- [BJDCTF2020]JustRE
32304353
安全汇编
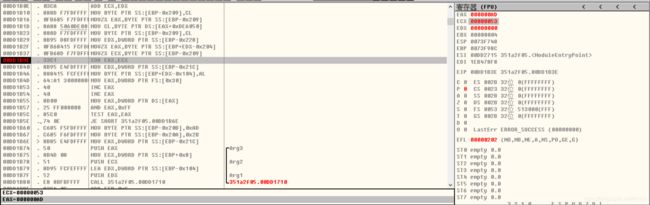
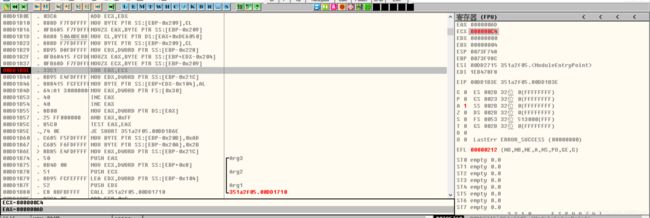
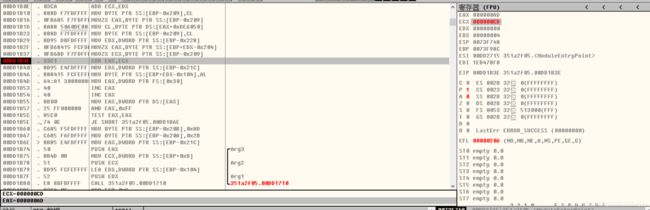
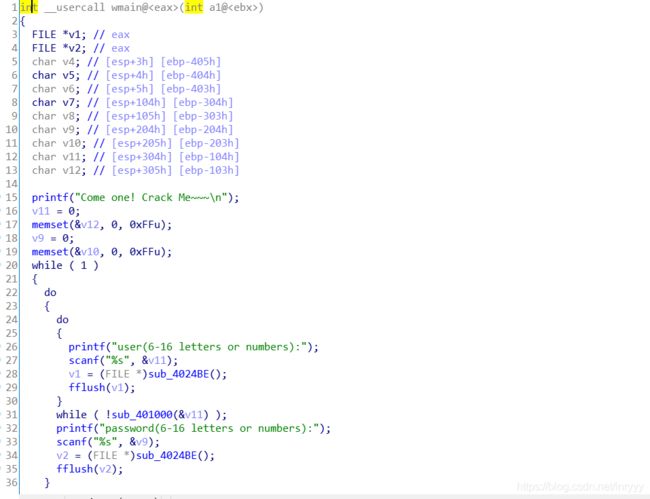
打开程序发现需要进行点击获取flag拖入IDA进行分析F5挨个查看代码发现疑似falg的数据经过判断,需要点击19999次获得flag把%d带入即可获取flagflag{1999902069a45792d233ac}提交flag解题思路参考文章BUUCTF-[BJDCTF2020]JustRE1-CSDN博客
- buuctf-变异凯撒
qis_qis
crypto其他
凯撒密码作为最古老的密码体制之一,相信大多数人都知道,即简单的移位操作,那么问题来了,变异的凯撒密码又会是什么呢?拿到题先比对acsii码值对比表:acsii码通过上面的acsii码值对比表可以看到第一个字符向后移了5,第二个向后移了6,第三个向后移了7,以此类推,很容易想到变异凯撒即每个向后移的位数是前一个加1:str="afZ_r9VYfScOeO_UL^RWUc"k=5foriinstr:p
- buuctf-Quoted-printable
qis_qis
crypto
解压打开:=E9=82=A3=E4=BD=A0=E4=B9=9F=E5=BE=88=E6=A3=92=E5=93=A6刚开始看到这一个字符串,误以为是什么编码特有的格式直到后面发现标题即提示,即Quoted-printable也是一种编码:得到flag:那你也很棒哦
- 138,【5】buuctf web [RootersCTF2019]I_<3_Flask
rzydal
flaskpython后端
进入靶场这段代码是利用Python的类继承和反射机制来尝试执行系统命令读取flag.txt文件内容''.__class__:空字符串对象调用__class__属性,得到str类,即字符串的类型。__class__.__base__:str类的__base__属性指向其基类,在Python中str是新式类,其基类是object。__base__.__subclasses__():object类的__
- 141,【1】buuctf web [SUCTF 2019]EasyWeb
rzydal
web安全
进入靶场代码审计18){die('Oneinchlong,oneinchstrong!');}//使用正则表达式检查$hhh是否包含特定字符集(包括一些常见字符和控制字符等),如果包含则终止脚本执行if(preg_match('/[\x00-0-9A-Za-z\'"\`~_&.,|=[\x7F]+/i',$hhh))die('Trysomethingelse!');//获取$hhh中使用到的字符,
- BUUCTF 逆向工程(reverse)之Java逆向解密
若丶时光破灭
CTF-逆向工程CTF逆向工程
程序员小张不小心弄丢了加密文件用的秘钥,已知还好小张曾经编写了一个秘钥验证算法,聪明的你能帮小张找到秘钥吗?注意:得到的flag请包上flag{}提交下载好题目后,发现它是个以.class为后缀的。所以用JD-GUI打开这个文件。就可以看到Java代码importjava.util.ArrayList;importjava.util.Scanner;publicclassReverse{publi
- BUUCTF——[极客大挑战 2019]PHP
south_1
webphpphp
