CEH v11 笔记总结 Module 1 (C)
CEH v11笔记
Module 1 Introduction to Ethical Hacking ( C )
5. Information Security Controls
5.1. Information Assurance (IA)
IA refers to the assurance of the integrity, availability, confidentiality, and authenticity of information and information systems during the usage, processing, storage, and transmission of information. Security experts accomplish information assurance with the help of physical, technical, and administrative controls. Information Assurance and Information Risk Management (IRM) ensure that only authorized personnel access and use information. This helps in achieving information security and business continuity.
Some of the processes that help in achieving information assurance include:
- Developing local policy, process, and guidance in such a way to maintain the information systems at an optimum security level
- Designing network and user authentication strategy—Designing a secure network ensures the privacy of user records and other information on the network. Implementing an effective user authentication strategy secures the information system’s data
- Identifying network vulnerabilities and threats—Vulnerability assessments outline the security posture of the network. Performing vulnerability assessments in search of network vulnerabilities and threats help to take the proper measures to overcome them
- Identifying problems and resource requirements
- Creating a plan for identified resource requirements
- Applying appropriate information assurance controls
- Performing the Certification and Accreditation (C&A) process of information systems helps to trace vulnerabilities, and implement safety measures to nullify(消除) them
- Providing information assurance training to all personnel in federal and private organizations brings among them an awareness of information technology
5.2. Defense-in-Depth
Defense-in-depth is a security strategy in which security professionals use several protection layers throughout an information system. This strategy uses the military principle that it is more difficult for an enemy to defeat a complex and multi-layered defense system than to penetrate a single barrier. Defense-in-depth helps to prevent direct attacks against an information system and its data because a break in one layer only leads the attacker to the next layer. If a hacker gains access to a system, defense-in-depth minimizes any adverse(不利的) impact and gives administrators and engineers time to deploy new or updated countermeasures to prevent a recurrence of the intrusion.

5.3. Risk Management
Risk management is the process of identifying, assessing, responding to, and implementing the activities that control how the organization manages the potential effects of risk. It has a prominent place throughout the security life cycle and is a continuous and ever-increasing complex process. The types of risks vary from organization to organization, but the act of preparing a risk management plan is common to all organizations.
5.3.1. What is Risk
Risk refers to the degree of uncertainty or expectation of potential damage that an adverse event may cause to the system or its resources, under specified conditions. Alternatively, risk can also be:
The probability of the occurrence of a threat or an event that will damage, cause loss to, or have other negative impacts on the organization, either from internal or external liabilities.
The possibility of a threat acting upon an internal or external vulnerability and causing harm to a resource.
The product of the likelihood that an event will occur and the impact that the event might have on an information technology asset.
The relation between Risk, Threats, Vulnerabilities, and Impact is as follows
R I S K = T h r e a t s × V u l n e r a b i l i t i e s × I m p a c t RISK=Threats×Vulnerabilities×Impact RISK=Threats×Vulnerabilities×Impact
The impact of an event on an information asset is the product of vulnerability in the asset and the asset’s value to its stakeholders. IT risk can be expanded to
R I S K = T h r e a t s × V u l n e r a b i l i t i e s × A s s e t V a l u e RISK=Threats×Vulnerabilities×Asset Value RISK=Threats×Vulnerabilities×AssetValue
In fact, the risk is the combination of the following two factors:
The probability of the occurrence of an adverse event
The consequence of the adverse event
5.3.2. Risk Level
The risk level is an assessment of the resulted impact on the network. Various methods exist to differentiate the risk levels depending on the risk frequency and severity. One of the common methods used to classify risks is to develop a two-dimensional matrix. Working out the frequency or probability of an incident happening (likelihood) and its possible consequences is necessary to analyze risks. This is referred to as the level of risk. Risk can be represented and calculated using the following formula:
L e v e l o f R i s k = C o n s e q u e n c e × L i k e l i h o o d Level of Risk=Consequence×Likelihood LevelofRisk=Consequence×Likelihood
Risks are categorized into different levels according to their estimated impact on the system. Primarily, there are four risk levels, which include extreme, high, medium, and low levels. Remember that control measures may decrease the level of a risk, but do not always entirely eliminate the risk.
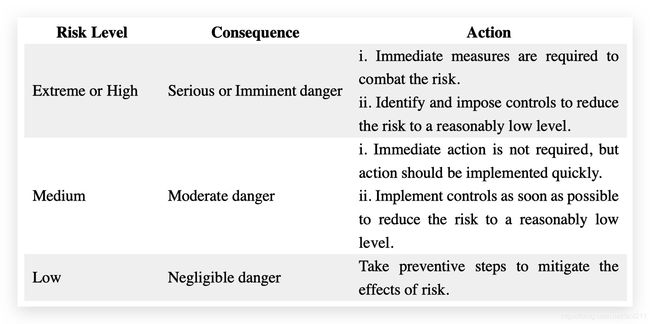
5.3.3. Risk Matrix
The risk matrix scales the risk occurrence or likelihood probability, along with its consequences or impact. It is the graphical representation of risk severity and the extent to which the controls can or will mitigate it. The Risk matrix is one of the simplest processes to use for increased visibility of risk; it contributes to the management’s decision-making capability. The risk matrix defines various levels of risk and categorizes them as the product of negative probability and negative severity. Although there are many standard risk matrices, individual organizations must create their own.
