USG6000V通过IKE方式协商IPSec VPN隧道(采用预共享秘钥认证)
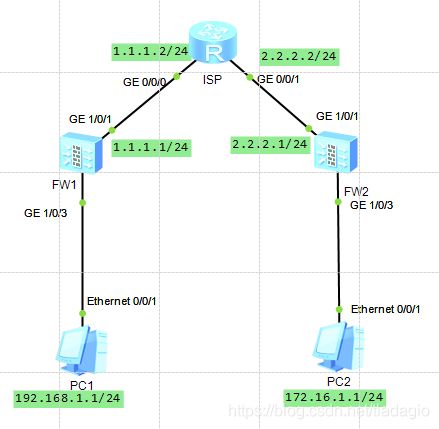
网络拓扑:
操作步骤
一、配置FW1
1、配置接口IP地址
system-view
[USG6000V1]sysname FW1
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]ip address 1.1.1.1 24
[FW1-GigabitEthernet1/0/1]q
[FW1]interface GigabitEthernet 1/0/3
[FW1-GigabitEthernet1/0/3]ip address 192.168.1.254 24
[FW1-GigabitEthernet1/0/3]q 2、配置接口加入对于安全区域
[FW1]firewall zone trust
[FW1-zone-trust]add interface GigabitEthernet 1/0/3
[FW1-zone-trust]q
[FW1]firewall zone untrust
[FW1-zone-untrust]add interface GigabitEthernet 1/0/1
[FW1-zone-untrust]q3、配置域间安全策略(配置Local域和Untrust域的域间安全策略的目的为允许IPSec隧道两端设备通信,使其能够进行隧道协商。)
[FW1]security-policy
[FW1-policy-security]rule name policy1
[FW1-policy-security-rule-policy1]source-zone trust
[FW1-policy-security-rule-policy1]destination-zone untrust
[FW1-policy-security-rule-policy1]source-address 192.168.1.0 24
[FW1-policy-security-rule-policy1]destination-address 172.16.1.0 24
[FW1-policy-security-rule-policy1]action permit
[FW1-policy-security-rule-policy1]q
[FW1-policy-security]rule name policy2
[FW1-policy-security-rule-policy2]source-zone untrust
[FW1-policy-security-rule-policy2]destination-zone trust
[FW1-policy-security-rule-policy2]source-address 172.16.1.0 24
[FW1-policy-security-rule-policy2]destination-address 192.168.1.0 24
[FW1-policy-security-rule-policy2]action permit
[FW1-policy-security-rule-policy2]q
[FW1-policy-security]rule name policy3
[FW1-policy-security-rule-policy3]source-zone local
[FW1-policy-security-rule-policy3]destination-zone untrust
[FW1-policy-security-rule-policy3]source-address 1.1.1.1 32
[FW1-policy-security-rule-policy3]destination-address 2.2.2.1 32
[FW1-policy-security-rule-policy3]action permit
[FW1-policy-security-rule-policy3]q
[FW1-policy-security]rule name policy4
[FW1-policy-security-rule-policy4]source-zone untrust
[FW1-policy-security-rule-policy4]destination-zone local
[FW1-policy-security-rule-policy4]source-address 2.2.2.1 32
[FW1-policy-security-rule-policy4]destination-address 1.1.1.1 32
[FW1-policy-security-rule-policy4]action permit
[FW1-policy-security-rule-policy4]q4、配置静态路由
[FW1]ip route-static 0.0.0.0 0 1.1.1.25、定义被保护的数据流
[FW1]acl 3000
[FW1-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
[FW1-acl-adv-3000]q6、配置IPSec安全提议
[FW1]ipsec proposal tran1
