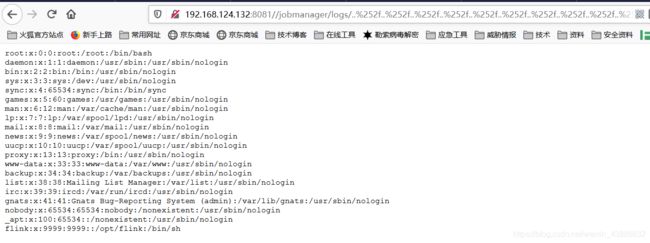
- Apache Tomcat 远程代码执行漏洞复现(CVE-2025-24813)(附脚本)
iSee857
漏洞复现apachetomcatjavaweb安全安全
免责申明:本文所描述的漏洞及其复现步骤仅供网络安全研究与教育目的使用。任何人不得将本文提供的信息用于非法目的或未经授权的系统测试。作者不对任何由于使用本文信息而导致的直接或间接损害承担责任。如涉及侵权,请及时与我们联系,我们将尽快处理并删除相关内容。0x01产品描述:ApacheTomcat是一个开源的JavaServlet容器和Web服务器,支持运行JavaServlet、JavaServerP
- CVE - 2016 - 6628 漏洞复现:深入剖析及实战演示
Waitccy
网络安全网络安全java
CVE-2016-6628漏洞复现:深入剖析及实战演示一、引言在网络安全领域,漏洞复现是理解和应对安全威胁的重要手段。CVE-2016-6628是一个影响广泛的严重漏洞,它主要存在于某些版本的Android系统中,攻击者可利用此漏洞通过特制的应用程序获取敏感信息、执行任意代码等,给用户带来极大的安全风险。本文将详细介绍CVE-2016-6628漏洞的背景、原理,并进行完整的漏洞复现过程,帮助读者更
- 零基础到网络安全工程师
幼儿园扛把子\
web安全安全
爆肝!三个月从零基础到网络安全工程师:2025年黑客技术实战指南(附工具包+100G资源)网络安全攻防示意图|数据来源:CSDN技术社区关键词:网络安全、红队实战、CTF竞赛、渗透测试、漏洞挖掘一、为什么90%的人学不会黑客技术?这3个误区正在毁掉你!1.错误认知:把"黑客"等同于"攻击者"真相:网络安全法实施后,合规的渗透测试工程师(白帽黑客)已成国家战略人才,平均月薪25K+案例:某学员通过挖
- 新手必看——ctf六大题型介绍及六大题型解析&举例解题
沛哥网络安全
web安全学习安全udp网络协议
CTF(CaptureTheFlag)介绍与六大题型解析一、什么是CTF?CTF(CaptureTheFlag),意为“夺旗赛”,是一种信息安全竞赛形式,广泛应用于网络安全领域。CTF竞赛通过模拟现实中的网络安全攻防战,让参赛者以攻防对抗的形式,利用各种信息安全技术进行解决一系列安全问题,最终获得“旗帜(Flag)”来获得积分。CTF赛事一般分为两种形式:Jeopardy(解题模式):参赛者通过解
- 新手必看——ctf六大题型介绍及六大题型解析&举例解题
沛哥网络安全
web安全学习安全udp网络协议
CTF(CaptureTheFlag)介绍与六大题型解析一、什么是CTF?CTF(CaptureTheFlag),意为“夺旗赛”,是一种信息安全竞赛形式,广泛应用于网络安全领域。CTF竞赛通过模拟现实中的网络安全攻防战,让参赛者以攻防对抗的形式,利用各种信息安全技术进行解决一系列安全问题,最终获得“旗帜(Flag)”来获得积分。CTF赛事一般分为两种形式:Jeopardy(解题模式):参赛者通过解
- Web安全攻防入门教程——hvv行动详解
白帽子黑客罗哥
web安全安全hw护网行动网络安全
Web安全攻防入门教程Web安全攻防是指在Web应用程序的开发、部署和运行过程中,保护Web应用免受攻击和恶意行为的技术与策略。这个领域不仅涉及防御措施的实现,还包括通过渗透测试、漏洞挖掘和模拟攻击来识别潜在的安全问题。本教程将带你入门Web安全攻防的基础概念、常见攻击类型、防御技术以及一些实战方法。一、Web安全基础Web应用安全的三大核心目标(CIA三原则)机密性(Confidentialit
- Web安全攻防入门教程——hvv行动详解
白帽子黑客罗哥
web安全安全学习网络网络安全
Web安全攻防入门教程Web安全攻防是指在Web应用程序的开发、部署和运行过程中,保护Web应用免受攻击和恶意行为的技术与策略。这个领域不仅涉及防御措施的实现,还包括通过渗透测试、漏洞挖掘和模拟攻击来识别潜在的安全问题。本教程将带你入门Web安全攻防的基础概念、常见攻击类型、防御技术以及一些实战方法。一、Web安全基础Web应用安全的三大核心目标(CIA三原则)机密性(Confidentialit