打开题目,页面上显示说习惯备份,尝试下载备份www.zip,下载后打开查看flag文件里并不是flag,查看其他的在class文件中发现代码,应该是让我们反序列化,给出源代码username=$username;$this->password=$password;}function__wakeup(){$this->username='guest';}function__destruct(){if
- BUUCTF Crypto题目记录
Vigorousy
密码学
MD5e00cf25ad42683b3df678c61f42c6bda进行MD5加密flag{admin1}Url编码%66%6c%61%67%7b%61%6e%64%20%31%3d%31%7dflag{and1=1}看我回旋踢synt{5pq1004q-86n5-46q8-o720-oro5on0417r1}观察已知字符串已经存在flag雏形,猜测为凯撒密码flag{5cd1004d-86a5
- BUUCTF系列 // [极客大挑战 2019] Http
Ga1axy_z
CTF
前言本题知识点:常用HTTP请求头WP打开题目,在页面中没有发现明显的提示,查看网页源码,经搜索后发现一个似乎存在猫腻的网页‘Secret.php’访问该页面,得到第一个提示题目要求我们从‘https://www.Sycsecret.com’进入该页面,故使用burpsuite抓包,在请求头中增加Referer字段即可RefererHTTPReferer是header的一部分,当浏览器向Web服务
- buuctf [极客大挑战 2019]FinalSQL
cng_Capricornus
buuctfweb安全
进入题目,又是这个作者,试试万能密码经过实验,双写什么的都没用。作者说的神秘代码,点进去发现url变了发现并没有什么卵用……正当我没有头绪的时候,我突然看到一句话,审题真的很重要:盲注!这里附上大佬的脚本:importrequestsimporttimeurl="http://def9937b-1746-4f41-98c7-a2b55b95664a.node4.buuoj.cn:81/search
- 八月刷题总结
Uzero.
ctf
2021DASCTFJulyXCBCTF--catflag考察日志文件位置,escapeshellarg函数绕过DASCTFJulyXCBCTF4th--ezrceYAPIMock远程代码执行漏洞BUUCTF--[HarekazeCTF2019]EasyNotesSESSION反序列化BUUCTF--[SWPU2019]Web3伪造Session,生成linux中的软链接BUUCTF--[wate
- [BUUCTF][极客大挑战 2019]PHP
朋克归零膏
CTFphplinuxfirefox
备份根据提示应该就是网站备份文件能被爆破出来随手写了个爆破脚本,基于御剑字典,只供学习使用importrandomimportrequestsimporttimefrommultiprocessingimportPooldefmultiScan(target,file_name,pool_num,delay):local_pool=Pool(pool_num)dirs=get_path_dict(
- BUUCTF [极客大挑战 2019]Secret File 1
THEMIScale
还差一步这道题就出来了在想了在想了别骂了别骂了打开题目后一片黑这个时候根据经验有事没事先ctrl+a安排一下果然有问题在最下方有一个连接打开链接出现一个按钮按他就完事了并没有出来什么用burp拦截后发现提示:secr3t.php打开后提示flag在flag.php中并且给了一串php其中stristr函数不用绕过直接干就完了然后就是啊哈!你找到我了!可是你看不到我QAQ~~~我就在这里这边最后请教
- BUUCTF--[羊城杯 2020]Easyphp2
Uzero.
