, E6400, E6600, and E6700.
- Intel Q965 (Averill) Express Chipset with ICH8DO.
vPro, AMT, Core i relationships[edit]
There are numerous Intel brands. However, the key differences between vPro (an umbrella marketing term), AMT (a technology under the vPro brand), Intel Core i5 and Intel Core i7 (a branding of a package of technologies), and Core i5 and Core i7 (a processor) are as follows:
The Core i7, the first model of the i series was launched in 2008, and the less-powerful i5 and i3 models were introduced in 2009 and 2010, respectively. The microarchitecture of the Core i series was code-named Nehalem, and the second generation of the line was code-named Sandy Bridge.
Intel Centrino 2 was a branding of a package of technologies that included Wi-Fi and, originally, the Intel Core 2 Duo.[3] The Intel Centrino 2 brand was applied to mobile PCs, such as laptops and other small devices. Core 2 and Centrino 2 have evolved to use Intel's latest 45-nm manufacturing processes, havemulti-core processing, and are designed for multithreading.
Intel vPro is a brand name for a set of Intel technology features that can be built into the hardware of the laptop or desktop PC.[1] The set of technologies are targeted at businesses, not consumers. A PC with the vPro brand often includes Intel AMT, Intel Virtualization Technology (Intel VT), Intel Trusted Execution Technology (Intel TXT), a gigabit network connection, and so on. There may be a PC with a Core 2 processor, without vPro features built in. However, vPro features require a PC with at least a Core 2 processor. The technologies of current versions of vPro are built into PCs with Core 2 Duo or Core 2 Quad processors and more recently some versions of Core i5 and Core i7 processors.
Intel AMT is part of the Intel Management Engine that is built into PCs with the Intel vPro brand. Intel AMT is a set of remote management and security hardware features that let a sys-admin with AMT security privileges access system information and perform specific remote operations on the PC.[4] These operations include remote power up/down (via wake on LAN), remote / redirected boot (via integrated device electronics redirect, or IDE-R), console redirection (via serial over LAN), and other remote management and security features.
http://www.intel.com/content/www/us/en/architecture-and-technology/intel-active-management-technology.html
Intel® Active Management Technology
Query, restore, upgrade, and protect devices remotely
Increase efficiency and effectiveness, automatically
Using integrated platform capabilities and popular third-party management and security applications, Intel® Active Management Technology (Intel® AMT) allows IT or managed service providers to better discover, repair, and protect their networked computing assets. Intel AMT enables IT or managed service providers to manage and repair not only their PC assets, but workstations and entry servers as well, utilizing the same infrastructure and tools across platforms for management consistency. For embedded developers, this means that devices can be diagnosed and repaired remotely, ultimately lowering IT support costs. Intel AMT is a feature of Intel® Core™ processors with Intel® vPro™ technology1,2 and workstation platforms based on select Intel® Xeon® processors.
The solution to challenging IT and intelligent systems issues
Intel design teams determined that better asset management, reduced downtime, and minimized desk-side visits were best addressed through platform architectural enhancements, resulting in the following features and benefits for supporting those needs.
Out-of-band system access
With built-in manageability, Intel AMT allows IT to discover assets even while platforms are powered off.1,2
Remote troubleshooting and recovery
With out-of-band management capabilities, including Keyboard-Video-Mouse (KVM) Remote Control,3 Intel AMT allows IT to remotely remediate and recover systems after OS failures. Out-of-band alerting and event logging also help to reduce downtime.
Hardware-based agent presence checking
Ensuring better protection for your enterprise, hardware-based agent presence checking proactively detects when software agents are running. When missing agents are detected, alerts are sent to the management console.
Proactive alerting
Intel® AMT System Defense Manager proactively blocks incoming threats, containing infected clients before they impact the network and alerting IT when critical software agents are removed.
Remote hardware and software asset tracking
Intel AMT helps keep software and virus protection up-to-date across the enterprise, enabling third-party software to store version numbers or policy data in non-volatile memory for off-hours retrieval or updates.
Expanded capabilities
With the Intel® vPro™ Technology Module for Microsoft Windows PowerShell*, IT has direct access to Intel AMT and can use Windows PowerShell scripts to take advantage of features not available in their existing management console—for example, remotely configuring alarm clock settings.
Increase efficiency and effectiveness
Windows PowerShell scripts integrate seamlessly into existing tools, enabling IT to quickly and easily execute Intel AMT commands on their Intel vPro-based managed clients and workstations and Intel AMT-capable entry servers.
1. Intel® vPro™ technology is sophisticated and requires setup and activation. Availability of features and results will depend upon the setup and configuration of your hardware, software, and IT environments. To learn more visit: www.intel.com/content/www/us/en/architecture-and-technology/vpro/vpro-technology-general.html.