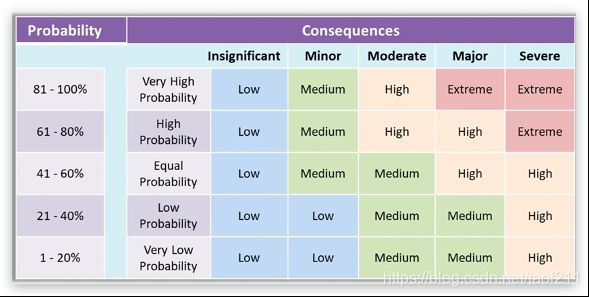
The above table is an example of the graphical representation of a risk matrix, which is used to visualize and compare risks. It differentiates the two levels of risk and is a simple way of analysing them:
- Likelihood: The chance of the risk occurring
- Consequence: The severity of a risk event that occurs
5.3.4. Risk Management Objectives
The objectives of risk management include:
- Identify potential risks—this is the main objective of risk management
- Identify the impact of risks and help the organization develop better risk management strategies and plans
- Prioritize the risks, depending on the impact or severity of the risk, and use established risk management methods, tools, and techniques to assist in this task
- Understand and analyze the risks and report identified risk events.
- Control the risk and mitigate its effect.
- Create awareness among the security staff and develop strategies and plans for lasting risk management strategies.
5.3.5. Risk Management Phases
Risk management is a continuous process performed by achieving goals at every phase. It helps reduce and maintain risk at an acceptable level utilizing a well-defined and actively employed security program. This process is applied in all stages of the organization, for example, to specific network locations in both strategic and operational contexts. The four key steps commonly termed as risk management phases, which should be followed by all organizations, are:
a. Risk Identification
The initial step of the risk management plan. Its main aim is to identify the risks—including the sources, causes, and consequences of the internal and external risks affecting the security of the organization before they cause harm. The risk identification process depends on the skill set of the people, and it differs from one organization to another.
b. Risk Assessment
This phase assesses the organization’s risks and estimates the likelihood and impact of those risks. Risk assessment is an ongoing iterative process that assigns priorities for risk mitigation and implementation plans, which in turn help to determine the quantitative and qualitative value of risk. Every organization should adopt a risk evaluation process in order to detect, prioritize, and remove risks. The risk assessment determines the kind of risks present, their likelihood and severity, and the priorities and plans for risk control. Organizations perform a risk assessment when they identify a hazard(危险) but are not able to control it immediately. A risk assessment is followed by a regular update of all information facilities.
c. Risk Treatment
Risk treatment is the process of selecting and implementing appropriate controls on the identified risks in order to modify them. The risk treatment method addresses and treats the risks according to their severity level. Decisions made in this phase are based on the results of a risk assessment. The purpose of this step is to identify treatments for the risks that fall outside the department’s risk tolerance(容忍) and provide an understanding of the level of risk with controls and treatments. It identifies the priority order in which individual risks should be treated, monitored, and reviewed. The following information is needed before treating the risk: the appropriate method of treatment, the people responsible for the treatment, the costs involved, the benefits of treatment, the likelihood of success, and ways to measure and assess the treatment.
d. Risk Tracking and Review
An effective risk management plan requires a tracking and review structure to ensure effective identification and assessment of the risks as well as the use of appropriate controls and responses. The tracking and review process should determine the measures and procedures adopted and ensure that the information gathered to perform the assessment was appropriate. The review phase evaluates the performance of the implemented risk management strategies. Performing regular inspections of policies and standards, as well as regularly reviewing them, helps to identify the opportunities for improvement. Further, the monitoring process ensures that there are appropriate controls in place for the organization’s activities and that all procedures are understood and followed.
5.4. Threat Modeling
5.4.1. Cyber Treat Intelligence
According to the Oxford dictionary, a threat is defined as “the possibility of a malicious attempt to damage or disrupt a computer network or system.” A threat is a potential occurrence of an undesired event that can eventually damage and interrupt the operational and functional activities of an organization. A threat can affect the integrity and availability factors of an organization. The impact of threats is very great and may affect the state of the physical IT assets in an organization. The existence of threats may be accidental, intentional, or due to the impact of some action.
Cyber threat intelligence, usually known as CTI, is the collection and analysis of information about threats and adversaries, and the drawing up(拟定) of patterns. These patterns provide an ability to make knowledgeable decisions for preparedness, prevention, and response actions against various cyberattacks. It is the process of recognizing or discovering any “unknown threats” that an organization may face so that necessary defense mechanisms can be applied to avoid such occurrences. It involves collecting, researching, and analysing trends and technical developments in the field of cyber threats (including cybercrime, hacktivism, and espionage(间谍行为)). Any knowledge about threats that result in an organization’s planning and decision-making to handle it is a piece of threat Intelligence. The main aim of CTI is to make the organization aware of existing or emerging(正在出现的) threats and prepare them to develop a proactive cybersecurity posture in advance of exploitation. This process, where unknown threats are converted into possibly known ones, helps to anticipate(预期) the attack before it can happen and ultimately results in a better and more secure system. Thus, threat Intelligence is useful in achieving secure data sharing and global transactions among organizations.
Threat intelligence processes can be used to identify the risk factors that are responsible for malware attacks, SQL injections, web application attacks, data leaks(数据泄露), phishing, denial-of-service attack, and other attacks. Such risks, after being filtered out, can be put on a checklist and handled appropriately. Threat intelligence is beneficial for an organization to handle cyber threats with effective planning and execution. Along with a thorough(周密的) analysis of the threat, CTI also strengthens the organization’s defense system, creates awareness about impending(迫近的) risks, and aids in responding against such risks.
5.4.2. Types of Treat Intelligence
Threat intelligence is contextual information that describes threats and guides organizations in making various business decisions. It is extracted from a huge collection of sources and information. It provides operational insight by looking outside the organization and issuing alerts on evolving threats to the organization. For the better management of information that is collected from different sources, it is important to subdivide threat intelligence into different types. This subdivision is performed based on the consumers and goals of the intelligence. From the perspective of consumption, threat intelligence is divided into four different types. They are named as strategic, tactical, operational, and technical threat intelligence.