进入后的页面根据题目提示我们可以知道这是一道PHP代码审计的题所以使用伪协议查看源代码,这里使用的是两次url编码绕过/?file=php://filter/read=convert.quoted-printable-encode/resource=GWHT.php/?file=php://filter/read=convert.%2562%2561%2573%2565%2536%2534-enc
- BUUCTF:[ISITDTU 2019]EasyPHP --- rce 超级异或,,,吐了,,,字符之间异或, 成型的异或payload!!!
Zero_Adam
BUUCTF刷题记录RCEpython
目录:一、自己做:二、学的的三、学习WP1.这里先来个不限制字符个数的关于这个%ff以及异或的事情,咱们好好唠唠1.生成异或中间值的python脚本2.看有字符限制的时候,:参考:末初一、自己做:0xd)die('youaresoclose,omg');eval($_);?>过滤了,不少,我一般碰到rce的题,就看自己的笔记,然后把payload一股脑的网上怼,,,二、学的的正则看不明白的时候,可
- BUUCTF [b01lers2020]little_engine
皮皮蟹!
BUUCTF
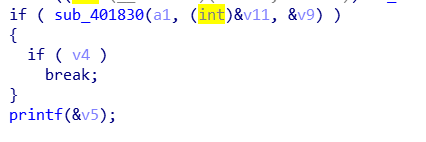
1.拿到文件,进入主函数:这个是动调之前的主函数,开始动调:其中,已知字符串已经给出,为unk_5617CE521220,一共300位:进入加密函数sub_5608DAAB8510:通过多次动态调试,得到了加密算法的逻辑。看判断函数sub_5608DAAB85A0:综上,写出加密脚本:a=[0xE1,0xE
- BUUCTF--[羊城杯 2020]Blackcat
Uzero.
进入后查看源码发现提示都说听听歌了!下载Hei_Mao_Jing_Chang.mp3文件,使用命令stringsHei_Mao_Jing_Chang.mp3查看文件在文末看到一段PHP代码if(empty($_POST['Black-Cat-Sheriff'])||empty($_POST['One-ear'])){die('$clandestine=getenv("clandestine");i
- 84,【8】BUUCTF WEB [羊城杯 2020]Blackcat
rzydal
前端
进入靶场音乐硬控我3分钟回去看源码开始解题运行得到afd556602cf62addfe4132a81b2d62b9db1b6719f83e16cce13f51960f56791b最终组成payload:White-cat-monitor[]=1&Black-Cat-Sheriff=afd556602cf62addfe4132a81b2d62b9db1b6719f83e16cce13f51960f5
- BUUCTF--[HarekazeCTF2019]Avatar Uploader 1
Uzero.
name随便输一个,进入之后看到是让上传头像,这个应该是一个文件上传漏洞接下来分析所给的源码256000){error('Uploadedfileistoolarge.');}//checkfiletype$finfo=finfo_open(FILEINFO_MIME_TYPE);$type=finfo_file($finfo,$_FILES['file']['tmp_name']);finfo_
- BUUCTF_Crypto_[WUSTCTF2020]B@se
qq_58370970
经验分享
给了一个txt文件:从题目可以看出是与base64相关,不难发现是base64的变种,将base64的顺序改变了,但还有4个字符不知道可以写python脚本得到缺失的4个字符代码如下:importstrings='JASGBWcQPRXEFLbCDIlmnHUVKTYZdMovwipatNOefghq56rs****kxyz012789+/'j='ABCDEFGHIJKLMNOPQRSTUVWXY
- BUUCTF--October 2019 Twice SQL Injection
Uzero.
