【OpenSSH】CentOS7.x 上升级OpenSSH到8.3p1版本
一、实验背景
客户请第三方安全公司扫描了下他们的服务器,发现 SSH 存在许多安全漏洞,原因是 CentOS 7.2 使用了一个比较旧的 OpenSSH 版本 v6.6.1,而这些漏洞在新版的 OpenSSH 中均已被修复,所以出于安全考虑,需要升级。
yum 仓库中并没有最新版的 OpenSSH,我们需要自己从官方下载最新的opeenSSh源码包编译制作 rpm 安装包。
因为客户服务器不能连外网,所以还需要将其做成离线升级包。
二、实验环境
操作系统: CentOS7.2 Mininal
serverA 192.168.1.104 模拟开发机,能联网,用于制作离线升级包
serverB 192.168.1.106 模拟客户服务器,不能联网,openSSH相关包及其依赖版本较低
三、实验预期
在severA上完成openSSH相关编译及依赖下载,写成一键升级脚本,拖到serverB上完成openSSH的升级。
OpenSSH源码包官网:http://www.openssh.com
截止目前,最新OpenSSH源码包版本为 openssh-8.3p1.tar.gz
What is the difference between OpenSSH Release and OpenSSH Portable Release?
https://www.openssh.com/portable.html
http://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/
四、实验操作
在serverA
# useradd rpmbuilder
# mkdir -p /home/rpmbuilder/rpmbuild/{SOURCES,SPECS}
# yum -y install vim wget epel-release
# yum -y install rpm-build gcc make
# yum -y install openssl openssl-devel krb5-devel pam-devel libX11-devel xmkmf libXt-devel gtk2-devel
# wget http://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-8.3p1.tar.gz
# wget https://src.fedoraproject.org/lookaside/pkgs/openssh/x11-ssh-askpass-1.2.4.1.tar.gz/8f2e41f3f7eaa8543a2440454637f3c3/x11-ssh-askpass-1.2.4.1.tar.gz
# tar -zxf openssh-8.3p1.tar.gz
# cp ./openssh-8.3p1/contrib/redhat/openssh.spec /home/rpmbuilder/rpmbuild/SPECS/
# cp openssh-8.3p1.tar.gz /home/rpmbuilder/rpmbuild/SOURCES/
# cp x11-ssh-askpass-1.2.4.1.tar.gz /home/rpmbuilder/rpmbuild/SOURCES/
# chown -R rpmbuilder:rpmbuilder /home/rpmbuilder/
# su - rpmbuilder
# cd /home/rpmbuilder/rpmbuild/SPECS/
$ sed -i "s/%global no_gnome_askpass 0/%global no_gnome_askpass 1/g" openssh.spec
$ sed -i "s/%global no_x11_askpass 0/%global no_x11_askpass 1/g" openssh.spec
$ sed -i "s/BuildRequires: openssl-devel >= 1.0.1/#BuildRequires: openssl-devel >= 1.0.1/g" openssh.spec
$ sed -i "s/BuildRequires: openssl-devel < 1.1/#BuildRequires: openssl-devel < 1.1/g" openssh.spec
$ sed -i 's/^%__check_fil/#&/' /usr/lib/rpm/macros
$ rpmbuild -bb openssh.spec
编译完成后记得将编译机上的 /usr/lib/rpm/macros文件改回来:
$ exit
