Delegating Computation: Interactive Proofs for Muggles 学习笔记
1. 引言
Goldwasser的等人2008年论文《Delegating Computation: Interactive Proofs for Muggles》,该论文的full version版本见:full verion 版本的 Delegating Computation: Interactive Proofs for Muggles》。
在该论文中,关注的是interactive proofs for tractable languages。要求:
- (honest)prover(又称为“muggle”) 为efficient, run in polynomial time。
- Verifier为super-efficient,run in nearly-linear time。
这种proof sysstem 可用于算力外包:
- server run a computation for a client 的同时,interactively prove the correctness of the result。
- client可verify the result’s correctness in nearly-linear time (而不是run the entire computation itselt)。
本文实现了a public coin interactive proof for any language computable by a log-space uniform boolean circuit with depth d d d and input length n n n:
- Verifier:runs in time ( n + d ) ⋅ p o l y l o g ( n ) (n+d)\cdot polylog(n) (n+d)⋅polylog(n) and space O ( log ( n ) ) O(\log(n)) O(log(n));
- communication complexity: d ⋅ p o l y l o g ( n ) d\cdot polylog(n) d⋅polylog(n);
- Prover:runs in time p o l y ( n ) poly(n) poly(n)。
特别地,对于languages ccomputable by log-space unifrom N C \mathcal{NC} NC (circuits of p o l y l o g ( n ) polylog(n) polylog(n) depth):
- Prover:efficient;
- Verifier:runs in time n ⋅ p o l y l o g ( n ) n\cdot polylog(n) n⋅polylog(n) and space O ( log ( n ) ) O(\log(n)) O(log(n));
- communication complexity: p o l y l o g ( n ) polylog(n) polylog(n)。
目前,针对interactive proofs的大量研究都着力于改进Verifier的complexity in terms of various resouce measures,如:
- time
- space
- depth
- rounds
- randomness
而通常认为Prover端的算力是无限的。如Arthur-Merlin游戏中,认为Merlin(作为Prover)的算力是无限的。
本文则针对真实场景,考虑的是:
- Prover端的算力也是有限的,即将unbounded magical Merlin替换为a “Muggle” prover。“Muggle” 限制为具有probabilistic polynomial-time computation。
- input to the interactive proof来自于outside source,甚至来自于the Verifier。(即Prover无法获取auxiliary secret。)
本文着力于针对polynomial-time computable languages构建interactive proofs,具有:
- super-efficient verifier;【time complexity为linear in the size of the input x x x and poly-logarithmic in the size of the computation of L L L。同时,要求Verifier验证所需的时间和资源要远远小于自己完成相应计算。】
- efficient prover;【time complexity为polynomial in the size of the input。】
- 具有unconditionally soundness;(即对dishonest prover不做任何算力上的假设限制。)
- communication complexity:polylogarithmic in the size of the computation。
1.1 算力外包
interactive proofs的一个真实场景的主要应用为:
delegate polynomial time computations to an untrusted party。
如网络中有多个算力不同的设备,某些设备由于资源有限算力较弱,当任务过于复杂时,算力弱的设备delegate computation to 同网络中算力强的设备。
典型的例子有:
-
1)large scale distributed computing 大规模分布式计算:
“Volunteer Computing” 是指:a server split large computations into small units, send these units to volunteers for processing, and reassemble the result (via a much easier computation)。
相应的例子使用Berkeley Open Infrastructure for Network Computing (BOINC) [5,6] 的SETI@home [3,1],用于扫描是否存在外星人的无线电信号。另一个例子是Great Internet Mersenne Prime Search,用于寻找梅森素数。 -
2)weak peripheral devices 弱外围设备:
越来越多小的、低算力外围设备(如手机、打印机、相机、安全门禁卡、音乐播放器以及传感器)通过网络与强算力的远程计算机连接。假设的一个场景为:a sensor that is presented with an access-card, sends it a ranom challenge, and receives a digitial signature of the random challenge. The computation required to verify the signature involves public-key operations which are too expensive both in time and space for the sensor to run。相反的,sensor可interact with a remote mainframe (delegatee), which can do the computation。
存在的一个主要问题为:
how can a delegator verifiy that the delegatees performed the computation correctly, without running the computation itself?
