【Kubernetes】基于ingress-nginx-controller实现服务发现和负载均衡
整个过程探索了很久,原理没太搞明白,反正能通过自定义的ingress规则访问到后端(node上运行的pod里面的)Nginx服务了。
另外,本试验的可重复性未做验证,请勿在生产环境执行下面的过程复现。
环境说明:
- k8s二进制集群(1.21.4):3master+3node
- Harbor:2.3.1
- Ingress-nginx:0.48.1
过程步骤展示:
提前将ingress-nginx-v0.48.1.yaml里面引用的两个镜像文件上传到Harbor仓库,然后创建对应的secret,以实现K8s连接到harbor仓库的认证。
修改ingress-nginx.yaml的配置,两处:
第一处:修改镜像的地址为本地Harbor仓库的地址
image: 192.168.223.100/ingress-nginx/controller:v0.48.1
image: 192.168.223.100/ingress-nginx/kube-webhook-certgen:v1.5.1
image: 192.168.223.100/ingress-nginx/kube-webhook-certgen:v1.5.1第二处:增加一处配置
spec:
hostNetwork: true # 增加改配置
dnsPolicy: ClusterFirst
containers:
- name: controller
image: 192.168.223.100/ingress-nginx/controller:v0.48.1
imagePullPolicy: IfNotPresent
--- 创建3个副本的Nginx Pod,命名空间用的默认的,即default
# kubectl create deployment nginx --image=nginx:1.20.1 --replicas=3
deployment.apps/nginx created
--- 创建对应的service
# kubectl expose deployment/nginx --port=80 --protocol=TCP --target-port=80
service/nginx exposed
--- 查看创建的pods和service
# kubectl get pods,svc -A -o wide
NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
default pod/nginx-9dfb46bc4-cx5gh 1/1 Running 0 3m38s 192.145.0.19 k8s-node02
default pod/nginx-9dfb46bc4-jtnm5 1/1 Running 0 3m38s 192.145.0.87 k8s-node03
default pod/nginx-9dfb46bc4-rsblk 1/1 Running 0 3m38s 192.145.0.212 k8s-node01
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
default service/nginx ClusterIP 10.0.0.41 80/TCP 118s app=nginx 创建Ingress-nginx-controller的服务发现规则
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-service
spec:
rules:
- host: www.cnskylee.com # 自定义的域名
http:
paths:
- pathType: Prefix
path: /
backend:
service:
name: nginx # 上面创建的服务名
port:
number: 80 # 宿主机上暴露的端口,80、443,这里用的80
报错:在执行上面的规则创建的时候,发现一条报错信息
Error from server (InternalError): error when creating "ingress-web-reguler.yaml": Internal error occurred: failed calling webhook "validate.nginx.ingress.kubernetes.io": Post "https://ingress-nginx-controller-admission.ingress-nginx.svc:443/networking/v1beta1/ingresses?timeout=10s": dial tcp 10.0.0.192:443: connect: connection refused
解决:删除ingress-nginx-admission的校验配置
# kubectl delete -A ValidatingWebhookConfiguration ingress-nginx-admission
validatingwebhookconfiguration.admissionregistration.k8s.io "ingress-nginx-admission" deleted再次执行,成功
# kubectl apply -f ingress-web-reguler.yaml
ingress.networking.k8s.io/ingress-service created查询ingress-nginx-controller在哪个node节点,结果显示k8s-node02这个节点上,对应的node-ip为192.168.223.95
# kubectl get pods -n ingress-nginx -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
ingress-nginx-admission-create-qknjg 0/1 Completed 0 27m 192.145.0.22 k8s-node02
ingress-nginx-admission-patch-4d4zp 0/1 Completed 0 27m 192.145.0.214 k8s-node01
ingress-nginx-controller-fd9db6658-g7r87 1/1 Running 0 25m 192.168.223.95 k8s-node02 修改c:\Windows\System32\drivers\etc\hosts,增加域名和IP的映射关系
# The node ip which Ingress-controller pod run in
192.168.223.95 www.cnskylee.com
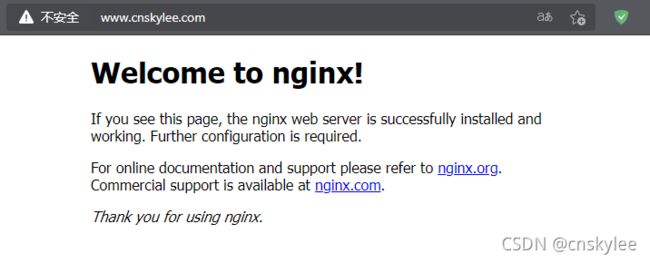
在浏览器中通过域名访问后端pod里面的Nginx服务,结果成功!
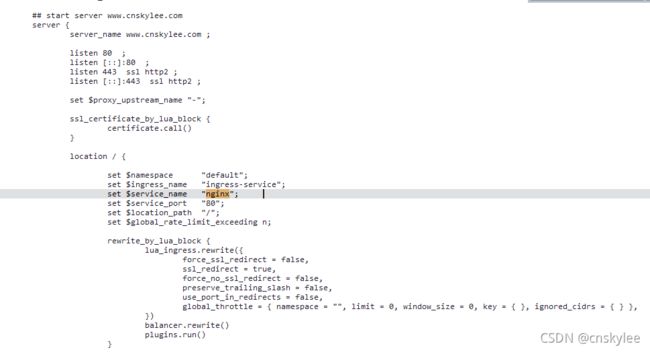
使用kubectl exec -ti 进入到ingress-nginx-controller的pod内部,在/etc/nginx/nginx.conf中可以看到规则里面的访问域名和端口被写入了Nginx的配置里面。