【AIOT】RFID Security
RFID系统本身的安全问题可归纳为隐私和认证两个方面:在隐私方面主要是可追踪性问题,即如何防止攻击者对RFID标签进行任何形式的跟踪; 在认证方面主要是要确保只有合法的阅读器才能够与标签进行交互通信。
0. Security Problem
1. Information transmission
无线信号,存在着被窃取、监听和其他的危险。目前,在信息传输中攻击者使用的主要方式可分为两大类,即主动攻击和被动攻击,主动攻击中最常见的的攻击手段为信道堵塞,而被动攻击主要以监听和窃听技术为主。
2. Data authenticity
攻击者可利用伪造标签替换原有标签,或通过重写合法的RFID标签内容,使用低价物品的标签替换高价物品标签从而非法获益。同时,攻击者也可以通过某种方式隐藏标签,使读写器无法发现该标签,从而成功地实施物品转移。
3. Information and user privacy disclosure
信息泄露是RFID标签发送的信息被暴露,该信息包括标签用户或者识别对象的相关信息,这些信息一般包含一些用户的隐私和其他敏感数据。如RFID物流商品通信信息是公开的,收发双方及物品信息其他任何人都可以获得。当电子标签应用与药品时,很可能暴露药物使用者的病理,隐私侵犯者可以通过扫描服用的药物推断出某人的健康状况。
4. Data confidentiality
目前读写器和标签的通信是不受保护的,未采用安全机制的RFID标签会向邻近的读写器泄露标签内容和一些敏感信息。由于缺乏支持点对点加密和PKI密钥交换的功能,因此在物联网系统的应用过程中,攻击者能够获取并利用RFID标签上的内容。
1. RFID Security Attack
1. Reverse Engineering
RFID tags and reader can be reverse engineered; however, it would take a lot of knowledge about the protocols and features to be successful. Hackers would take apart the chip in order to find out how it works in order to receive the data from the IC.
Purpose: Steal Information and/or Gain Access
2. Power Analysis
Power analysis attacks can be mounted on RFID systems by monitoring the power consumption levels of RFID tags. Researchers stumbled upon this hacking technique when studying the power emission levels in smart cards, especially in the difference in power levels between a correct passcode and an incorrect passcode
Purpose: Steal Information and/or Gain Access
3. Eavesdropping & Replay(窃听,重播)
Eavesdropping, like it sounds, occurs when an unauthorized RFID reader listens to conversations between a tag and reader then obtains important data.
Purpose: Steal Information and/or Gain Access
4. Man-in-the-Middle Attack or Sniffing
Like eavesdropping, the hacker listens for communication between a tag and reader and then intercepts and manipulates the information. The hacker diverts the original signal and then sends false data while pretending to be a normal component in the RFID system. 大部分的RFID标签并不认证RFID阅读器的合法性。
Purpose: Take Down System
5. Denial of Service
A Denial of Service attack is the broad concept of an RFID system failure that is associated with an attack. These attacks are usually physical attacks like jamming the system with noise interference, blocking radio signals, or even removing or disabling RFID tags.
Purpose: Take Down System
6. Cloning&Spoofing(cheat)
Cloning is duplicating data from a pre-existing tag, and spoofing is then using the cloned tag to gain access to a secured area or item. Because the hacker has to know the data on the tag to clone it, this type of attack is mainly seen in asset or asset management operations.
Purpose: Gain Access
7. Viruses
A virus programmed on an RFID tag by an unknown source could cripple an RFID system when the tagged item is read at a facility. When read, the virus would transfer from tag to reader and then to a company’s network and software – bringing down connected computers, RFID components, and networks.
Purpose: Take Down System
8. Tracking
When a user has special tagged objects, an adversary can trace user’s movement using messages transmitted by the tags. In the concrete, when a target tag transmits a response to a reader, an adversary can record the transmitted message and is able to establish a link between the response and the target tag. As the link is established, the adversary is able to know the user’s movement and obtain location history of the user. ???
9. Insert Attack
The attacker inserts the attack command into the normal data stored by the label.
9. Physical Attack
A physical attack sends information that an attacker can physically access and tamper with a label. Physical attacks can take many forms, such as using a micro probe to read modified label content, using X-rays or other rays to destroy label content, and using electromagnetic interference to disrupt communication between labels and readers.