因此要求delegatee提供a proof that the computation was performed correctly。(这就要求delegator验证proof的时间 要远小于 自己独立完成相应计算的时间;同时要求delegatee生成proof不会引入过多的时间。)
因此,interactive proofs with efficient provers (the delgatees) and super-efficient verifiers (the delegators) provide a natural solution to this problem。
1.2 相关研究
除ineractive proof model之外,针对check the correctness of computations的相关研究有:
- Babai等人[10] 的Holographic proofs model (or alternatively the PCP model)。
- Micali [50] 和 Kilian [45] 的computationally sound argument systems。
以上这些研究类似本文,但是需要super-efficient verifiability, and efficient provability (polynomial time in the non-deterministic time complexity of accepting the input)。
In contrast, our work is in the standard interactive proof model [37] where soundness is achieved unconditionally, making no assumptions on the power of the dishonest prover (as in [50, 45]), nor making assumptions on the non-adaptivity of the dishonest prover(as in [10]).
1.3 low degree extension
1.4 low degree test
Fix a finite field F \mathbb{F} F,假设Verifier想要验证whether a function π : F m → F \pi:\mathbb{F}^m\rightarrow \mathbb{F} π:Fm→F is an m m m-variate polynomial of degree ≤ d \leq d ≤d (think of d d d as significantly smaller than ∣ F ∣ |\mathbb{F}| ∣F∣)。
可将low degree test看成是an interactive proof for π \pi π being close to an m m m-variate polynomial of degree ≤ d \leq d ≤d。该proof应short (即size ≤ p o l y ( ∣ F ∣ , m ) \leq poly(|\mathbb{F}|,m) ≤poly(∣F∣,m))。Verifier 仅需要oracle access to π \pi π,允许query π \pi π at only a few points (也就是 only one point)。
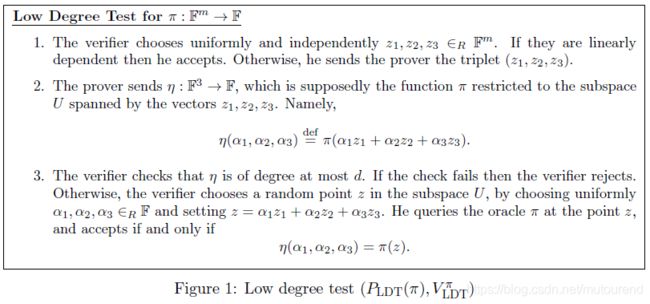
1.5 interactive sum-check protocol
Fix a finite field F \mathbb{F} F and a subset H ⊆ F H\subseteq \mathbb{F} H⊆F。
在sum-check protocol中,a (not necessarily efficient) prover 的输入为:
an m m m-variate polynomial f : F m → F f:\mathbb{F}^m\rightarrow \mathbb{F} f:Fm→F of degree ≤ d \leq d ≤d in each variable (think of d d d as significantly smaller than ∣ F ∣ |\mathbb{F}| ∣F∣)。
Prover的目标是证明:
∑ z ∈ H m f ( z ) = β \sum_{z\in H^m}f(z)=\beta ∑z∈Hmf(z)=β
for some constant β ∈ F \beta\in\mathbb{F} β∈F。
Verifier仅具有oracle access to f f f,以及constant β ∈ F \beta\in\mathbb{F} β∈F,要求Verifier为efficient in both its running time 和 its number of oracle queries。

2. 主要技术点
假设circuit C C C为a depth d d d arithmetic circuit in a layered form where there are as many layers as the depth of the circuit。【Every circuit can be converted into this format by at most squaring its size and not changing the depth。】
本文采用interactive protocol来实现(parallelized)computation of C C C, layer by layer, from the output layer to the input layer,numbering the layers in increasing order from the top (output) of the circuit to the bottom (input) of the circuit。【如layer 0 0 0对应为output layer,layer d d d为input layer。】
The verifier has no time to compute points in the low-degree extension of the computation on x x x in layer i i i: this is the low-degree extension (a high distance encoding) of the vector of values that the gates in the circuit’s i i i-th layer take on input x x x,and to compute it one needs to actually evaluate C C C, which we want to avoid!
