docker搭建本地免密仓库、私有仓库registry加密访问控制(身份验证)
前言:
本篇博客是在做了阿里云镜像仓库和加速器的环境
什么是仓库
-
Docker 仓库是用来包含镜像的位置,Docker提供一个注册服
务器(Register)来保存多个仓库,每个仓库又可以包含多个
具备不同tag的镜像。 -
Docker运行中使用的默认仓库是 Docker Hub 公共仓库。
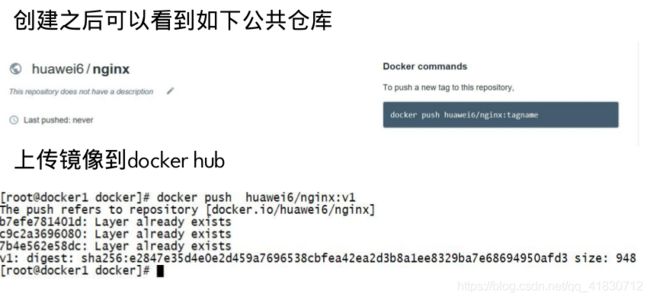
首先在https://cloud.docker.com/网站注册一个账号
docker hub为了区分不同用户的同名镜像,要求镜像的格式是:[username]/xxx.tag
为什么要搭建私有仓库?
docker hub虽然方便,但是还是有限制
- 需要internet连接,速度慢
- 所有人都可以访问
- 由于安全原因企业不允许将镜像放到外网
好消息是docker公司已经将registry开源,我们可以快速构建企业私有仓库
如何搭建私有仓库?
- 第一种用docker命令拉取docker registry,将docker的仓库镜像拉取到本地,在本地构建一个docker仓库,这种方法要自己对仓库进行权限管理,没有图形化页面操作,命令操作比较繁琐,另外在dockertoolbox下搭建私有镜像库出现的问题比较多,建议还是安装linux系统进行搭建。
- 第二种集成harbor,docker-compose可以进行图形化页面仓库以及图形化权限管理,harbor也集成了mysql和log。
我们今天首先给大家讲解一下docker registry私人仓库的搭建和使用!!!
一、实验环境及原理
selinux和firewalld状态为disabled
server1(Docker) 172.25.1.1
Registry工作原理
一次docker pull 或 push背后发生的事情
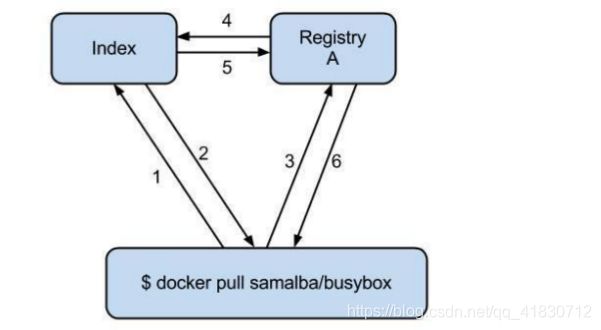
index服务主要提供镜像索引以及用户认证的功能。当下载一个镜像的时候,首先会去index服务上做认证,然后查找镜像所在的registry的地址并放回给docker客户端,docker客户端再从registry下载镜像,在下载过程中 registry会去index校验客户端token的合法性,不同镜像可以保存在不同的registry服务上,其索引信息都放在index服务上。
Docker Registry有三个角色,分别是index、registry和registryclient。
-
index
负责并维护有关用户帐户、镜像的校验以及公共命名空间的信息。
Web UI
元数据存储
认证服务
符号化 -
registry
是镜像和图表的仓库,它不具有本地数据库以及不提供用户认证,
通过Index Auth service的Token的方式进行认证。 -
Registry Client
Docker充当registry客户端来维护推送和拉取,以及客户端的授权。
二、下载registry镜像到docker仓库中,并运行容器
下载镜像
[root@server1 ~]# docker pull registry:2
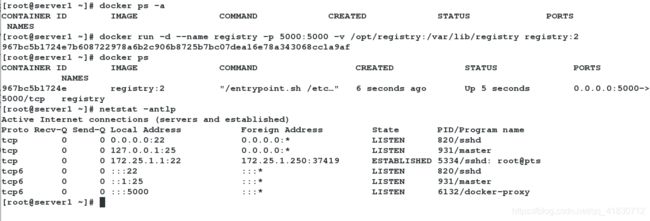
[root@server1 ~]# docker ps -a #查看所有容器
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
[root@server1 ~]# docker run -d --name registry -p 5000:5000 -v /opt/registry:/var/lib/registry registry:2
967bc5b1724e7b608722978a6b2c906b8725b7bc07dea16e78a343068cc1a9af
[root@server1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