In addition, anyone can easily use a knife or other tool to artificially damage the label, so that the reader can not recognize the label.
EMV chips were made for security purposes and contain complex encryption technology, meaning they do not apply to any part of this article.
Future attacks like these can be mitigated by using encryption methods (when available), chip coatings, filtering methods, and authentication methods or use software or middleware as an additional protective layer.
https://www.atlasrfidstore.com/rfid-insider/7-types-security-attacks-rfid-systems
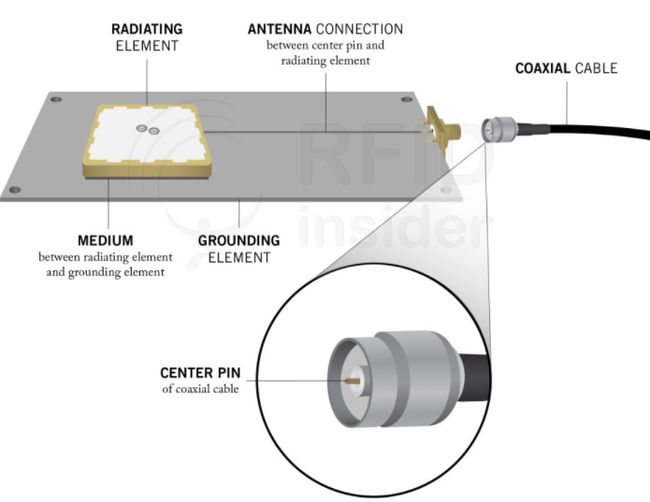
2. RFID Energy Flow
reader to cable, cable to antenna, and antenna to tag (and back) ensures effective energy transfer between the segments.
2.1. Reader to cable
Energy flows out of an electrical outlet as AC power (Alternating Current power) which means electrons periodically reverse directions as they are traveling, enabling the energy to be transmitted longer distances relative to DC power (Direct Current power). A typical RFID reader power supply included with an RFID reader is an AC to DC power converter, changing the alternating current from the outlet to a direct current
Next, the direct current runs through an Oscillator and Phase Locked Loop (PLL) module which then converts the direct current from the power supply to an alternating current at a variable frequency. The variable frequency is determined by a frequency hopping algorithm inside the RFID reader
An RF amplifier determines the power of the signal to be transmitted by the RFID reader (i.e. its transmit power) and amplifies the RF signal to that desired power level.The amplified signal is then passed through an RF Bandpass Filter that eliminates any additional frequencies that are outside of the allowed transmission band. After passing through the Bandpass Filter, the signal is then output to the antenna port and, subsequently, to the coaxial cable through a directional coupler.
2.2. Cable to Antenna
- 在这个过程中,由于信号沿电缆传输时衰减而断电。
2.3. Attenna to Tag&back
The energy received travels through the RFID tag’s antenna and a portion of it is used to activate the chip (i.e. the Integrated Circuit, or IC) and prepare for transmission of data based on commands received from the RFID reader
When the chip is turned on, it modulates the energy with the information stored in the tag (pertinent to the reader’s request) and “reflects” the remaining energy back. This information could be EPC memory, User Memory, or anything programmed on the tag. This reflection of energy back to the antenna is known as backscatter radiation.
3. Communication Methods
3.1. Capacitive Coupling(电容耦合)
flush to 1-2 cm – systems that use capacitive coupling use electric currents instead of the magnetic field in order to couple. Contact to a few centimeters of read range is normal for (LF) or Low Frequency communication because of the need to produce an electric field using electrodes. Because this type of coupling is only effective at such a small proximity, it is not used by very many RFID systems on the market today. One application example is access control/smart cards.
3.2. Close Coupling(紧密耦合)
Readers employed for close coupling using a magnetic field have a winding primary coil and when the tag is in close proximity (0.1 cm – 1 cm) the secondary winding coil of the tag combines with the primary coil via their shared magnetic field in order to communicate. Readers and tags that use electric-field coupling are constructed so that the coupling surfaces when brought together, and inserted parallel, form an electric current for communication.
