Halo: Recursive Proof Composition without a Trusted Setup 学习笔记
1. 引言
Bowe等人2019年论文《Halo: Recursive Proof Composition without a Trusted Setup》。
代码实现参见:
- https://github.com/zcash/halo2
- https://github.com/mir-protocol/plonky
- https://github.com/ebfull/halo
要点:
1)基于inner product argument (其中 b ⃗ = ( 1 , x , x 2 , ⋯ , x d − 1 ) \vec{b}=(1,x,x^2,\cdots,x^{d-1}) b=(1,x,x2,⋯,xd−1)) 来构建polynomial commitment scheme,其在最后一轮的proof size比Hyrax的实现少一个 G \mathbb{G} G group element。基于Bulletproofs的二分思路实现了without trusted setup。
2)指出Hyrax的方案中的“U”存在Prover作弊问题,应该类似Bulletproofs中那样基于verifier challenge来构建新的“U”值。
3)采用了一些摊销策略,减少了Verifier的计算压力。
如Verifier需计算的 b ′ = < s ⃗ , b ⃗ > b'=<\vec{s},\vec{b}> b′=<s,b>可看成是对多项式 g ( X , u 1 , u 2 , ⋯ , u k ) = ∏ i = 1 k ( u i − 1 + u i X 2 i − 1 ) g(X,u_1,u_2,\cdots,u_k)=\prod_{i=1}^{k}(u_i^{-1}+u_iX^{2^{i-1}}) g(X,u1,u2,⋯,uk)=∏i=1k(ui−1+uiX2i−1)在 x x x point的evaluation值,也可由Prover来计算并提供相应证明。
如将Verifier需计算的 G ′ = < s ⃗ , G ⃗ > G'=<\vec{s},\vec{G}> G′=<s,G>的计算看成是对多项式 g ( X , u 1 , u 2 , ⋯ , u k ) = ∏ i = 1 k ( u i − 1 + u i X 2 i − 1 ) g(X,u_1,u_2,\cdots,u_k)=\prod_{i=1}^{k}(u_i^{-1}+u_iX^{2^{i-1}}) g(X,u1,u2,⋯,uk)=∏i=1k(ui−1+uiX2i−1)的commitment,改由Prover来完成,使得Verifier只需验证该polynomial commitment是否正确即可。
4)借鉴了Sonic的helper模式,实现了双变量polynomial commitment的延迟验证,从而可将a stream of arguments的验证工作延迟到最后一个argument,将verification工作量降为几乎为logarithmic。
5)借鉴Sonic思路,将arithmetic circuit转换为证明Laurent polynomial P ( X ) P(X) P(X)的 X 0 X^0 X0 constant term的系数为0。
6)构建了Tweedledum和Tweedledee的非pairing-friendly的2-cycle curve,具有endomorphism属性,可用于优化verifier challenge值,提升计算效率。
Non-interactive arguments of knowledge可用于demonstrate the faithful execution of arbitrary computations with publicly verifiable proofs。
借助recursive proof composition,可对large computational effort进行incrementally verify。
之前实现的recursive proof composition 都需要trusted setup和cycles of expensive pairing-friendly elliptic curves。
本文实现的Halo算法:
- 是第一个实用的recursive proof composition without a trusted setup;
- 基于discrete log assumption over normal cycles of elliptic curves。
zk-SNARKs全称为:zero-knowledge succinct non-interactive arguments of knowledge。
当前效率最高的zk-SNARKs都需要pairing-friendly elliptic curves和trusted setup,但是具有small, constant-size proofs with constant-time verification。如Groth 2016年论文《On the size of pairing-based non-interactive arguments》。
- Gennaro 等人2010年论文《Non-interactive verifiable computing: Outsourcing computation to untrusted workers》中提出,将zk-SNARKs用于verifiable computation,将computation委托给不可信第三方,第三方在返回结果的同时提供cryptographic proof来证明结果是正确的。理论上,要求该proof要更小,且相比于直接计算更易于验证,即要求zk-SNARKs具有succinctness属性。
- Valiant 2008年论文《Incrementally verifiable computation or proofs of knowledge imply time/space efficiency》中引入了incrementally verifiable computation的概念,其proof不仅证明the correct execution of a computation,还保证the validity of a previous proof。这样,a large and virtually unbounded amount of computation can be verified with a single proof, and with this proof alone we may extend the computation with further proofs。
受incrementally verifiable computation启发,可将区块链看成是需要所有参与方下载区块链上的所有历史记录,仅仅是为了validate each individual state transition (transaction) merely in order to validate and process new state changes。SNARKs allow us to partially address this scalability problem by outsourcing some of these verification steps to a third party,但是参与方仍然需要下载并验证每一个proof。Incrementally verifiable computation可解决该问题,使用a single proof来证明the correctness of many previous proofs,参与方仅需要下载当前状态和证明该状态是正确的proof,further proofs of state changes can be constructed with the latest proof alone, allowing active participants to prune old state changes。
本文借助recursive proof composition来实现incremental verifiable computation。这些proofs可用于保证the satisfaction of compliance predicates between old and new states,从而可引出proof-carrying data 概念(参见 2010年Chiesa等人论文《Proof-Carrying Data and hearsay arguments from signature cards》)。proof-carrying data概念可用于实现verifiable distributed computations(参见Bitansky等人2013年论文《Recursive composition and bootstrapping for SNARKs and Proof-Carrying Data》)。
- Ben-Sasson等人2014年论文《Scalable Zero Knowledge via cycles of elliptic curve》中,第一次实现了实用的recursive proof composition,其依赖于SNARKs built over pairing-friendly elliptic curves。
Elliptic curve groups通常instantiated over a base field F p \mathbb{F}_p Fp,但是这些groups具有的prime order q q q通常不等于 p p p,因此用于demonstrate satisfiability of an arithmetic circuit over the scalar field F q \mathbb{F}_q Fq 所构建的SNARK 无法efficiently encode the F p \mathbb{F}_p Fp arithmetic needed to verify its own proofs。
在该论文中,Ben-Sasson等人通过构建2-cycle of pairing-friendly elliptic curves such that the base field of either curve is the scalar field of the other 来规避该问题。但是,Chiesa等人2018年论文《On cycles of pairing-friendly elliptic curves》中指出,目前仅有一个pairing-friendly curves family满足该要求,而该curves family的embedding degree很低,需要基于large (780-bit) field才能构建足够安全的curve,field太大会影响pairing计算性能。而且更重要的是,现有的所有pairing-based SNARKs,均需要trusted setup。
1.1 主要贡献
-