967bc5b1724e registry:2 "/entrypoint.sh /etc…" 6 seconds ago Up 5 seconds 0.0.0.0:5000->5000/tcp registry
[root@server1 ~]# netstat -antlp #查看5000端口是否开启
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 820/sshd
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 931/master
tcp 0 0 172.25.1.1:22 172.25.1.250:37419 ESTABLISHED 5334/sshd: root@pts
tcp6 0 0 :::22 :::* LISTEN 820/sshd
tcp6 0 0 ::1:25 :::* LISTEN 931/master
tcp6 0 0 :::5000 :::* LISTEN 6132/docker-proxy
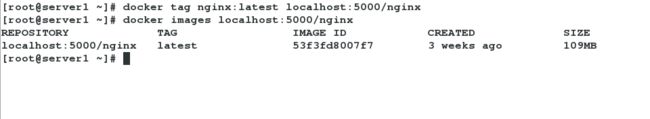
三、上传localhost:5000/nginx(要上传的镜像随便选,但是/前面必须是本地localhost或localhost:5000))
首先设定nginx镜像的标签为localhost:5000/nginx,本地镜像在命名时需要加上仓库的ip和端口
[root@server1 ~]# docker tag nginx:latest localhost:5000/nginx
[root@server1 ~]# docker push localhost:5000/nginx
The push refers to repository [localhost:5000/nginx]
332fa54c5886: Pushed
6ba094226eea: Pushed
6270adb5794c: Pushed
latest: digest: sha256:e770165fef9e36b990882a4083d8ccf5e29e469a8609bb6b2e3b47d9510e2c8d size: 948
我们可以看到/opt/registry目录下有相应的registry私有仓库的镜像数据(分层存储)

四、测试:下载localhost:5000/nginx
在下载之前,
1.我们需要先获取registry仓库有的镜像:
[root@server1 registry]# curl http://localhost:5000/v2/_catalog
{"repositories":["nginx"]}
2.获取某个镜像的标签列表
[root@server1 registry]# curl http://172.25.1.1:5000/v2/nginx/tags/list
{"name":"nginx","tags":["latest"]}
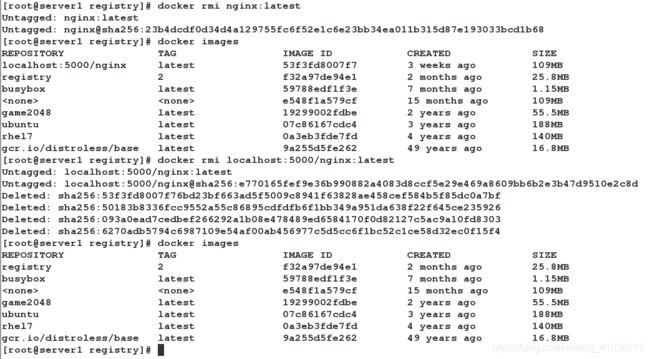
3.我们删除原有的镜像,方便看到效果
4.从我们搭建的私有仓库下载
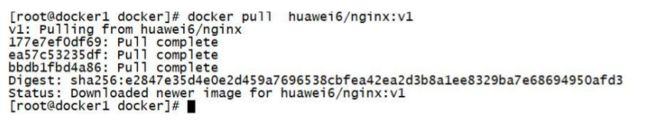
[root@server1 registry]# docker pull localhost:5000/nginx
五、配置私有仓库registry加密访问控制证书
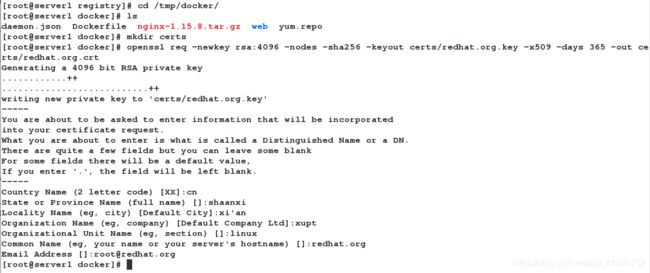
1、创建certs证书,生成服务器私钥
[root@server1 registry]# cd /tmp/docker/
[root@server1 docker]# ls
daemon.json Dockerfile nginx-1.15.8.tar.gz web yum.repo
[root@server1 docker]# mkdir certs #在哪个目录下创建certs都可以,该目录的名字随意给
