防火墙IPSec配置(初学防火墙的小伙伴,带你了解防火墙,每天更新一篇关于防火墙的配置,零基础入手,快速了解防火墙,一起学习,讨论,进步)
1.简介
GRE XXX解决了分支机构互联的问题,但是GRE XXX采用明文传输,无法对数据进行加密,因此安全性无法得到保障。IPsec xxx通过对等体间建立双向安全联盟,形成一个安全互通的IPsec隧道,实现互联网数据的安全传输
2.测试拓扑
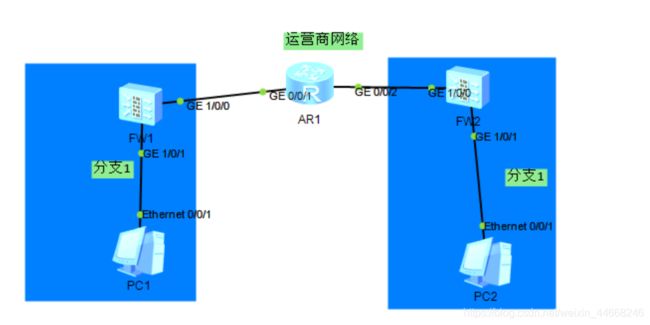
3.测试配置
a.防火墙FW1配置
1.接口配置,用于连接内部网络和外部网络,允许ping以及https访问
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.100.100.2 255.255.255.0
service-manage https permit
service-manage ping permit
ipsec policy ankang
return
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.10.10.1 255.255.255.0
service-manage https permit
service-manage ping permit
return
2.将配置好的接口添加到相应的区域
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
firewall zone dmz
set priority 50
3.配置FW1防火墙安全策略,需要放通trust、untrust区域相互访问,同时还要放通local、untrust区域相互访问
security-policy
rule name 1
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
action permit
rule name 2
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
return
4.配置FW1防火墙acl列表,定义源网络及目标网络
acl number 3000
rule 1 permit ip source 10.10.10.0 0.0.0.255 destination 10.10.20.0 0.0.0.255
5.配置FW1防火墙IKE安全提议及IKE对等体
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm aes-xcbc-96
prf hmac-sha2-256
ike peer 2
exchange-mode auto
pre-shared-key Huawei@123
ike-proposal 1
remote-id-type ip
remote-address 200.200.200.2
6.配置FW1防火墙IPsec安全提议及安全策略及安全策略应用到接口
ipsec proposal 1
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec policy ankang 1 isakmp
security acl 3000
ike-peer 2
proposal 1
interface GigabitEthernet1/0/0
ipsec policy ankang
b.配置FW2防火墙
1.接口配置,用于连接内部和外部网络,运行ping以及https访问及接口添加安全区域
interface GigabitEthernet1/0/0
undo shutdown
ip address 200.200.200.2 255.255.255.0
service-manage https permit
service-manage ping permit
ipsec policy ankang
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.10.20.1 255.255.255.0
service-manage https permit
service-manage ping permit
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
2.配置防火墙安全策略及acl列表
security-policy
rule name 1
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
action permit
rule name 2
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
acl number 3000
rule 1 permit ip source 10.10.20.0 0.0.0.255 destination 10.10.10.0 0.0.0.255
3.配置防火墙FW2防火墙Ike安全提议及IKE对等体
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm aes-xcbc-96
prf hmac-sha2-256
ike peer 2
exchange-mode auto
pre-shared-key Huawei@123
ike-proposal 1
remote-id-type ip
remote-address 100.100.100.2
4.配置FW2防火墙ipsec安全提议及安全策略及策略应该到出接口
ipsec proposal 1
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ipsec policy ankang 1 isakmp
security acl 3000
ike-peer 2
proposal 1
interface GigabitEthernet1/0/0
ipsec policy ankang
4.业务验证
PC2配置10.10.20.100与PC1配置10.10.10.100 互通,说明IPsec XXX隧道建立成功
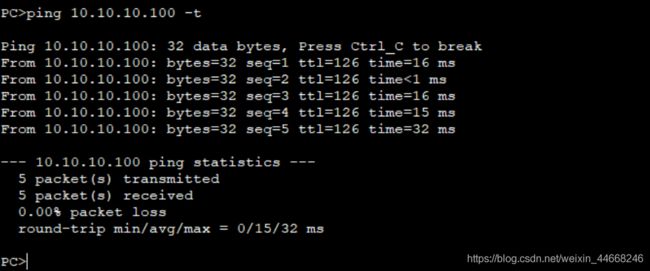
查看FW1及FW2会话
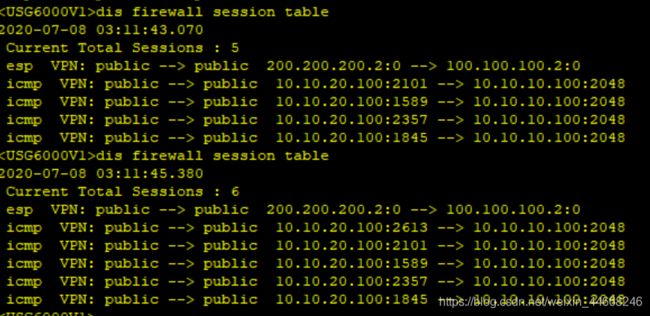
可以看到防火墙已经有XXX会话信息