理论上,可用任意的zk-SNARK来实现recursive proof composition。Ben-Sasson等人在2018年论文《Scalable, transparent, and post-quantum secure computational integrity》中提出的STARKs算法,不需要trusted setup。目前暂无对recursive proof composition的实用实现,如STARKs对相对简单computation的proof size都在几百kB。
本文提出的Halo算法,是第一个实用的recursive proof composition without a trusted setup。与Ben-Sasson等人2014年论文《Scalable Zero Knowledge via cycles of elliptic curve》中的思路类似,本文使用了cycle of elliptic curves,使得proofs constructed with one curve can efficiently verify proofs constructed over the other。但是,对任一曲线均不要求为pairing-friendly,包含了normal 255-bit prime-order curves的cycle,其具有的security level 接近128-bit。且Halo中的proof size和verification time并不会随着recursion depth的增加而增加。 -
提出了基于inner product argument具有amortized succinctness的polynomial commitment scheme。
(参见博客 Hyrax: Doubly-efficient zkSNARKs without trusted setup学习笔记)
受Wahby等人2018年论文《Doubly-efficient zkSNARKs without trusted setup》中的dot-product proof protocol启发,发现利用the smooth structure of vectors that the verifier must work with, we can amortize away (across many proofs) the linear-time verification operation for commitment openings with the assistance of an untrusted third party “helper”。特别地,与perform a linear-time operation for each commitment opening proof不同,“helper”会提供the claimed output of these linear-time operations for each proof,然后用 a new argument来demonstrate that every claimed output was correct。该new argument仍然需要Verifier做linear-time操作,但是此时,仅需要对整个proofs batch做一次linear-time operation即可。这种策略使得我们可以build proofs for arithmetic circuit satisfiability,其边界verification time为logarithmic in the size of the circuit——相比于Bulletproofs的linear verification time有了改进。“help”的作用类似于Maller等人2019年《Sonic: Zero-Knowledge SNARKs from linear-size universal and updatable Structured Reference Strings》中第8节的helped variant的作用,但是,本文的“helper”无需trusted setup。 -
Nested Amortization嵌套摊销
之前实现recursive proof composition的思路均为:
– 首先build a fully succinct, non-interactive argument system;
– 然后构建 a verification circuit for this system。
由于succinctness属性的要求,at some threshold the verification circuit will be smaller than the size of the circuit being checked, allowing arbitrary-depth recursion to be achieved。
基于elliptic curve groups构建的argument systems具有smallest communication complexity known in the literature,但是这些argument systems 要么需要trusted setup (如所有的pairing-based SNARKs),要么需要linear-time verifiers且not fully succinct (如Bulletproofs)。
本文主要贡献是通过采用amortization strategy来reduce verification circuit size。本文 verification circuit 从来不自己做linear-time operations,而仅take the input and (claimed) output of the linear-time operation to be public inputs to the circuit,i.e. they are encoded in the statement being proven。The circuit proceeds on the assumption that the claimed output is correct and so the circuit is sublinear in size. This effectively defers the full verification of the “inner” proof to the verifier, who must also perform a similar linear-time operation to check the “outer” proof. 借助“helper”,Verifier可将这2种计算压缩为一种。 -
2-cycle of elliptic curves:
本文所使用的2-cycle elliptic curves分别称为Tweedledum和Tweedledee,具有attractive performance和security。其cyclic nature可高效express 类似 Ben-Sasson等人2014年论文《Scalable Zero Knowledge via cycles of elliptic curve》中的 verification circuits。本文所选择的这两种曲线支持特定的endomorphisms,可用于reduce the size of the verification circuit。
1.2 同期研究成果
-
Chiesa等人2019年论文《Fractal: Post-quantum and transparent recursive proofs from holography》中基于高效的low-degree testing技术,构建了recursive zero-knowledge protocol,具有plausible post-quantum security和full succinctness。
本文的Verifier’s work is linear in the circuit size,不具有fully succinct,但是128-bit security level 情况下,本文的fully-recursive proofs size为3.5KB,而Fractal的size 超过120KB。
另外,Halo的recursion threshold为小于 2 17 2^{17} 217个multiplication gates,比Fractal的小一个数量级,Halo has the potential for substantially reducing proving time/memory requirements。 -
Bu¨nz等人2019年论文《Supersonic: Transparent SNARKs from DARK compilers》中基于unknown order groups 构建了zk-SNARK,无需trusted setup。不清楚与本文的竞争对比。
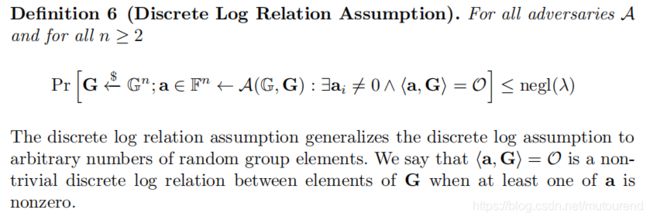
2. 基于的安全假设
- Discrete Log Relation Assumption:
即已知 G ⃗ ∈ G n \vec{G}\in\mathbb{G}^n G∈Gn,查找 a ⃗ \vec{a} a,其中至少有一个 a i ≠ 0 a_i\neq 0 ai=0,使得 < a ⃗ , G ⃗ > = O <\vec{a},\vec{G}>=\mathcal{O} <a,G>=O。
3. Polynomial commitments
Kate等人2010年论文《Constant-size commitments to polynomials and their applications》中首次提出了Polynomial commitment scheme。
目前polynomial commitment被广泛用于现代知识证明算法中,如:
- Maller等人2019年论文《Sonic: Zero-Knowledge SNARKs from linear-size universal and updatable Structured Reference Strings》;
- Chiesa等人2020年论文《Marlin: Preprocessing zkSNARKs with universal and updatable SRS》;
- Gabizon等人2019年论文《PLONK: Permutations over Lagrange-bases for Oecumenical Noninteractive arguments of Knowledge》;
- Bu¨nz等人2019年论文《Supersonic: Transparent SNARKs from DARK compilers》
本文基于Wahby等人2018年论文《Hyrax: Doubly-efficient zkSNARKs without trusted setup》中的多变量polynomial commitment(其本质为基于Bulletproofs进行调整的inner product argument)提出了单变量polynomial commitment scheme,包含的算法有 ( S e t u p , C o m m i t , O p e n , V e r i f y O p e n ) (Setup, Commit, Open, VerifyOpen) (Setup,Commit,Open,VerifyOpen)。
假设polynomial p ( X ) p(X) p(X) 的degree bound为 d − 1 d-1 d−1,则:
- S e t u p ( 1 λ , d ) Setup(1^{\lambda}, d) Setup(1λ,d):输出为common reference string σ = ( G , F p , G ⃗ , H ) \sigma=(\mathbb{G},\mathbb{F}_p,\vec{G},H) σ=(G,Fp,G,H) for group G \mathbb{G} G of prime order p p p, with random G ⃗ ∈ G d \vec{G}\in\mathbb{G}^d G∈Gd and H ∈ G H\in\mathbb{G} H∈G。
- C o m m i t ( σ , p ( X ) ; r ) = < a ⃗ , G ⃗ > + [ r ] H Commit(\sigma,p(X);r)=<\vec{a},\vec{G}>+[r]H Commit(σ,p(X);r)=<a,G>+[r]H,其中 r r r为blinding factor, a i ∈ F a_i\in\mathbb{F} ai∈F为多项式 p ( X ) p(X) p(X)的 i i ith degree term 系数, p ( X ) ∈ F p [ X ] p(X)\in\mathbb{F}_p[X] p(X)∈Fp[X]为maximal degree d − 1 d-1 d−1。可将其看成是对多项式系数的Pedersen vector commitment,具有很好的hiding和加法同态属性——对于 ∀ a , b , r , s ∈ F p , p ( X ) , q ( X ) ∈ F p [ X ] \forall a,b,r,s\in\mathbb{F}_p, p(X),q(X)\in\mathbb{F}_p[X] ∀a,b,r,s∈Fp,p(X),q(X)∈Fp[X],有:
[ a ] C o m m i t ( σ , p ( X ) ; r ) + [ b ] C o m m i t ( σ , q ( X ) ; s ) = C o m m i t ( σ , a ⋅ p ( X ) + b ⋅ q ( X ) ; a r + b s ) [a]Commit(\sigma,p(X);r)+[b]Commit(\sigma,q(X);s)=Commit(\sigma,a\cdot p(X)+b\cdot q(X); ar+bs) [a]Commit(σ,p(X);r)+[b]Commit(σ,q(X);s)=Commit(σ,a⋅p(X)+b⋅q(X);ar+bs) - O p e n ( p ( X ) , x ) Open(p(X),x) Open(p(X),x):输出为 v ∈ F p v\in\mathbb{F}_p v∈Fp。
- V e r i f y O p e n ( P , x , v ) VerifyOpen(P,x,v) VerifyOpen(P,x,v):判断the polynomial contained “inside” the commitment P P P evaluates to v v v at x x x。输出为1表示接受,0表示拒绝。
然后可将 ( S e t u p , O p e n , V e r i f y O p e n ) (Setup,Open,VerifyOpen) (Setup,Open,VerifyOpen)看成是a PSHVZK (perfect special honest-verifier zero knowledge) argument of knowledge for the relation:
{ ( ( P , x , v ) : ( a ⃗ , r ) ) : P = < a ⃗ , G ⃗ > + [ r ] H ∧ v = < a ⃗ , ( 1 , x , x 2 , ⋯ , x d − 1 ) > } \{((P,x,v):(\vec{a},r)): P=<\vec{a},\vec{G}>+[r]H\wedge v=<\vec{a},(1,x,x^2,\cdots,x^{d-1})>\} { ((P,x,v):(a,r)):P=<a,G>+[r]H∧v=<a,(1,x,x2,⋯,xd−1)>}
以上relation 可用于证明 the polynomial contained “inside” the commitment P P P evaluates to v v v at x x x,甚至 the committed polynomial has maximum degree d − 1 d-1 d−1。
基本信息展开为:
- public info: P ∈ G , x , v ∈ F p P\in\mathbb{G},x,v\in\mathbb{F}_p P∈G,x,v∈Fp
- private info: a ⃗ ∈ F p n , r ∈ F p \vec{a}\in\mathbb{F}_p^n,r\in\mathbb{F}_p a∈Fpn,r∈Fp
- relation: P = < a ⃗ , G ⃗ > + [ r ] H ∧ v = < a ⃗ , ( 1 , x , x 2 , ⋯ , x d − 1 ) > P=<\vec{a},\vec{G}>+[r]H\wedge v=<\vec{a},(1,x,x^2,\cdots,x^{d-1})> P=<a,G>+[r]H∧v=<a,(1,x,x2,⋯,xd−1)>
详细的思路为:
- Verifier:生成随机group element U ∈ G U\in\mathbb{G} U∈G,将 U ∈ G U\in\mathbb{G} U∈G发送给Prover。
- Prover和Verifier:都计算 P ′ = P + [ v ] U P'=P+[v]U P′=P+[v]U。
- Prover:转为证明Prover知道 a ⃗ ∈ F p d , r , v ′ ∈ F p \vec{a}\in\mathbb{F}_p^d,r,v'\in\mathbb{F}_p a∈Fpd,r,v′∈Fp,使得 P ′ = < a ⃗ , G ⃗ > + [ r ] H + [ v ′ ] U P'=<\vec{a},\vec{G}>+[r]H+[v']U P′=<a,G>+[r]H+[v′]U成立,其中 v ′ = < a ⃗ , ( 1 , x , x 2 , ⋯ , x d − 1 ) > v'=<\vec{a},(1,x,x^2,\cdots,x^{d-1})> v′=<a,(1,x,x2,⋯,xd−1)>。若Prover无法提前知道 U U U,则 v = v ′ v=v' v=v′成立。【注意,本文的“U”由Verifier在收到commitment P P P之后才提供,Bulletproofs中的也类似,而Hyrax中的dot-product proof protocol中没有做相应约定,存在prover在 P P P中包含 U U U信息,进而伪造证明的情况——a prover with malicious control of P P P would then be able to interfere with the argument by including terms involving U U U in P P P。】(参见博客 Hyrax: Doubly-efficient zkSNARKs without trusted setup学习笔记 第4.2节“dot-product proof with Bulletproofs”)
Bulletproofs中实现的基本信息为:(此处的 U U U由Verifier先知道 P = < a ⃗ , G ⃗ > + < b ⃗ , H ⃗ > P=<\vec{a},\vec{G}>+<\vec{b},\vec{H}> P=<a,G>+<b,H>后,发送challenge x ∈ F x\in\mathbb{F} x∈F,然后Prover和Verifier重新计算的 U = x U ∈ G U=xU\in\mathbb{G} U=xU∈G。)【非zero-knowledge的inner product argument】
- public info:commitment P ′ P' P′,generators G ⃗ , H ⃗ ∈ G d , U ∈ G \vec{G},\vec{H}\in\mathbb{G}^d,U\in\mathbb{G} G,H∈Gd,U∈G。
- private info: a ⃗ , b ⃗ ∈ F d \vec{a},\vec{b}\in\mathbb{F}^d a,b∈Fd。
- relation: P ′ = < a ⃗ , G ⃗ > + < b ⃗ , H ⃗ > + [ < a ⃗ , b ⃗ > ] U P'=<\vec{a},\vec{G}>+<\vec{b},\vec{H}>+[<\vec{a},\vec{b}>]U P′=<a,G>+<b,H>+[<a,b>]U
本文针对的情况是,其中 b ⃗ = ( 1 , x , x 2 , ⋯ , x n − 1 ) \vec{b}=(1,x,x^2,\cdots,x^{n-1}) b=(1,x,x2,⋯,xn−1) 为public info,对Prover和Verifier均已知,所以,此时不再需要 H ⃗ ∈ G d \vec{H}\in\mathbb{G}^d H∈Gd。根据需要,可额外再引入generator H ∈ G H\in\mathbb{G} H∈G来实现blinding both prover messages and the commitment P ′ P' P′。最终基本信息为:
- public info:commitment P ′ P' P′,generators G ⃗ ∈ G d , H , U ∈ G \vec{G}\in\mathbb{G}^d, H, U\in\mathbb{G} G∈Gd,H,U∈G 和 b ⃗ ∈ F d \vec{b}\in\mathbb{F}^d b∈Fd。
- private info: a ⃗ ∈ F d \vec{a}\in\mathbb{F}^d a∈Fd和blinding r ∈ F r\in\mathbb{F} r∈F。
- relation: P ′ = < a ⃗ , G ⃗ > + r H + [ < a ⃗ , b ⃗ > ] U P'=<\vec{a},\vec{G}>+rH+[<\vec{a},\vec{b}>]U P′=<a,G>+rH+[<a,b>]U。
假设 d = 2 k , k > 0 d=2^k,k>0 d=2k,k>0,Prover初始化 G ⃗ ′ = G ⃗ , a ⃗ ′ = a ⃗ , b ⃗ ′ = b ⃗ , P = P ′ \vec{G}'=\vec{G},\vec{a}'=\vec{a},\vec{b}'=\vec{b},P=P' G′=G,a′=a,b′=b,P=P′,然后进行 k k k轮交互,其中 in the j j jth round (starting with j = k j=k j=k and finishing with j = 1 j=1 j=1):
1)若 d = 1 d=1 d=1,则:【目前有2种实现思路。】
1.1)Hyrax中的思路为:【此时有 P = a ′ G ′ + r H + a ′ b ′ U P=a'G'+rH+a'b'U P=a′G′+rH+a′b′U,其中 a ′ , r ∈ F a',r\in\mathbb{F} a′,r∈F为private info, b ′ ∈ F , G ′ , H , U , P ∈ G b'\in\mathbb{F}, G',H,U,P\in\mathbb{G} b′∈F,G′,H,U,P∈G均为public info。】