- 【漏洞复现】泛微OA E-Cology getdata.jsp SQL注入漏洞
0x0000001
漏洞复现javasql开发语言webweb渗透web安全漏洞
免责声明:本文内容旨在提供有关特定漏洞或安全漏洞的信息,以帮助用户更好地了解可能存在的风险。公布此类信息的目的在于促进网络安全意识和技术进步,并非出于任何恶意目的。阅读者应该明白,在利用本文提到的漏洞信息或进行相关测试时,可能会违反某些法律法规或服务协议。同时,未经授权地访问系统、网络或应用程序可能导致法律责任或其他严重后果。作者不对读者基于本文内容而产生的任何行为或后果承担责任。读者在使用本文所
- Web安全攻防入门教程——hvv行动详解
白帽子黑客罗哥
web安全安全网络安全pythonjava
Web安全攻防入门教程Web安全攻防是指在Web应用程序的开发、部署和运行过程中,保护Web应用免受攻击和恶意行为的技术与策略。这个领域不仅涉及防御措施的实现,还包括通过渗透测试、漏洞挖掘和模拟攻击来识别潜在的安全问题。本教程将带你入门Web安全攻防的基础概念、常见攻击类型、防御技术以及一些实战方法。一、Web安全基础Web应用安全的三大核心目标(CIA三原则)机密性(Confidentialit
- 【漏洞复现】泛微OA E-Office /iweboffice/officeserver.php 多个参数存在任意文件读取漏洞
0x0000001
漏洞复现php开发语言网络安全web安全渗透测试网络安全
免责声明:本文旨在提供有关特定漏洞的信息,以帮助用户了解潜在风险。发布此信息旨在促进网络安全意识和技术进步,并非出于恶意。读者应理解,利用本文提到的漏洞或进行相关测试可能违反法律或服务协议。未经授权访问系统、网络或应用程序可能导致法律责任或严重后果。作者对读者基于本文内容的行为不承担责任。读者在使用信息时必须遵守适用法律法规和服务协议,独自承担所有风险和责任。如有侵权,请联系删除。漏洞描述泛微OA
- Weblogic XMLDecoder反序列化漏洞复现(CVE-2017-10271)
又菜又爱倒腾
漏洞复现安全漏洞
#WeblogicXMLDecoder反序列化漏洞(CVE-2017-10271)#一、漏洞简介weblogic的WLSSecurity组件对外提供webservice服务,其中使用了XMLDecoder来解析用户传入的XML数据,在解析的过程中出现反序列化漏洞,导致可执行任意命令。二、漏洞影响影响版本10.3.6.0.0,12.1.3.0.0,12.2.1.1.0,12.2.1.2.0三、产生原
- 【漏洞复现】用友NC-accept-任意文件上传
.Rain.
漏洞复现web安全漏洞复现
目录0x01产品简介0x02漏洞概述0x03网络测绘0x04漏洞复现0x05Nuclei0x01产品简介用友NC是北京用友软件股份有限公司(简称“用友”)开发的一款企业管理软件,支持财务会计、人力资源、供应链、生产制造、客户关系管理等多个业务领域,涵盖了企业核心业务及管理流程。用友NC是基于B/S架构的软件系统,提供基于云计算、SaaS模式、本地部署等多种部署方式,广泛应用于国内外众多中小型企业和
- 新手必看——ctf六大题型介绍及六大题型解析&举例解题
沛哥网络安全
web安全学习安全udp网络协议
CTF(CaptureTheFlag)介绍与六大题型解析一、什么是CTF?CTF(CaptureTheFlag),意为“夺旗赛”,是一种信息安全竞赛形式,广泛应用于网络安全领域。CTF竞赛通过模拟现实中的网络安全攻防战,让参赛者以攻防对抗的形式,利用各种信息安全技术进行解决一系列安全问题,最终获得“旗帜(Flag)”来获得积分。CTF赛事一般分为两种形式:Jeopardy(解题模式):参赛者通过解
- 2025HW行动面试题20道全解析(附答案)黑客技术零基础入门到精通实战教程!