根据题目可以知道这是一个二次注入题注册时把我们sql语句放到username处,登录后即可看到我们想要的信息payload为:username=1'unionselectdatabase()#username=1'unionselectgroup_concat(table_name)frominformation_schema.tableswheretable_schema='ctftrainin
- BUUCTF gyctf_2020_borrowstack
Bengd0u
第一个read的只能溢出0x10字节,也就是刚好覆盖返回地址,如果要ROP地方肯定不够所以栈迁移到bank,在那里ROP之前没遇到过这样的题,怎么迁过去我苦思冥想,最终还是看了wp,,用两个leave来控制rsp和rbp寄存器,太妙了leave是个伪代码,,分解开就是movrsp,rbppoprbp如果把栈构造成这样‘A’*0x60bank_addrleave_addr那么就有两次leavemov
- 2025.1.17—misc—一、黑客帝国 压缩包加密|图片文件格式问题
然然阿然然
“破晓”计划第一阶段训练安全网络安全misc
题目来源:buuctf黑客帝国目录一、解题思路step1:下载文件,查看情况step2:利用脚本转换数据step3:利用ARCHPR破解压缩包密码step4:解压后查看新文件一、解题思路step1:下载文件,查看情况下载附件,发现一堆数据有字母有数字,很像十六进制数据,利用python脚本将这些十六进制数据转换为二进制写入文件。step2:利用脚本转换数据importbinasciihex_dat
- BUUCTF 2021-10-4 Pwn
Ch1lkat
BUUCTFPwnlinuxpwn
文章目录保持手感echo分析EXPPwnme1分析EXPwdb_2018_1st_babyheap分析EXPFSOPhouseoforange_hitcon_2016分析前置知识House_of_orangeFSOPEXPzctf_2016_note3分析EXPgyctf_2020_document分析EXP动态调试复现护网杯_gettingstart分析EXPpicoctf_2018_buffe
- 【BUUCTF】[SWPU2019]神奇的二维码
shane_seven
ctfwp
0x00 刚拿到这题的时候,还以为很简单的样子,结果发现才是一坑接一坑,套娃坑套娃。(出题人友好点儿吧,球球了>_<)0x01 惯例下好文件,是个rar,打开发现是个“神奇的二维码”,直接扫描无果,拿到winhex下查看,发现好几个rar文件 分别手动复制粘贴到新文件,保存,共有四个rar,按照在文件里的位置先后顺序排列 1.rar打开是一行base64编码的字符串,解码后为 打开2.rar,里面
- BUUCTF misc 专题(127)[UTCTF2020]spectogram
tt_npc
安全网络安全音视频
下载下来一个音频,拖到au中没啥发现,也听不出来这题需要用到的一个工具是SonicVisualiser,也是看了大佬的博客才知道的DownloadSonicVisualiser打开是这样的一个界面右键选择Layer->AddSpectrogram能很明显看到flagflag{sp3tr0gr4m0ph0n3}
- BUUCTF msic 专题(128)[ACTF新生赛2020]剑龙
tt_npc
网络安全安全
下载附件,最后解压出来一张jpg,一个无后缀文件和一个pwd.txt先把无后缀文件拖进010查看一下,看不出来什么。看看明显的pwd.txtaaencode解密jjencode与aaencode解密工具-jjencode解密-aaencode解密-在线工具得到welcom3!;再看看图片,welcom3!;岷县是一个密码那么猜测是steghide隐写应该是需要des解密的密文,但是缺个密钥在图片的
- BUUCTF misc 专题(30)webshell后门
tt_npc
python网络安全安全
看题目,又是一道后门查杀的题目,下载了资源以后我们发现是一个rar的文件解压里面的文件后打开D盾进行后门查杀在这里找到了,并根据路径打开所在的文件夹,找到文件根据题目提示,我们在这里找到了md5再根据md5中的pass我们可以找到pass包上flag就是答案了flag{ba8e6c6f35a53933b871480bb9a9545c}
- BUUCTF misc 专题(126)voip
tt_npc
安全网络安全音视频
下载附件,是一个流量包,wireshark打开分析协议分级发现都是RTP流,也不是很懂,上网搜了一下,发现是一种语音通话技术然后wireshark中有电话的选项,可以选中分析rtp流,并且播放播放的音频就是flag,flag{9001IVR}
- BUUCTF misc 专题(11)wireshark
tt_npc
wireshark测试工具网络网络安全
读题,很明显,这是一波带领你收集工具的题目,就是wiresharkWireshark·Downloadhttps://www.wireshark.org/download.html先是对wireshark的下载和安装下载好题目资源以后进行解压,直接拖入到wireshark中由题知,管理员的密码就是答案那么我们直接用http.request.method=="POST"滤出post就行让我们再用TC
- Spring4.1新特性——Spring MVC增强
jinnianshilongnian
spring 4.1
目录
Spring4.1新特性——综述
Spring4.1新特性——Spring核心部分及其他
Spring4.1新特性——Spring缓存框架增强
Spring4.1新特性——异步调用和事件机制的异常处理
Spring4.1新特性——数据库集成测试脚本初始化
Spring4.1新特性——Spring MVC增强
Spring4.1新特性——页面自动化测试框架Spring MVC T
- mysql 性能查询优化
annan211
javasql优化mysql应用服务器
1 时间到底花在哪了?