- Prover:引入Prover私有blinding随机数 d , r δ , r β ← F d,r_{\delta},r_{\beta}\leftarrow\mathbb{F} d,rδ,rβ←F,计算 δ = d G ′ + r δ H , β = d U + r δ H \delta=dG'+r_{\delta}H, \beta=dU+r_{\delta}H δ=dG′+rδH,β=dU+rδH,将 δ , β ∈ G \delta,\beta\in\mathbb{G} δ,β∈G发送给Verifier。
- Verifier:发送challenge c ← F c\leftarrow \mathbb{F} c←F 给Prover。
- Prover:计算 z 1 = d + c ⋅ a ′ b ′ , z 2 = b ′ ( c ⋅ r + r β ) + r δ z_1=d+c\cdot a'b', z_2=b'(c\cdot r+r_{\beta})+r_{\delta} z1=d+c⋅a′b′,z2=b′(c⋅r+rβ)+rδ,将 z 1 , z 2 ∈ F z_1,z_2\in\mathbb{F} z1,z2∈F发送给Verifier。
- Verifier:验证 b ′ ( c P + β ) + δ = z 1 ( G ′ + b ′ U ) + z 2 H b'(cP+\beta)+\delta=z_1(G'+b'U)+z_2H b′(cP+β)+δ=z1(G′+b′U)+z2H是否成立即可。
1.2)本文的思路为(相比于Hyrax方案,proof size少了一个group element G \mathbb{G} G):【此时有 P = [ a ′ ] G ′ + [ r ] H + [ a ′ b ′ ] U = [ a ′ ] ( G + [ b ′ ] U ) + [ r ] H P=[a']G'+[r]H+[a'b']U=[a'](G+[b']U)+[r]H P=[a′]G′+[r]H+[a′b′]U=[a′](G+[b′]U)+[r]H,其中 a ′ , r ∈ F a',r\in\mathbb{F} a′,r∈F为private info, b ′ ∈ F , G ′ , H , U , P ∈ G b'\in\mathbb{F}, G',H,U,P\in\mathbb{G} b′∈F,G′,H,U,P∈G均为public info。】(其中 ( G + [ b ′ ] U ) (G+[b']U) (G+[b′]U)为public info,可直接用 博客 基于Sigma protocol实现的零知识证明protocol集锦 第2.4节 “2.4 Protocol 4. Knowledge of the opening of Pedersen commitment”来计算。)
- Prover:引入Prover私有blinding随机数 d , r δ ← F d,r_{\delta}\leftarrow\mathbb{F} d,rδ←F,计算 δ = d ( G ′ + b ′ U ) + r δ H \delta=d(G'+b'U)+r_{\delta}H δ=d(G′+b′U)+rδH,将 δ ∈ G \delta \in\mathbb{G} δ∈G发送给Verifier。
- Verifier:发送challenge c ← F c\leftarrow \mathbb{F} c←F 给Prover。
- Prover:计算 z 1 = d + a ′ c , z 2 = r δ + r c z_1=d+a'c, z_2=r_{\delta}+rc z1=d+a′c,z2=rδ+rc,将 z 1 , z 2 ∈ F z_1,z_2\in\mathbb{F} z1,z2∈F发送给Verifier。
- Verifier:验证 c P + δ = z 1 ( G ′ + b ′ U ) + z 2 H cP+\delta=z_1(G'+b'U)+z_2H cP+δ=z1(G′+b′U)+z2H是否成立即可。
2)若 d > 1 d>1 d>1,则 j = log 2 d , d ′ = d 2 j=\log_2{d}, d'=\frac{d}{2} j=log2d,d′=2d,有:
-
Prover:计算:
d ′ = d / 2 d'=d/2 d′=d/2。
引入Prover私有blinding随机数 l j , r j ← F l_j,r_j\leftarrow\mathbb{F} lj,rj←F,计算 L j = < a ⃗ l o ′ , G ⃗ h i ′ > + [ l j ] H + [ < a ⃗ l o ′ , b ⃗ h i ′ > ] U L_j=<\vec{a}'_{lo},\vec{G}'_{hi}>+[l_j]H+[<\vec{a}'_{lo},\vec{b}'_{hi}>]U Lj=<alo′,Ghi′>+[lj]H+[<alo′,bhi′>]U, R j = < a ⃗ h i ′ , G ⃗ l o ′ > + [ r j ] H + [ < a ⃗ h i ′ , b ⃗ l o ′ > ] U R_j=<\vec{a}'_{hi},\vec{G}'_{lo}>+[r_j]H+[<\vec{a}'_{hi},\vec{b}'_{lo}>]U Rj=<ahi′,Glo′>+[rj]H+[<ahi′,blo′>]U。
将 L j , R j ∈ G L_j,R_j\in\mathbb{G} Lj,Rj∈G发送给Verifier。 -
Verifier:发送random challenge u j ∈ F u_j\in\mathbb{F} uj∈F 给Prover。
-
Prover:计算:
a ⃗ ′ = a ⃗ h i ′ ⋅ u j − 1 + a ⃗ l o ′ ⋅ u j \vec{a}'=\vec{a}'_{hi}\cdot u_j^{-1}+\vec{a}'_{lo}\cdot u_j a′=ahi′⋅uj−1+alo′⋅uj
r ′ = l j u j 2 + r + r j u j − 2 r'=l_ju_j^2+r+r_ju_j^{-2} r′=ljuj2+r+rjuj−2 -
Prover和Verifier:计算:
b ⃗ ′ = b ⃗ l o ′ ⋅ u j − 1 + b ⃗ h i ′ ⋅ u j \vec{b}'=\vec{b}'_{lo}\cdot u_j^{-1}+\vec{b}'_{hi}\cdot u_j b′=blo′⋅uj−1+bhi′⋅uj
G ⃗ ′ = G ⃗ l o ′ ⋅ u j − 1 + G ⃗ h i ′ ⋅ u j \vec{G}'=\vec{G}'_{lo}\cdot u_j^{-1}+\vec{G}'_{hi}\cdot u_j G′=Glo′⋅uj−1+Ghi′⋅uj
P ′ = [ u j 2 ] L j + P + [ u j − 2 ] R j P'= [u_j^2]L_j+P+ [u_j^{-2}]R_j P′=[uj2]Lj+P+[uj−2]Rj -
设置 d = d ′ , P = P ′ , r = r ′ d=d',P=P',r=r' d=d′,P=P′,r=r′,继续从步骤1)开始执行。
在以上证明过程中,关注Prover在每轮递归调用时计算的内容:
a ⃗ ′ = a ⃗ h i ′ ⋅ u j − 1 + a ⃗ l o ′ ⋅ u j \vec{a}'=\vec{a}'_{hi}\cdot u_j^{-1}+\vec{a}'_{lo}\cdot u_j a′=ahi′⋅uj−1+alo′⋅uj
b ⃗ ′ = b ⃗ l o ′ ⋅ u j − 1 + b ⃗ h i ′ ⋅ u j \vec{b}'=\vec{b}'_{lo}\cdot u_j^{-1}+\vec{b}'_{hi}\cdot u_j b′=blo′⋅uj−1+bhi′⋅uj
G ⃗ ′ = G ⃗ l o ′ ⋅ u j − 1 + G ⃗ h i ′ ⋅ u j \vec{G}'=\vec{G}'_{lo}\cdot u_j^{-1}+\vec{G}'_{hi}\cdot u_j G′=Glo′⋅uj−1+Ghi′⋅uj
- 与最后一轮 d = 1 d=1 d=1时的 G ′ ∈ G , b ′ ∈ F G'\in\mathbb{G},b'\in\mathbb{F} G′∈G,b′∈F之间的关系为 G ′ = < s ⃗ , G ⃗ > , b ′ = < s ⃗ , b ⃗ > G'=<\vec{s},\vec{G}>,b'=<\vec{s},\vec{b}> G′=<s,G>,b′=<s,b>,其中 s ⃗ \vec{s} s为:
s ⃗ = ( u 1 − 1 u 2 − 1 ⋯ u k − 1 , u 1 u 2 − 1 ⋯ u k − 1 , u 1 − 1 u 2 ⋯ u k − 1 , u 1 u 2 ⋯ u k − 1 , ⋮ u 1 u 2 ⋯ u k ) \vec{s}=(u_1^{-1}u_2^{-1}\cdots u_k^{-1}, \\ u_1 u_2^{-1}\cdots u_k^{-1}, \\ u_1^{-1}u_2\cdots u_k^{-1},\\ u_1u_2\cdots u_k^{-1},\\ \vdots \\ u_1u_2\cdots u_k) s=(u1−1u2−1⋯uk−1,u1u2−1⋯uk−1,u1−1u2⋯uk−1,u1u2⋯uk−1,⋮u1u2⋯uk) - Verifier在最后一轮收到的commitment P ′ P' P′,满足以下公式:
P ′ = ∑ j = 1 k ( [ u j 2 ] L j ) + P + ∑ j = 1 k ( [ u j − 2 ] R j ) P'= \sum_{j=1}^{k}([u_j^2]L_j)+P+ \sum_{j=1}^{k}([u_j^{-2}]R_j) P′=∑j=1k([uj2]Lj)+P+∑j=1k([uj−2]Rj) - Prover在最后一轮的blinding值 r ′ r' r′满足如下公式:
r ′ = ∑ j = 1 k ( l j u j 2 ) + r + ∑ j = 1 k ( r j u j − 2 ) r'=\sum_{j=1}^{k}(l_ju_j^2)+r+\sum_{j=1}^{k}(r_ju_j^{-2}) r′=∑j=1k(ljuj2)+r+∑j=1k(rjuj−2)
3.1 Amortization Strategy摊销策略
以上polynomial commitment,尽管其communication complexity为 O ( log 2 ( d ) ) O(\log_2(d)) O(log2(d)),其中 d − 1 d-1 d−1为多项式的degree bound,但是Verifier必须在验证时计算 G ′ = < s ⃗ , G ⃗ > , b ′ = < s ⃗ , b ⃗ > G'=<\vec{s},\vec{G}>,b'=<\vec{s},\vec{b}> G′=<s,G>,b′=<s,b>,其中 s ⃗ = ( u 1 − 1 u 2 − 1 ⋯ u k − 1 , u 1 u 2 − 1 ⋯ u k − 1 , u 1 − 1 u 2 ⋯ u k − 1 , u 1 u 2 ⋯ u k − 1 , ⋮ u 1 u 2 ⋯ u k ) \vec{s}=(u_1^{-1}u_2^{-1}\cdots u_k^{-1}, \\ u_1 u_2^{-1}\cdots u_k^{-1}, \\ u_1^{-1}u_2\cdots u_k^{-1},\\ u_1u_2\cdots u_k^{-1},\\ \vdots \\ u_1u_2\cdots u_k) s=(u1−1u2−1⋯uk−1,u1u2−1⋯uk−1,u1−1u2⋯uk−1,u1u2⋯uk−1,⋮u1u2⋯uk)。