因此,the low-degree extension of the i i i-th layer, 将由Prover提供。为了防止Prover作弊,在each phase of the protocol,允许Verifier能 reduce, verification of a single point in the low-degree extension of an advanced step (layer) in parallel computation, to, verification of a single point in the low-degree extension of the previous step (layer)。整个过程将repeated iteratively (for as many layers as the circuit has),直到the verification has been reduced to verifying a single poin in the extension of the first step in the computation。在the first step of the computation (即the input layer), the only information “computed” is the input x x x, the verifier can compute the low degree extension of the input x x x on its own。
根据以上描述,关键点在于:如何reduce, verification of a single point in the low degree extension of a layer in the circuit, to, verification of a single point in the low degree extension of the previous layer。
观察可发现:
every point in the low degree extension (LDE) of the advanced layer (layer i i i) is a linear combination or a weighted sum, of the values of that layer’s gates。假设circuit具有fan-in 2,则可 express the value of each gate g g g in layer i i i as a sum,over all possible pairs ( k , l ) (k,l) (k,l) of gates in the layer below (layer i + 1 i+1 i+1), of some (low degree) function of the values of the gates k k k and l l l,as well as a predicate that indicates whether those gates are indeed the “children” of gate g g g。
Arithmetizing this entire sum of sums,可运行sum-check protocol来verify the value of one point in the low-degree extension of layer i i i。
为了简化,可假设现在Verifier具有access to (a low-degree extension of) the predicate that says wheter a pair of gates ( g , l ) (g,l) (g,l) are the children of the gate g g g。然后(modulo many details)at the end of this sum-check protocol the verifier only needs to verify the values of a pair of points in the LDE of layer i + 1 i+1 i+1。但是这仍然不够,我们需要reduce, the verification of a single point in the LDE of layer i i i, to, the verification of a single point in layer i + 1 i+1 i+1 and not of a pair of points。因此,最终需要使用an interactive protocol来reduce, verifying two points in the LDE of layer i + 1 i+1 i+1, to, verifying just one。
接下来的关键问题在于:
how the verifier gains access to such LDE’s of predicates that decide whether circuit gates are connected, without looking at the entire circuit (as the circuit itself is much larger than the verifier’s running time)。
The verifier’s running time in each of these phases is polylogarithmic in the circuit size。在最后一步,computing one point in the low-degree extension of the input requires only nearly-linear time, indepedent of the rest of the circuit。
另一个重要的点是,the Verifier不需要记住anything about earlier phases of the verification, at any point in time it only needs to remember what is being verified about a certain point in the computation,这样就可以大量解压Verfier的空间。
而对于Prover来说,其running time的节约在于the prover does not need to arithmetize the entire computation, but rather proves statements about one (parallel) computation step at a time。
剩下的问题为:
how the verifier can compute (a low-degree extensions of) a predicate that decides whether circuit gates are connected, without looking at the entire circuit。
为了解决该问题,约定了circuit的uniformity一致性,这样就有非常short implicit representation。
类似地,在[11]中,相应的computation reduce为an (exponential) 3SAT formula, and the (polynomial-time) verifier needs to access a low-degree extension of a function computing which variables are in a specific clause of the formula。【利用了Cook-Levin reduction transform。】
而本文无法使用Cook-Levin reduction transform,因为在本文中要求transform unifrom computations into low-depth circuits without blowing up the input size。
为了解决该问题,本文:
- 1)检查low space computations,如,uniform log-space Turing Machines (deterministic or non-deterministic)。A log-space machine can be transformed into a family of boolean circuits with poly-logarithmic depth and polynomial size。在这样的circuits簇中,it is possible to compute the predicate that decides whether circuit gates are connected in poly-logarithmic time and constant ( A C 0 \mathcal{AC}^0 AC0) depth。This computation can itself be arithmetized, which allows the verifier to compute a low-degree extension of the predicate in poly-logarithmic time。然后就可obtain an interactive proof with an efficient prover and super-efficient verifier for any L \mathcal{L} L or N L \mathcal{NL} NL computation。
- 2)对于non-uniform circuits,the only “heavy” computation that the verifier needs to do is computing low-degree extensions of the predicate that decides whether circuit gates are connected。The locations at which the verifier needs to access this predicate are only a function of its own randomness (and not of the input or the prover’s responses)。
这就意味着,对于completely non-uniform circuit, the verifier can compute these evaluations of the predicate’s low-degree extension off-line on its own,without knowing the input or interacting with the prover。该off-line phase requires run-time that is proportional to the circuit size。Once the input is specified, the verifier, who has the (poly-logarithmically many) evaluations of the predicate’s low degree extension that it computed off-line, can run the interactive proof on-line with the prover。
The verifier will be super efficient in this on-line phase。
3. a bare-bones protocol
3.1 相关约定
针对circuit C : { 0 , 1 } n → { 0 , 1 } C:\{0,1\}^n\rightarrow \{0,1\} C:{ 0,1}n→{ 0,1} of size S S S and of depth d ≤ S d\leq S d≤S,and a string x ∈ { 0 , 1 } n x\in\{0,1\}^n x∈{ 0,1}n, provess to a verifier that C ( x ) = 0 C(x)=0 C(x)=0。
C C C为a layered arithmetic circuit of fan-in 2 (over the gates × \times × and + + + and the field F \mathbb{F} F),且all its layers are of size S S S。【只有input layer 例外,input layer的size为 n n n。】A depth- d d d layered circuit,其gates会切分为 ( d + 1 ) (d+1) (d+1)层,其中 0 0 0 layer为the output layer (由output gate组成), d d d layer为the input layer(由input gates组成)。
对于layered circuit,wires仅可连接相邻层的gates,即,the output wire of a gate in layer i i i can only be the input wire for a gate in layer ( i − 1 ) (i-1) (i−1)。为了简单起见,假设 C C C中的所有layers都具有相同的size(except for the input layer),假设the size of each layer is S S S。
