Winja CTF | Nullcon Berlin 2022 wp
文章目录
- Pwn
-
- Francisco Torres
- Steganography
-
- Arturo
- Miscellaneous
-
- Suárez
- Inmate
- crypto
-
- sP!R@L:
- TR@VeLL!ng
- Forensics
-
- Manila
- Benito Antoñanzas
Pwn
Francisco Torres
和pwn没什么关系,就是每次返回一张二维码要在几秒之内提交结果。虽然可以手撸但是太多张了,浪费时间。
from pwn import *
from PIL import Image
from pyzbar import pyzbar
import cv2
p = remote('3.145.216.156',41879)
while 1:
r = p.recvuntil(b'Enter the Flag you got till now >')
pos = r.index(b'\n\xe2\x96\x88')
r = r[pos + 1:-35]
r = r.split(b'\n')
# print(r)
img = Image.new('RGB',(50,50),(255,255,255)) #没去管大小,写了个较大的数50
for i in range(len(r)):
count = 0
for j in range(len(r[i])):
if(r[i][j:j+3] == b'\xe2\x96\x88'):
img.putpixel((count,i*2),(255,255,255))
img.putpixel((count,i*2+1),(255,255,255))
count += 1
elif(r[i][j:j+2] == b'\xc2\xa0'):
img.putpixel((count,i*2),(0,0,0))
img.putpixel((count, i*2+1), (0, 0, 0))
count += 1
elif(r[i][j:j+3] == b'\xe2\x96\x84'):
img.putpixel((count,i*2),(0,0,0))
img.putpixel((count, i*2+1), (255,255,255))
count += 1
elif(r[i][j:j+3] == b'\xe2\x96\x80'):
img.putpixel((count,i*2),(255,255,255))
img.putpixel((count, i*2+1), (0,0,0))
count += 1
img = img.resize((500,500))
img.save('flag.png')
# img.show()
qrcode = cv2.imread('flag.png')
data = pyzbar.decode(qrcode)
text = data[0].data.decode('utf-8')
p.sendline(text.encode())
print(text)
Steganography
Arturo
在用stegsolve查看的时候发现2 1 0通道最上面有额外数据,导出发现是另一张png,稍微修复一下即可得到flag。
Miscellaneous
Suárez
一个py的字节码

发现第二个const为索引,而第一个load_const为值,因此以第二个load_const从小到大将第一个load_const值chr之后进行排序
Inmate
连上ssh后,想要执行命令,发现都回显Illegal character
fuzz一下发现禁止了0-9a-zA-Z
尝试用通配符,发现当前文件夹有个flag.txt
![]()
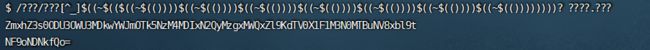
想用通配符输出 /???/???无法匹配到cat 因此想用base64
需要构造数字,去翻了一下ctfshow web入门的命令执行
print("$((~$(("+"$((~$(())))"*5+"))))")
#4
print("$((~$(("+"$((~$(())))"*7+"))))")
#6

发现这样去匹配还会匹配到一个/bin/x86_64,因此不匹配_
/???/???[^_]$((~$(($((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))))))? ????.???
crypto
sP!R@L:
reverse + 6次base64得到一串逐渐增大的数字,处理一下之后相减即为flag
s = '0 102 210 307 410 533 589 687 736 787 838 886 940 993 1043 1143 1241 1289 1389 1446 1497 1552 1653 1707 1806 1906 2005 2057 2157 2209 2265 2314 2362 2411 2460 2516 2617 2717 2812 2877 2913 2949 3016 3089 3162 3257 3354 3464 3564 3659 3695 3812 3889 4014'
s = s.split(' ')
for i in range(len(s)-1):
print(chr(int(s[i+1]) - int(s[i])),end='')
TR@VeLL!ng
题目描述:
The policia is attempting to find professor. They took a train , it went around 10 miles in north and turn to north-east and move 5 miles. They reached the location but could not find the professor. What a waste??
ee:```5qEaf4`00`a4h@{b634E673gh30G=5d_0D625h5):=82_2~0NL2#
Forensics
Manila
PDF,在用010查看每个obj的大小的时候,发现有一个obj开头是DNEI,于是搜了一下GNP也是存在的,说明就是倒过来了一个png,因此写个脚本再倒过来,然后删除其他数据即可得到flag
f = open("Manila.pdf",'rb').read()[::-1]
f1 = open("png.png",'wb')
f1.write(f)
Benito Antoñanzas
首先pslist,发现开了mspaint、cmd、ie
这里看iehistory可以发现访问过本地的一个flag.txt
BELLA CIAO
KA42 1Y U7I 15W2 XIW HT53 7H5 A9UY STP FPKFGLKK FRPR EQOQ
KEYWORD = NULLCON
KEY = WINJA
TOTAL = 16
SHIFT = 5
CHARSET = ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890_
在dcode上搜了之后发现是Bellaso Cipher

结合hint和mspaint,很明显是需要memdump然后配合gimp看快照图像
具体操作可以看volatility安装、内存取证常见知识点及例题讲解(已进行两次更新)
flag{7313db9b42db2ccbed3ae00efb46cdf8_It5_doLpHIN_t1m3}