注意,本文针对的情况是 b ⃗ = ( 1 , x , x 2 , ⋯ , x n − 1 ) \vec{b}=(1,x,x^2,\cdots,x^{n-1}) b=(1,x,x2,⋯,xn−1)为public info的情况,其中的 < s ⃗ , b ⃗ > <\vec{s},\vec{b}> <s,b>可看成对多项式:【注意,感觉论文的 g ( X , u 1 , u 2 , ⋯ , u k ) g(X,u_1,u_2,\cdots,u_k) g(X,u1,u2,⋯,uk)公式有点问题,但是作者说木问题。。。】
g ( X , u 1 , u 2 , ⋯ , u k ) = ∏ i = 1 k ( u i − 1 + u i X 2 i − 1 ) g(X,u_1,u_2,\cdots,u_k)=\prod_{i=1}^{k}(u_i^{-1}+u_iX^{2^{i-1}}) g(X,u1,u2,⋯,uk)=∏i=1k(ui−1+uiX2i−1)
在point x x x的evaluation值,即 b ′ = < s ⃗ , b ⃗ > = g ( x , u 1 , u 2 , ⋯ , u k ) b'=<\vec{s},\vec{b}>=g(x,u_1,u_2,\cdots,u_k) b′=<s,b>=g(x,u1,u2,⋯,uk)。Verifier可计算该evaluation值in logarithmic time。
但是,对于 G ′ = < s ⃗ , G ⃗ > G'=<\vec{s},\vec{G}> G′=<s,G>计算,仍然需要a linear-time multiscalar multiplication。但是仔细观察,可将 G ’ G’ G’看成是对多项式 g ( X , u 1 , u 2 , ⋯ , u k ) g(X,u_1,u_2,\cdots,u_k) g(X,u1,u2,⋯,uk)系数的commitment值:
G ′ = C o m m i t ( σ , g ( X , u 1 , u 2 , ⋯ , u k ) ) G'=Commit(\sigma, g(X,u_1,u_2,\cdots,u_k)) G′=Commit(σ,g(X,u1,u2,⋯,uk))
所以 与其让Verifier为 m m m个(independent)arguments 自己计算 G i ′ G'_i Gi′,不如将该计算外包给不可信的第三方“helper“ ,”helper”在提供 G 1 ′ , G 2 ′ , ⋯ , G m ′ G_1',G_2',\cdots,G_m' G1′,G2′,⋯,Gm′ (for m m m separate arguments) 计算结果的同时提供相应的argument that each are correct by demonstrating that a random linear combination of the commitments opens at a random point to a value the verifier can compute in time O ( m log ( d ) ) O(m\log(d)) O(mlog(d))。基于Schwartz-Zippel Lemma,”helper“可让Verifier信服其结果是正确计算的(其伪造成功的概率不高于 d − 1 p − 1 \frac{d-1}{p-1} p−1d−1)。
也就是说,此时,Verifier需调用“helper“运行对 g ( X , u 1 , u 2 , ⋯ , u k ) g(X,u_1,u_2,\cdots,u_k) g(X,u1,u2,⋯,uk)的polynomial commitment opening protocol,最终Verifier仍需要进行一次linear-time operation,但是通过此操作,the verifier has traded m m m linear-time operations for one, with a marginal cost that is logarithmic in the degree bound。
3.2 Nested Amortization嵌套摊销
通常,实现recursive proof composition需要:
- 首先获得a non-interactive argument of knowledge for arithmetic circuit satisfiability,如 C ( x , w ) = 1 C(x,w)=1 C(x,w)=1 for auxiliary input w w w and public input x x x。
- 然后encode the verification algorithm for this argument into such an arithmetic circuit。
假设a proof的verification circuit is sublinear in the size of the circuit,则存在某个阈值,使得recursively verify proofs 成为可能。本文并未实现a protocol which can be fully verified in sublinear time,因此如果只是naively apply this strategy并不能yield results beyond fixed-depth composition。通过里利用论文第五章的sublinear marginal verification time and logarithmic proof size protocol,本文提出了一种可避免在每一层recursion中都需要fully verifying proofs的技术。
Arithmetic circuits通常可以constraint system形式表示:已知a satisfying assignment of variables (the prover’s witness), the satisfaction of the constraint system implies the satisfiability of the circuit。在该过程中,the inherent non-determinism是some expensive operations可由Prover来协助完成。举个例子:在circuits中,当需要对field variable u u u求倒数,直观的做法是利用 u p − 1 ≡ 1 m o d p u^{p-1}\equiv 1\ mod\ p up−1≡1 mod p,求解其倒数 u − 1 = u p − 2 m o d p u^{-1}=u^{p-2}\ mod\ p u−1=up−2 mod p需要 log ( p ) \log(p) log(p)个multiplication constraints,改为:由Prover来提供witness v = u − 1 v=u^{-1} v=u−1,为证明其倒数关系只需引入一个multiplication constraint u v = 1 uv=1 uv=1。
本文利用了该non-determinism进行优化:当circuit中包含了an expensive fixed operation f f f that is invoked with some input x x x,就改为由Prover来witness y = f ( x ) y=f(x) y=f(x),然后将 ( x , y ) (x,y) (x,y)作为circuit的public inputs。在假设 y y y是正确的情况下,circuit将继续运行,将验证 y y y的正确性的责任转给Verifier的proof (delegating the responsibility of checking the correctness of y y y to the verifier of the proof)。
本文的proof composition中,Verifier不执行任何linear-time (or otherwise expensive) operation f f f,而是将 x x x和Prover所声称的 y = f ( x ) y=f(x) y=f(x)作为public inputs 并入到verification circuit中。注意,当proofs are continually composed时,increasing instances of ( x , y ) (x,y) (x,y) accumulate because the verification circuit will not check them but rather continually delegate these checks to its verifier。为了避免这种runaway cost,引入了如下摊销策略:
已知instances ( x , y ) (x,y) (x,y)和 ( x ′ , y ′ ) (x',y') (x′,y′),Prover将提供a non-interactive proof that y = f ( x ) y=f(x) y=f(x) and y ′ = f ′ ( x ′ ) y'=f'(x') y′=f′(x′) as a witness to the verification circuit,and the verification circuit will check this proof。
为了fully check this amortization proof,the verification circuit可能需要perform a linear-time (or otherwise expensive) operation。但是,若该operation是类似inovking f f f,则Verifier相当于将2个instances ( x , y ) (x,y) (x,y)和 ( x ′ , y ′ ) (x',y') (x′,y′)压缩为了1个新的instance ( x ′ ′ , y ′ ′ ) (x'', y'') (x′′,y′′),从而允许随着proofs的生成,摊销掉invoking f f f的成本。 f f f仅在circuit的“outside” 由 the ultimate verifier 仅invoke一次,从而可证明整个underlying tree of proofs的正确性。
在论文第五章介绍的PSHVZK argument就是利用了该嵌套摊销策略,利用本博文3.1节提到的polynomial commitment amortization技术。可描述为:
- P r o v e r → V e r i f i e r Prover\rightarrow Verifier Prover→Verifier: a stream of arguments。