程序员七海
web安全网络安全干货分享计算机渗透测试护网行动黑客技术
HW行动作为国家级网络安全攻防演练的重要环节,对安全工程师的技术能力和实战经验提出了极高要求。本文结合近年护网面试高频考点与实战经验,整理出20道面试题及详细解析,涵盖渗透测试、漏洞分析、防御技术、应急响应等方向,助力从业者系统备战。一、基础概念与攻防技术什么是DDoS攻击?如何防御?答:DDoS攻击通过向目标发送海量请求耗尽资源,导致服务瘫痪。防御需结合流量清洗(CDN)、负载均衡、IPS/ID
- Web安全攻防入门教程——hvv行动详解
白帽子黑客罗哥
web安全安全网络安全系统安全红蓝对抗
Web安全攻防入门教程Web安全攻防是指在Web应用程序的开发、部署和运行过程中,保护Web应用免受攻击和恶意行为的技术与策略。这个领域不仅涉及防御措施的实现,还包括通过渗透测试、漏洞挖掘和模拟攻击来识别潜在的安全问题。本教程将带你入门Web安全攻防的基础概念、常见攻击类型、防御技术以及一些实战方法。一、Web安全基础Web应用安全的三大核心目标(CIA三原则)机密性(Confidentialit
- Web安全攻防入门教程——hvv行动详解
白帽子黑客罗哥
web安全安全网络安全系统安全红蓝对抗
Web安全攻防入门教程Web安全攻防是指在Web应用程序的开发、部署和运行过程中,保护Web应用免受攻击和恶意行为的技术与策略。这个领域不仅涉及防御措施的实现,还包括通过渗透测试、漏洞挖掘和模拟攻击来识别潜在的安全问题。本教程将带你入门Web安全攻防的基础概念、常见攻击类型、防御技术以及一些实战方法。一、Web安全基础Web应用安全的三大核心目标(CIA三原则)机密性(Confidentialit
- Web安全攻防入门教程——hvv行动详解
白帽子黑客罗哥
web安全安全网络安全pythonjava
Web安全攻防入门教程Web安全攻防是指在Web应用程序的开发、部署和运行过程中,保护Web应用免受攻击和恶意行为的技术与策略。这个领域不仅涉及防御措施的实现,还包括通过渗透测试、漏洞挖掘和模拟攻击来识别潜在的安全问题。本教程将带你入门Web安全攻防的基础概念、常见攻击类型、防御技术以及一些实战方法。一、Web安全基础Web应用安全的三大核心目标(CIA三原则)机密性(Confidentialit
- phpcms v9文件上传漏洞复现
熬夜且瞌睡
网络php开发语言
1.压缩包文件无递归删除$file=$_FILES['file'];#检查文件是否为空文件if(!$file){exit("请勿上传空文件");}$name=$file['name'];$dir='upload/';$ext=strtolower(substr(strrchr($name,'.'),1));functioncheck_dir($dir)#检查文件格式{$handle=opendir
- 网络安全从入门到精通(特别篇V):应急响应之webshell处置流程
HACKNOE
网络安全应急响应科研室web安全系统安全网络安全应急响应
应急响应应急响应之webshell处置流程1.1Webshell简介1.2Webshell的分类1.3Webshell的用途1.4Webshell的检测方法1.5Webshell的防御方法1.6常规处置方法1.6.1入侵时间确定1.6.2WEB日志分析1.6.3漏洞分析1.6.4漏洞复现1.6.5漏洞修复1.7常用工具1.7.1D盾1.7.2河马1.7.3wireshark应急响应之webshel
- JeeWMS graphReportController.do SQL注入漏洞复现(CVE-2025-0392)
iSee857
漏洞复现安全web安全
免责申明:本文所描述的漏洞及其复现步骤仅供网络安全研究与教育目的使用。任何人不得将本文提供的信息用于非法目的或未经授权的系统测试。作者不对任何由于使用本文信息而导致的直接或间接损害承担责任。如涉及侵权,请及时与我们联系,我们将尽快处理并删除相关内容。0x01产品描述:JeeWMS是一款基于JavaEE企业级架构开发的开源仓库管理系统(WMS),专为优化仓储管理和物流操作而设计。它支持多仓库、多货主