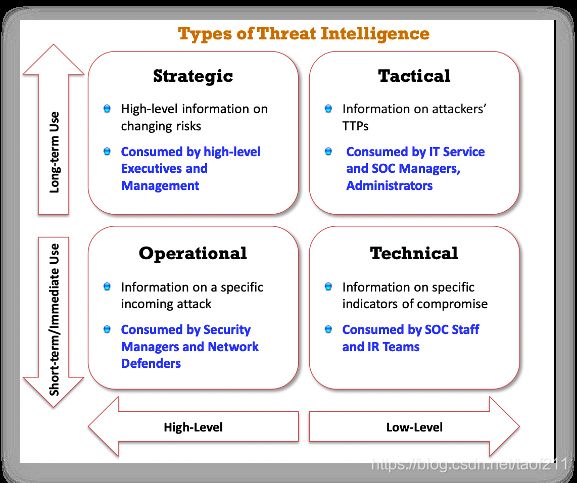
These four types differ in terms of data collection, data analysis, and intelligence consumption.
a. Strategic Threat Intelligence
Strategic threat intelligence provides high-level information regarding cybersecurity posture, threats, details about the financial impact of various cyber activities, attack trends, and the impact of high-level business decisions. This information is consumed by the high-level executives and management of the organization, such as IT management and CISO. It helps the management to identify current cyber risks, unknown future risks, threat groups, and attribution of breaches. The intelligence obtained provides a risk-based view that mainly focuses on high-level concepts of risks and their probability. It mainly deals with long-term issues and provides real-time alerts for threats to the organization’s critical assets, such as IT infrastructure, employees, customers, and applications. This intelligence is used by the management to make strategic business decisions and to analyze their effect. Based on the analysis, the management can allocate sufficient budget and staff to protect critical IT assets and business processes. The strategic threat intelligence helps organizations identify any similar past incidents, their intentions, and any attributes that might identify the attacking adversaries, why the organization is within the scope of the attack, major attack trends, and how to reduce the risk level. Generally, strategic threat intelligence includes the following information: the financial impact of cyber activity; attribution for intrusions and data breaches; threat actors and attack trends; the threat landscape for various industry sectors; statistical information on data breaches, data theft, and malware; geopolitical conflicts involving various cyberattacks; information on how adversary TTPs change over time; and industry sectors that might impact due to high-level business decisions.
b. Tactical Threat Intelligence
Tactical threat intelligence plays a major role in protecting the resources of the organization. It provides information related to the TTPs used by threat actors (attackers) to perform attacks. Tactical threat intelligence is consumed by cybersecurity professionals such as IT service managers, security operations managers, network operations centre (NOC) staff, administrators, and architects. It helps the cybersecurity professionals understand how the adversaries are expected to perform their attack on the organization, identify the information leakage from the organization, and assess the technical capabilities and goals of the attackers along with the attack vectors(媒介). Using tactical threat intelligence, security personnel develop detection and mitigation strategies beforehand through procedures such as updating security products with identified indicators and patching vulnerable systems. The collection sources for tactical threat intelligence include campaign reports, malware, incident reports, attack group reports, and human intelligence, among other information. This intelligence is generally obtained by reading white or technical papers, communicating with other organizations, or purchasing intelligence from third parties. It includes highly technical information on topics such as malware, campaigns, techniques, and tools in the form of forensic reports. Tactical threat intelligence provides day-to-day operational support by helping analysts assess various security incidents related to events, investigations, and other activities. It also guides the high-level executives of the organizations in making strategic business decisions.
c. Operational Threat Intelligence
Operational threat intelligence provides information about specific threats against the organization. It provides contextual information about security events and incidents that help defenders disclose potential risks, provide greater insight into attacker methodologies, identify past malicious activities, and perform investigations on malicious activity in a more efficient way. It is consumed by security managers or heads of incident response, network defenders, security forensics, and fraud detection teams. It helps organizations to understand the possible threat actors and their intention, capability, and opportunity to attack vulnerable IT assets and the impact of a successful attack. In many cases, only government organizations can collect this type of intelligence. However, doing so helps IR and forensic teams to deploy security assets to identify and stop upcoming attacks, improve early-stage attack detecting capability, and reduce an attack’s damage to IT assets. Operational threat intelligence is generally collected from sources such as humans, social media, and chat rooms; it may and also be collected from the real-world activities and events that result in cyberattacks. Operational threat intelligence is obtained by analysing human behaviour, threat groups, and by similar means. This information helps to predict future attacks and thus enhances incident response plans and mitigation strategies. Operational threat intelligence generally appears as a report that contains identified malicious activities, recommended courses of action, and warnings of emerging attacks.
d. Technical Threat Intelligence
Technical threat intelligence provides information about resources an attacker uses to perform an attack; this includes command and control channels, tools, and other items. It has a shorter lifespan compared to tactical threat intelligence and mainly focuses on a specific IoC. It provides rapid distribution and response to threats. For example, a piece of malware used to perform an attack is tactical threat intelligence, whereas the details related to the specific implementation of the malware come under technical threat intelligence. Other examples of technical threat intelligence include the specific IP addresses and domains used by malicious endpoints, phishing email headers, and hash checksums of malware, among others. Technical threat intelligence is consumed by SOC staff and IR teams. The indicators of technical threat intelligence are collected from active campaigns, attacks that are performed on other organizations, or data feeds provided by external third parties. These indicators are generally collected as part of investigations of attacks performed on various organizations. This information helps security professionals add the identified indicators to the defensive systems such as IDS and IPS, firewalls, and endpoint security systems, thereby enhancing the detection mechanisms used to identify the attacks at an early stage. It also helps them identify malicious traffic and IP addresses suspected of spreading malware and spam emails. This intelligence is directly fed into the security devices in digital format to block and identify inbound and outbound malicious traffic entering the organization’s network.