- Verifie:maintain logarithmic-size state 和 perform logarithmic-time operations to partially verify each proof in sequence。最终,at the end of a stream of proofs, the verifier will choose to accept or reject all of them simultaneously in linear time。
借助Fia-Shamir heuristic,可将以上argument转为non-interactive zero-knowledge argument of knowledge。最终实现的就是nested amortization嵌套摊销技术的雏形,其中由Verifier maintain的”state”都是the deferred values that are shepherded(带领/护送) through public inputs。从而可实现任意depth 的recursive proof,而the verifier outside the circuit 仅需对the verifier state验证一次即可,在circuit里面不存在任何linear-time operation。
4. Main Argument
本文是在Sonic main argument的基础上引入了polynomial commitment scheme进行改进。
首先考虑一种简单的场景,即:
对固定的circuit C C C,Prover重复多次与Verifier交互来生成multiple arguments in sequence。
而本文的目的是,Verifier仅需要perform logarithmic marginal work来决定accept or reject all of the arguments simultaneously。
接下来,假设 N , Q , k N,Q,k N,Q,k为整数,且 d = 4 N = 2 k , 3 Q < d d=4N=2^k, 3Q
Prover为了证明 C ( x , w ) = 1 C(x,w)=1 C(x,w)=1 without reveal w w w,其中 x x x为 public input, w w w为witness,可将circuit C C C表示为arithmetic constraints system——包含 N N N个multiplication constraints和 Q Q Q个linear constraints,即转为Prover知道witness a ⃗ , b ⃗ , c ⃗ ∈ F N \vec{a},\vec{b},\vec{c}\in\mathbb{F}^N a,b,c∈FN,使得:
a i ⋅ b i = c i a_i\cdot b_i=c_i ai⋅bi=ci
以及 Q Q Q个linear constraints,对其中的第 q q qth constraint可表示为:(其中 k ⃗ ∈ F Q \vec{k}\in\mathbb{F}^Q k∈FQ)
( ∑ i = 1 N a i ⋅ ( u ⃗ q ) i ) + ( ∑ i = 1 N b i ⋅ ( v ⃗ q ) i ) + ( ∑ i = 1 N c i ⋅ ( w ⃗ q ) i ) = k q (\sum_{i=1}^{N}a_i\cdot (\vec{u}_q)_i)+ (\sum_{i=1}^{N}b_i\cdot (\vec{v}_q)_i)+ (\sum_{i=1}^{N}c_i\cdot (\vec{w}_q)_i)=k_q (∑i=1Nai⋅(uq)i)+(∑i=1Nbi⋅(vq)i)+(∑i=1Nci⋅(wq)i)=kq
接下来,采用与Maller等人2019年《Sonic: Zero-Knowledge SNARKs from linear-size universal and updatable Structured Reference Strings》论文第5章中类似的方法:(详情参见博客 Arithmetic circuit 中第3节“3. Arithmetic circuit的constraint system表示”)
1)引入变量 Y Y Y将multiplication constraints和linear constraints合并为一个方程式:
∑ i = 1 N a i ⋅ Y N u i ( Y ) + ∑ i = 1 N b i ⋅ Y N v i ( Y ) + ∑ i = 1 N c i ⋅ ( Y N w i ( Y ) − Y i − Y − i ) + ∑ i = 1 N a i b i ⋅ ( Y i + Y − i ) − Y N k ( Y ) = 0 \sum_{i=1}^{N}a_i\cdot Y^Nu_i(Y)+\sum_{i=1}^{N}b_i\cdot Y^Nv_i(Y)+\sum_{i=1}^{N}c_i\cdot (Y^Nw_i(Y)-Y^i-Y^{-i})+\sum_{i=1}^{N}a_ib_i\cdot(Y^i+Y^{-i})-Y^Nk(Y)=0 ∑i=1Nai⋅YNui(Y)+∑i=1Nbi⋅YNvi(Y)+∑i=1Nci⋅(YNwi(Y)−Yi−Y−i)+∑i=1Naibi⋅(Yi+Y−i)−YNk(Y)=0……(4)
其中:
u i ( Y ) = ∑ q = 1 Q Y q ( u ⃗ q ) i u_i(Y)=\sum_{q=1}^{Q}Y^q(\vec{u}_q)_i ui(Y)=∑q=1QYq(uq)i
v i ( Y ) = ∑ q = 1 Q Y q ( v ⃗ q ) i v_i(Y)=\sum_{q=1}^{Q}Y^q(\vec{v}_q)_i vi(Y)=∑q=1QYq(vq)i
w i ( Y ) = ∑ q = 1 Q Y q ( w ⃗ q ) i w_i(Y)=\sum_{q=1}^{Q}Y^q(\vec{w}_q)_i wi(Y)=∑q=1QYq(wq)i
k ( Y ) = ∑ q = 1 Q Y q k q k(Y)=\sum_{q=1}^{Q}Y^qk_q k(Y)=∑q=1QYqkq
所以,若given a choice of a ⃗ , b ⃗ , c ⃗ , k ⃗ \vec{a},\vec{b},\vec{c},\vec{k} a,b,c,k使得方程式(4)都成立,则可认为该constraint system is satisfied。基于Schwartz-Zippel Lemma,若field足够大,则该方程式成立而不是正确解的概率不高于 Q + N p − 1 \frac{Q+N}{p-1} p−1Q+N。
2)再引入变量 X X X,构建Laurent polynomial t ( X , Y ) t(X,Y) t(X,Y),使得其 X 0 X^0 X0 constant term 项的系数为方程式(4)的左侧值:【注意,除 r ( X , Y ) r(X,Y) r(X,Y)外, s ( X , Y ) , s ′ ( X , Y ) s(X,Y),s'(X,Y) s(X,Y),s′(X,Y)均与witness a ⃗ , b ⃗ , c ⃗ \vec{a},\vec{b},\vec{c} a,b,c无关。】
r ( X , Y ) = ∑ i = 1 N a i X i Y i + ∑ i = 1 N b i X − i Y − i + ∑ i = 1 N c i X − i − N Y − i − N r(X,Y)=\sum_{i=1}^{N}a_iX^iY^i+\sum_{i=1}^{N}b_iX^{-i}Y^{-i}+\sum_{i=1}^{N}c_iX^{-i-N}Y^{-i-N} r(X,Y)=∑i=1NaiXiYi+∑i=1NbiX−iY−i+∑i=1NciX−i−NY−i−N
s ( X , Y ) = ∑ i = 1 N u i ( Y ) X − i + ∑ i = 1 N v i ( Y ) X i + ∑ i = 1 N w i ( Y ) X i + N s(X,Y)=\sum_{i=1}^{N}u_i(Y)X^{-i}+\sum_{i=1}^{N}v_i(Y)X^i+\sum_{i=1}^{N}w_i(Y)X^{i+N} s(X,Y)=∑i=1Nui(Y)X−i+∑i=1Nvi(Y)Xi+∑i=1Nwi(Y)Xi+N
s ′ ( X , Y ) = Y N s ( X , Y ) − ∑ i = 1 N ( Y i + Y − i ) X i + N s'(X,Y)=Y^Ns(X,Y)-\sum_{i=1}^{N}(Y^i+Y^{-i})X^{i+N} s′(X,Y)=YNs(X,Y)−∑i=1N(Yi+Y−i)Xi+N
t ( X , Y ) = r ( X , 1 ) ( r ( X , Y ) + s ′ ( X , Y ) ) − Y N k ( Y ) t(X,Y)=r(X,1)(r(X,Y)+s'(X,Y))-Y^Nk(Y) t(X,Y)=r(X,1)(r(X,Y)+s′(X,Y))−YNk(Y)
注意观察,其中 r ( X , Y ) = r ( X Y , 1 ) r(X,Y)=r(XY,1) r(X,Y)=r(XY,1),Prover可使用单变量polynomial commitment scheme 对 r ( X , Y ) r(X,Y) r(X,Y)进行commit,如 C o m m i t ( σ , r ( X , 1 ) ) Commit(\sigma,r(X,1)) Commit(σ,r(X,1))。
剩下的多项式 s ( X , Y ) , s ′ ( X , Y ) s(X,Y),s'(X,Y) s(X,Y),s′(X,Y)均与witness a ⃗ , b ⃗ , c ⃗ \vec{a},\vec{b},\vec{c} a,b,c无关,为了使 t ( X , Y ) t(X,Y) t(X,Y)的constant term系数为0, s ( X , Y ) s(X,Y) s(X,Y)和 s ′ ( X , Y ) s'(X,Y) s′(X,Y)会跟随 r ( X , Y ) r(X,Y) r(X,Y)的选择不同而变动。
3)至此,总的策略就变为了:
- Prover发送对 r ( X , Y ) r(X,Y) r(X,Y)的commitment,然后证明 t ( X , Y ) t(X,Y) t(X,Y)的constant term为zero polynomial。
- Verifier发送random challenge y ∈ I y\in\mathbb{I} y∈I。
- Prover发送对 t ( X , y ) t(X,y) t(X,y)的commitment。
- Verifier发送random challenge x ∈ I x\in\mathbb{I} x∈I。
- Prover 发送openings a = r ( x , 1 ) , b = r ( x , y ) , t = t ( x , y ) a=r(x,1),b=r(x,y),t=t(x,y) a=r(x,1),b=r(x,y),t=t(x,y)。
- Verifier 验证 t = a ( b + s ’ ( x , y ) ) − k ( y ) t=a(b+s’(x,y))-k(y) t=a(b+s’(x,y))−k(y)是否成立,即可证明the commitment to t ( X , y ) t(X,y) t(X,y) is correct with high probability。