[root@server1 docker]# openssl req -newkey rsa:4096 -nodes -sha256 -keyout certs/redhat.org.key -x509 -days 365 -out certs/redhat.org.crt
Generating a 4096 bit RSA private key
............++
...........................++
writing new private key to 'certs/redhat.org.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:shaanxi
Locality Name (eg, city) [Default City]:xi'an
Organization Name (eg, company) [Default Company Ltd]:xupt
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:redhat.org #域名(必须上面指定的redhat.org)
Email Address []:[email protected]
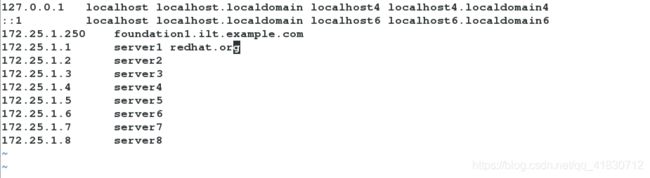
2、写入本地解析
[root@server1 docker]# vim /etc/hosts
3、启动仓库
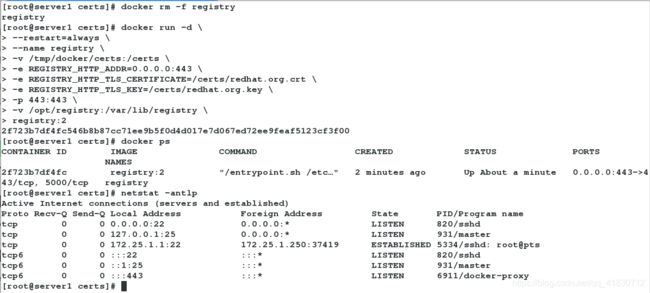
[root@server1 certs]# docker rm -f registry #首先删除我们之前搭建的registry容器
registry
[root@server1 certs]# docker run -d \
> --restart=always \
> --name registry \
> -v /tmp/docker/certs:/certs \
> -e REGISTRY_HTTP_ADDR=0.0.0.0:443 \
> -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/redhat.org.crt \
> -e REGISTRY_HTTP_TLS_KEY=/certs/redhat.org.key \
> -p 443:443 \
> -v /opt/registry:/var/lib/registry \
> registry:2
2f723b7df4fc546b8b87cc71ee9b5f0d4d017e7d067ed72ee9feaf5123cf3f00
参数说明:
-d:后台静默运行容器。
–restart:设置容器重启策略。
–name:命名容器。
-v:挂载信息
-e REGISTRY_HTTP_ADDR:设置仓库主机地址格式。
-e REGISTRY_HTTP_TLS_CERTIFICATE:设置环境变量告诉容器证书的位置。
-e REGISTRY_HTTP_TLS_KEY:设置环境变量告诉容器私钥的位置。
-p:将容器的 443 端口映射到Host主机的 443 端口
4、将certs证书放到我们的docker数据目录
[root@server1 certs]# cd /etc/docker/
[root@server1 docker]# mkdir certs.d
[root@server1 docker]# cd certs.d/
[root@server1 certs.d]# ls
[root@server1 certs.d]# mkdir redhat.org
[root@server1 certs.d]# cd redhat.org/
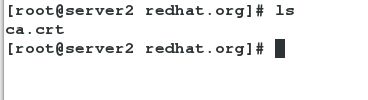
[root@server1 redhat.org]# ls
[root@server1 redhat.org]# cp /tmp/docker/certs/redhat.org.crt ca.crt
