Basic Usage
Generate Key Pair
ssh-keygen -t dsa -b4096
Exchange Key
scp ~/.ssh/id_dsa.pub [email protected]:.ssh/authorized_keys
If you have ssh-copy-id installed, you can just run
ssh-copy-id [email protected]
Login Remote Instance
After puting your public keys in remote instance, then you can run:
to login remote instance
Excute Cammand On Remote Host
ssh [email protected] ls -l /
Using Scp
Local to remote
scp [email protected]:
Remote to local
scp [email protected]:report.docreport.doc
Test Connection
ssh-T git@host-v
Server Configurations
将PasswordAuthentication no加入server的/etc/ssh/sshd_config来阻止使用密码ssh登陆
通过Port 4444来使用自定义端口
限定用户AllowUsers user1 user2
限定用户组AllowGroups sshmembers
Disable root loginPermitRootLogin no
Client Configuration
Ssh client configuration lies in~/.ssh/config
Example common settings like followings:
Host github-default
HostName github.com
User username
IdentityFile ~/.ssh/gitkey_default
Host
Only the host of the ssh command match this value, will the following rule applied to this command HostName The real hostname the command will try to connect
Username
The real Username the command will use
IdentityFile
Location of the private key
For other configuration, please refer to ssh man page
Reuse Session & Tunel
Host *
ControlMaster auto
ControlPath ~/.ssh/sockets/%r@%h-%p
ControlPersist 600
ControlMaster auto
The ControlMaster option is one of SSH's best kept secrets. It instructs SSH to reuse an existing connection to the server if it already exists. This means that, if you run sshexample.com, open another terminal, and run sshexample.comthere, the two sessions will be transported over the same underlying connection. The second session starts much more quickly because the SSH handshake has already been completed.
ControlPath ~/.ssh/sockets/%r@%h-%p
ControlPath is a specification of where to create the control socket on your filesystem. If you use the value provided here, make sure to manually mkdir ~/.ssh/sockets. At any time, you can manually remove the control socket (using plain-old rm), and the next ssh invocation will establish a new connection. This is especially useful if you've recently reopened your laptop and your SSH connections haven't yet figured out that the server terminated them.
ControlPersist 600
Without ControlPersist, once the first SSH session you open is closed, all other sessions on that connection are closed as well. This can lead to a variety of surprising behavior: if you exit the initial SSH shell while other sessions are sharing the connection, the process will just hang. If you send it a Ctrl-C, all of those other sessions will be abruptly terminated.
Further Use
Set Tunnel From Local To Remote Server
ssh -i key -f -N -L 8888:example.com:80 username@remote_host
Pattern
ssh -i key -f -N -L your_port:site_or_IP_to_access:site_port username@host
-f options let SSH to go into the background before executing
-N options let SSH not open a shell or execute a program on the remote side
When you visit 127.0.0.1:8888 on your local computer, then you will go through the tunnel and access the example.com:80 via your remote computer
Set Tunnel From Remote To Local
ssh -f -N -R 8888:example.com:80 username@remote_host
Pattern
ssh -R remote_port:site_or_IP_to_access:site_port username@host
When you visit 127.0.0.1:8888 on your remote computer, then you will go through the tunnel and access the example.com:80 via your local computer
Set Dynamic Tunneling to a Remote Server
ssh -f -N -D 7777 username@remote_host
From here, you can start pointing your SOCKS-aware application (like a web browser), to the port you selected. The application will send its information into a socket associated with the port.
The method of directing traffic to the SOCKS port will differ depending on application. For instance, in Firefox, the general location is Preferences > Advanced > Settings > Manual proxy configurations. In Chrome, you can start the application with the --proxy-server= flag set. You will want to use the localhost interface and the port you forwarded.
ProxyCommand
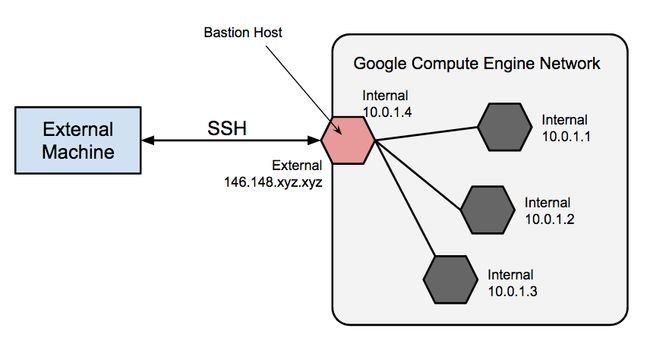
Some times you will protect your servers behind a bastion instance, or event 3 or 4 layers like following:
If you want ssh onto internal instances, you need jump from bastion and then do another ssh command.
It's not fancy isn't it? It`s time to embrace proxy command. You can just run command as followings:
ssh -o ProxyCommand='ssh -W 10.0.1.1:22 [email protected]' [email protected]
It will setup a tunnel forward socket from local to internal via bastion, and then you [email protected], it will be forwarded to the internal instances.
Done.
Conclusion
Let just use the former problem as an example we can set our ssh configuration file like this
Host */*
ControlMaster auto
ControlPath ~/.ssh/sockets/%r@%h-%p
ControlPersist 600
ProxyCommand ssh%r@$(dirname%h) -W$(basename%h):%p
Then you can run ssh user@bastion/internal and it will directly ssh onto the internal instance