Reducing browser privileges
Reducing browser privileges
Mark Squire 2005-10-04
Security companies and researchers have made careers out of identifying the latest bugs in Internet Explorer. While Microsoft has been relatively idle, the developers of Firefox have continued to add functionality and provide what was perceived to be more secure code. The story doesn't end there, though. The past six months have seen major vulnerabilities in Firefox too, and its adoption has slowed. Some people are beginning to question the wisdom in switching to another browser that is possibly just as insecure as IE.
Meanwhile a simple yet little-known approach exists for users to avoid many of these vulnerabilities in any web browser. It is a novel tool called "Drop My Rights," created by Microsoft's Michael Howard. While it was released last year and is very simple to use, it has not gained popularity despite all the vulnerabilities found in IE, Firefox, and various email applications. Therefore it's important to understand why such a tool is needed before looking at the tool itself. We'll test it in a virtual machine environment against various websites known to install spyware or viruses and look at the results.
Least privilege
It is important that administrators follow the rule of least privilege. This means that users should operate their computer with only the minimum set of privileges that they need to do their job. Typically this means operating as a normal user, and only when absolutely necessary use the Run As or MakeMeAdmin commands to elevate privileges. Otherwise, a normal user would be forced to log out, and then log back in as an administrative user to perform necessary actions such as install software - or even many browser-based plugins. When faced with this inconvenience, most users when given the choice will continue to operate as an administrator. Herein is the problem.
Corporate policy that disallows administrator access to desktop machines is still the best approach. However, political issues with "power users" or users in very decentralized networks continue to pose a problem. Additionally, administrators themselves who browse the web are still at risk. Reducing privileges of Internet-facing applications is one approach to reducing that risk.
After publishing his tool, Michael Howard repeats that, "Running with an administrative account is dangerous to the health of your computer and your data." Readers of SecurityFocus should all know this, yet many still do it anyway. Rather than trying to lowering user rights across the board, a good approach for power users is to simply lower the rights of Internet-facing applications like Internet Explorer, Firefox, IM applications, Outlook and Outlook Express, Notes, Thunderbird, and so on.
Drop My Rights
Drop My Rights is an executable that accepts a path to your favorite program as a command-line argument. Consider for a moment that an administrator would want to run IE or Firefox in a more safe security context. The administrator would, in the case of IE, run the following command:
c:\path\to\dropmyrights.exe "C:\Program Files\Internet Explorer\iexplore.exe" CThis tells Internet Explorer to run at a reduced privilege level C, or "constrained user." This makes it so that if there is any sort of hole/vulnerability in IE or Firefox, the damage that can be done by an exploit is severely limited. The levels in this simple application are as follows:
N for Normal User
C for constrained user
U for untrusted user - however, most Internet applications will fail
The important question is "does it work?" This can be answered with a few simple experiments. The idea is to test whether a system using this utility will be more protected than a system without this utility when browsing malicious websites.
Testing procedure
Before the actual tests, some prep work needs to be done. This experiment demands a controlled test environment. Virtual machines, as provided from VMWare and Microsoft, are the perfect choice for such an environment. They have the ability to set a snapshot of a particular point in time, allowing one to make changes to the virtual machine, observe the results, then revert it back to the state that it was in before any of those changes were made. For this experiment a virtual machine with Windows XP installed (no service packs or patches), with a snapshot taken just after installation.
During the experiments, one of the free online antivirus scans will be used to test the machine for infection, but first it is necessary to establish that the machine is clean to begin with. To do this an initial scan was completed on the virtual machine before any tests were conducted. The results came back negative for viruses, as expected, and to keep all things equal, the virtual machine was immediately reverted back to its snapshot after the initial scan was complete.
The procedure for the first test was as follows:
Revert the virtual machine to its snapshot (completed above).
Obtain a list of unfriendly websites.
Open each of these sites on the virtual machine using Internet Explorer.
Note any strangeness observed during the experiments.
Run virus scan once these procedures are complete.
Copy the list of URL's from the Internet Explorer's history to Notepad. This will be useful later on.
During the testing a number of unrecognized applications were installed. Changes were made to the GUI of Internet Explorer including the addition of various buttons and search-bars. Phantom windows would appear and disappear at random, and there were numerous popups. The virtual machine itself was running noticeably slower as well. Although an online virus scan was initiated, it didn't complete successfully. In fact the scan died with an error before it actually completed. It found 7 infections, however, before it finally died.
The procedure for the second test was as follows:
Revert the virtual machine to its snapshot (completed above).
Use the list of URLs obtained from the history in the last test.
Install "Drop My Rights" and install according to instructions (for this test it is run with the "N" parameter which runs IE under normal privileges mode - still significantly lower than administrator privileges).