# sed -i 's/^#%__check_files/%__check_files/g' /usr/lib/rpm/macros
编译好后的文件被放在/home/rpmbuilder/rpmbuild/RPMS/x86_64/ 目录下:
# ll /home/rpmbuilder/rpmbuild/RPMS/x86_64/
注:openssh-debuginfo-8.3p1-1.el7.centos.x86_64.rpm 这个包是一个debug包,升级时用不到,需要删除。
将上述操作脚本化:
# cat build.sh
#####################################################
#!/bin/bash
useradd rpmbuilder
mkdir -p /home/rpmbuilder/rpmbuild/{SOURCES,SPECS}
yum -y install vim wget epel-release
yum -y install rpm-build gcc make
yum -y install openssl openssl-devel krb5-devel pam-devel libX11-devel xmkmf libXt-devel gtk2-devel
wget http://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-8.3p1.tar.gz
wget https://src.fedoraproject.org/lookaside/pkgs/openssh/x11-ssh-askpass-1.2.4.1.tar.gz/8f2e41f3f7eaa8543a2440454637f3c3/x11-ssh-askpass-1.2.4.1.tar.gz
tar -zxf openssh-8.3p1.tar.gz
cp ./openssh-8.3p1/contrib/redhat/openssh.spec /home/rpmbuilder/rpmbuild/SPECS/
cp openssh-8.3p1.tar.gz /home/rpmbuilder/rpmbuild/SOURCES/
cp x11-ssh-askpass-1.2.4.1.tar.gz /home/rpmbuilder/rpmbuild/SOURCES/
chown -R rpmbuilder:rpmbuilder /home/rpmbuilder/
su - rpmbuilder
cd /home/rpmbuilder/rpmbuild/SPECS/
sed -i "s/%global no_gnome_askpass 0/%global no_gnome_askpass 1/g" openssh.spec
sed -i "s/%global no_x11_askpass 0/%global no_x11_askpass 1/g" openssh.spec
sed -i "s/BuildRequires: openssl-devel >= 1.0.1/#BuildRequires: openssl-devel >= 1.0.1/g" openssh.spec
sed -i "s/BuildRequires: openssl-devel < 1.1/#BuildRequires: openssl-devel < 1.1/g" openssh.spec
sed -i 's/^%__check_fil/#&/' /usr/lib/rpm/macros
rpmbuild -bb openssh.spec
########################################################
五、在开发机上做openSSH升级测试
在serverA
# cd /home/rpmbuilder/rpmbuild/RPMS/x86_64/
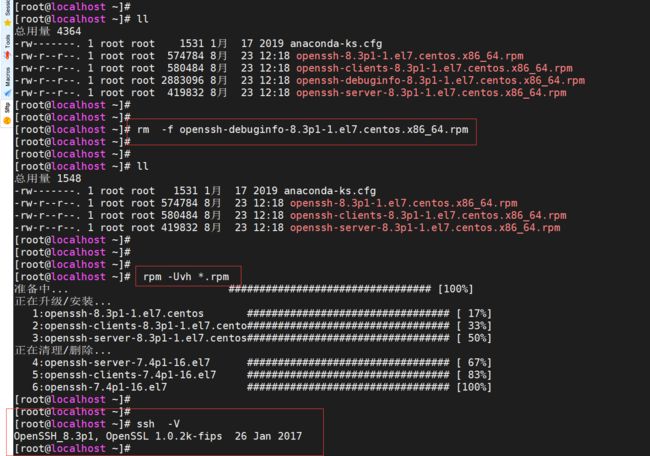
# rm -f openssh-debuginfo-8.3p1-1.el7.centos.x86_64.rpm
# rpm -Uvh *.rpm
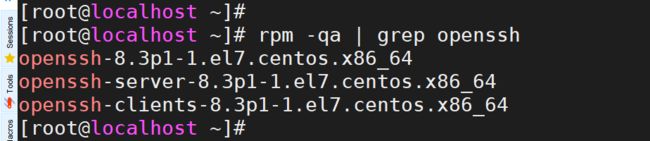
# rpm -qa | grep openssh
本来到此,我们升级就完成了,但是从客户端登陆的时候却失败了!
开始我们以为自己制作的 rpm 包有问题,几经折腾,最后发现还是默认的配置不正确导致的结果。
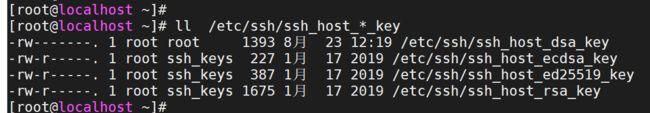
无法用 ssh key 方式登录,默认的 host key 文件授权太大,需要修改 key 文件的权限!