mysql在执行查询的时候需要执行一系列的子任务,这些子任务包含了整个查询周期最重要的阶段,这其中包含了大量为了
检索数据列到存储引擎的调用以及调用后的数据处理,包括排序、分组等。在完成这些任务的时候,查询需要在不同的地方
花费时间,包括网络、cpu计算、生成统计信息和执行计划、锁等待等。尤其是向底层存储引擎检索数据的调用操作。这些调用需要在内存操
- windows系统配置
cherishLC
windows
删除Hiberfil.sys :使用命令powercfg -h off 关闭休眠功能即可:
http://jingyan.baidu.com/article/f3ad7d0fc0992e09c2345b51.html
类似的还有pagefile.sys
msconfig 配置启动项
shutdown 定时关机
ipconfig 查看网络配置
ipconfig /flushdns
- 人体的排毒时间
Array_06
工作
========================
|| 人体的排毒时间是什么时候?||
========================
转载于:
http://zhidao.baidu.com/link?url=ibaGlicVslAQhVdWWVevU4TMjhiKaNBWCpZ1NS6igCQ78EkNJZFsEjCjl3T5EdXU9SaPg04bh8MbY1bR
- ZooKeeper
cugfy
zookeeper
Zookeeper是一个高性能,分布式的,开源分布式应用协调服务。它提供了简单原始的功能,分布式应用可以基于它实现更高级的服务,比如同步, 配置管理,集群管理,名空间。它被设计为易于编程,使用文件系统目录树作为数据模型。服务端跑在java上,提供java和C的客户端API。 Zookeeper是Google的Chubby一个开源的实现,是高有效和可靠的协同工作系统,Zookeeper能够用来lea
- 网络爬虫的乱码处理
随意而生
爬虫网络
下边简单总结下关于网络爬虫的乱码处理。注意,这里不仅是中文乱码,还包括一些如日文、韩文 、俄文、藏文之类的乱码处理,因为他们的解决方式 是一致的,故在此统一说明。 网络爬虫,有两种选择,一是选择nutch、hetriex,二是自写爬虫,两者在处理乱码时,原理是一致的,但前者处理乱码时,要看懂源码后进行修改才可以,所以要废劲一些;而后者更自由方便,可以在编码处理
- Xcode常用快捷键
张亚雄
xcode
一、总结的常用命令:
隐藏xcode command+h
退出xcode command+q
关闭窗口 command+w
关闭所有窗口 command+option+w
关闭当前
- mongoDB索引操作
adminjun
mongodb索引
一、索引基础: MongoDB的索引几乎与传统的关系型数据库一模一样,这其中也包括一些基本的优化技巧。下面是创建索引的命令: > db.test.ensureIndex({"username":1}) 可以通过下面的名称查看索引是否已经成功建立: &nbs
- 成都软件园实习那些话
aijuans
成都 软件园 实习
无聊之中,翻了一下日志,发现上一篇经历是很久以前的事了,悔过~~
断断续续离开了学校快一年了,习惯了那里一天天的幼稚、成长的环境,到这里有点与世隔绝的感觉。不过还好,那是刚到这里时的想法,现在感觉在这挺好,不管怎么样,最要感谢的还是老师能给这么好的一次催化成长的机会,在这里确实看到了好多好多能想到或想不到的东西。
都说在外面和学校相比最明显的差距就是与人相处比较困难,因为在外面每个人都
- Linux下FTP服务器安装及配置
ayaoxinchao
linuxFTP服务器vsftp
检测是否安装了FTP
[root@localhost ~]# rpm -q vsftpd
如果未安装:package vsftpd is not installed 安装了则显示:vsftpd-2.0.5-28.el5累死的版本信息
安装FTP
运行yum install vsftpd命令,如[root@localhost ~]# yum install vsf
- 使用mongo-java-driver获取文档id和查找文档
BigBird2012
driver
注:本文所有代码都使用的mongo-java-driver实现。
在MongoDB中,一个集合(collection)在概念上就类似我们SQL数据库中的表(Table),这个集合包含了一系列文档(document)。一个DBObject对象表示我们想添加到集合(collection)中的一个文档(document),MongoDB会自动为我们创建的每个文档添加一个id,这个id在
- JSONObject以及json串
bijian1013