[root@server1 redhat.org]# ls
ca.crt
5、上传镜像
修改镜像标签
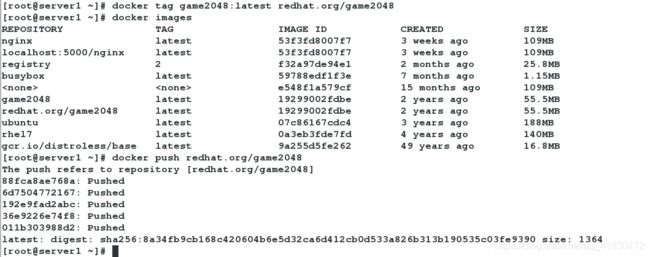
[root@server1 ~]# docker tag game2048:latest redhat.org/game2048
[root@server1 ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest 53f3fd8007f7 3 weeks ago 109MB
localhost:5000/nginx latest 53f3fd8007f7 3 weeks ago 109MB
registry 2 f32a97de94e1 2 months ago 25.8MB
busybox latest 59788edf1f3e 7 months ago 1.15MB
e548f1a579cf 15 months ago 109MB
game2048 latest 19299002fdbe 2 years ago 55.5MB
redhat.org/game2048 latest 19299002fdbe 2 years ago 55.5MB
ubuntu latest 07c86167cdc4 3 years ago 188MB
rhel7 latest 0a3eb3fde7fd 4 years ago 140MB
gcr.io/distroless/base latest 9a255d5fe262 49 years ago 16.8MB
上传镜像
[root@server1 ~]# docker push redhat.org/game2048
The push refers to repository [redhat.org/game2048]
88fca8ae768a: Pushed
6d7504772167: Pushed
192e9fad2abc: Pushed
36e9226e74f8: Pushed
011b303988d2: Pushed
latest: digest: sha256:8a34fb9cb168c420604b6e5d32ca6d412cb0d533a826b313b190535c03fe9390 size: 1364
6、客户端测试(server2):
server2上编写/etc/hosts文件,增加域名解析;获取证书;并进行测试:下载redhat.org/game2048。
1、安装docker
[root@server2 ~]# ls
docker
[root@server2 ~]# cd docker/
[root@server2 docker]# ls
container-selinux-2.21-1.el7.noarch.rpm pigz-2.3.4-1.el7.x86_64.rpm
docker-ce-18.06.1.ce-3.el7.x86_64.rpm policycoreutils-2.5-17.1.el7.x86_64.rpm
libsemanage-2.5-8.el7.x86_64.rpm policycoreutils-python-2.5-17.1.el7.x86_64.rpm
libsemanage-python-2.5-8.el7.x86_64.rpm
[root@server2 docker]# yum install -y *
2、启动docker
[root@server2 docker]# systemctl start docker
3、创建放置证书的目录
[root@server2 docker]# cd /etc/docker/
[root@server2 docker]# ls
key.json
[root@server2 docker]# mkdir certs.d/redhat.org -p
[root@server2 docker]# ls
certs.d key.json
[root@server2 docker]# cd certs.d/redhat.org/
