SSL Certificate Signed Using Weak Hashing Algorithm(CVE-2004-2761)
SSL Certificate Signed Using Weak Hashing Algorithm
操作系统版本:Windows Server 2012 R2
前言:解决SSL Certificate Signed Using Weak Hashing Algorithm过程中生成证书时采用自签名故仍然会保留SSL Certificate Cannot Be Trusted、SSL Self-Signed Certificate问题,解决SSL Certificate Cannot Be Trusted、SSL Self-Signed Certificate可申请官方机构颁布证书
SSL Certificate Signed Using Weak Hashing Algorithm
SSL Certificate Signed Using Weak Hashing Algorithm
Description
The remote service uses an SSL certificate chain that has been signed using a cryptographically weak hashing algorithm (e.g. MD2, MD4, MD5, or SHA1). These signature algorithms are known to be vulnerable to collision attacks. An attacker can exploit this to generate another certificate with the same digital signature, allowing an attacker to masquerade as the affected service.
Note that this plugin reports all SSL certificate chains signed with SHA-1 that expire after January 1, 2017 as vulnerable. This is in accordance with Google’s gradual sunsetting of the SHA-1 cryptographic hash algorithm.
Note that certificates in the chain that are contained in the Nessus CA database (known_CA.inc) have been ignored.
Solution
Contact the Certificate Authority to have the SSL certificate reissued.
See Also
https://tools.ietf.org/html/rfc3279
http://www.nessus.org/u?9bb87bf2
http://www.nessus.org/u?e120eea1
http://www.nessus.org/u?5d894816
http://www.nessus.org/u?51db68aa
http://www.nessus.org/u?9dc7bfba
Output
The following certificates were part of the certificate chain sent by
the remote host, but contain hashes that are considered to be weak.
Subject : CN=SSL_Self_Signed_Fallback
Signature Algorithm : SHA-1 With RSA Encryption
Valid From : Dec 17 19:04:21 2020 GMT
Valid To : Dec 17 19:04:21 2050 GMT
Raw PEM certificate :
-----BEGIN CERTIFICATE-----
MIIB + zCCAWSgAwIBAgIQetsANEKCqoZC74W4Z0idJjANBgkqhkiG9w0BAQUFADA7MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEAbABsAGIAYQBjAGswIBcNMjAxMjE3MTkwNDIxWhgPMjA1MDEyMTcxOTA0MjFaMDsxOTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBsAGwAYgBhAGMAazCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAyYE0CntRczYPDMlxdYUiCLICPQDtzC3qgf3EvS4Gy8YISvhtxZ0GFYBfxwulmPRitOzbs6BU8 / BGKCP7dJ4nwbVx6WFDKEdaHJ3j / WrFKL8KJK0nrOP2hyIwbLqke237QT6d4Hu3C4zVmO4rTAcGdvWs1PTWk7zcnnufUs6COL0CAwEAATANBgkqhkiG9w0BAQUFAAOBgQAHcHkn6n7hDfsqJcmVylQxNcBKqTbW6tYS + IbQi0Hlpd9hcqyKJ / 3NI1hAZi2 + bhlv + Eg2Wx7X11Rg4kwGCaAqGJx4rABKYx7K + H3Xyq8OUzGMcfedY7h + K / QQlbR + 1Z1tPjsmgWpPX6lhcXB0ba18qfMfyRxhEbq8gm7PEXmeHQ ==
-----END CERTIFICATE-----
Risk Information
Risk Factor: Medium
CVSS v3.0 Base Score 7.5
CVSS v3.0 Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N
CVSS v3.0 Temporal Vector: CVSS:3.0/E:P/RL:O/RC:C
CVSS v3.0 Temporal Score: 6.7
CVSS v2.0 Base Score: 5.0
CVSS v2.0 Temporal Score: 3.9
CVSS v2.0 Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
CVSS v2.0 Temporal Vector: CVSS2#E:POC/RL:OF/RC:C
Vulnerability Information
CPE: cpe:/a:ietf:md5 cpe:/a:ietf:x.509_certificate
Exploit Available: true
Exploit Ease: Exploits are available
Vulnerability Pub Date: August 18, 2004
Reference Information
CWE: 310
CERT: 836068
BID: 11849, 33065
CVE: CVE-2004-2761
解释说明
SSL Certificate Signed Using Weak Hashing Algorithm是因SSL证书中使用的签名算法不符合IETF要求,需要重新生成SSL证书且SSL证书中的签名算法、密钥长度均要注意符合当前的IETF要求,同时根据其受影响软件情况更换受影响软件的SSL证书。
SSL Certificate Signed Using Weak Hashing Algorithm in RDP
SSL Certificate Signed Using Weak Hashing Algorithm
Description
The remote service uses an SSL certificate chain that has been signed using a cryptographically weak hashing algorithm (e.g. MD2, MD4, MD5, or SHA1). These signature algorithms are known to be vulnerable to collision attacks. An attacker can exploit this to generate another certificate with the same digital signature, allowing an attacker to masquerade as the affected service.
Note that this plugin reports all SSL certificate chains signed with SHA-1 that expire after January 1, 2017 as vulnerable. This is in accordance with Google’s gradual sunsetting of the SHA-1 cryptographic hash algorithm.
Note that certificates in the chain that are contained in the Nessus CA database (known_CA.inc) have been ignored.
