bWAPP通关记录(A2)
A2 - Broken Auth. & Session Mgmt(失效的身份认证和会话管理)
- Broken Authentication - CAPTCHA Bypassin
- Broken Authentication - Forgotten Function
- Broken Authentication - Insecure Login Forms
- Broken Authentication - Logout Management
- Broken Authentication - Password Attacks
- Broken Authentication - Weak Passwords
- Session Management - Administrative Portals
- Session Management - Cookies (HTTPOnly)
- Session Management - Cookies (Secure)
- Session Management - Session ID in URL
- Session Management - Strong Sessions
Broken Authentication - CAPTCHA Bypassin
验证码绕过,且验证码没有时间限制,所以提交一次验证码后,可以暴力破解用户名和密码
Broken Authentication - Forgotten Function
暴力破解邮箱,上字典往出跑
medium
// Security level MEDIUM
// Mails the secret
if($_COOKIE["security_level"] == "1")
{
if($smtp_server != "")
{
ini_set( "SMTP", $smtp_server);
// Debugging
// $debug = "true";
}
$secret = $row->secret;
// Sends a mail to the user
$subject = "bWAPP - Your Secret";
$sender = $smtp_sender;
$content = "Hello " . ucwords($login) . ",\n\n";
$content.= "Your secret: " . $secret . "\n\n";
$content.= "Greets from bWAPP!";
$status = @mail($email, $subject, $content, "From: $sender");
if($status != true)
{
$message = "An e-mail could not be sent...";
// Debugging
// die("Error: mail was NOT send");
// echo "Mail was NOT send";
}
else
{
$message = "An e-mail with your secret has been sent.";
}
}
$content = "Hello " . ucwords($login) . ",\n\n";
$content.= "Your secret: " . $secret . "\n\n";
$content.= "Greets from bWAPP!";
安全问题会发送邮箱
high
// Security level HIGH
// Mails a reset code
if($_COOKIE["security_level"] == "2")
{
if($smtp_server != "")
{
ini_set( "SMTP", $smtp_server);
// Debugging
// $debug = "true";
}
// 'Reset code' generation
$reset_code = random_string();
$reset_code = hash("sha1", $reset_code, false);
// Debugging
// echo $reset_code;
// Sends a reset mail to the user
$subject = "bWAPP - Change Your Secret";
$server = $_SERVER["HTTP_HOST"];
$sender = $smtp_sender;
$email_enc = urlencode($email);
$content = "Hello " . ucwords($login) . ",\n\n";
$content.= "Click the link to reset and change your secret: http://" . $server . "/bWAPP/secret_change.php?email=" . $email_enc . "&reset_code=" . $reset_code . "\n\n";
$content.= "Greets from bWAPP!";
$status = @mail($email, $subject, $content, "From: $sender");
if($status != true)
{
$message = "An e-mail could not be sent...";
// Debugging
// die("Error: mail was NOT send");
// echo "Mail was NOT send";
}
else
{
$sql = "UPDATE users SET reset_code = '" . $reset_code . "' WHERE email = '" . $email . "'";
// Debugging
// echo $sql;
$recordset = $link->query($sql);
if(!$recordset)
{
die("Error: " . $link->error);
}
// Debugging
// echo "
Affected rows: ";
// printf($link->affected_rows);
$message = "An e-mail with a reset code has been sent.";
}
}
}
else
{
if($_COOKIE["security_level"] != "1" && $_COOKIE["security_level"] != "2")
{
$message = "Invalid user!";
}
else
{
$message = "An e-mail with a reset code has been sent. Yeah right :)";
}
}
}
}
// 'Reset code' generation
$reset_code = random_string();
$reset_code = hash("sha1", $reset_code, false);
会将sha1的随机哈希值发送到邮箱,通过安全问题找回页面重置安全问题
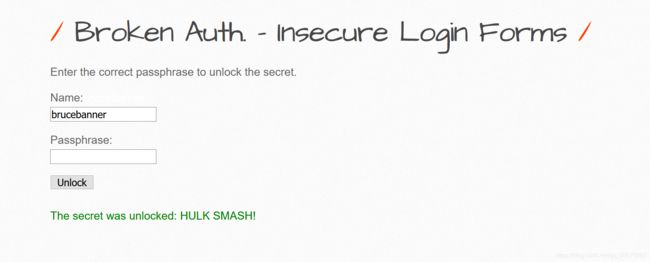
Broken Authentication - Insecure Login Forms

查看页面源码会找见账号tonystark密码I am Iron Man
medium
查看页面源码会发现js脚本

在控制台中复制这段js代码,然后输入secret即会出现密码hulk smash!
