WEP,WPA-PSK,WPA2-PSK握手深入分析2--CCMP(AES)加密和解密
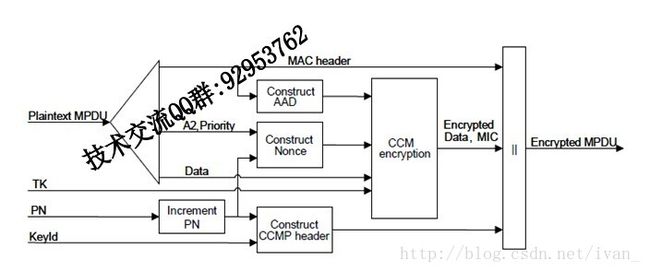
CCMP加密流程:
TA:发送端MAC地址
TK:握手中生产的TK
TSC:发送端维护的序列号计数器
以下是e文描述:
a) Increment the PN, to obtain a fresh PN for each MPDU, so that the PN never repeats for the same
temporal key. Note that retransmitted MPDUs are not modified on retransmission.
b) Use the fields in the MPDU header to construct the additional authentication data (AAD) for CCM.
The CCM algorithm provides integrity protection for the fields included in the AAD. MPDU header
fields that may change when retransmitted are muted by being masked to 0 when calculating the
AAD.
c) Construct the CCM Nonce block from the PN, A2, and the Priority field of the MPDU where A2 is
MPDU Address 2. The Priority field has a reserved value set to 0.
d) Place the new PN and the key identifier into the 8-octet CCMP header.
e) Use the temporal key, AAD, nonce, and MPDU data to form the cipher text and MIC. This step is
known as CCM originator processing.
CCMP解密流程:
以下是e文描述:
CCMP decrypts the payload of a cipher text MPDU and decapsulates a plaintext MPDU using the following
steps:
a) The encrypted MPDU is parsed to construct the AAD and nonce values.
b) The AAD is formed from the MPDU header of the encrypted MPDU.
c) The nonce value is constructed from the A2, PN, and Priority Octet fields (reserved and set to 0).
d) The MIC is extracted for use in the CCM integrity checking.
e) The CCM recipient processing uses the temporal key, AAD, nonce, MIC, and MPDU cipher text
data to recover the MPDU plaintext data as well as to check the integrity of the AAD and MPDU
plaintext data.
f) The received MPDU header and the MPDU plaintext data from the CCM recipient processing may
be concatenated to form a plaintext MPDU.
g) The decryption processing prevents replay of MPDUs by validating that the PN in the MPDU is
greater than the replay counter maintained for the session.
l CCMP数据帧格式
和TKIP基本一致,只是没有TKIP的WEP ICV段
欢迎转载,转载时请保留作者链接,尊重原作者:http://blog.csdn.net/ivan_
wifi技术交流群QQ:92953762