- Prover 若能证明其commitment to r ( X , Y ) r(X,Y) r(X,Y) is bounded at degree N N N,则可说明 t ( X , Y ) t(X,Y) t(X,Y)的constant term is exactly the left-hand side of Equation 4;若 t ( X , Y ) t(X,Y) t(X,Y)的commitment的constant term能证明为0值,则可证明the Prover has knowledge of a satisfying witness with high probability。
3.1)为了证明 r ( X , Y ) r(X,Y) r(X,Y)的degree bound为 N N N,Prover需要改为发送commitment R = C o m m i t ( σ , r ( X , 1 ) X 3 N − 1 ; δ R ) R=Commit(\sigma,r(X,1)X^{3N-1};\delta_{R}) R=Commit(σ,r(X,1)X3N−1;δR),其中 δ R \delta_R δR为blinding factor,commitment R R R对应的多项式的degree bound为 d − 1 = 4 N − 1 d-1=4N-1 d−1=4N−1。Verifier仅需rescale openings of this commitment by X − 3 N + 1 X^{-3N+1} X−3N+1 to obtain the desired value。
3.2)观察多项式 t ( X , y ) t(X,y) t(X,y)中,基于 X X X的幂乘范围为 X − 4 N X^{-4N} X−4N至 X 3 N X^{3N} X3N,其中constant term值为0。
设 t l o ( X , y ) , t h i ( X , y ) t_{lo}(X,y),t_{hi}(X,y) tlo(X,y),thi(X,y)多项式的degree为 d − 1 d-1 d−1【此时 d = 4 N d=4N d=4N】,使得 t ( X , y ) = t l o ( X , y ) X − d + t h i ( X , y ) X t(X,y)=t_{lo}(X,y)X^{-d}+t_{hi}(X,y)X t(X,y)=tlo(X,y)X−d+thi(X,y)X,与其直接对 t ( X , y ) t(X,y) t(X,y)直接进行commit,可通过分别对 t l o ( X , y ) t_{lo}(X,y) tlo(X,y)和 t h i ( X , y ) t_{hi}(X,y) thi(X,y)进行commit T l o = C o m m i t ( σ , t l o ( X , y ) , δ l o ) , T h i = C o m m i t ( σ , t h i ( X , y ) , δ h i ) T_{lo}=Commit(\sigma,t_{lo}(X,y),\delta_{lo}),T_{hi}=Commit(\sigma,t_{hi}(X,y),\delta_{hi}) Tlo=Commit(σ,tlo(X,y),δlo),Thi=Commit(σ,thi(X,y),δhi),将 ( T l o , T h i ) (T_{lo}, T_{hi}) (Tlo,Thi)可看成是对 “constant term为0的Laurent polynomial” 的commitment,Verifier此时仍可rescale commitment openings as appropriate。
3.3)为了减轻Verifier的计算压力,Verifier不直接计算 k ( y ) k(y) k(y)值,改为:由Prover计算 k ( Y ) k(Y) k(Y)的commitment值 K = C o m m i t ( σ , k ( Y ) ) K=Commit(\sigma,k(Y)) K=Commit(σ,k(Y)),然后open 该commitment at y y y。
3.4)为了evaluate s ’ ( x , y ) s’(x,y) s’(x,y),借助了Maller等人2019年《Sonic: Zero-Knowledge SNARKs from linear-size universal and updatable Structured Reference Strings》中的策略:
- Prover:发送commitment S = C o m m i t ( σ , s ( X , y ) X N ) S=Commit(\sigma,s(X,y)X^N) S=Commit(σ,s(X,y)XN)。
- Verifier:发送random challenge x x x。
- Prover:发送opening for commitment S S S at x x x: s a s_a sa。
- Verifier:验证opening正确,然后计算 s ( x , y ) = s a ⋅ x − N s(x,y)=s_a\cdot x^{-N} s(x,y)=sa⋅x−N。(注意此处验证opening正确需要linear work in ∣ C ∣ |C| ∣C∣,而本论文的目标是Verifier仅在最后进行一次linear-time operation at the end of a sequence of arguments,且the marginal cost of checking an argument must be logarithmic in ∣ C ∣ |C| ∣C∣)。
注意,别忘了此时针对的场景是:
对固定的circuit C C C,Prover重复多次与Verifier交互来生成multiple arguments in sequence。
也就是说,在每个argument中都包含了 y n e w y_{new} ynew值和commitment S n e w = C o m m i t ( σ , s ( X , y n e w ) X N ) S_{new}=Commit(\sigma,s(X,y_{new})X^N) Snew=Commit(σ,s(X,ynew)XN)。假设 ( y o l d , S o l d ) (y_{old}, S_{old}) (yold,Sold)为 ( y n e w , S n e w ) (y_{new},S_{new}) (ynew,Snew)前一个argument的值。则Prover可通过如下方式来验证 S n e w S_{new} Snew和 S o l d S_{old} Sold是否正确:
【看后续的完整协议实现,实际协议中是默认Verifier验证成立,从而减少communication cost和Verification work。借助了Sonic论文第8章的思路。即认为若:open C = C o m m i t ( σ , s ( x , Y ) X N ) C=Commit(\sigma,s(x,Y)X^N) C=Commit(σ,s(x,Y)XN) at y o l d y_{old} yold的值等于open S o l d = C o m m i t ( σ , s ( X , y o l d ) ) S_{old}=Commit(\sigma,s(X,y_{old})) Sold=Commit(σ,s(X,yold))的值;且, open C = C o m m i t ( σ , s ( x , Y ) X N ) C=Commit(\sigma,s(x,Y)X^N) C=Commit(σ,s(x,Y)XN) at y y y的值等于open S = C o m m i t ( σ , s ( X , y ) ) S=Commit(\sigma,s(X,y)) S=Commit(σ,s(X,y))的值,则可说明 “若 C C C is a commitment to the correct polynomial,则大概率 S o l d , S S_{old}, S Sold,S 每个commitment is to the correct polynomial”。
此时,Verifier不直接验证commitment C C C的正确性,而改为sample random y n e w ∈ I y_{new}\in\mathbb{I} ynew∈I,要求Prover提供 S n e w = C o m m i t ( σ , s ( X , y n e w ) X N ) S_{new}=Commit(\sigma,s(X,y_{new})X^N) Snew=Commit(σ,s(X,ynew)XN),然后要求Prover证明 S n e w S_{new} Snew open at x x x的值与 C C C open at y n e w y_{new} ynew的值相同,这就说明 “大概率 the correctness of S n e w S_{new} Snew 可代表 the correctness of C C C”。Verifier take this ( y n e w , S n e w ) (y_{new},S_{new}) (ynew,Snew) for the next argument。
为了accept a sequence of arguments, Verifier仅需验证 S n e w = C o m m i t ( σ , s ( X , y n e w ) X N ) S_{new}=Commit(\sigma,s(X,y_{new})X^N) Snew=Commit(σ,s(X,ynew)XN) for the final argument,而不需要perform linear-time marginal work with respect to evaluating s(X,Y)。
】
- Verifier:发送random challenge x x x。
- Prover:发送Commitment C = C o m m i t ( σ , s ( x , Y ) x N ) C=Commit(\sigma,s(x,Y)x^N) C=Commit(σ,s(x,Y)xN);发送openings for commitment S o l d S_{old} Sold和 S n e w S_{new} Snew at x x x: s a o l d , s a n e w s_{aold}, s_{anew} saold,sanew。
- Verifier:发送 random challenge y o l d , y n e w y_{old},y_{new} yold,ynew。
- Prover:发送openings for commitment C C C at y o l d , y n e w y_{old},y_{new} yold,ynew: c a o l d , c a n e w c_{aold},c_{anew} caold,canew。
- Verifier:验证openings for commitment S o l d S_{old} Sold和 S n e w S_{new} Snew at x x x是否正确;验证openings for commitment C C C at y o l d , y n e w y_{old},y_{new} yold,ynew是否正确;最后验证 s a o l d = c a o l d , s a n e w = c a n e w s_{aold}= c_{aold}, s_{anew}= c_{anew} saold=caold,sanew=canew是否成立即可。