high
include("security.php");
include("security_level_check.php");
include("admin/settings.php");
$bugs = file("bugs.txt");
if(isset($_POST["form_bug"]) && isset($_POST["bug"]))
{
$key = $_POST["bug"];
$bug = explode(",", trim($bugs[$key]));
// Debugging
// print_r($bug);
header("Location: " . $bug[1]);
exit;
}
if(isset($_POST["form_security_level"]) && isset($_POST["security_level"]))
{
$security_level_cookie = $_POST["security_level"];
switch($security_level_cookie)
{
case "0" :
$security_level_cookie = "0";
break;
case "1" :
$security_level_cookie = "1";
break;
case "2" :
$security_level_cookie = "2";
break;
default :
$security_level_cookie = "0";
break;
}
if($evil_bee == 1)
{
setcookie("security_level", "666", time()+60*60*24*365, "/", "", false, false);
}
else
{
setcookie("security_level", $security_level_cookie, time()+60*60*24*365, "/", "", false, false);
}
header("Location: ba_insecure_login.php");
exit;
}
if(isset($_COOKIE["security_level"]))
{
switch($_COOKIE["security_level"])
{
case "0" :
$security_level = "low";
break;
case "1" :
$security_level = "medium";
break;
case "2" :
$security_level = "high";
break;
case "666" :
$security_level = "666";
break;
default :
$security_level = "low";
break;
}
}
else
{
$security_level = "not set";
}
$message = "Remember: a bee is a bug...";
if(isset($_POST["form"]))
{
if($_POST["login"] == $login && $_POST["password"] == $password)
{
$message = "Successful login!";
}
else
{
$message = "Invalid credentials!";
}
}
?>
Broken Authentication - Logout Management
但发现Low级别退出登陆后还可以通过浏览器的前进后退功能还是可以返回第一个页面
看源码
switch($_COOKIE["security_level"])
{
case "0" :
// Do nothing
break;
case "1" :
// Destroys the session
session_destroy();
break;
case "2" :
// Unsets all of the session variables
$_SESSION = array();
// Destroys the session
session_destroy();
break;
default :
// Do nothing
break;
}
Low级别退出登录时session没有销毁,账号依然有效
Medium级别退出登录时session已经销毁,需重新登录
High级别退出登录时session先被清空然后销毁,需要重新登录
Broken Authentication - Password Attacks
直接抓包爆破
medium
同样抓包
但查看页面源码后会发现
high
Broken Authentication - Weak Passwords
没说的直接爆破
Session Management - Administrative Portals
switch($_COOKIE["security_level"])
{
case "0" :
if(isset($_GET["admin"]))
{
if($_GET["admin"] == "1")
{
$message = "Cowabunga...You unlocked this page using an URL manipulation.
";
}
else
{
$message="This page is locked.HINT: check the URL...
";
}
}
else
{
header("Location: " . $_SERVER["SCRIPT_NAME"] . "?admin=0");
exit;
}
break;
case "1" :
if((isset($_COOKIE["admin"])))
{
if($_COOKIE["admin"] == "1")
{
$message = "Cowabunga...You unlocked this page using a cookie manipulation.
";
}
else
{
$message="This page is locked.HINT: check the cookies...
";
}
}
else
{
// Sets a cookie 'admin' when there is no cookie detected
setcookie("admin", "0", time()+300, "/", "", false, false);
header("Location: " . $_SERVER["SCRIPT_NAME"]);
exit;
}
break;
case "2" :
// Debugging
// print_r($_SESSION);
if(isset($_SESSION["admin"]) && $_SESSION["admin"] == 1)
{
$message = "Cowabunga...You unlocked this page with a little help from the dba :)
";
}
else
{
$message="This page is locked.HINT: contact your dba...
";
}
break;
if(isset($_GET["admin"]))
{
if($_GET["admin"] == "1")
{
$message = "Cowabunga...You unlocked this page using an URL manipulation.
";
}
if((isset($_COOKIE["admin"])))
{
if($_COOKIE["admin"] == "1")
{
$message = "Cowabunga...You unlocked this page using a cookie manipulation.