# ll /etc/ssh/ssh_host_*_key
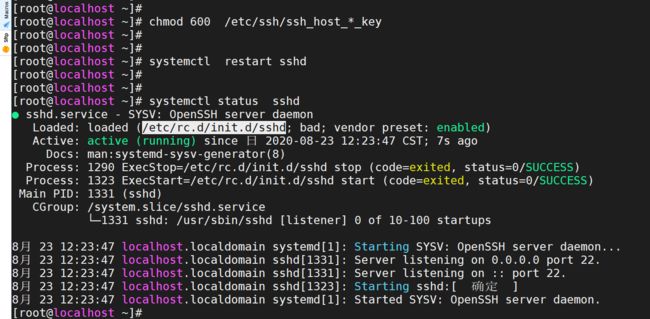
# chmod 600 /etc/ssh/ssh_host_*_key
# ll /etc/ssh/ssh_host_*_key
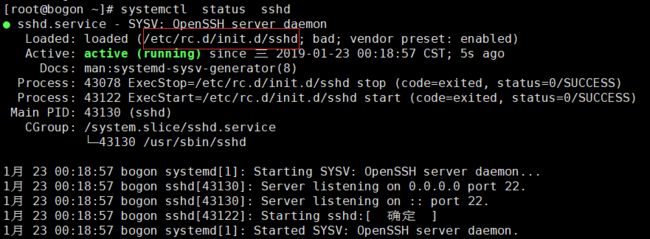
# systemctl restart sshd
# systemctl status sshd
升级完后的openSSH默认不允许用密码方式登录,我们需要更改配置文件:
# cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
# sed -i -e "s/#PasswordAuthentication yes/PasswordAuthentication yes/g" /etc/ssh/sshd_config
# sed -i -e "s/#PermitRootLogin prohibit-password/PermitRootLogin yes/g" /etc/ssh/sshd_config
# sed -i -e "s/#PermitEmptyPasswords no/PermitEmptyPasswords no/g" /etc/ssh/sshd_config
# sed -i -e "s/#UsePAM no/UsePAM yes/g" /etc/ssh/sshd_config
默认的 /etc/pam.d/sshd 中使用了过时的 pam_stack.so 动态库,需要更新:
# cp /etc/pam.d/sshd /etc/pam.d/sshd.bak
# cat > /etc/pam.d/sshd <
#%PAM-1.0
auth required pam_sepermit.so
auth include password-auth
account required pam_nologin.so
account include password-auth
password include password-auth
# pam_selinux.so close should be the first session rule
session required pam_selinux.so close
session required pam_loginuid.so
# pam_selinux.so open should only be followed by sessions to be executed in the user context
session required pam_selinux.so open env_params
session optional pam_keyinit.so force revoke
session include password-auth
EOF
重启ssh服务,查看服务状态:
# systemctl restart sshd
# systemctl enable sshd
# systemctl status sshd
你会发现,升级后的sshd服务,是用的启动脚本,不是/usr/lib/systemd/system/sshd.service文件了。
实际上升级过程中,程序已经将 /usr/lib/systemd/system/sshd.service 删除了,并且添加了服务启动脚本 /etc/init.d/sshd
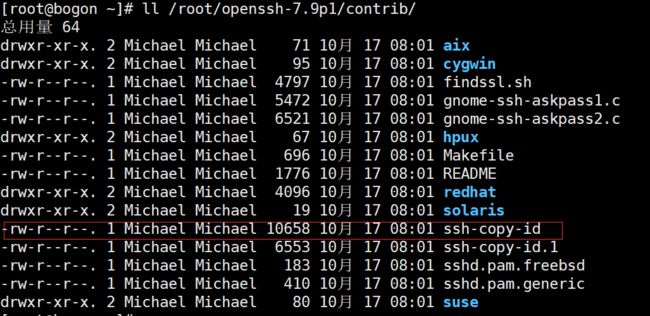
细心的你还会发现,升级完后,我们经常用于做免密登录的公钥拷贝命令 ssh-copy-id也没有了!