Open these same set of sites on the virtual machine using Internet Explorer.
Note any strangeness observed during the experiments.
Run virus scan once these procedures are complete.
The only observation of note during the experiment is that pop-ups still occurred. There were no phantom windows or unexplained applications installed. However the virus scan still turned up 4 viruses. Since the author recommends the "C" parameter while surfing more questionable sites, the next portion of the experiment did exactly that.
The procedure for the final test was as follows:
Revert the virtual machine to its snapshot (completed above).
Use the list of URLs obtained from the history in the last test.
Install "Drop My Rights" and install according to instructions (for this test it is run with the "C" parameter which runs IE under constricted privileges mode – which incidentally what the author of the utility suggests using when opening "questionable" sites).
Open each of these sites on the virtual machine using Internet Explorer.
Note any strangeness observed during the experiments.
Run virus scan once these procedures are complete.
During this final experiment the only oddity observed was that the Internet Explorer window would maximize if it wasn't already. There were no pop-ups, pop-unders, or any of the other effects previously observed, and this time the virus scan turned up zero viruses. Drop My Rights works just as the author described according in the tests conducted.
Simplifying for users
It's very easy to adjust an application shortcut so that the application runs with reduced rights. This is ideal for power users or others who insist on running as an administrator. When viewing the shortcut properties, simply change the target of the application to call DropMyRights.exe first, such as, C:\windows\dropmyrights.exe "C:\Program Files\Mozilla Firefox\firefox.exe" N, as shown below in Figure 1.
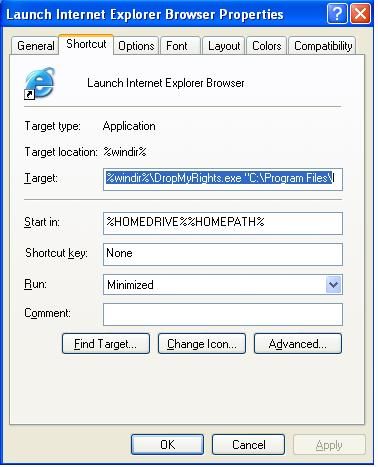
Figure 1. Setting up a shortcut to use DropMyRights.exe.
Note that other applications will inherit these reduced privileges when spawned. For example, Windows Media Player, Adobe Acrobat, WinZip, and others will run with reduced privileges when launched from the browser. This is ideal, however it does not provide complete protection as we will see.
A tool such as SysInternals' free Process Explorer can be used to verify the privileges of the process as well as any processes it spawns.
There is also an IE toolbar written by Aaron Margosis called PrivBar that makes it very easy to see what privileges IE is running under (Administrator, Power User, User, or Restricted). This can be useful when testing DropMyRights.exe.
Drawbacks
As mentioned earlier, restricted privilege sometimes impacts functionality. Internet Explorer won't work at all when running it as an argument to dropmyrights.exe with the "U" parameter (the most restrictive setting). Additionally when running in "constricted" mode, some sites don't work. For instance www.espn.com shows up incomplete in my testing. Typing www.espn.com will result in IE opening it, but it will throw up an error window first.
Using the "normal" mode still has a lot of restricted privileges, but many of the annoyances of the "constricted" mode aren't there. SSL also doesn't work in "constricted" mode but works fine in "normal" mode, a fact the author of the code is well aware of. In fact there is a large list of software that simply doesn't work with restricted privileges. While this utility works perfectly for IE, it is best used with any Internet facing program. This includes instant messengers, email programs, media players for example. Try it with the most restrictive privileges, and check for functionality. Make separate shortcuts available if you absolutely need raise your privileges to gain a certain functionality.
Any time you drop privileges in an operating system, you sacrifice functionality. Take for instance the program "Macromedia Shockwave." Shockwave needs administrative privileges to install. In this author's experience it also needs administrative privileges to run as in certain isolated circumstances. The point is that the principle of least privilege isn't always practical. If you have a user, who has a legitimate need to have administrative privileges, this utility can therefore be helpful.
Complete protection?
While all of this sounds good, it can offer a false sense of security. Applications spawned from a browser with reduced privileges will inherit those reduced privileges, but privilege escalation is still always a possibility. Additionally, exploits that make use of spoofing obviously would not be stopped by this utility. Phishing is probably the most notable example as it uses a combination of spoofing and social engineering to accomplish its goal. This tool was not designed to handle those problems anyway, but historically, the most troublesome bugs in IE have had to do with buffer-overflows. This utility would be able to severely limit the potential damage done as a result of these bugs.