";
}
if(isset($_SESSION["admin"]) && $_SESSION["admin"] == 1)
{
$message = "Cowabunga...You unlocked this page with a little help from the dba :)
";
}
对比发现low要在url中修改admin的值为1,medium要在cookie中修改,而high改不了
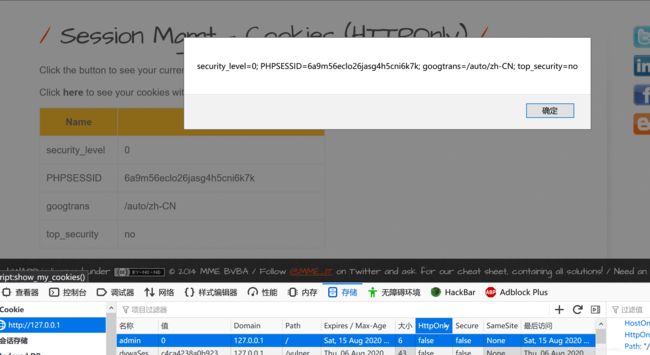
Session Management - Cookies (HTTPOnly)
switch($_COOKIE["security_level"])
{
case "0" :
// The cookie will be available within the entire domain
setcookie("top_security", "no", time()+3600, "/", "", false, false);
break;
case "1" :
// The cookie will be available within the entire domain
// Sets the Http Only flag
setcookie("top_security", "maybe", time()+3600, "/", "", false, true);
break;
case "2" :
// The cookie will be available within the entire domain
// The cookie expires at end of the session
// Sets the Http Only flag
setcookie("top_security", "yes", time()+300, "/", "", false, true);
break;
default :
// The cookie will be available within the entire domain
setcookie("top_security", "no", time()+3600, "/", "", false, false);
break;
}
通过源码可以看出
low
Cookies中httponly字段设置为false 点击 Click Here,本地JS脚本可以直接访问到top_security这个变量值
Cookies中httponly字段设置为true,点击Click Here,本地JS脚本无法访问top_security变量值,通过服务器端是可以直接访问的
Cookies中httponly字段设置为ture,同时缩短了cookies的存在时间,与中级难度的区别在于,调整了Cookie的存在时间,仅有300秒
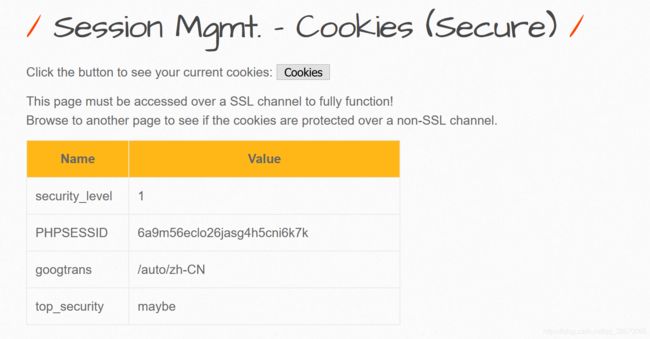
Session Management - Cookies (Secure)
// Deletes the cookies
setcookie("top_security_nossl", "", time()-3600, "/", "", false, false);
setcookie("top_security_ssl", "", time()-3600, "/", "", false, false);
switch($_COOKIE["security_level"])
{
case "0" :
$message.= "Browse to another page to see if the cookies are protected over a non-SSL channel.
";
// The cookie will be available within the entire domain
// Sets the Http Only flag
setcookie("top_security", "no", time()+3600, "/", "", false, true);
break;
case "1" :
$message = "This page must be accessed over a SSL channel to fully function!
";
$message.= "Browse to another page to see if the cookies are protected over a non-SSL channel.
";
// The cookie will be available within the entire domain
// Sets the Http Only flag and the Secure flag
setcookie("top_security", "maybe", time()+3600, "/", "", true, true);
break;
case "2" :
$message = "This page must be accessed over a SSL channel to fully function!
";
$message.= "Browse to another page to see if the cookies are protected over a non-SSL channel.