3.3. Inductive Coupling(电感耦合)
Increasing the amount of loops of wire (coils) in a tag that uses inductive coupling increases the amount of current that would be generated in the tag. In turn, this would increase the power of the transmitted signal from the tag back to the reader.
3.4. Radiative Coupling(辐射耦合)
Electromagnetic waves are sent through the air from the reader antenna to the tag antenna. The energy is received by the tag antenna and a small amount energy is then reflected back to the reader.
4. Application
4.1. Law Enforcement
Using passive RFID in conjunction with real-time data-collection systems will help to ensure safety and protection of an officer’s vehicle and equipment at all times. Currently, the program remains in the pilot stage, but if it provides visibility into the movements of equipment, the program could potentially be implemented in other law enforcement precincts and set a standard for RFID asset tracking.
4.2. Manufacturing
By adhering extremely rugged, orientation insensitive wet inlays on these plastic pallets, the company is able to track them among their pallet pool system between the various regions. These custom RFID tags enable the company to rent and successfully recover their reusable pallets without wasting employee time searching for them.
4.3. Education
tracking books (both loaned and school library books), IT equipment, and other school property enabling them to protect themselves from theft and loss. Attendance tracking is also currently deployed in colleges which will ultimately reduce time to take roll, as well as encourage student attendance.
4.4. Business Environments
inefficiencies in workflow, human error, labor costs, asset loss and theft, and zero visibility into internal assets and inventory. Altogether, RFID asset tracking can improve processes and allow businesses to become a highly effective and efficient functioning business unit.
4.5. Healthcare
The problems hospitals face, such as lost or stolen assets, can leave patients without beds or machines critical for their treatment.
4.5.RTLS
- Transponders – also called Tags, Beacons, or Smart Devices.
- Receivers – also called Readers, Location Sensors, Access Points, Beacons, or Smart Devices.
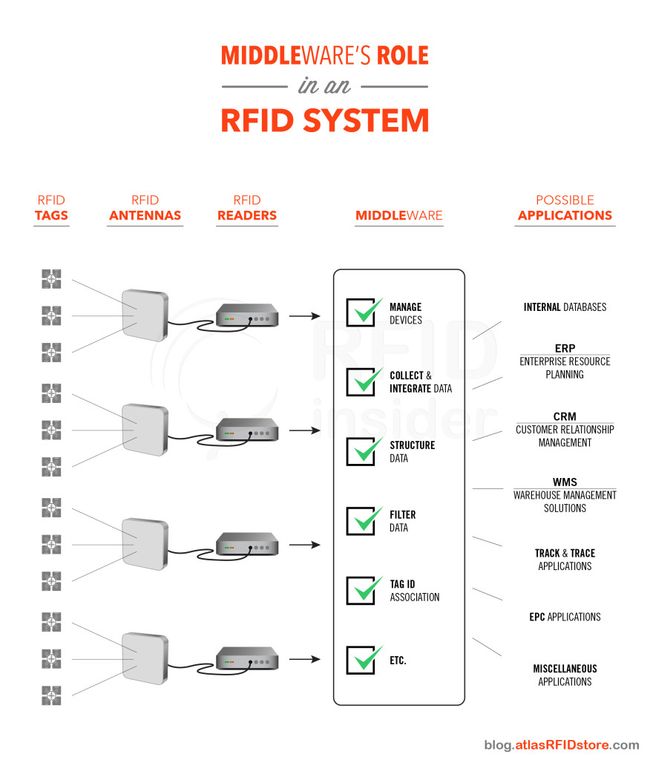
- Software – can be grouped as Firmware, Software, Application Software, or Middleware.