其实不是没有了,而是我们需要去解压后源码包拷贝到/usr/bin/目录
# cp /root/openssh-7.9p1/contrib/ssh-copy-id /usr/bin/
# chmod 755 /usr/bin/ssh-copy-id
六、制作离线升级安装包
在serverA
# yum -y install yum-utils createrepo
# mkdir /root/localrepo
# repotrack openssl -p /root/localrepo/
你可能会疑惑:不是找openssh相关包的依赖么,怎么找的是openssl了?
其实从上面安装可以,升级openssh版本并不会缺少依赖,我们们只是需要相应地升级一下openssl的版本:
# rm -f /home/rpmbuilder/rpmbuild/RPMS/x86_64/openssh-debuginfo-8.3p1-1.el7.centos.x86_64.rpm
# cp /home/rpmbuilder/rpmbuild/RPMS/x86_64/*.rpm /root/localrepo
# createrepo -v /root/localrepo
编写离线升级安装脚本:
cat install.sh
######################################################
#!/bin/bash
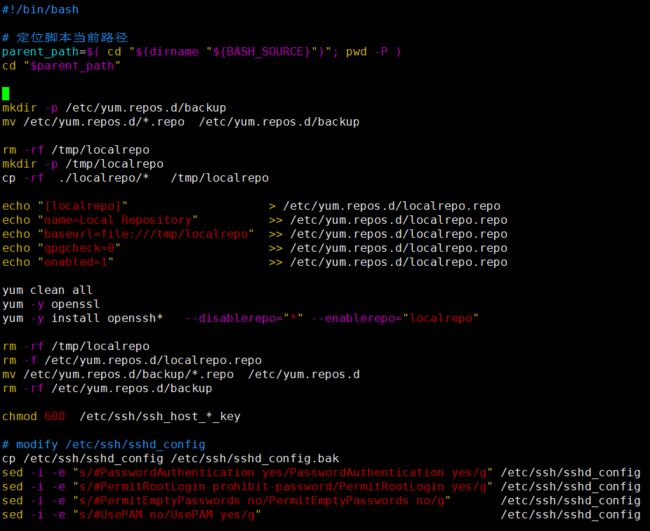
# 定位脚本当前路径
parent_path=$( cd "$(dirname "${BASH_SOURCE}")"; pwd -P )
cd "$parent_path"
mkdir -p /etc/yum.repos.d/backup
mv /etc/yum.repos.d/*.repo /etc/yum.repos.d/backup
rm -rf /tmp/localrepo
mkdir -p /tmp/localrepo
cp -rf ./localrepo/* /tmp/localrepo
echo "[localrepo]" > /etc/yum.repos.d/localrepo.repo
echo "name=Local Repository" >> /etc/yum.repos.d/localrepo.repo
echo "baseurl=file:///tmp/localrepo" >> /etc/yum.repos.d/localrepo.repo
echo "gpgcheck=0" >> /etc/yum.repos.d/localrepo.repo
echo "enabled=1" >> /etc/yum.repos.d/localrepo.repo
yum clean all
yum -y install openssl
yum -y install openssh* --disablerepo="*" --enablerepo="localrepo"
rm -rf /tmp/localrepo
rm -f /etc/yum.repos.d/localrepo.repo
mv /etc/yum.repos.d/backup/*.repo /etc/yum.repos.d
rm -rf /etc/yum.repos.d/backup
chmod 600 /etc/ssh/ssh_host_*_key
# modify /etc/ssh/sshd_config
cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
sed -i -e "s/#PasswordAuthentication yes/PasswordAuthentication yes/g" /etc/ssh/sshd_config
sed -i -e "s/#PermitRootLogin prohibit-password/PermitRootLogin yes/g" /etc/ssh/sshd_config
sed -i -e "s/#PermitEmptyPasswords no/PermitEmptyPasswords no/g" /etc/ssh/sshd_config
sed -i -e "s/#UsePAM no/UsePAM yes/g" /etc/ssh/sshd_config
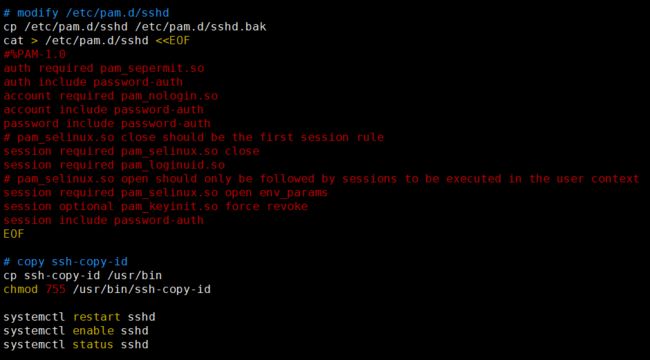
# modify /etc/pam.d/sshd
cp /etc/pam.d/sshd /etc/pam.d/sshd.bak
cat > /etc/pam.d/sshd <
#%PAM-1.0
auth required pam_sepermit.so
auth include password-auth
account required pam_nologin.so
account include password-auth
password include password-auth
# pam_selinux.so close should be the first session rule
session required pam_selinux.so close