- Cuppa CMS任意文件读取漏洞(CVE-2022-25401)
风中追风-fzzf
#文件读取安全web安全
一、漏洞概述CuppaCMSv1.0中文件管理器的复制功能允许将任何文件复制到当前目录,从而授予攻击者对任意文件得读取权限,/templates/default/html/windows/right.php文件存在任意文件读取漏洞。二、影响范围v1.0三、访问页面四、漏洞复现1、访问接口POST接口/templates/default/html/windows/right.phpPOST/temp
- WordPress Course Booking System SQL注入漏洞复现 (CVE-2025-22785)(附脚本)
iSee857
漏洞复现安全web安全
免责申明:本文所描述的漏洞及其复现步骤仅供网络安全研究与教育目的使用。任何人不得将本文提供的信息用于非法目的或未经授权的系统测试。作者不对任何由于使用本文信息而导致的直接或间接损害承担责任。如涉及侵权,请及时与我们联系,我们将尽快处理并删除相关内容。0x01产品描述:课程预订系统是一个在线平台,旨在简化课程报名流程。用户可以通过系统浏览可用课程,查看详细的课程描述、时间安排和讲师信息,并通过简单的
- [ vulhub漏洞复现篇 ] solr 远程命令执行 (CVE-2017-12629-RCE)
_PowerShell
[靶场实战]vulhubvulhub漏洞复现ApacheSolr远程命令执行CVE-2017-12629渗透测试
博主介绍博主介绍:大家好,我是_PowerShell,很高兴认识大家~✨主攻领域:【渗透领域】【数据通信】【通讯安全】【web安全】【面试分析】点赞➕评论➕收藏==养成习惯(一键三连)欢迎关注一起学习一起讨论⭐️一起进步文末有彩蛋作者水平有限,欢迎各位大佬指点,相互学习进步!文章目录博主介绍一、漏洞编号二、影响范围三、漏洞描述四、环境搭建1、进入CVE-2017-12629-RCE环境2、启动C
- [ vulhub漏洞复现篇 ] Apche log4j远程代码执行漏洞(CVE-2021-44228)
_PowerShell
[靶场实战]vulhubCVE-2021-44228远程代码执行漏洞Apchelog4j渗透测试
博主介绍博主介绍:大家好,我是_PowerShell,很高兴认识大家~✨主攻领域:【渗透领域】【数据通信】【通讯安全】【web安全】【面试分析】点赞➕评论➕收藏==养成习惯(一键三连)欢迎关注一起学习一起讨论⭐️一起进步文末有彩蛋作者水平有限,欢迎各位大佬指点,相互学习进步!文章目录博主介绍一、漏洞编号二、影响版本三、漏洞描述四、环境搭建1.进入CVE-2021-44228环境2.启动CVE-2
- 2025年AI网络安全攻防战:挑战深度解析与全链路防御体系构建指南
emmm形成中
网络安全人工智能web安全安全
2025年AI网络安全攻防战:挑战深度解析与全链路防御体系构建指南引言:AI技术是一把双刃剑随着ChatGPT、Sora等生成式AI技术的爆发式应用,2025年被称为“AI应用元年”。然而,AI在赋能网络安全防御的同时,也为攻击者提供了新型武器。根据瑞星《2024年中国网络安全报告》,AI驱动的钓鱼邮件攻击成功率较传统手段提升47%,而Darktrace预测2025年企业内部“影子AI”工具使用量
- Web安全攻防入门教程——hvv行动详解
白帽子黑客罗哥
web安全安全网络安全系统安全红蓝对抗
Web安全攻防入门教程Web安全攻防是指在Web应用程序的开发、部署和运行过程中,保护Web应用免受攻击和恶意行为的技术与策略。这个领域不仅涉及防御措施的实现,还包括通过渗透测试、漏洞挖掘和模拟攻击来识别潜在的安全问题。本教程将带你入门Web安全攻防的基础概念、常见攻击类型、防御技术以及一些实战方法。一、Web安全基础Web应用安全的三大核心目标(CIA三原则)机密性(Confidentialit