5. Protocal
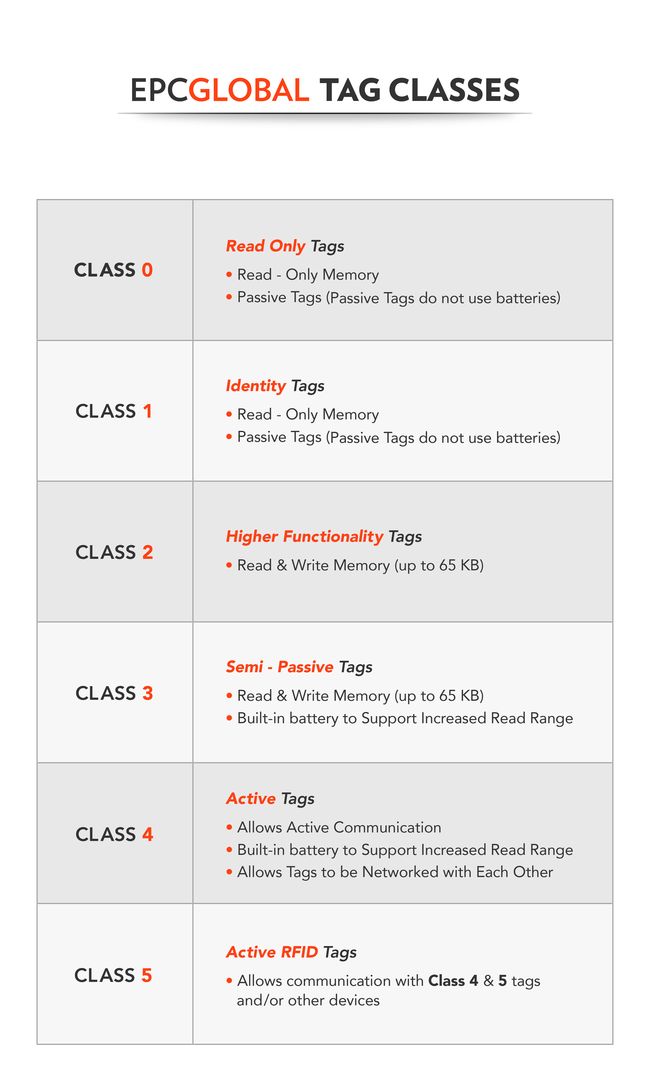
5.1. EPCGlobal Tag Classes
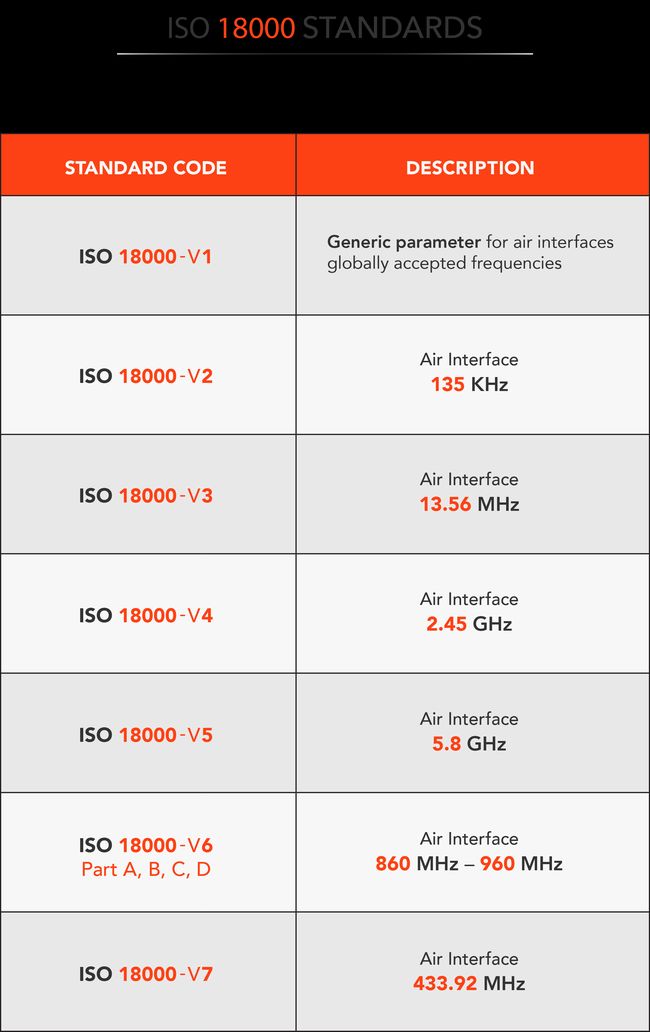
5.2. ISO 18000
5.3. Anti-Collision
If two tags respond at the same time to a reader, the reader is not able to read either due to the collision without collision algorithm;