5.4.3. Introduction to Treat Modelling
Threat modelling is a risk assessment approach for analysing the security of an application by capturing, organizing, and analysing all the information that affects it. The threat model consists of three major building blocks: understanding the adversary’s perspective, characterizing the security of the system, and determining threats. Every application should have a developed and documented threat model that should be revisited as the application evolves and development progresses. Threat modeming helps to:
- Identify relevant threats to a particular application scenario
- Identify key vulnerabilities in an application’s design
- Improve security design
When using this approach, an administrator should keep the following in mind:
- Try not to be rigid about specific steps or implementations; instead, focus on the approach. If any step becomes impassable, go right to step 4 of the threat modelling process and identify the problem.
- Use scenarios to scope the modelling activity.
- Use existing design documents. Use items like documented use cases or use stories, architectural diagrams, data flow diagrams, or other design documentation.
- Start with a whiteboard before capturing information in documents or getting lost in detail. It may be helpful to use a digital camera with printing capabilities to document and distribute the information from the whiteboard.
- Use an iterative approach. Add more details and improve the threat model as design and development continues. This will help with becoming familiar with the modelling process and developing the threat model to better examine more possible scenarios.
- Obtain input about the host and network constraints from the system and network administrators. To better understand the end-to-end deployment diagram, obtain as much information as possible about host configurations, firewall policies allowed protocols and ports, and other relevant details.
5.4.4. Steps of Treat Modelling
The threat modelling process involves five steps:
a. Identify Security Objectives
Security objectives are the goals and constraints related to the application’s confidentiality, integrity, and availability. Security-specific objectives guide the threat modelling efforts and help to determine how much effort needs to be put toward subsequent steps. To identify security objectives, administrators should ask the following questions:
- What data should be protected?
- Are there any compliance requirements?
- Are there specific quality-of-service requirements?
- Are there intangible assets to protect?
b. Application Overview
Identify the components, data flows, and trust boundaries. To draw the end-to-end deployment scenario, the administrator should use a whiteboard. First, they should draw a rough diagram that explains the workings and structure of the application, its subsystems, and its deployment characteristics. The deployment diagram should contain the following:
- End-to-end deployment topology(拓扑结构)
- Logical layers
- Key components
- Key services
- Communication ports and protocols
- Identities
- External dependencies
Identify Roles - The administrator should identify people and the roles and actions they can perform within the application. For example, are there higher-privileged groups of users? Who can read data? Who can update data? Who can delete data?
Identify Key Usage Scenarios - The administrator should use the application’s use cases to determine its objective. Use cases explain how the application is used and misused.
Identify Technologies - The administrator should list the technologies and key features of the software, as well as the following technologies in use: operating systems; web server software; database server software; technologies for presentation, business, and data access layers; and development languages. Identifying these technologies helps to focus on technology-specific threats.
Identify Application Security Mechanisms - The administrator should identify some key points regarding the following: input and data validation; authorization and authentication; sensitive data; configuration management; session management; parameter manipulation; cryptography; exception management; auditing and logging. These efforts aim to identify relevant details and to add details where required, or to identify areas that require more.
c. Decompose(分解) the Application
In this step, the administrator breaks down the application to identify the trust boundaries, data flows, entry points, and exit points. Doing so makes it considerably easier to find more relevant and more detailed threats and vulnerabilities.
Identify Trust Boundaries - Identifying the application’s trust boundaries helps the administrator to focus on the relevant areas of the application. It indicates where trust levels change.
- Identify outer system boundaries
- Identify access control points or key places where access requires extra privileges or role membership
- Identify trust boundaries from a data flow perspective
Identify Data Flows - The administrator should list the application’s data input from entry to exit. This helps to understand how the application communicates with outside systems and clients, and how the internal components interact. They should pay particular attention to the data flow across trust boundaries and the data validation at the trust boundary entry point. A good approach is to start at the highest level and then deconstruct(解构) the application by testing the data flow between different subsystems.
Identify Entry Points - The application’s entry point can also serve as an entry point for attacks. All users interact with the application at these entry points. Other internal entry points uncovered by subcomponents over the layers of the application may be present only to support internal communication with other components. The administrator should identify these entry points to determine the methods used by an intruder to get in through them. They should focus on the entry points that allow access to critical functionalities and provide adequate defense for them.
Identify Exit Points - The administrator should also identify the points where the application transfers data to the client or external systems. They should prioritize the exit points at which the application writes data containing client input or data from untrusted sources, such as a shared database.
d. Identify Threats
The administrator should identify threats relevant to the control scenario and context using the information obtained in the application overview and decompose application steps. They should bring members of the development and test teams together to identify potential threats. The team should start with a list of common threats grouped by their application vulnerability category. This step uses a question-driven approach to help identify threats.
e. Identify Vulnerabilities
A vulnerability is a weakness in an application (deployed in an information system) that allows attacker exploitation, thereby leading to security breaches. Security administrators should identify any weaknesses related to the threats found using the vulnerability categories to identifying vulnerabilities and fix them beforehand to keep intruders away.
5.5. Incident Management
Incident management is a set of defined processes to identify, analyze, prioritize, and resolve security incidents to restore the system to normal service operations as soon as possible, and prevent the recurrence of the incident. It involves not only responding to incidents but also triggering alerts to prevent potential risks and threats. A security administrator must identify software that is open to attacks before someone takes advantage of the vulnerabilities. Incident management includes the following:
- Vulnerability analysis
- Artifact analysis
- Security awareness training
- Intrusion detection
- Public or technology monitoring
The incident management process is designed to improve service quality, resolve problems proactively(主动地), reduce the impact of incidents on an organization or its business, meet service availability requirements, increase staff efficiency and productivity, improve user and customer satisfaction, and assist in handling future incidents.