在server1端将证书同步过来
[root@server1 certs]# cd /etc/docker/certs.d/redhat.org/
[root@server1 redhat.org]# ls
ca.crt
[root@server1 redhat.org]# scp ca.crt [email protected]:/etc/docker/certs.d/redhat.org/
vim /etc/hosts
[root@server2 ~]# docker pull redhat.org/game2048
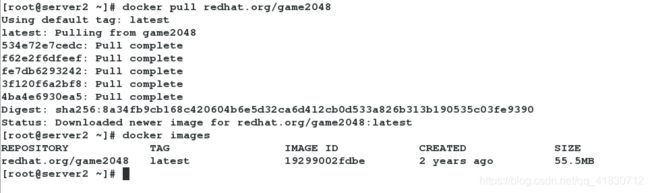
服务端可以上传镜像,也可以下载镜像(这里不再演示,同客户端的pull);客户端如果有证书,当然可以上传镜像(这里不再演示,同服务端的push),也可以下载镜像。
六、 通过基本身份验证实现私有仓库registry加密访问控制
1、创建certs证书,生成服务器私钥(第五步做过了)
2、生成鉴权密码文件
[root@server1 docker]# docker run --rm --entrypoint htpasswd registry:2 -Bbn ztc redhat > auth/htpasswd #用户ztc密码redhat
[root@server1 docker]# cat auth/htpasswd
ztc:$2y$05$2gQVDMKLsmPbnTy8OdzCDuKKNwb9kc5skh9TuDCjXLJAStfCvQhmy
–entrypoint string:覆盖镜像默认的ENTRYPOINT,之前我们说过,ENTRYPOINT是不可以被覆盖的,如果实在要覆盖需要使用此参数
-B:强制密码加密
-b:使用命令行中的密码而不是提示输入密码
-n:不更新加密文件,只将加密后的用户名密码显示在屏幕上
3、删除之前创建的仓库registry(映射到本地主机的443端口),防止冲突。
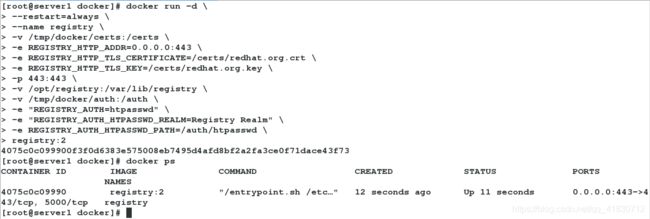
4、启动容器
[root@server1 docker]# docker run -d \
> --restart=always \
> --name registry \
> -v /tmp/docker/certs:/certs \
> -e REGISTRY_HTTP_ADDR=0.0.0.0:443 \
> -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/redhat.org.crt \
> -e REGISTRY_HTTP_TLS_KEY=/certs/redhat.org.key \
> -p 443:443 \
> -v /opt/registry:/var/lib/registry \
> -v /tmp/docker/auth:/auth \
> -e "REGISTRY_AUTH=htpasswd" \
> -e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" \
> -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd \
> registry:2
#参数解释:
REGISTRY_AUTH:验证方式,固定写法
REGISTRY_AUTH_HTPASSWD_REALM:验证域名,固定写法
REGISTRY_AUTH_HTPASSWD_PATH:容器中验证文件的路径,要写文件的路径
5、测试
先登录,在上传:
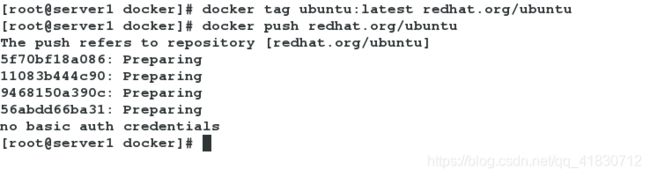
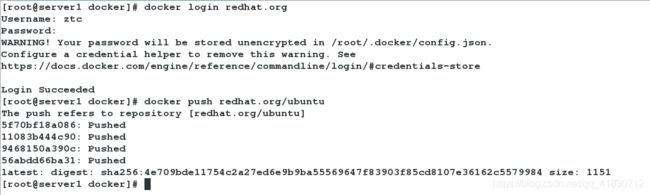
[root@server1 docker]# docker login redhat.org
[root@server1 docker]# docker push redhat.org/ubuntu