- 机器学习安全核心算法全景解析
金外飞176
网络空间安全机器学习安全算法
机器学习安全核心算法全景解析引言机器学习系统的脆弱性正成为安全攻防的新战场。从数据投毒到模型窃取,攻击者不断突破传统防御边界。本文系统性梳理ML安全关键技术图谱,重点解析12类核心算法及其防御价值。一、数据安全防护算法1.对抗样本防御算法名称核心思想2024年最新进展典型应用场景TRADES鲁棒性-准确性权衡优化Facebook提出自监督TRADES改进版自动驾驶目标检测JacobianSVD输入
- #渗透测试#批量漏洞挖掘#锐捷校园网自助服务系统 任意文件读取(CVE-2023-17233 )
独行soc
漏洞挖掘网络安全漏洞挖掘web安全面试护网
免责声明本教程仅为合法的教学目的而准备,严禁用于任何形式的违法犯罪活动及其他商业行为,在使用本教程前,您应确保该行为符合当地的法律法规,继续阅读即表示您需自行承担所有操作的后果,如有异议,请立即停止本文章读。目录一、漏洞核心原理与技术背景1.漏洞定义与触发条件2.常见攻击向量二、漏洞复现与渗透实战1.环境搭建与工具链2.漏洞验证步骤3.高级绕过技巧三、修复方案与安全加固1.代码层修复2.系统层加固
- 【漏洞复现】泛微OA E-Cology WorkflowServiceXml Sql注入
0x0000001
漏洞复现sql数据库webweb漏洞漏洞网络安全web安全
免责声明:本文内容旨在提供有关特定漏洞或安全漏洞的信息,以帮助用户更好地了解可能存在的风险。公布此类信息的目的在于促进网络安全意识和技术进步,并非出于任何恶意目的。阅读者应该明白,在利用本文提到的漏洞信息或进行相关测试时,可能会违反某些法律法规或服务协议。同时,未经授权地访问系统、网络或应用程序可能导致法律责任或其他严重后果。作者不对读者基于本文内容而产生的任何行为或后果承担责任。读者在使用本文所
- phpcms set inc.php,phpcms V9 sql注入漏洞测试
朱娟娟
phpcmsV9版本存在SQL注入漏洞,漏洞复现如下0x00以GET方式访问如下链接,得到返回包里mvbpqw_siteid值:http://127.0.0.1/index.php?m=wap&c=index&a=init&siteid=10x01构造SQL语句,将0x00中的mvbpqw_siteid值代入下面链接,以POST方式发起请求0x02将0x01步中的json值代入下面链接中,以POS
- jquery实现的jsonp掉java后台
知了ing
javajsonpjquery
什么是JSONP?
先说说JSONP是怎么产生的:
其实网上关于JSONP的讲解有很多,但却千篇一律,而且云里雾里,对于很多刚接触的人来讲理解起来有些困难,小可不才,试着用自己的方式来阐释一下这个问题,看看是否有帮助。
1、一个众所周知的问题,Ajax直接请求普通文件存在跨域无权限访问的问题,甭管你是静态页面、动态网页、web服务、WCF,只要是跨域请求,一律不准;
2、
- Struts2学习笔记
caoyong
struts2
SSH : Spring + Struts2 + Hibernate
三层架构(表示层,业务逻辑层,数据访问层) MVC模式 (Model View Controller)
分层原则:单向依赖,接口耦合
1、Struts2 = Struts + Webwork
2、搭建struts2开发环境
a>、到www.apac
- SpringMVC学习之后台往前台传值方法
满城风雨近重阳
springMVC
springMVC控制器往前台传值的方法有以下几种:
1.ModelAndView
通过往ModelAndView中存放viewName:目标地址和attribute参数来实现传参:
ModelAndView mv=new ModelAndView();
mv.setViewName="success
- WebService存在的必要性?