Conducting training sessions to spread awareness among users is an important part of incident management. Such sessions help end-users to recognize suspicious events or incidents easily and report an attacker’s behavior to the appropriate authority. The following people perform incident management activities:
- Human Resources (HR) Personnel
HR personnel take steps to fire employees suspected of harmful computer activities. - The Legal Counsel
The legal counsel sets the rules and regulations in an organization. These rules can influence the internal security policies and practices of the organization in case an insider or an attacker uses the organization’s system for harmful or malicious activities. - The firewall manager keeps filters in place. These filters are frequently where denial-of-service attacks are made.
- An Outsourced Service Provider
An outsourced service provider repairs system infected by viruses and malware.
Incident response is one of the functions performed in incident handling. In turn, incident handling is one of the services provided as part of incident management. The following diagram illustrates the relationship between incident response, incident handling, and incident management.
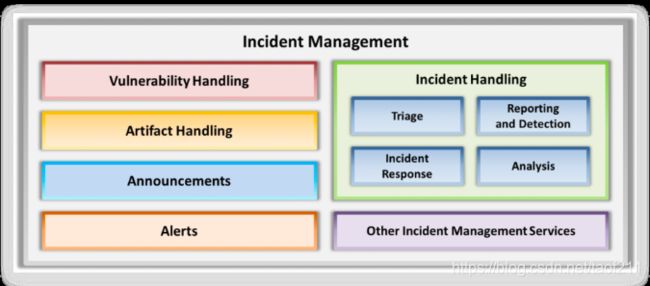
[Incident Handling & Response]
Incident handling and response (IH&R) is the process of taking organized and careful steps when reacting to a security incident or cyberattack. It is a set of procedures, actions, and measures taken against an unexpected event occurrence. It involves logging, recording, and resolving incidents that take place in the organization. It notes the incident, when it occurred, its impact, and its cause. It is the practice of managing the incident response processes, such as preparation, detection, containment, eradication, and recovery, to overcome the impact of an incident quickly and efficiently. IH&R processes are important to provide a focused approach for restoring normal business operations as quickly as possible after an incident and with a minimal impact on the business.
The IH&R process involves defining user policies, developing protocols, building incident response teams, auditing organizational assets, planning incident response procedures, obtaining management approval, incident reporting, prioritization, and managing response. It also includes establishing proper communication between the individuals responding to an incident and guiding them to detect, analyze, contain, recover, and prevent incidents.
Discussed below are the steps involved in the IH&R process:
Step1: Preparation
The preparation phase includes performing an audit of resources and assets to determine the purpose of security and define the rules, policies, and procedures that drive the IH&R process. It also includes building and training an incident response team, defining incident readiness procedures, and gathering required tools as well as training the employees to secure their systems and accounts.
Step2: Incident Recording & Assignment
In this phase, the initial reporting and recording of the incident take place. This phase handles identifying an incident and defining proper incident communication plans for the employees and also includes communication methods that involve informing IT support personnel or submitting an appropriate ticket.
Step3: Incident Triage
In this phase, the identified security incidents are analyzed, validated, categorized, and prioritized. The IH&R team further analyzes the compromised device to find incident details such as the type of attack, its severity(严重程度), target, impact, and method of propagation(传播), and any vulnerabilities it exploited.
Step4: Notification
In the notification phase, the IH&R team informs various stakeholders, including management, third-party vendors, and clients, about the identified incident.
Step5: Containment
This phase helps to prevent the spread of infection to other organizational assets, preventing additional damage.
Step6: Evidence Gathering & Forensic Analysis
In this phase, the IH&R team accumulates all possible evidence related to the incident and submits it to the forensic department for investigation. Forensic analysis of an incident reveals details such as the method of attack, vulnerabilities exploited, security mechanisms averted(绕过的), network devices infected, and applications compromised.
Step7: Eradication(摧毁)
In the eradication phase, the IH&R team removes or eliminates the root cause of the incident and closes all the attack vectors to prevent similar incidents in the future.
Step8: Recovery
After eliminating the causes for the incidents, the IH&R team restores the affected systems, services, resources, and data through recovery. It is the responsibility of the incident response team to ensure that that the incident causes no disruption to the services or business of the organization.
Step9: Post-Incident Activities
Once the process is complete, the security incident requires additional review and analysis before closing the matter. Conducting a final review is an important step in the IH&R process that includes:
- Incident documentation
- Incident impact assessment
- Reviewing and revising policies
- Closing the investigation
- Incident disclosure
5.6. Role of AI and ML in Cyber Security
Machine learning (ML) and Artificial Intelligence (AI) are now popularly used across various industries and applications due to the increase in computing power, data collection, and storage capabilities. Along with technological advancements in AI, there is also a rise in threats such as ransomware, botnets, malware, and phishing. Using AI and ML in cybersecurity helps to identify new exploits and weaknesses, which can be easily analyzed to mitigate further attacks. It reduces the pressure on security professionals and alerts them whenever an action is needed. The cybersecurity market is set to exceed $300 billion by 2024, and the AI-related cybersecurity market is predicted to reach a value of $38.2 billion by 2026.
5.6.1. What are AL and ML
Artificial Intelligence is the only solution to defend networks against the various attacks that an antivirus scan cannot detect. A huge amount of collected data is fed into the AI, which processes and analyzes it to understand its details and trends. ML is a branch of artificial intelligence (AI) that gives the systems the ability to self-learn without any explicit programs. This self-learning system is used to define what the normal network, along with its devices, looks like, and then uses this to backtrack and report any deviations or anomalies in real-time. There are two types of ML classification techniques:
a. Supervised Learning
Supervised learning uses algorithms that input a set of labeled training data to attempt to learn the differences between the given labels. Supervised learning is further divided into two subcategories, namely, classification and regression. The classification includes completely divided classes. Its main task is to define the test sample to identify its class. Regression is used when data classes are not separated, such as when the data is continuous.
b. Unsupervised Learning
Unsupervised learning makes use of algorithms that input unlabeled training data to attempt to deduce all the categories without guidance. Unsupervised learning is further divided into two subcategories, namely, clustering and dimensionality reduction. Clustering divides the data into clusters based on their similarities, regardless of class information. Dimensionality reduction is the process of reducing the dimensions (attributes) of data.