任意的circuit (of size S S S) 都可tranform为one with exactly S S S gates in each level, by adding < S < S <S dummy gates (that are the constant zero) to each layer。
特别地,会add dummy gates to the output layer, 使得the transformed circuit C ′ : F n → F s C':\mathbb{F}^n\rightarrow \mathbb{F}^s C′:Fn→Fs satisfies that for every ( x 1 , ⋯ , x n ) ∈ F n (x_1,\cdots,x_n)\in\mathbb{F}^n (x1,⋯,xn)∈Fn:
C ′ ( x 1 , ⋯ , x n ) = ( C ( x 1 , ⋯ , x n ) , 0 , ⋯ , 0 ) C'(x_1,\cdots,x_n)=(C(x_1,\cdots,x_n),0,\cdots,0) C′(x1,⋯,xn)=(C(x1,⋯,xn),0,⋯,0)
这会increase the size of the circuit by at most a quadratic factor,但是不会增加circuit的depth。
【可将任意的arithmetic circuit 转换为 layered arithmetic circuit of fan-in 2,代价是increase the size of the circuit by at most a polynomial factor and increase the depth of the circuit by at most a factor of O ( log ( S ) ) O(\log(S)) O(log(S))。】
对于任意的 0 ≤ i ≤ d − 1 0\leq i\leq d-1 0≤i≤d−1,label the S S S gates in the i i i-th layer of C C C by values in { g i , 0 , g i , 1 , ⋯ , g i , S − 1 } \{g_{i,0},g_{i,1},\cdots,g_{i,S-1}\} { gi,0,gi,1,⋯,gi,S−1}。【the n n n gates in the d d d-th layer of C C C(即,the input layer) 表示为 ( g d , 0 , g d , 1 , ⋯ , g d , n − 1 ) (g_{d,0},g_{d,1},\cdots,g_{d,n-1}) (gd,0,gd,1,⋯,gd,n−1)。】
对于任意的 i ∈ [ d − 1 ] i\in[d-1] i∈[d−1],associate with C C C two functions a d d i , m u l t i : H m × H m × H m → { 0 , 1 } add_i,mult_i:\mathbb{H}^m\times\mathbb{H}^m\times\mathbb{H}^m\rightarrow \{0,1\} addi,multi:Hm×Hm×Hm→{ 0,1}【即 a d d i , m u l t i : { 0 , 1 , S − 1 } 3 → { 0 , 1 } add_i,mult_i:\{0,1,S-1\}^3\rightarrow \{0,1\} addi,multi:{ 0,1,S−1}3→{ 0,1}】。这两个function的输入为3 gate labels ( j 1 , j 2 , j 3 ) (j_1,j_2,j_3) (j1,j2,j3),输出为 1 1 1当且仅当the gate j 1 j_1 j1 in layer i − 1 i-1 i−1 is the addition or multiplication (respectively) of gates ( j 2 , j 3 ) (j_2,j_3) (j2,j3) in layer i i i,否则输出为 0 0 0。【注意,gate labels in [ S ] [S] [S] are represented as vectors in H m \mathbb{H}^m Hm】
即有:

-
对于任意的 i ∈ [ d − 1 ] i\in[d-1] i∈[d−1],设置 a d d ~ i , m u l t ~ i : F 3 m → F \tilde{add}_i,\tilde{mult}_i:\mathbb{F}^{3m}\rightarrow \mathbb{F} add~i,mult~i:F3m→F 为the low-degree extensions of a d d i , m u l t i add_i,mult_i addi,multi with respect to H , F , m \mathbb{H},\mathbb{F},m H,F,m, of degree δ \delta δ in each variable (recall δ < ∣ F ∣ \delta<|\mathbb{F}| δ<∣F∣)。
对于每一个 z 1 , z 2 , z 3 ∈ H m z_1,z_2,z_3\in\mathbb{H}^m z1,z2,z3∈Hm,使得 α ( z 1 ) , α ( z 2 ) , α ( z 3 ) ≤ S − 1 \alpha(z_1),\alpha(z_2),\alpha(z_3)\leq S-1 α(z1),α(z2),α(z3)≤S−1(其中 α : H m → { 0 , 1 , ⋯ , ∣ H ∣ m − 1 } \alpha: \mathbb{H}^m\rightarrow \{0,1,\cdots,|\mathbb{H}|^m-1\} α:Hm→{ 0,1,⋯,∣H∣m−1} is the lexicographic order。), a d d ~ i , m u l t ~ i \tilde{add}_i,\tilde{mult}_i add~i,mult~i与 a d d i , m u l t i add_i,mult_i addi,multi的关系为:
a d d ~ i ( z 1 , z 2 , z 3 ) = a d d i ( α ( z 1 ) , α ( z 2 ) , α ( z 3 ) ) \tilde{add}_i(z_1,z_2,z_3)=add_i(\alpha(z_1),\alpha(z_2),\alpha(z_3)) add~i(z1,z2,z3)=addi(α(z1),α(z2),α(z3))
m u l t ~ i ( z 1 , z 2 , z 3 ) = m u l t i ( α ( z 1 ) , α ( z 2 ) , α ( z 3 ) ) \tilde{mult}_i(z_1,z_2,z_3)=mult_i(\alpha(z_1),\alpha(z_2),\alpha(z_3)) mult~i(z1,z2,z3)=multi(α(z1),α(z2),α(z3))