jsonJSONObject
一.JAR包简介
要使程序可以运行必须引入JSON-lib包,JSON-lib包同时依赖于以下的JAR包:
1.commons-lang-2.0.jar
2.commons-beanutils-1.7.0.jar
3.commons-collections-3.1.jar
&n
- [Zookeeper学习笔记之三]Zookeeper实例创建和会话建立的异步特性
bit1129
zookeeper
为了说明问题,看个简单的代码,
import org.apache.zookeeper.*;
import java.io.IOException;
import java.util.concurrent.CountDownLatch;
import java.util.concurrent.ThreadLocal
- 【Scala十二】Scala核心六:Trait
bit1129
scala
Traits are a fundamental unit of code reuse in Scala. A trait encapsulates method and field definitions, which can then be reused by mixing them into classes. Unlike class inheritance, in which each c
- weblogic version 10.3破解
ronin47
weblogic
版本:WebLogic Server 10.3
说明:%DOMAIN_HOME%:指WebLogic Server 域(Domain)目录
例如我的做测试的域的根目录 DOMAIN_HOME=D:/Weblogic/Middleware/user_projects/domains/base_domain
1.为了保证操作安全,备份%DOMAIN_HOME%/security/Defa
- 求第n个斐波那契数
BrokenDreams
今天看到群友发的一个问题:写一个小程序打印第n个斐波那契数。
自己试了下,搞了好久。。。基础要加强了。
&nbs
- 读《研磨设计模式》-代码笔记-访问者模式-Visitor
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
import java.util.ArrayList;
import java.util.List;
interface IVisitor {
//第二次分派,Visitor调用Element
void visitConcret
- MatConvNet的excise 3改为网络配置文件形式
cherishLC
matlab
MatConvNet为vlFeat作者写的matlab下的卷积神经网络工具包,可以使用GPU。
主页:
http://www.vlfeat.org/matconvnet/
教程:
http://www.robots.ox.ac.uk/~vgg/practicals/cnn/index.html
注意:需要下载新版的MatConvNet替换掉教程中工具包中的matconvnet:
http
- ZK Timeout再讨论
chenchao051
zookeepertimeouthbase
http://crazyjvm.iteye.com/blog/1693757 文中提到相关超时问题,但是又出现了一个问题,我把min和max都设置成了180000,但是仍然出现了以下的异常信息:
Client session timed out, have not heard from server in 154339ms for sessionid 0x13a3f7732340003
- CASE WHEN 用法介绍
daizj
sqlgroup bycase when
CASE WHEN 用法介绍
1. CASE WHEN 表达式有两种形式
--简单Case函数
CASE sex
WHEN '1' THEN '男'
WHEN '2' THEN '女'
ELSE '其他' END
--Case搜索函数
CASE
WHEN sex = '1' THEN
- PHP技巧汇总:提高PHP性能的53个技巧
dcj3sjt126com
PHP
PHP技巧汇总:提高PHP性能的53个技巧 用单引号代替双引号来包含字符串,这样做会更快一些。因为PHP会在双引号包围的字符串中搜寻变量, 单引号则不会,注意:只有echo能这么做,它是一种可以把多个字符串当作参数的函数译注: PHP手册中说echo是语言结构,不是真正的函数,故把函数加上了双引号)。 1、如果能将类的方法定义成static,就尽量定义成static,它的速度会提升将近4倍