一炮送你回车库
webservice
做Java的经常在选择Webservice框架上徘徊很久,Axis Xfire Axis2 CXF ,他们只有一个功能,发布HTTP服务然后用XML做数据传输。
是的,他们就做了两个功能,发布一个http服务让客户端或者浏览器连接,接收xml参数并发送xml结果。
当在不同的平台间传输数据时,就需要一个都能解析的数据格式。
但是为什么要使用xml呢?不能使json或者其他通用数据
- js年份下拉框
3213213333332132
java web ee
<div id="divValue">test...</div>测试
//年份
<select id="year"></select>
<script type="text/javascript">
window.onload =
- 简单链式调用的实现技术
归来朝歌
方法调用链式反应编程思想
在编程中,我们可以经常遇到这样一种场景:一个实例不断调用它自身的方法,像一条链条一样进行调用
这样的调用你可能在Ajax中,在页面中添加标签:
$("<p>").append($("<span>").text(list[i].name)).appendTo("#result");
也可能在HQ
- JAVA调用.net 发布的webservice 接口
darkranger
webservice
/**
* @Title: callInvoke
* @Description: TODO(调用接口公共方法)
* @param @param url 地址
* @param @param method 方法
* @param @param pama 参数
* @param @return
* @param @throws BusinessException
- Javascript模糊查找 | 第一章 循环不能不重视。
aijuans
Way
最近受我的朋友委托用js+HTML做一个像手册一样的程序,里面要有可展开的大纲,模糊查找等功能。我这个人说实在的懒,本来是不愿意的,但想起了父亲以前教我要给朋友搞好关系,再加上这也可以巩固自己的js技术,于是就开始开发这个程序,没想到却出了点小问题,我做的查找只能绝对查找。具体的js代码如下:
function search(){
var arr=new Array("my
- 狼和羊,该怎么抉择
atongyeye
工作
狼和羊,该怎么抉择
在做一个链家的小项目,只有我和另外一个同事两个人负责,各负责一部分接口,我的接口写完,并全部测联调试通过。所以工作就剩下一下细枝末节的,工作就轻松很多。每天会帮另一个同事测试一些功能点,协助他完成一些业务型不强的工作。
今天早上到公司没多久,领导就在QQ上给我发信息,让我多协助同事测试,让我积极主动些,有点责任心等等,我听了这话,心里面立马凉半截,首先一个领导轻易说
- 读取android系统的联系人拨号
百合不是茶
androidsqlite数据库内容提供者系统服务的使用
联系人的姓名和号码是保存在不同的表中,不要一下子把号码查询来,我开始就是把姓名和电话同时查询出来的,导致系统非常的慢
关键代码:
1, 使用javabean操作存储读取到的数据
package com.example.bean;
/**
*
* @author Admini
- ORACLE自定义异常
bijian1013
数据库自定义异常
实例:
CREATE OR REPLACE PROCEDURE test_Exception
(
ParameterA IN varchar2,
ParameterB IN varchar2,
ErrorCode OUT varchar2 --返回值,错误编码
)
AS
/*以下是一些变量的定义*/
V1 NUMBER;
V2 nvarc
- 查看端号使用情况
征客丶
windows
一、查看端口
在windows命令行窗口下执行:
>netstat -aon|findstr "8080"
显示结果:
TCP 127.0.0.1:80 0.0.0.0:0 &
- 【Spark二十】运行Spark Streaming的NetworkWordCount实例
bit1129
wordcount
Spark Streaming简介
NetworkWordCount代码
/*
* Licensed to the Apache Software Foundation (ASF) under one or more
* contributor license agreements. See the NOTICE file distributed with
- Struts2 与 SpringMVC的比较
BlueSkator
struts2spring mvc
1. 机制:spring mvc的入口是servlet,而struts2是filter,这样就导致了二者的机制不同。 2. 性能:spring会稍微比struts快。spring mvc是基于方法的设计,而sturts是基于类,每次发一次请求都会实例一个action,每个action都会被注入属性,而spring基于方法,粒度更细,但要小心把握像在servlet控制数据一样。spring
- Hibernate在更新时,是可以不用session的update方法的(转帖)
BreakingBad
Hibernateupdate
地址:http://blog.csdn.net/plpblue/article/details/9304459
public void synDevNameWithItil()
{Session session = null;Transaction tr = null;try{session = HibernateUtil.getSession();tr = session.beginTran
- 读《研磨设计模式》-代码笔记-观察者模式
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
import java.util.ArrayList;
import java.util.List;
import java.util.Observable;
import java.util.Observer;
/**
* “观
- 重置MySQL密码
chenhbc
mysql重置密码忘记密码
如果你也像我这么健忘,把MySQL的密码搞忘记了,经过下面几个步骤就可以重置了(以Windows为例,Linux/Unix类似):
1、关闭MySQL服务
2、打开CMD,进入MySQL安装目录的bin目录下,以跳过权限检查的方式启动MySQL
mysqld --skip-grant-tables
3、新开一个CMD窗口,进入MySQL
mysql -uroot
- 再谈系统论,控制论和信息论
comsci
设计模式生物能源企业应用领域模型
再谈系统论,控制论和信息论
偶然看
- oracle moving window size与 AWR retention period关系
daizj
oracle
转自: http://tomszrp.itpub.net/post/11835/494147
晚上在做11gR1的一个awrrpt报告时,顺便想调整一下AWR snapshot的保留时间,结果遇到了ORA-13541这样的错误.下面是这个问题的发生和解决过程.