Summary
It would be better for the Internet as a whole if users did not use their Windows web browsers with administrator privileges. Malicious viruses, spyware and Trojans are frequently installed through vulnerabilities in Internet-facing applications - either by visiting websites or by social engineering such as users clicking on malicious attachments in their email. However, due to the inconvenient and clumsy way of installing applications that require administrator privileges, many users continue to run as administrator. The easy use of DropMyAdmin can reduce the impact of a browser-based vulnerability and machine compromise, but it is still just one aspect of Least Privilege that administrators can use.
Mark Squire 2005-10-04
Security companies and researchers have made careers out of identifying the latest bugs in Internet Explorer. While Microsoft has been relatively idle, the developers of Firefox have continued to add functionality and provide what was perceived to be more secure code. The story doesn't end there, though. The past six months have seen major vulnerabilities in Firefox too, and its adoption has slowed. Some people are beginning to question the wisdom in switching to another browser that is possibly just as insecure as IE.
Meanwhile a simple yet little-known approach exists for users to avoid many of these vulnerabilities in any web browser. It is a novel tool called "Drop My Rights," created by Microsoft's Michael Howard. While it was released last year and is very simple to use, it has not gained popularity despite all the vulnerabilities found in IE, Firefox, and various email applications. Therefore it's important to understand why such a tool is needed before looking at the tool itself. We'll test it in a virtual machine environment against various websites known to install spyware or viruses and look at the results.
Least privilege
It is important that administrators follow the rule of least privilege. This means that users should operate their computer with only the minimum set of privileges that they need to do their job. Typically this means operating as a normal user, and only when absolutely necessary use the Run As or MakeMeAdmin commands to elevate privileges. Otherwise, a normal user would be forced to log out, and then log back in as an administrative user to perform necessary actions such as install software - or even many browser-based plugins. When faced with this inconvenience, most users when given the choice will continue to operate as an administrator. Herein is the problem.
Corporate policy that disallows administrator access to desktop machines is still the best approach. However, political issues with "power users" or users in very decentralized networks continue to pose a problem. Additionally, administrators themselves who browse the web are still at risk. Reducing privileges of Internet-facing applications is one approach to reducing that risk.
After publishing his tool, Michael Howard repeats that, "Running with an administrative account is dangerous to the health of your computer and your data." Readers of SecurityFocus should all know this, yet many still do it anyway. Rather than trying to lowering user rights across the board, a good approach for power users is to simply lower the rights of Internet-facing applications like Internet Explorer, Firefox, IM applications, Outlook and Outlook Express, Notes, Thunderbird, and so on.
Drop My Rights
Drop My Rights is an executable that accepts a path to your favorite program as a command-line argument. Consider for a moment that an administrator would want to run IE or Firefox in a more safe security context. The administrator would, in the case of IE, run the following command:
c:\path\to\dropmyrights.exe "C:\Program Files\Internet Explorer\iexplore.exe" CThis tells Internet Explorer to run at a reduced privilege level C, or "constrained user." This makes it so that if there is any sort of hole/vulnerability in IE or Firefox, the damage that can be done by an exploit is severely limited. The levels in this simple application are as follows:
N for Normal User
C for constrained user
U for untrusted user - however, most Internet applications will fail
The important question is "does it work?" This can be answered with a few simple experiments. The idea is to test whether a system using this utility will be more protected than a system without this utility when browsing malicious websites.
Testing procedure
Before the actual tests, some prep work needs to be done. This experiment demands a controlled test environment. Virtual machines, as provided from VMWare and Microsoft, are the perfect choice for such an environment. They have the ability to set a snapshot of a particular point in time, allowing one to make changes to the virtual machine, observe the results, then revert it back to the state that it was in before any of those changes were made. For this experiment a virtual machine with Windows XP installed (no service packs or patches), with a snapshot taken just after installation.
During the experiments, one of the free online antivirus scans will be used to test the machine for infection, but first it is necessary to establish that the machine is clean to begin with. To do this an initial scan was completed on the virtual machine before any tests were conducted. The results came back negative for viruses, as expected, and to keep all things equal, the virtual machine was immediately reverted back to its snapshot after the initial scan was complete.
The procedure for the first test was as follows:
Revert the virtual machine to its snapshot (completed above).
Obtain a list of unfriendly websites.
Open each of these sites on the virtual machine using Internet Explorer.
Note any strangeness observed during the experiments.
Run virus scan once these procedures are complete.
Copy the list of URL's from the Internet Explorer's history to Notepad. This will be useful later on.
During the testing a number of unrecognized applications were installed. Changes were made to the GUI of Internet Explorer including the addition of various buttons and search-bars. Phantom windows would appear and disappear at random, and there were numerous popups. The virtual machine itself was running noticeably slower as well. Although an online virus scan was initiated, it didn't complete successfully. In fact the scan died with an error before it actually completed. It found 7 infections, however, before it finally died.