[FW1-ipsec-proposal-tran1]esp authentication-algorithm sha2-256
[FW1-ipsec-proposal-tran1]esp encryption-algorithm aes-256
[FW1-ipsec-proposal-tran1]q7、配置Ike安全提议
[FW1]ike proposal 10
[FW1-ike-proposal-10]authentication-method pre-share
[FW1-ike-proposal-10]authentication-algorithm sha2-256
[FW1-ike-proposal-10]prf hmac-sha2-256
[FW1-ike-proposal-10]encryption-algorithm aes-256
[FW1-ike-proposal-10]dh group14
[FW1-ike-proposal-10]integrity-algorithm hmac-sha2-256
[FW1-ike-proposal-10]q8、配置Ike peer(采用预共享秘钥)
[FW1]ike peer b
[FW1-ike-peer-b]ike-proposal 10
[FW1-ike-peer-b]remote-address 2.2.2.1
[FW1-ike-peer-b]pre-shared-key admin@123
[FW1-ike-peer-b]q9、配置IPSec策略
[FW1]ipsec policy map1 10 isakmp
[FW1-ipsec-policy-isakmp-map1-10]security acl 3000
[FW1-ipsec-policy-isakmp-map1-10]proposal tran1
[FW1-ipsec-policy-isakmp-map1-10]ike-peer b
[FW1-ipsec-policy-isakmp-map1-10]q10、接口应用IPSec策略
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]ipsec policy map1
[FW1-GigabitEthernet1/0/1]q二、配置FW2
1、配置接口IP地址
system-view
[USG6000V1]sysname FW2
[FW2]interface GigabitEthernet 1/0/3
[FW2-GigabitEthernet1/0/3]ip address 172.16.1.254 24
[FW2-GigabitEthernet1/0/3]q
[FW2]interface GigabitEthernet 1/0/1
[FW2-GigabitEthernet1/0/1]ip address 2.2.2.1 24
[FW2-GigabitEthernet1/0/1]q 2、配置接口加入对于安全区域
[FW2]firewall zone trust
[FW2-zone-trust]add interface GigabitEthernet 1/0/3
[FW2-zone-trust]q
[FW2]firewall zone untrust
[FW2-zone-untrust]add interface GigabitEthernet 1/0/1
[FW2-zone-untrust]q3、配置域间安全策略
[FW2]security-policy
[FW2-policy-security]rule name policy1
[FW2-policy-security-rule-policy1]source-zone trust
[FW2-policy-security-rule-policy1]destination-zone untrust
[FW2-policy-security-rule-policy1]source-address 172.16.1.0
[FW2-policy-security-rule-policy1]destination-address 192.168.1.0 24
[FW2-policy-security-rule-policy1]action permit
[FW2-policy-security-rule-policy1]q
[FW2-policy-security]rule name policy2
[FW2-policy-security-rule-policy2]source-zone untrust
[FW2-policy-security-rule-policy2]destination-zone trust
[FW2-policy-security-rule-policy2]source-address 192.168.1.0 24
[FW2-policy-security-rule-policy2]destination-zone 172.16.1.0 24
[FW2-policy-security-rule-policy2]action permit
[FW2-policy-security-rule-policy2]q
[FW2-policy-security]rule name policy3