若 z 1 , z 2 , z 3 ∈ H m z_1,z_2,z_3\in\mathbb{H}^m z1,z2,z3∈Hm,但是其中的某个值 α ( z j ) > S − 1 \alpha(z_j)>S-1 α(zj)>S−1,则 a d d ~ i , m u l t ~ i \tilde{add}_i,\tilde{mult}_i add~i,mult~i均返回0值。 -
对于 i = d i=d i=d,即input layer,有:
a d d ~ d , m u l t ~ d : F m × F m ′ × F m ′ → F \tilde{add}_d,\tilde{mult}_d:\mathbb{F}^m\times \mathbb{F}^{m'}\times \mathbb{F}^{m'}\rightarrow \mathbb{F} add~d,mult~d:Fm×Fm′×Fm′→F
为multivariate polynomials of degree ≤ δ \leq \delta ≤δ in each variable。
其中每一个 z 1 ∈ H m z_1\in\mathbb{H}^m z1∈Hm应满足 α ( z 1 ) ≤ S − 1 \alpha(z_1)\leq S-1 α(z1)≤S−1;每一个 z 2 , z 3 ∈ H m ′ z_2,z_3\in\mathbb{H}^{m'} z2,z3∈Hm′应满足 α ( z 2 ) , α ( z 3 ) ≤ n − 1 \alpha(z_2),\alpha(z_3)\leq n-1 α(z2),α(z3)≤n−1,有:
a d d ~ d ( z 1 , z 2 , z 3 ) = a d d d ( α ( z 1 ) , α ( z 2 ) , α ( z 3 ) ) \tilde{add}_d(z_1,z_2,z_3)=add_d(\alpha(z_1),\alpha(z_2),\alpha(z_3)) add~d(z1,z2,z3)=addd(α(z1),α(z2),α(z3))
m u l t ~ d ( z 1 , z 2 , z 3 ) = m u l t d ( α ( z 1 ) , α ( z 2 ) , α ( z 3 ) ) \tilde{mult}_d(z_1,z_2,z_3)=mult_d(\alpha(z_1),\alpha(z_2),\alpha(z_3)) mult~d(z1,z2,z3)=multd(α(z1),α(z2),α(z3))
若 α ( z 1 ) > S − 1 \alpha(z_1)>S-1 α(z1)>S−1 或 α ( z 2 ) > n − 1 \alpha(z_2)>n-1 α(z2)>n−1 或 α ( z 3 ) > n − 1 \alpha(z_3)>n-1 α(z3)>n−1,则 a d d ~ d , m u l t ~ d \tilde{add}_d,\tilde{mult}_d add~d,mult~d均返回0值。
注意:
{ a d d i , m u l t i } i ∈ [ d ] \{add_i,mult_i\}_{i\in[d]} { addi,multi}i∈[d]可唯一确定circuit C C C,而extensions { a d d ~ i , m u l t ~ i } i ∈ [ d ] \{\tilde{add}_i,\tilde{mult}_i\}_{i\in[d]} { add~i,mult~i}i∈[d] 无法唯一确定circuit C C C。
对于 δ > ∣ H ∣ − 1 \delta>|\mathbb{H}|-1 δ>∣H∣−1的情况下,有很多符合条件的extensions { a d d ~ i , m u l t ~ i } i ∈ [ d ] \{\tilde{add}_i,\tilde{mult}_i\}_{i\in[d]} { add~i,mult~i}i∈[d] 。
定义oracle F \mathcal{F} F accessed by the prover and verifier in the bare-bones protocol:
F = { a d d ~ i , m u l t ~ i } i ∈ [ d ] \mathcal{F}=\{\tilde{add}_i,\tilde{mult}_i\}_{i\in[d]} F={ add~i,mult~i}i∈[d]
其中,Prover和Verifier可access a d d ~ i \tilde{add}_i add~i or m u l t ~ i \tilde{mult}_i mult~i by querying F \mathcal{F} F with the proper i i i, a bit specifying a d d ~ \tilde{add} add~ or m u l t ~ \tilde{mult} mult~, and an input in ( F m ) 3 (\mathbb{F}^m)^3 (Fm)3 or (for i = d i=d i=d) in F m × ( F m ′ ) 2 \mathbb{F}^m\times (\mathbb{F}^{m'})^2 Fm×(Fm′)2。
在bare-bones protocol中,假设the verifier 具有oracle access to the functions a d d ~ i , m u l t ~ i \tilde{add}_i,\tilde{mult}_i add~i,mult~i for every i ∈ [ d − 1 ] i\in[d-1] i∈[d−1]。
最后,对于任意的 0 ≤ i ≤ d − 1 0\leq i\leq d-1 0≤i≤d−1,为the i i i-th layer of the circuit C C C 关联a vector v i = ( v i , 0 , ⋯ , v i , S − 1 ) ∈ F s v_i=(v_{i,0},\cdots,v_{i,S-1})\in\mathbb{F}^s vi=(vi,0,⋯,vi,S−1)∈Fs。the d d d-th layer of circuit C C C 关联的vector为 v d = ( v d , 0 , ⋯ , v d , n − 1 ) ∈ F n v_d=(v_{d,0},\cdots,v_{d,n-1})\in\mathbb{F}^n vd=(vd,0,⋯,vd,n−1)∈Fn。
这些vectors为functions of the input x = ( x 1 , ⋯ , x n ) ∈ F n x=(x_1,\cdots,x_n)\in\mathbb{F}^n x=(x1,⋯,xn)∈Fn,可定义为:
For each 0 ≤ i ≤ d 0\leq i\leq d 0≤i≤d,设置 v i v_i vi为vector that consists of the values of all the gates in the i i i-th layer of the circuit when it is evaluated on input x x x。
因此, v 0 v_0 v0对应output layer,满足 v 0 = ( C ( x ) , 0 , ⋯ , 0 ) ∈ F s v_0=(C(x),0,\cdots,0)\in\mathbb{F}^s v0=(C(x),0,⋯,0)∈Fs; v d v_d vd对应input layer,满足 v d = ( x 1 , ⋯ , x n ) v_d=(x_1,\cdots,x_n) vd=(x1,⋯,xn)。
类似地,对于 0 ≤ i ≤ d − 1 0\leq i\leq d-1 0≤i≤d−1,设置 V ~ i : F m → F \tilde{V}_i:\mathbb{F}^m\rightarrow \mathbb{F} V~i:Fm→F 为the (unique) low degree extension of v i v_i vi with respect to H , F , m \mathbb{H},\mathbb{F},m H,F,m。【 V ~ d : F m ′ → F \tilde{V}_d:\mathbb{F}^{m'}\rightarrow \mathbb{F} V~d:Fm′→F】
注意function V ~ i \tilde{V}_i V~i具有degree ≤ ∣ H ∣ − 1 \leq |\mathbb{H}|-1 ≤∣H∣−1 in each of its m m m variables and is efficiently computable。
3.2 Bare-Bones protocol
对于bare-bones protocol,Prover想证明 C ( x ) = 0 C(x)=0 C(x)=0,等价地,想证明 V ~ 0 ( 0 , ⋯ , 0 ) = 0 \tilde{V}_0(0,\cdots,0)=0 V~0(0,⋯,0)=0。证明过程包含 d d d phases,其中 d d d为the depth of C C C:
- 在第 i i i-th phase( 1 ≤ i ≤ d 1\leq i\leq d 1≤i≤d),Prover reduce the task of proving that V ~ i − 1 ( z i − 1 ) = r i − 1 \tilde{V}_{i-1}(z_{i-1})=r_{i-1} V~i−1(zi−1)=ri−1 to the task of proving that V ~ i ( z i ) = r i \tilde{V}_i(z_i)=r_i V~i(zi)=ri。其中 z i z_i zi为a random value determined by the protocol(有 z 0 = ( 0 , ⋯ , 0 ) , r 0 = 0 z_0=(0,\cdots,0),r_0=0 z0=(0,⋯,0),r0=0)。
- 最后,在 d d d phase后,Verifier自己验证 V ~ d ( z d ) = r d \tilde{V}_{d}(z_d)=r_d V~d(zd)=rd。注意, V ~ d \tilde{V}_d V~d为the low degree extension of the input x x x with respect to H , F , m ′ \mathbb{H},\mathbb{F},m' H,F,m′。
在此,Verifier需compute a single point in the low degree extension of the input x x x,这是Verifier的最大算力开销,且该计算与circuit C C C无关,can be done in quasi-linear time in the input length。
此外,若Verifier具有oracle access to the low-degree extension of x x x,则此时仅需要一次oracle call。
在每一个phase,communication complexity为 p o l y ( d , log S ) poly(d,\log S) poly(d,logS),Prover running time为不多于 p o l y ( S ) poly(S) poly(S),Verifier running time为 p o l y ( d , log S ) poly(d,\log S) poly(d,logS)。
在第 i i i-th phase ( i ∈ [ d − 1 ] i\in[d-1] i∈[d−1]),需reduce the task of proving that V ~ i − 1 ( z i − 1 ) = r i − 1 \tilde{V}_{i-1}(z_{i-1})=r_{i-1} V~i−1(zi−1)=ri−1 to the task of proving that V ~ i ( Z i ) = r i \tilde{V}_i(Z_i)=r_i V~i(Zi)=ri,其中 z i ∈ F m z_i\in\mathbb{F}^m zi∈Fm 为 a random value determined by the verifier, r i r_i ri为a value determined by the protocol。

对于 p , w 1 , w 2 ∈ F m p,w_1,w_2\in\mathbb{F}^m p,w1,w2∈Fm,定义:
f i ( p , w 1 , w 2 ) = a d d ~ i ( p , w 1 , w 2 ) ⋅ ( V ~ i ( w 1 ) + V ~ i ( w 2 ) ) + m u l t ~ i ( p , w 1 , w 2 ) ⋅ V ~ i ( w 1 ) ⋅ V ~ i ( w 2 ) f_i(p,w_1,w_2)=\tilde{add}_i(p,w_1,w_2)\cdot (\tilde{V}_i(w_1)+\tilde{V}_i(w_2))+\tilde{mult}_i(p,w_1,w_2)\cdot \tilde{V}_i(w_1)\cdot \tilde{V}_i(w_2) fi(p,w1,w2)=add~i(p,w1,w2)⋅(V~i(w1)+V~i(w2))+mult~i(p,w1,w2)⋅V~i(w1)⋅V~i(w2)
对于每个 p ∈ H m p\in\mathbb{H}^m p∈Hm, V ~ i − 1 ( p ) = ∑ w 1 , w 2 ∈ H m f i ( p , w 1 , w 2 ) \tilde{V}_{i-1}(p)=\sum_{w_1,w_2\in\mathbb{H}^m}f_i(p,w_1,w_2) V~i−1(p)=∑w1,w2∈Hmfi(p,w1,w2)。