The procedure for the second test was as follows:
Revert the virtual machine to its snapshot (completed above).
Use the list of URLs obtained from the history in the last test.
Install "Drop My Rights" and install according to instructions (for this test it is run with the "N" parameter which runs IE under normal privileges mode - still significantly lower than administrator privileges).
Open these same set of sites on the virtual machine using Internet Explorer.
Note any strangeness observed during the experiments.
Run virus scan once these procedures are complete.
The only observation of note during the experiment is that pop-ups still occurred. There were no phantom windows or unexplained applications installed. However the virus scan still turned up 4 viruses. Since the author recommends the "C" parameter while surfing more questionable sites, the next portion of the experiment did exactly that.
The procedure for the final test was as follows:
Revert the virtual machine to its snapshot (completed above).
Use the list of URLs obtained from the history in the last test.
Install "Drop My Rights" and install according to instructions (for this test it is run with the "C" parameter which runs IE under constricted privileges mode – which incidentally what the author of the utility suggests using when opening "questionable" sites).
Open each of these sites on the virtual machine using Internet Explorer.
Note any strangeness observed during the experiments.
Run virus scan once these procedures are complete.
During this final experiment the only oddity observed was that the Internet Explorer window would maximize if it wasn't already. There were no pop-ups, pop-unders, or any of the other effects previously observed, and this time the virus scan turned up zero viruses. Drop My Rights works just as the author described according in the tests conducted.
Simplifying for users
It's very easy to adjust an application shortcut so that the application runs with reduced rights. This is ideal for power users or others who insist on running as an administrator. When viewing the shortcut properties, simply change the target of the application to call DropMyRights.exe first, such as, C:\windows\dropmyrights.exe "C:\Program Files\Mozilla Firefox\firefox.exe" N, as shown below in Figure 1.

Figure 1. Setting up a shortcut to use DropMyRights.exe.
Note that other applications will inherit these reduced privileges when spawned. For example, Windows Media Player, Adobe Acrobat, WinZip, and others will run with reduced privileges when launched from the browser. This is ideal, however it does not provide complete protection as we will see.
A tool such as SysInternals' free Process Explorer can be used to verify the privileges of the process as well as any processes it spawns.
There is also an IE toolbar written by Aaron Margosis called PrivBar that makes it very easy to see what privileges IE is running under (Administrator, Power User, User, or Restricted). This can be useful when testing DropMyRights.exe.
Drawbacks
As mentioned earlier, restricted privilege sometimes impacts functionality. Internet Explorer won't work at all when running it as an argument to dropmyrights.exe with the "U" parameter (the most restrictive setting). Additionally when running in "constricted" mode, some sites don't work. For instance www.espn.com shows up incomplete in my testing. Typing www.espn.com will result in IE opening it, but it will throw up an error window first.
Using the "normal" mode still has a lot of restricted privileges, but many of the annoyances of the "constricted" mode aren't there. SSL also doesn't work in "constricted" mode but works fine in "normal" mode, a fact the author of the code is well aware of. In fact there is a large list of software that simply doesn't work with restricted privileges. While this utility works perfectly for IE, it is best used with any Internet facing program. This includes instant messengers, email programs, media players for example. Try it with the most restrictive privileges, and check for functionality. Make separate shortcuts available if you absolutely need raise your privileges to gain a certain functionality.
Any time you drop privileges in an operating system, you sacrifice functionality. Take for instance the program "Macromedia Shockwave." Shockwave needs administrative privileges to install. In this author's experience it also needs administrative privileges to run as in certain isolated circumstances. The point is that the principle of least privilege isn't always practical. If you have a user, who has a legitimate need to have administrative privileges, this utility can therefore be helpful.
Complete protection?
While all of this sounds good, it can offer a false sense of security. Applications spawned from a browser with reduced privileges will inherit those reduced privileges, but privilege escalation is still always a possibility. Additionally, exploits that make use of spoofing obviously would not be stopped by this utility. Phishing is probably the most notable example as it uses a combination of spoofing and social engineering to accomplish its goal. This tool was not designed to handle those problems anyway, but historically, the most troublesome bugs in IE have had to do with buffer-overflows. This utility would be able to severely limit the potential damage done as a result of these bugs.
Summary
It would be better for the Internet as a whole if users did not use their Windows web browsers with administrator privileges. Malicious viruses, spyware and Trojans are frequently installed through vulnerabilities in Internet-facing applications - either by visiting websites or by social engineering such as users clicking on malicious attachments in their email. However, due to the inconvenient and clumsy way of installing applications that require administrator privileges, many users continue to run as administrator. The easy use of DropMyAdmin can reduce the impact of a browser-based vulnerability and machine compromise, but it is still just one aspect of Least Privilege that administrators can use.