session required pam_loginuid.so
# pam_selinux.so open should only be followed by sessions to be executed in the user context
session required pam_selinux.so open env_params
session optional pam_keyinit.so force revoke
session include password-auth
EOF
# copy ssh-copy-id
cp ssh-copy-id /usr/bin
chmod 755 /usr/bin/ssh-copy-id
systemctl restart sshd
systemctl enable sshd
systemctl status sshd
rpm -qa | grep open
systemctl status sshd| grep "Active: active (running)"
if [ $? -eq 0 ]; then
echo -e "\033[32m[INFO] OpenSSH upgraded to 8.3p1 successfully!\033[0m"
else
echo -e "\033[31m[ERROR] OpenSSH upgraded to 8.3p1 faild!\033[0m"
fi
##############################################################
打包离线安装包:
# mkdir /root/opensshUpgrade
# cp install.sh /root/opensshUpgrade
# cp -r lcoalrepo /root/opensshUpgrade
# cp /root/openssh-8.3p1/contrib/ssh-copy-id /root/opensshUpgrade/
# tar openssshUpgrade.tar.gz opensshUpgrade
七、离线安装升级openSSH
将离线升级安装包 openssshUpgrade.tar.gz拷贝到serverB 服务器
# tar -zxf openssshUpgrade.tar.gz
# cd openssshUpgrade
# bash install.sh | tee install.log
# rpm -qa | grep openssl
# rpm -qa | grep openssh
# systemctl status sshd
测试登录
八、参考
rpmbuild 检查未打包 openssh ssh-sk-helper 错误 解决方法
https://bbs.aqzt.com/thread-1079-1-1.html
https://aq2.cn/c/openssh
Upgrade OpenSSH in CentOS 7
https://blog.forhot2000.cn/linux/2017/09/04/upgrade-openssh-in-centos-7.html
编译升级OpenSSH 7.9
https://blog.csdn.net/weixin_42123737/article/details/85283972
Centos 6.5升级openssh到7.9p1
https://blog.csdn.net/qq_25934401/article/details/83419849
openssh升级脚本分享(openssh-7.7p1版)
https://blog.csdn.net/GX_1_11_real/article/details/82152459
Upgrade OpenSSH to 7.7p1 in CentOS 6
https://docs.junyangz.com/upgrade-openssh-to-7.7p1-in-centos-6
createrepo生成仓库元数据,搭建本地yum源
https://www.jianshu.com/p/5cb5af152e75
解决离线安装依赖包的方法
https://www.jianshu.com/p/6f4f9a80a726
升级操作系统OpenSSH及其OpenSSL的正确姿势
https://blog.51cto.com/techsnail/2138927
Openssh版本升级修复漏洞
https://www.cnblogs.com/Dev0ps/p/9629694.html
CentOS7 openssh升级到7.9p1
https://www.jianshu.com/p/220f7fd908b0
OpenSSH-8.0p1
http://www.linuxfromscratch.org/blfs/view/svn/postlfs/openssh.html
CenOS7.2 升级OpenSSH 8.0 升级步骤及排错
https://blog.csdn.net/weixin_40592911/article/details/90519686