SQL> select * from v$version;
BANNER
-------------------
- Python版B树
dieslrae
python
话说以前的树都用java写的,最近发现python有点生疏了,于是用python写了个B树实现,B树在索引领域用得还是蛮多了,如果没记错mysql的默认索引好像就是B树...
首先是数据实体对象,很简单,只存放key,value
class Entity(object):
'''数据实体'''
def __init__(self,key,value)
- C语言冒泡排序
dcj3sjt126com
算法
代码示例:
# include <stdio.h>
//冒泡排序
void sort(int * a, int len)
{
int i, j, t;
for (i=0; i<len-1; i++)
{
for (j=0; j<len-1-i; j++)
{
if (a[j] > a[j+1]) // >表示升序
- 自定义导航栏样式
dcj3sjt126com
自定义
-(void)setupAppAppearance
{
[[UILabel appearance] setFont:[UIFont fontWithName:@"FZLTHK—GBK1-0" size:20]];
[UIButton appearance].titleLabel.font =[UIFont fontWithName:@"FZLTH
- 11.性能优化-优化-JVM参数总结
frank1234
jvm参数性能优化
1.堆
-Xms --初始堆大小
-Xmx --最大堆大小
-Xmn --新生代大小
-Xss --线程栈大小
-XX:PermSize --永久代初始大小
-XX:MaxPermSize --永久代最大值
-XX:SurvivorRatio --新生代和suvivor比例,默认为8
-XX:TargetSurvivorRatio --survivor可使用
- nginx日志分割 for linux
HarborChung
nginxlinux脚本
nginx日志分割 for linux 默认情况下,nginx是不分割访问日志的,久而久之,网站的日志文件将会越来越大,占用空间不说,如果有问题要查看网站的日志的话,庞大的文件也将很难打开,于是便有了下面的脚本 使用方法,先将以下脚本保存为 cutlog.sh,放在/root 目录下,然后给予此脚本执行的权限
复制代码代码如下:
chmo
- Spring4新特性——泛型限定式依赖注入
jinnianshilongnian
springspring4泛型式依赖注入
Spring4新特性——泛型限定式依赖注入
Spring4新特性——核心容器的其他改进
Spring4新特性——Web开发的增强
Spring4新特性——集成Bean Validation 1.1(JSR-349)到SpringMVC
Spring4新特性——Groovy Bean定义DSL
Spring4新特性——更好的Java泛型操作API
Spring4新
- centOS安装GCC和G++
liuxihope
centosgcc
Centos支持yum安装,安装软件一般格式为yum install .......,注意安装时要先成为root用户。
按照这个思路,我想安装过程如下:
安装gcc:yum install gcc
安装g++: yum install g++
实际操作过程发现,只能有gcc安装成功,而g++安装失败,提示g++ command not found。上网查了一下,正确安装应该
- 第13章 Ajax进阶(上)
onestopweb
Ajax
index.html
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/
- How to determine BusinessObjects service pack and fix pack
blueoxygen
BO
http://bukhantsov.org/2011/08/how-to-determine-businessobjects-service-pack-and-fix-pack/
The table below is helpful. Reference
BOE XI 3.x
12.0.0.
y BOE XI 3.0 12.0.
x.
y BO
- Oracle里的自增字段设置
tomcat_oracle
oracle
大家都知道吧,这很坑,尤其是用惯了mysql里的自增字段设置,结果oracle里面没有的。oh,no 我用的是12c版本的,它有一个新特性,可以这样设置自增序列,在创建表是,把id设置为自增序列
create table t
(
id number generated by default as identity (start with 1 increment b
- Spring Security(01)——初体验
yang_winnie
springSecurity
Spring Security(01)——初体验
博客分类: spring Security
Spring Security入门安全认证
首先我们为Spring Security专门建立一个Spring的配置文件,该文件就专门用来作为Spring Security的配置

 0x04 漏洞复现
0x04 漏洞复现