- Yii框架中CGridView的使用方法以及详细示例
dcj3sjt126com
yii
CGridView显示一个数据项的列表中的一个表。
表中的每一行代表一个数据项的数据,和一个列通常代表一个属性的物品(一些列可能对应于复杂的表达式的属性或静态文本)。 CGridView既支持排序和分页的数据项。排序和分页可以在AJAX模式或正常的页面请求。使用CGridView的一个好处是,当用户浏览器禁用JavaScript,排序和分页自动退化普通页面请求和仍然正常运行。
实例代码如下:
- Maven项目打包成可执行Jar文件
dyy_gusi
assembly
Maven项目打包成可执行Jar文件
在使用Maven完成项目以后,如果是需要打包成可执行的Jar文件,我们通过eclipse的导出很麻烦,还得指定入口文件的位置,还得说明依赖的jar包,既然都使用Maven了,很重要的一个目的就是让这些繁琐的操作简单。我们可以通过插件完成这项工作,使用assembly插件。具体使用方式如下:
1、在项目中加入插件的依赖:
<plugin>
- php常见错误
geeksun
PHP
1. kevent() reported that connect() failed (61: Connection refused) while connecting to upstream, client: 127.0.0.1, server: localhost, request: "GET / HTTP/1.1", upstream: "fastc
- 修改linux的用户名
hongtoushizi
linuxchange password
Change Linux Username
更改Linux用户名,需要修改4个系统的文件:
/etc/passwd
/etc/shadow
/etc/group
/etc/gshadow
古老/传统的方法是使用vi去直接修改,但是这有安全隐患(具体可自己搜一下),所以后来改成使用这些命令去代替:
vipw
vipw -s
vigr
vigr -s
具体的操作顺
- 第五章 常用Lua开发库1-redis、mysql、http客户端
jinnianshilongnian
nginxlua
对于开发来说需要有好的生态开发库来辅助我们快速开发,而Lua中也有大多数我们需要的第三方开发库如Redis、Memcached、Mysql、Http客户端、JSON、模板引擎等。
一些常见的Lua库可以在github上搜索,https://github.com/search?utf8=%E2%9C%93&q=lua+resty。
Redis客户端
lua-resty-r
- zkClient 监控机制实现
liyonghui160com
zkClient 监控机制实现
直接使用zk的api实现业务功能比较繁琐。因为要处理session loss,session expire等异常,在发生这些异常后进行重连。又因为ZK的watcher是一次性的,如果要基于wather实现发布/订阅模式,还要自己包装一下,将一次性订阅包装成持久订阅。另外如果要使用抽象级别更高的功能,比如分布式锁,leader选举
- 在Mysql 众多表中查找一个表名或者字段名的 SQL 语句
pda158
mysql
在Mysql 众多表中查找一个表名或者字段名的 SQL 语句:
方法一:SELECT table_name, column_name from information_schema.columns WHERE column_name LIKE 'Name';
方法二:SELECT column_name from information_schema.colum
- 程序员对英语的依赖
Smile.zeng
英语程序猿
1、程序员最基本的技能,至少要能写得出代码,当我们还在为建立类的时候思考用什么单词发牢骚的时候,英语与别人的差距就直接表现出来咯。
2、程序员最起码能认识开发工具里的英语单词,不然怎么知道使用这些开发工具。
3、进阶一点,就是能读懂别人的代码,有利于我们学习人家的思路和技术。
4、写的程序至少能有一定的可读性,至少要人别人能懂吧...
以上一些问题,充分说明了英语对程序猿的重要性。骚年
- Oracle学习笔记(8) 使用PLSQL编写触发器
vipbooks
oraclesql编程活动Access
时间过得真快啊,转眼就到了Oracle学习笔记的最后个章节了,通过前面七章的学习大家应该对Oracle编程有了一定了了解了吧,这东东如果一段时间不用很快就会忘记了,所以我会把自己学习过的东西做好详细的笔记,用到的时候可以随时查找,马上上手!希望这些笔记能对大家有些帮助!
这是第八章的学习笔记,学习完第七章的子程序和包之后