2. Requires activation and a system with a corporate network connection, an Intel® AMT-enabled chipset, network hardware, and software. For notebooks, Intel AMT may be unavailable or limited over a host OS-based VPN, when connecting wirelessly, on battery power, sleeping, hibernating, or powered off. Results dependent upon hardware, setup, and configuration. For more information, visit www.intel.com/technology/vpro/index.htm.
3. KVM Remote Control (Keyboard, Video, Mouse) is only available with the Intel® Xeon® processor family, Intel® Core™ i5 vPro™ processor, and Intel® Core™ i7 vPro™ processor running activated and configured Intel® Active Management Technology with integrated graphics. Discrete graphics are not supported.
http://linux.die.net/man/7/amt-howto
Name
amt-howto - Intel AMT with linux mini howto
Description
What is AMT and why I should care?
AMT stands for "Active Management Technology". It provides some remote management facilities. They are handled by the hardware and firmware, thus they work independant from the operation system. Means: It works before Linux bootet up to the point where it activated the network interface. It works even when your most recent test kernel deadlocked the machine. Which makes it quite useful for development machines ...
Intel AMT is part of the vPro Platform. Recent intel-chipset based business machines should have it. My fairly new Intel SDV machine has it too.
Documentation
Look here for documentation beyond this mini howto:
http://www.intel.com/technology/platform-technology/intel-amt/
Most useful to get started: "Intel AMT Deployment and Reference Guide"
Very short AMT enabling instructions.
- Enter BIOS Setup.
- * Enable AMT
- Enter ME (Management Extention) Setup. Ctrl-P hotkey works for me.
-
* Login, factory default password is "admin".
* Change password. Trivial ones don't work, must include upper- and lowercase letters, digits, special characters.
* Enable AMT Managment. - Reboot, Enter ME Setup again with AMT enabled.
-
* Configure AMT (hostname, network config, ...)
* Use SMB (Small Business) management mode. The other one (Enterprise) requires Active Directory Service Infrastructure, you don't want that, at least not for your first steps ...
Testing AMT
Take your browser, point it to http://machine:16992/. If you configured AMT to use DHCP (which is the default) the OS and the management stack share the same IP address.
You must do that from a remote host as the NIC intercepts network packets for AMT, thus it doesn't work from the local machine as the packets never pass the NIC then. If everything is fine you'll see a greeting page with a button for login.
You can login now, using "admin" as username and the password configured during setup. You'll see some pages with informations about the machine. You can also change AMT settings here.
Control Machine
You might have noticed already while browing the pages: There is a "Remote Control" page. You can remotely reset and powercycle the machine there, thus recover the machine after booting a b0rken kernel, without having someone walk over to the machine and hit the reset button.
Serial-over-LAN (SOL) console
AMT also provides a virtual serial port which can be accessed via network. That gives you a serial console without a serial cable to another machine.
If you have activated AMT and SOL the linux kernel should see an additional serial port, like this on my machine:
[root@xeni ~]# dmesg | grep ttyS2 0000:00:03.3: ttyS2 at I/O 0xe000 (irq = 169) is a 16550A
Edit initab, add a line like this:
S2:2345:respawn:/sbin/agetty ttyS2 115200 vt100-nav
You should add the serial port to /etc/securetty too so you are able to login as root. Reload inittab ("init q"). Use amtterm to connect. Tap enter. You should see a login prompt now and be able to login.
You can also use that device as console for the linux kernel, using the usual "console=ttyS2,115200" kernel command line argument, so you see the boot messages (and kernel Oopses, if any).
You can tell grub to use that serial device, so you can pick a working kernel for the next boot. Usual commands from the grub manual, except that you need "--port=0xe000" instead of "--unit=0" due to the non-standard I/O port for the serial line (my machine, yours might use another port, check linux kernel boot messages).
The magic command for the Xen kernel is "com1=115200,8n1,0xe000,0" (again, you might have to replace the I/O port). The final '0' disables the IRQ, otherwise the Xen kernel hangs at boot after enabling interrupts.
Fun with Xen and AMT
The AMT network stack seems to become slightly confused when running on a Xen host in DHCP mode. Everything works fine as long as only Dom0 runs. But if one starts a guest OS (with bridged networking) AMT suddenly changes the IP address to the one the guest aquired via DHCP.
It is probably a good idea to assign a separate static IP address to AMT then. I didn't manage to switch my machine from DHCP to static IP yet though, the BIOS refuses to accept the settings. The error message doesn't indicate why.
More fun with AMT
You might want to download the DTK (Developer Toolkit, source code is available too) and play with it. The .exe is a self-extracting rar archive and can be unpacked on linux using the unrar utility. The Switchbox comes with a linux binary (additionally to the Windows stuff). The GUI tools are written in C#. Trying to make them fly with mono didn't work for me though (mono version 1.2.3 as shipped with Fedora 7).
See Also
amtterm(1), gamt(1), amttool(1)
http://www.intel.com/technology/platform-technology/intel-amt/
Written by
Gerd Hoffmann <[email protected]>