The security threat landscape continues to evolve not just in scale, but, more importantly, in sophistication(复杂). Despite a range of advancements in the industry to safeguard against increasingly bold(大胆) and intricate(错综复杂的) threats, organizations have struggled to keep pace with(与…保持同步) the technologies and techniques employed by attackers. As companies continue to increase their digital footprints, “identify and diagnose” capabilities are not enough to remediate against(弥补) this growing fundamental business challenge for organizations of all shapes and sizes. The development of advanced security analytics is an important consideration for organizations looking to implement machine learning to defend against an array of internal and external security threats.
5.6.2. AL & ML Areas
According to CB Insights, alongside overall rising investment activity, many cybersecurity companies are emerging to offer novel(新颖的) solutions to cyber threats by leveraging the advantages of artificial intelligence (AI). According to CB Insights’ AI Deals Tracker, cybersecurity is the fourth most active industry for deals to companies applying AI. As per CB Insights’ data, there are over 80 private companies in cybersecurity that are using AI, categorized into the nine main areas in which they operate, including: anti-fraud and identity management; mobile security; behavioural analytics and anomaly detection; automated security; cyber-risk management; app security; IoT security; and deception security
5.6.3. Using AI & ML Prevent Cyber Attack
Artificial Intelligence (AI), and with it, Machine Learning (ML), is an emerging technology in the field of cybersecurity. It is widely adopted by largescale industries such as automation, IT services, manufacturing, production, and finance. AI plays a crucial role in detecting imminent cyber threats by incorporating machine learning as a subset. Following are different ways that AI and ML safeguard industries from cybersecurity attacks:
a. Password Protection and Authentication
Password credentials play a critical role in preventing illegitimate access to the organization’s or user’s data. If credentials are compromised, the reputation of the organization or person could be damaged. Sometimes, traditional face detection and other biometric security measures can also be vulnerable to these credential breaches. Programmers use AI to improve biometric validations and face recognition to thwart such attacks. AI provides the latest models for recognizing an individual’s face by tracking key correlations and patterns.
b. Phishing Detection and Prevention
Phishing is a common method that attackers employ to send their payloads via emails. The majority of users cannot figure out which received emails have a malicious attachment or payload. In this case, AI and ML could play a pivotal(关键的) role in identifying and preventing such phishing attacks. They can scan and identify phishing emails much faster than a human being can. They can also quickly differentiate malicious websites from legitimate websites.
c. Threat Detection
Machine learning assists companies in detecting cyber-attacks before systems are compromised. Being a part of AI, machine learning constantly keeps admins notified of imminent(迫近的) cyber threats by carrying out logical data analysis. ML allows systems to run its algorithms upon the data being received, then performs deep learning on the and comprehends(理解) the advancements required to ensure the safety of the information systems.
d. Vulnerability Management
AI and ML-based systems never allow vulnerability to exist for long; they dynamically scan for all types of vulnerabilities and alert the admins before the system is exploited. They can also provide the attacker’s information and the patterns used to perform the attack. These AI-and ML-based systems can also forecast how and when a vulnerability exploitation might occur.
e. Behavioral Analytics
Another notable security improvement by artificial intelligence is “Behavioral Analytics.” Attackers who have stolen the credentials of a legitimate user can perform malicious activities on the organization’s network; such attempts are difficult to detect and thwart. Here, AI with ML generates specific user patterns based on their regular usage. AI software instantly alerts the admin if it detects any suspicious activity or deviation(偏离行为) in regular usage.
f. Network Security
Two significant factors of network security are generating comprehensive security policies and mapping an enterprise’s network topology. Unfortunately, both of these factors are time-consuming. Therefore, administrators are adopting AI to enhance this operation; it can carry out the network traffic analysis and propose efficient security policies by default.
g. AI-based Antivirus
Traditional antivirus tools perform file scanning on the organization’s networks to check if any signatures match those of known viruses or malware. The issue with this is that antivirus tools must be updated when the user wants to scan for new malware or viruses. Updating is time-consuming, and new deployment often takes a certain amount of time. To overcome these issues, organizations employ AI-based antiviruses, which use anomaly detection to understand programs’ behaviour. AI-based antivirus detects suspicious program behaviour instead of matching signatures for viruses.
h. Fraud Detection
AI and ML algorithms carry out anomaly detection to identify payment inconsistencies and fraudulent transactions. They also perform automated pattern discovery across different transactions. ML can easily differentiate between authentic and illegitimate transactions and blocks fraudulent transactions.
i. Botnet Detection
Botnets can bypass the Instruction Detection System (IDS) by leveraging its ineffectiveness in matching signatures. Botnets can be embedded using a highly sophisticated code that makes them untraceable by traditional IDS implementations. Hence, security professionals use AI and ML algorithms that alert about the suspicious behavior of a network and detect unauthorized intrusions.
j. AI to Combat AI Threats
Attackers can also leverage AI technology to make their way into an organization’s network; such cyber threats must be detected immediately. AI software can detect such imminent AI-augmented attacks before the network is compromised.
6. Information Security Laws & Standards
Laws are a system of rules and guidelines that are enforced by a particular country or community to govern behavior. A Standard is a “document established by consensus and approved by a recognized body that provides, for common and repeated use, rules, guidelines, or characteristics for activities or their results, aimed at the achievement of the optimum degree of order in a given context.” This section deals with the various laws and standards dealing with information security in different countries.