至此,Verifier可认为自 ( y n e w , S n e w ) (y_{new},S_{new}) (ynew,Snew)之前的sequence arguments 都是正确的。In order to accept a sequence of arguments the verifier will need to check that S n e w = C o m m i t ( σ , s ( X , y n e w ) X N ) S_{new}=Commit(\sigma,s(X,y_{new})X^N) Snew=Commit(σ,s(X,ynew)XN) for the final argument but otherwise does not perform linear-time marginal work with respect to evaluating s ( X , Y ) s(X,Y) s(X,Y)。
4.1 合并多个polynomial commitment opening arguments
至此,Prover和Verifier进行了多个单独的polynomial commitment opening arguments。
(1)以下为均需open at x x x的polynomial commitments:
- R = C o m m i t ( σ , r ( X , 1 ) X 3 N − 1 ; δ R ) R=Commit(\sigma,r(X,1)X^{3N-1};\delta_{R}) R=Commit(σ,r(X,1)X3N−1;δR) 【即相当于计算 r ( x , 1 ) r(x,1) r(x,1)】
- S o l d = C o m m i t ( σ , s ( X , y o l d ) X N ) S_{old}=Commit(\sigma,s(X,y_{old})X^N) Sold=Commit(σ,s(X,yold)XN)
- S = C o m m i t ( σ , s ( X , y ) X N ) S=Commit(\sigma,s(X,y)X^N) S=Commit(σ,s(X,y)XN)
- S n e w = C o m m i t ( σ , s ( X , y n e w ) X N ) S_{new}=Commit(\sigma,s(X,y_{new})X^N) Snew=Commit(σ,s(X,ynew)XN)
- T l o = C o m m i t ( σ , t l o ( X , y ) , δ l o ) T_{lo}=Commit(\sigma,t_{lo}(X,y),\delta_{lo}) Tlo=Commit(σ,tlo(X,y),δlo)
- T h i = C o m m i t ( σ , t h i ( X , y ) , δ h i ) T_{hi}=Commit(\sigma,t_{hi}(X,y),\delta_{hi}) Thi=Commit(σ,thi(X,y),δhi)
(在收到对相同的点 x x x的openings之后,Verifier发送challenge z 1 z_1 z1,借助 Kate等人2010年论文《Constant-size commitments to polynomials and their applications》中的batch opening 策略,构建 P = R + [ z 1 ] S o l d + [ z 1 2 ] S + [ z 1 3 ] S n e w + [ z 1 4 ] T l o + [ z 1 5 ] T h i = C o m m i t ( σ , p ( Z ) ) P=R+[z_1]S_{old}+[z_1^2]S+[z_1^3]S_{new}+[z_1^4]T_{lo}+[z_1^5]T_{hi}=Commit(\sigma,p(Z)) P=R+[z1]Sold+[z12]S+[z13]Snew+[z14]Tlo+[z15]Thi=Commit(σ,p(Z)),其中多项式 p ( Z ) ∈ F [ Z ] p(Z)\in\mathbb{F}[Z] p(Z)∈F[Z]。)
(2)以下为均需open at y y y的polynomial commitments:
- K = C o m m i t ( σ , k ( Y ) ) K=Commit(\sigma,k(Y)) K=Commit(σ,k(Y)) 【即相当于计算 k ( y ) k(y) k(y)】
- C = C o m m i t ( σ , s ( x , Y ) x N ) C=Commit(\sigma,s(x,Y)x^N) C=Commit(σ,s(x,Y)xN)
(在收到对相同的点 y y y的openings之后,Verifier发送challenge z 1 z_1 z1,借助 Kate等人2010年论文《Constant-size commitments to polynomials and their applications》中的batch opening 策略,构建 Q = K + [ z 1 ] C = C o m m i t ( σ , q ( Z ) ) Q=K+[z_1]C=Commit(\sigma,q(Z)) Q=K+[z1]C=Commit(σ,q(Z)),其中多项式 q ( Z ) ∈ F [ Z ] q(Z)\in\mathbb{F}[Z] q(Z)∈F[Z]。)
(3)以下为需open at x y xy xy的polynomial commitments:
- R = C o m m i t ( σ , r ( X , 1 ) X 3 N − 1 ; δ R ) R=Commit(\sigma,r(X,1)X^{3N-1};\delta_{R}) R=Commit(σ,r(X,1)X3N−1;δR) 【即相当于计算 r ( x y , 1 ) = r ( x , y ) r(xy,1)=r(x,y) r(xy,1)=r(x,y)】
(4)以下为需open at y o l d y_{old} yold的polynomial commitments:
- C = C o m m i t ( σ , s ( x , Y ) x N ) C=Commit(\sigma,s(x,Y)x^N) C=Commit(σ,s(x,Y)xN)
(5)以下为需open at y n e w y_{new} ynew的polynomial commitments:
- C = C o m m i t ( σ , s ( x , Y ) x N ) C=Commit(\sigma,s(x,Y)x^N) C=Commit(σ,s(x,Y)xN)
借鉴Boneh等人2020年论文《Efficient polynomial commitment schemes for multiple points and polynomials》中的思路,将以上(1)~(5)的5个separate opening arguments reduce为1个:
对于 m m m个不同的evaluation points x 0 , x 1 , ⋯ , x m − 1 x_0,x_1,\cdots,x_{m-1} x0,x1,⋯,xm−1,可定义多项式:
h ( X , Z ) = ∑ i = 0 m − 1 Z i e i ( X ) − v i X − x i h(X,Z)=\sum_{i=0}^{m-1}Z^i\frac{e_i(X)-v_i}{X-x_i} h(X,Z)=∑i=0m−1ZiX−xiei(X)−vi
其中, m m m个commitments E 0 , E 1 , ⋯ , E m − 1 E_0,E_1,\cdots,E_{m-1} E0,E1,⋯,Em−1 满足 E i = C o m m i t ( σ , e i ( X ) ) E_i=Commit(\sigma,e_i(X)) Ei=Commit(σ,ei(X)),在point x i x_i xi 的evaluation 值为 v i v_i vi。【针对本文情况,此时 E 0 = P , E 1 = Q , E 2 = R , E 3 = C , E 4 = C E_0=P,E_1=Q,E_2=R,E_3=C,E_4=C E0=P,E1=Q,E2=R,E3=C,E4=C。】
- Prover:发送openings v i = e i ( x i ) v_i=e_i(x_i) vi=ei(xi) for all i i i。
- Verifier:发送 random challenge z 2 z_2 z2。
- Prover:发送commitment H = C o m m i t ( σ , h ( X , z 2 ) ; δ H ) H=Commit(\sigma,h(X,z_2);\delta_H) H=Commit(σ,h(X,z2);δH),其中 δ H ∈ F \delta_H\in\mathbb{F} δH∈F为blinding factor。
(为了证明 H H H是正确构建的,需要再引入Verifier challenge z 3 z_3 z3,Prover提供 P , Q , R , C P,Q,R,C P,Q,R,C的openings,然后Verifier可计算 h ( z 3 , z 2 ) h(z_3,z_2) h(z3,z2)值,并验证 h ( z 3 , z 2 ) h(z_3,z_2) h(z3,z2)为commitment H H H 在point z 3 z_3 z3的opening值。) - Verifier:发送random challenge z 3 z_3 z3。
- Prover:发送 P , Q , R , C P,Q,R,C P,Q,R,C的openings at z 3 z_3 z3: p ( z 3 ) , q ( z 3 ) , r ( z 3 , 1 ) , s ( x , z 3 ) p(z_3),q(z_3),r(z_3,1),s(x,z_3) p(z3),q(z3),r(z3,1),s(x,z3)。
- Verifier:根据 p ( z 3 ) , q ( z 3 ) , r ( z 3 , 1 ) , s ( x , z 3 ) p(z_3),q(z_3),r(z_3,1),s(x,z_3) p(z3),q(z3),r(z3,1),s(x,z3)计算 h ( z 3 , z 2 ) = p ( z 3 ) − v 0 z 3 − x 0 + z 2 ⋅ q ( z 3 ) − v 1 z 3 − x 1 + z 2 2 ⋅ r ( z 3 , 1 ) − v 2 z 3 − x 2 + z 2 3 ⋅ s ( x , z 3 ) − v 3 z 3 − x 3 + z 2 4 ⋅ s ( x , z 3 ) − v 4 z 3 − x 4 h(z_3,z_2)=\frac{p(z_3)-v_0}{z_3-x_0}+z_2\cdot \frac{q(z_3)-v_1}{z_3-x_1}+z_2^2\cdot \frac{r(z_3,1)-v_2}{z_3-x_2}+z_2^3\cdot \frac{s(x,z_3)-v_3}{z_3-x_3}+z_2^4\cdot \frac{s(x,z_3)-v_4}{z_3-x_4} h(z3,z2)=z3−x0p(z3)−v0+z2⋅z3−x1q(z3)−v1+z22⋅