[FW2-policy-security-rule-policy3]source-zone local
[FW2-policy-security-rule-policy3]destination-zone untrust
[FW2-policy-security-rule-policy3]source-address 2.2.2.1 32
[FW2-policy-security-rule-policy3]destination-address 1.1.1.1 32
[FW2-policy-security-rule-policy3]action permit
[FW2-policy-security-rule-policy3]q
[FW2-policy-security]rule name policy4
[FW2-policy-security-rule-policy4]source-zone untrust
[FW2-policy-security-rule-policy4]destination-zone local
[FW2-policy-security-rule-policy4]source-address 1.1.1.1 32
[FW2-policy-security-rule-policy4]destination-address 2.2.2.1 32
[FW2-policy-security-rule-policy4]action permit
[FW2-policy-security-rule-policy4]q4、配置静态路由
[FW2]ip route-static 0.0.0.0 0 2.2.2.25、定义被保护的数据流
[FW2]acl 3000
[FW2-acl-adv-3000]rule permit ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
[FW2-acl-adv-3000]q6、配置IPSec安全提议
[FW2]ipsec proposal tran1
[FW2-ipsec-proposal-tran1]esp authentication-algorithm sha2-256
[FW2-ipsec-proposal-tran1]esp encryption-algorithm aes-256
[FW2-ipsec-proposal-tran1]q7、配置Ike安全提议
[FW2]ike proposal 10
[FW2-ike-proposal-10]authentication-method pre-share
[FW2-ike-proposal-10]authentication-algorithm sha2-256
[FW2-ike-proposal-10]prf hmac-sha2-256
[FW2-ike-proposal-10]encryption-algorithm aes-256
[FW2-ike-proposal-10]dh group14
[FW2-ike-proposal-10]integrity-algorithm hmac-sha2-256
[FW2-ike-proposal-10]q8、配置Ike peer(采用预共享秘钥)
[FW2]ike peer a
[FW2-ike-peer-a]ike-proposal 10
[FW2-ike-peer-a]remote-address 1.1.1.1
[FW2-ike-peer-a]pre-shared-key admin@123
[FW2-ike-peer-a]q9、配置IPSec策略
[FW2]ipsec policy map1 10 isakmp
[FW2-ipsec-policy-isakmp-map1-10]security acl 3000
[FW2-ipsec-policy-isakmp-map1-10]proposal tran1
[FW2-ipsec-policy-isakmp-map1-10]ike-peer a
[FW2-ipsec-policy-isakmp-map1-10]q10、接口应用IPSec策略
[FW2]interface GigabitEthernet 1/0/1
[FW2-GigabitEthernet1/0/1]ipsec policy map1
[FW2-GigabitEthernet1/0/1]q三、配置ISP
1、配置接口IP地址
system-view
[Huawei]sysname ISP
[ISP]interface GigabitEthernet 0/0/1
[ISP-GigabitEthernet0/0/1]ip address 2.2.2.2 24
[ISP-GigabitEthernet0/0/1]q
[ISP]interface GigabitEthernet 0/0/0
[ISP-GigabitEthernet0/0/0]ip address 1.1.1.2 24
[ISP-GigabitEthernet0/0/0]q 四、验证
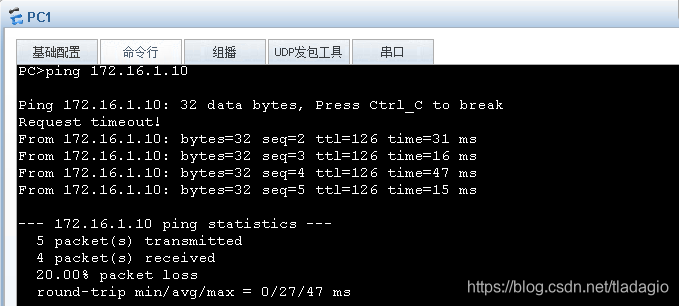
1、ping测试
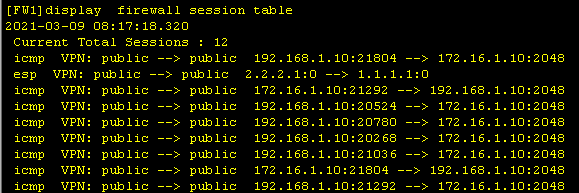
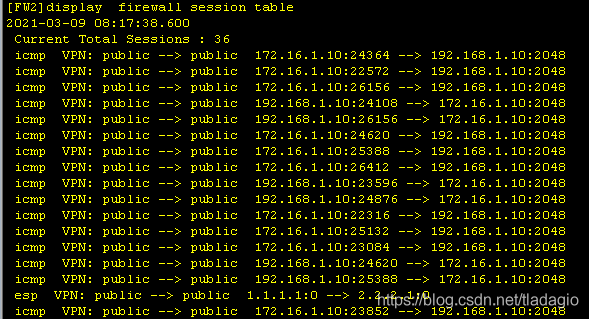
2、查看结果