6.1. Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary(独占的) information security standard for organizations that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and POS cards. This standard offers robust(强大的) and comprehensive standards and supporting materials to enhance payment card data security. These materials include a framework of specifications, tools, measurements, and support resources to help organizations ensure the safe handling of cardholder information. PCI DSS applies to all entities involved in payment card processing, including merchants, processors, acquirers(收单方), issuers, and service providers, as well as all other entities that store, process or transmit cardholder data. PCI DSS comprises a minimum set of requirements for protecting cardholder data. The Payment Card Industry (PCI) Security Standards Council has developed and maintains a high-level overview of PCI DSS requirements.

Failure to meet PCI DSS requirements may result in fines or the termination of payment-card processing privileges.
6.2. ISO/IEC 27001:2013
SO/IEC 27001:2013 specifies the requirements for establishing, implementing, maintaining, and continually improving an information security management system within the context of an organization. It includes requirements for the assessment and treatment of information security risks tailored to(为…量身定制) the needs of the organization. The regulation is intended to be suitable for several different uses, including:
- Use within organizations to formulate security requirements and objectives
- Use within organizations as a way to ensure that security risks are cost-effectively managed
- Use within organizations to ensure compliance with laws and regulations
- Defining new information security management processes
- Identifying and clarifying existing information security management processes
- Use by the management of organizations to determine the status of information security management activities
- Implementing business-enabling information security
- Use by organizations to provide relevant information about information security to customers
6.3. Health Insurance Portability and Accountability Act (HIPAA)
The HIPAA Privacy Rule provides federal protections for the individually identifiable health information held by covered entities and their business associates and gives patients an array of rights to that information. At the same time, the Privacy Rule permits the disclosure of health information needed for patient care and other necessary purposes. The Security Rule specifies a series of administrative, physical, and technical safeguards for covered entities and their business associates to use to ensure the confidentiality, integrity, and availability of electronically protected health information. The office of civil rights implemented HIPAA’s Administrative Simplification Statute and Rules, as discussed below:
a. Electronic Transaction and Code Set Standards
Transactions are electronic exchanges involving the transfer of information between two parties for specific purposes. The Health Insurance Portability and Accountability Act of 1996 (HIPAA) designated certain types of organizations as covered entities, including health plans, health care clearinghouses, and certain health care providers. In the HIPAA regulations, the Secretary(部长) of Health and Human Services (HHS) adopted certain standard transactions for the Electronic Data Interchange (EDI) of health care data. These transactions are claims and encounter information, payment and remittance advice, claim status, eligibility, enrolment and dis-enrolment, referrals and authorizations, coordination of benefits, and premium payment. Under HIPAA, if a covered entity electronically conducts one of the adopted transactions, they must use the adopted standard—either from ASC, X12N, or NCPDP (for certain pharmacy transactions). Covered entities must adhere to the content and format requirements of each transaction. Every provider who does business electronically must use the same health care transactions, code sets, and identifiers.
b. Privacy Rule
The HIPAA Privacy Rule establishes national standards to protect people’s medical records and other personal health information and applies to health plans, health care clearinghouses, and health care providers that conduct certain health care transactions electronically. The rule requires appropriate safeguards to protect the privacy of personal health information. It sets limits and conditions on the uses and disclosures that may be made of such information without patient authorization. The rule also gives patients’ rights over their health information, including the right to examine and obtain a copy of their health records and to request corrections.
c. Security Rule
The HIPAA Security Rule establishes national standards to protect individuals’ electronic personal health information that is created, received, used, or maintained by a covered entity. The Security Rule requires appropriate administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and security of electronically protected health information.
d. Employer Identifier Standard
The HIPAA requires that each employer has a standard national number that identifies them on standard transactions.
e. National Identifier Requirements
The National Provider Identifier (NPI) is a HIPAA Administrative Simplification Standard. The NPI is a unique identification number assigned to covered health care providers. Covered health care providers and all health plans and health care clearinghouses must use the NPIs in the administrative and financial transactions adopted under HIPAA. The NPI is a 10-position, intelligence-free numeric identifier (10-digit number). This means that the numbers do not carry other information about healthcare providers, such as the state in which they live or their medical specialty.
f. Enforcement Rule
The HIPAA Enforcement Rule contains provisions relating to compliance and investigation, as well as the imposition of civil monetary penalties for violations of the HIPAA Administrative Simplification Rules and procedures for hearings.
6.4. Sarbanes Oxley Act (SOA)
Enacted in 2002, the Sarbanes-Oxley Act aims to protect the public and investors by increasing the accuracy and reliability of corporate disclosures. This act does not explain how an organization must store records but describes the records that organizations must store and the duration of their storage. The Act mandated several reforms to enhance corporate responsibility, enhance financial disclosures, and combat corporate and accounting fraud. The key requirements and provisions of SOX are organized into 11 titles:
a. Title I: Public Company Accounting Oversight Board (PCAOB)
Title I consists of nine sections and establishes the Public Company Accounting Oversight Board to provide independent oversight of public accounting firms that provide audit services (“auditors”). It also creates a central oversight board tasked with registering audit services, defining the specific processes and procedures for compliance audits, inspecting and policing conduct and quality control, and enforcing compliance with the specific mandates of SOX.
b. Tile II: Auditor Independence
Title II consists of nine sections and establishes standards for external auditor independence to limit conflicts of interest. It also addresses new auditor approval requirements, audit partner rotation, and auditor reporting requirements. It restricts auditing companies from providing non-audit services (such as consulting) for the same clients.
c. Title III: Corporate Responsibility
Title III consists of eight sections and mandates that senior executives take individual responsibility for the accuracy and completeness of corporate financial reports. It defines the interaction between external auditors and corporate audit committees and specifies the corporate officers’ responsibility for the accuracy and validity of corporate financial reports. It enumerates specific limits on the behaviors of corporate officers and describes specific forfeitures of benefits and civil penalties for non-compliance.
