VulnHub渗透测试实战靶场 - Billu_b0x
VulnHub渗透测试实战靶场 - Billu_b0x
- 环境下载
- Billu_b0x靶机搭建
- 渗透测试
-
- 信息搜集
- 漏洞挖掘
- getshell
-
- 获得root权限
- 获得非root权限
- 提权
环境下载
戳此进行环境下载
Billu_b0x靶机搭建
将下载好的靶机环境,用VMware导入,将靶机和攻击机的网络连接设置为
NAT模式
渗透测试
信息搜集
用Kali中的arp扫描探测一下:
sudo arp-scan -l
使用Nmap扫描VMware Network Adapter VMnet8网卡的NAT网段C段IP:
sudo nmap -sP 192.168.23.1/24
确定目标ip地址:
192.168.23.130
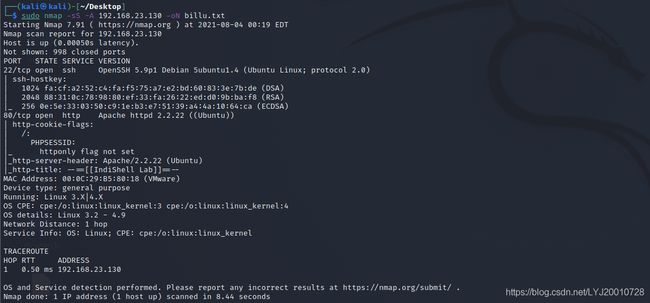
用Nmap进行深度扫描:sudo nmap -sS -A 192.168.23.130 -oN billu.txt
发现目标开放了22端口和80端口
漏洞挖掘
访问80端口进入web首页,发现用户名口令输入框,并提示"Show me your SQLI skills"
漏洞挖掘思路:
- SQL注入:首页提示注入,想办法注入成功
- 暴破目录:用DirBuster暴破,看是否有新网页,找新漏洞
- 漏洞扫描:暴破的新网页,送进AWVS或APPScan扫漏洞
- 手动挖掘:暴破的新页面,通过Firefox挂burp代理,在burp中观察Request和Response包,手动找漏洞
- 查看每个网页的源码,看是否有提示
- 如得到用户名,密码,尝试登录ssh,如能连接上,无需反弹shell了
先用sqlmap进行测试:
sqlmap -u http://192.168.23.130/ --data "un=admin&ps=admin&login=let%27s+login" --level 3 --dbms mysql,发现并没有什么效果
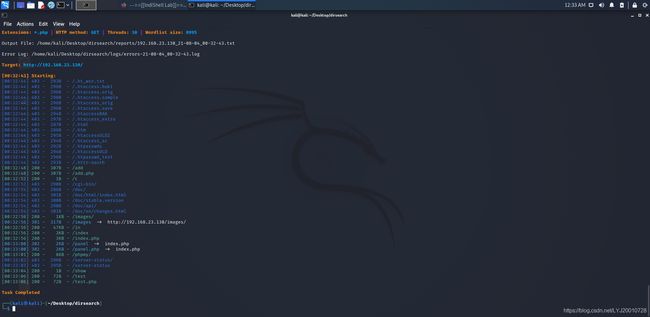
使用dirsearch扫描一下网站目录:
python3 dirsearch.py -u 192.168.23.130 -e *.php,发现存在挺多200的页面
测试后发现在
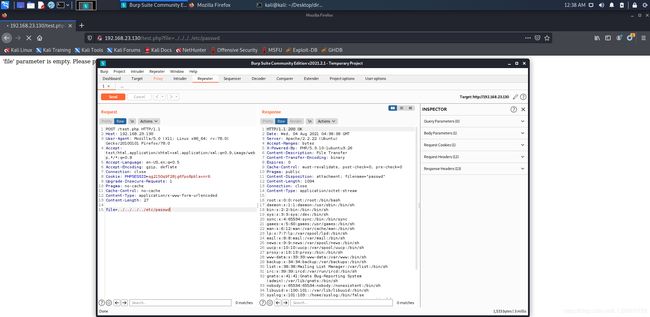
http://192.168.23.130/test.php存在文件包含
利用该漏洞,查看一下之前探测网站目录得到的php文件内容
- c.php
#header( 'Z-Powered-By:its chutiyapa xD' );
header('X-Frame-Options: SAMEORIGIN');
header( 'Server:testing only' );
header( 'X-Powered-By:testing only' );
ini_set( 'session.cookie_httponly', 1 );
$conn = mysqli_connect("127.0.0.1","billu","b0x_billu","ica_lab");
// Check connection
if (mysqli_connect_errno())
{
echo "connection failed -> " . mysqli_connect_error();
}
?>
- add.php
echo '';
?>
- index.php
session_start();
include('c.php');
include('head.php');
if(@$_SESSION['logged']!=true)
{
$_SESSION['logged']='';
}
if($_SESSION['logged']==true && $_SESSION['admin']!='')
{
echo "you are logged in :)";
header('Location: panel.php', true, 302);
}
else
{
echo '
--==[[ billu b0x ]]==--
Show me your SQLI skills