根据low-degree extension的定义,对于每一个 z ∈ F m z\in\mathbb{F}^m z∈Fm,有 V ~ i − 1 ( z ) = ∑ p ∈ H m β ~ ( z , p ) ⋅ V ~ i − 1 ( p ) \tilde{V}_{i-1}(z)=\sum_{p\in\mathbb{H}^m}\tilde{\beta}(z,p)\cdot \tilde{V}_{i-1}(p) V~i−1(z)=∑p∈Hmβ~(z,p)⋅V~i−1(p),其中 β ~ : F m × F m → F \tilde{\beta}:\mathbb{F}^m\times\mathbb{F}^m\rightarrow \mathbb{F} β~:Fm×Fm→F为 a polynomial of degree at most ∣ H ∣ − 1 |\mathbb{H}|-1 ∣H∣−1 in each variable,that can be computed in time ≤ p o l y ( ∣ H ∣ , m ) \leq poly(|\mathbb{H}|,m) ≤poly(∣H∣,m)。
结论为,对于每一个 z ∈ F m z\in\mathbb{F}^m z∈Fm,有:
V ~ i − 1 ( z ) = ∑ p , w 1 , w 2 ∈ H m β ~ ( z , p ) ⋅ f i ( p , w 1 , w 2 ) \tilde{V}_{i-1}(z)=\sum_{p,w_1,w_2\in\mathbb{H}^m}\tilde{\beta}(z,p)\cdot f_i(p,w_1,w_2) V~i−1(z)=∑p,w1,w2∈Hmβ~(z,p)⋅fi(p,w1,w2)
因此,证明 V ~ i − 1 ( z i − 1 ) = r i − 1 \tilde{V}_{i-1}(z_{i-1})=r_{i-1} V~i−1(zi−1)=ri−1 reduce为证明 r i − 1 = ∑ p , w 1 , w 2 ∈ H m β ~ ( z i − 1 , p ) ⋅ f i ( p , w 1 , w 2 ) r_{i-1}=\sum_{p,w_1,w_2\in\mathbb{H}^m}\tilde{\beta}(z_{i-1},p)\cdot f_i(p,w_1,w_2) ri−1=∑p,w1,w2∈Hmβ~(zi−1,p)⋅fi(p,w1,w2),可通过运行interactive sum-check protocol来证明。
在该sum-check protocol中,最终Verifier需自己计算 β ~ ( z i − 1 , p ) ⋅ f i ( p , w 1 , w 2 ) \tilde{\beta}(z_{i-1},p)\cdot f_i(p,w_1,w_2) β~(zi−1,p)⋅fi(p,w1,w2) on random inputs p , w 1 , w 2 ∈ R F m p,w_1,w_2\in_R\mathbb{F}^m p,w1,w2∈RFm(chosen by the verifier)。
注意,本文假设Verifier具有oracle access to the functions a d d ~ i , m u l t ~ i \tilde{add}_i,\tilde{mult}_i add~i,mult~i,因此计算function β ~ \tilde{\beta} β~ 需要时间为 ≤ p o l y ( ∣ H ∣ , m ) \leq poly(|\mathbb{H}|,m) ≤poly(∣H∣,m),因此verification中的主要开销在于计算 V ~ i ( w 1 ) \tilde{V}_i(w_1) V~i(w1) 和 V ~ i ( w 2 ) \tilde{V}_i(w_2) V~i(w2),which requres time p o l y ( S ) poly(S) poly(S) (and thus cannot be computed by our computationally bounded verifier)。因此,需要由Prover来计算 v 1 = V ~ i ( w 1 ) v_1=\tilde{V}_i(w_1) v1=V~i(w1) 和 v 2 = V ~ i ( w 2 ) v_2=\tilde{V}_i(w_2) v2=V~i(w2)发送给Verifier,而Verifier需要验证 V ~ i ( w 1 ) = v 1 \tilde{V}_i(w_1)=v_1 V~i(w1)=v1 和 V ~ i ( w 2 ) = v 2 \tilde{V}_i(w_2)=v_2 V~i(w2)=v2成立。
目前为止,使用the sum-check protocol,可reduce the task of proving that V ~ i − 1 ( z i − 1 ) = r i − 1 \tilde{V}_{i-1}(z_{i-1})=r_{i-1} V~i−1(zi−1)=ri−1 to the task of proving that both V ~ i ( w 1 ) = v 1 \tilde{V}_i(w_1)=v_1 V~i(w1)=v1 and V ~ i ( w 2 ) = v 2 \tilde{V}_i(w_2)=v_2 V~i(w2)=v2。注意,此处有2个等式需要判断,而本文的目标是reduce the task of proving that V ~ i − 1 ( z i − 1 ) = r i − 1 \tilde{V}_{i-1}(z_{i-1})=r_{i-1} V~i−1(zi−1)=ri−1 to the task of proving a single equality of the form V ~ i ( z i ) = r i \tilde{V}_i(z_i)=r_i V~i(zi)=ri。
因此,在第 i i i-th phase,需要reudce the task of proving that both V ~ i ( w 1 ) = v 1 \tilde{V}_i(w_1)=v_1 V~i(w1)=v1 and V ~ i ( w 2 ) = v 2 \tilde{V}_i(w_2)=v_2 V~i(w2)=v2 to the task of proving a single equality of the form V ~ i ( z i ) = r i \tilde{V}_i(z_i)=r_i V~i(zi)=ri。
4. Interactive Proofs: Implementing the Bare-Bones Protocol
引入了sub-circuit的概念。。。。。。
参考资料
[1] Justin Thaler A Note on the GKR Protocol