";
// The cookie will be available within the entire domain
// The cookie expires at end of the session
// Sets the Http Only flag and the Secure flag
setcookie("top_security", "yes", time()+300, "/", "", true, true);
break;
default :
$message.= "Browse to another page to see if the cookies are protected over a non-SSL channel
";
// The cookie will be available within the entire domain
// Sets the Http Only flag
setcookie("top_security", "no", time()+3600, "/", "", false, true);
break;;
}
low
low难度httponly已经设置为true,通过Session Mgmt. - Cookies (HTTPOnly)的页面,点击Click Here,本地JS脚本无法访问top_security
medium&high
SSL下Cookies才会有效,使用SSL后, top_security改为maybe
总结:
低等级只设置了httponly,中等级设置了需要通过https才能设置cookie,高等级则是再缩短了cookie生存期
Session Management - Session ID in URL
switch($_COOKIE["security_level"])
{
case "0" :
if(!(isset($_GET["PHPSESSID"])))
{
$session_id = session_id();
header("Location: smgmt_sessionid_url.php?PHPSESSID=". $session_id );
exit;
}
break;
case "1" :
break;
case "2" :
break;
default :
if(!(isset($_GET["PHPSESSID"])))
{
$session_id = session_id();
header("Location: smgmt_sessionid_url.php?PHPSESSID=". $session_id );
exit;
}
break;
}
low级别暴露了PHPSESSID
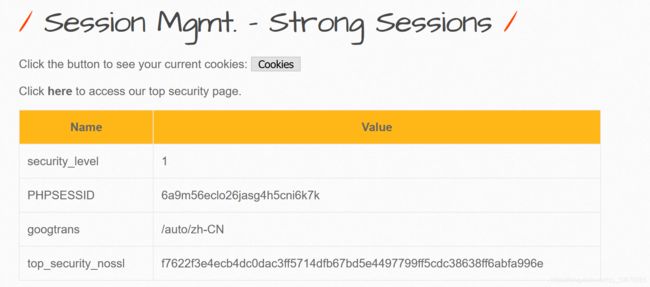
Session Management - Strong Sessions
本题主要是通过观察top_security_nossl和top_security_ssl的情况,来了解Session的安全存储
low
$token = hash("sha256", $token);
top_security_nossl的值使用了HASH处理
high
在非SSL情况下,看不到top_security_ssl的值
改用HTTPS后,可以观察到top_security_nossl值
// Deletes the cookie
setcookie("top_security", "", time()-3600, "/", "", false, false);
switch($_COOKIE["security_level"])
{
case "0" :
$message = "Click here to access our top security page.
";
// Deletes the cookies
setcookie("top_security_nossl", "", time()-3600, "/", "", false, false);
setcookie("top_security_ssl", "", time()-3600, "/", "", false, false);
break;
case "1" :
$message = "Click here to access our top security page.
";
// Deletes the cookie
setcookie("top_security_ssl", "", time()-3600, "/", "", false, false);
if(!isset($_POST["form"]))
{
// Generates a non-SSL secured cookie
// Generates a random token
$token = uniqid(mt_rand(0,100000));
$token = hash("sha256", $token);
$_SESSION["top_security_nossl"] = $token;
// The cookie will be available within the entire domain
// Sets the Http Only flag
setcookie("top_security_nossl", $token, time()+3600, "/", "", false, true);
}
break;
case "2" :
$message = "This page must be accessed over a SSL channel to fully function!
";
$message.= "Click here to access our top security page.
";
// Deletes the cookie
setcookie("top_security_nossl", "", time()-3600, "/", "", false, false);
if(!isset($_POST["form"]))
{
// Generates a non-SSL secured cookie
// Generates a random token
// $token = uniqid(mt_rand(0,100000));
// $token = hash("sha256", $token);
// $_SESSION["top_security_nossl"] = $token;
// The cookie will be available within the entire domain
// Sets the Http Only flag
// setcookie("top_security_nossl", $token, time()+3600, "/", "", false, true);
// Generates a SSL secured cookie
// Generates a random token
$token = uniqid(mt_rand(0,100000));
$token = hash("sha256", $token);
$_SESSION["top_security_ssl"] = $token;
// The cookie will be available within the entire domain
// Sets the Http Only flag and the Secure flag
setcookie("top_security_ssl", $token, time()+3600, "/", "", true, true);
}
break;
default :
$message = "Click here to access our top security page.
";
// Deletes the cookies
setcookie("top_security_nossl", "", time()-3600, "/", "", false, false);
setcookie("top_security_ssl", "", time()-3600, "/", "", false, false);
break;
}