d. Title IV: Enhanced Financial Disclosures
Title IV consists of nine sections. It describes enhanced reporting requirements for financial transactions, including off-balance-sheet transactions, Pro-forma figures, and the stock transactions of corporate officers. It requires internal controls to ensure the accuracy of financial reports and disclosures and mandates both audits and reports on those controls. It also requires timely reporting of material changes in financial conditions and specific enhanced reviews of corporate reports by the SEC or its agents.
e. Title V: Analyst Conflicts of Interest
Title V consists of only one section that discusses the measures designed to help restore investor confidence in the reporting of securities analysts. It defines the code of conduct for securities analysts and requires that they disclose any knowable conflicts of interest.
f. Title VI: Commission Resources and Authority
Title VI consists of four sections and defines practices to restore investor confidence in securities analysts. It also defines the SEC’s authority to censure or bar securities professionals from practice and defines the conditions to bar a person from practicing as a broker, advisor, or dealer.
g. Title VII: Studies and Reports
Title VII consists of five sections and requires the Comptroller General and the Securities and Exchange Commission (SEC) to perform various studies and to report their findings. The required studies and reports include the effects of the consolidation of public accounting firms, the role of credit rating agencies in the operation of securities markets, securities violations, enforcement actions, and whether investment banks assisted Enron, Global Crossing, and others to manipulate earnings and obfuscate true financial conditions.
h. Title VIII: Corporate and Criminal Fraud Accountability
Title VIII, also known as the “Corporate and Criminal Fraud Accountability Act of 2002,” consists of seven sections. It describes specific criminal penalties for the manipulation, destruction, or alteration of financial records or interference with investigations, while also providing certain protections for whistle-blowers.
i. Title IX: White-Collar-Crime Penalty Enhancement
Title IX, also known as the "White Collar Crime Penalty Enhancement Act of 2002,” consists of six sections. This title increases the criminal penalties associated with white-collar crimes and conspiracies. It recommends stronger sentencing guidelines and specifically adds failure to certify corporate financial reports as a criminal offense.
j. Tile X: Corporate Tax Returns
Title X consists of one section that states that the Chief Executive Officer should sign the company tax return.
k. Title XI: Corporate Fraud Accountability
Title XI consists of seven sections. Section 1101 recommends the following name for the title: “Corporate Fraud Accountability Act of 2002.” It identifies corporate fraud and records tampering as criminal offenses and joins those offenses to specific penalties. It also revises sentencing guidelines and strengthens penalties. Doing so enables the SEC to temporarily freeze “large” or “unusual” transactions or payments.
6.5. The Digital Millennium Copyright Act (DMCA)
The DMCA is an American copyright law that implements two 1996 treaties from the World Intellectual Property Organization (WIPO): the WIPO Copyright Treaty and the WIPO Performances and Phonograms Treaty. In order to implement US treaty obligations, the DMCA defines legal prohibitions against circumvention of the technological protection measures employed by copyright owners to protect their works, and against the removal or alteration of copyright management information. The DMCA contains five titles:
a. Title I: WIPO Treaty Implementation
Title I implements the WIPO treaties. First, it makes certain technical amendments to US law in order to provide the appropriate references and links to the treaties. Second, it creates two new prohibitions in Title 17 of the U.S. Code—one on circumvention of the technological measures used by copyright owners to protect their works and one on tampering with copyright management information—and adds civil remedies and criminal penalties for violating the prohibitions.
b. Title II: Online Copyright Infringement Liability Limitation
Title II of the DMCA adds a new section 512 to the Copyright Act to create four new limitations on liability for copyright infringement by online service providers. A service provider bases these limitations on the following four categories of conduct:
- Transitory communications
- System caching
- The user-directed storage of information on systems or networks
- Information location tools
New section 512 also includes special rules concerning the application of these limitations to nonprofit educational institutions.
c. Title III: Computer Management or Repair
Title III of the DMCA allows the owner of a copy of a program to make reproductions or adaptations when necessary to use the program in conjunction with a computer. The amendment permits the owner or lessee of a computer to make or to authorize the making of a copy of a computer program in the course of maintaining or repairing that computer.
d. Title IV: Miscellaneous(混杂的) Provisions
Title IV contains six miscellaneous provisions. The first provision announces the Clarification of the Authority of the Copyright Office; the second grants exemption for the making of “ephemeral recordings”; the third promotes study by distance education; the fourth provides an exemption for Nonprofit Libraries and Archives; the fifth allows Webcasting Amendments to the Digital Performance Right in Sound Recordings, and, finally, the sixth provision addresses concerns about the ability of writers, directors and screen actors to obtain residual payments for the exploitation of motion pictures in situations where the producer is no longer able to make these payments.
e. Title V: Protection of Certain Original Designs
Title V of the DMCA, entitles the Vessel Hull Design Protection Act (VHDPA). This act creates a new system for protecting the original designs of certain useful articles that make the article attractive or distinctive in appearance. For purposes of the VHDPA, “useful articles” are limited to the hulls (including the decks) of vessels no longer than 200 feet.
6.6. The Federal Information Security Management Act (FISMA)
The Federal Information Security Management Act of 2002 was enacted to produce several key security standards and guidelines required by Congressional legislation. The FISMA provides a comprehensive framework for ensuring the effectiveness of information security controls over information resources that support federal operations and assets. It requires each federal agency to develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or another source. The FISMA framework includes:
- Standards for categorizing information and information systems by mission impact
- Standards for the minimum-security requirements for information and information systems
- Guidance for selecting appropriate security controls for information systems
- Guidance for assessing security controls in information systems and determining their effectiveness
- Guidance for the security authorization of information systems