Solution
Contact the Certificate Authority to have the SSL certificate reissued.
See Also
https://tools.ietf.org/html/rfc3279
http://www.nessus.org/u?9bb87bf2
http://www.nessus.org/u?e120eea1
http://www.nessus.org/u?5d894816
http://www.nessus.org/u?51db68aa
http://www.nessus.org/u?9dc7bfba
Output
The following certificates were part of the certificate chain sent by
the remote host, but contain hashes that are considered to be weak.
Subject : CN=SSL_Self_Signed_Fallback
Signature Algorithm : SHA-1 With RSA Encryption
Valid From : Dec 17 19:04:21 2020 GMT
Valid To : Dec 17 19:04:21 2050 GMT
Raw PEM certificate :
-----BEGIN CERTIFICATE-----
MIIB + zCCAWSgAwIBAgIQetsANEKCqoZC74W4Z0idJjANBgkqhkiG9w0BAQUFADA7MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEAbABsAGIAYQBjAGswIBcNMjAxMjE3MTkwNDIxWhgPMjA1MDEyMTcxOTA0MjFaMDsxOTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBsAGwAYgBhAGMAazCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAyYE0CntRczYPDMlxdYUiCLICPQDtzC3qgf3EvS4Gy8YISvhtxZ0GFYBfxwulmPRitOzbs6BU8 / BGKCP7dJ4nwbVx6WFDKEdaHJ3j / WrFKL8KJK0nrOP2hyIwbLqke237QT6d4Hu3C4zVmO4rTAcGdvWs1PTWk7zcnnufUs6COL0CAwEAATANBgkqhkiG9w0BAQUFAAOBgQAHcHkn6n7hDfsqJcmVylQxNcBKqTbW6tYS + IbQi0Hlpd9hcqyKJ / 3NI1hAZi2 + bhlv + Eg2Wx7X11Rg4kwGCaAqGJx4rABKYx7K + H3Xyq8OUzGMcfedY7h + K / QQlbR + 1Z1tPjsmgWpPX6lhcXB0ba18qfMfyRxhEbq8gm7PEXmeHQ ==
-----END CERTIFICATE-----
Risk Information
Risk Factor: Medium
CVSS v3.0 Base Score 7.5
CVSS v3.0 Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N
CVSS v3.0 Temporal Vector: CVSS:3.0/E:P/RL:O/RC:C
CVSS v3.0 Temporal Score: 6.7
CVSS v2.0 Base Score: 5.0
CVSS v2.0 Temporal Score: 3.9
CVSS v2.0 Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
CVSS v2.0 Temporal Vector: CVSS2#E:POC/RL:OF/RC:C
Vulnerability Information
CPE: cpe:/a:ietf:md5 cpe:/a:ietf:x.509_certificate
Exploit Available: true
Exploit Ease: Exploits are available
Vulnerability Pub Date: August 18, 2004
Reference Information
CWE: 310
CERT: 836068
BID: 11849, 33065
CVE: CVE-2004-2761
Software
RDP
操作步骤
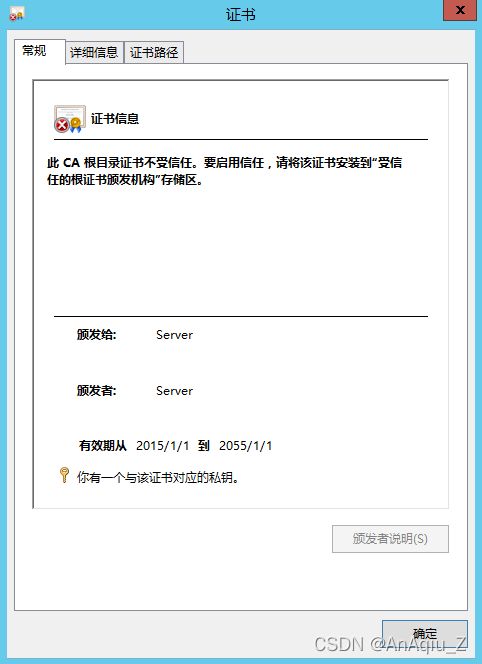
验证存在SSL Certificate Signed Using Weak Hashing Algorithm
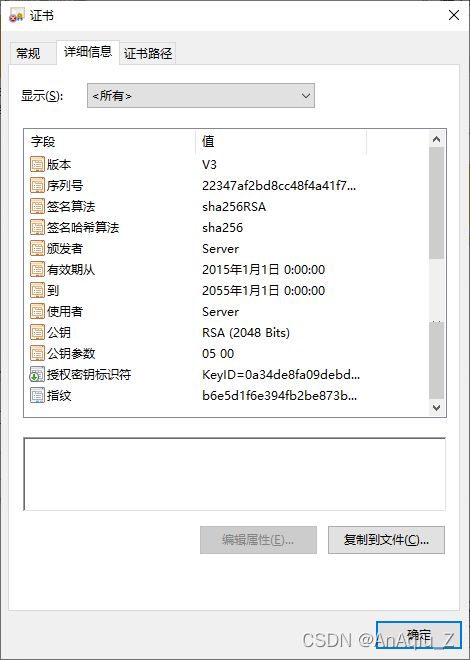
开启远程桌面查看远程桌面证书,看到证书的签名算法是SHA1RSA,公钥长度为RSA(2048 Bits)



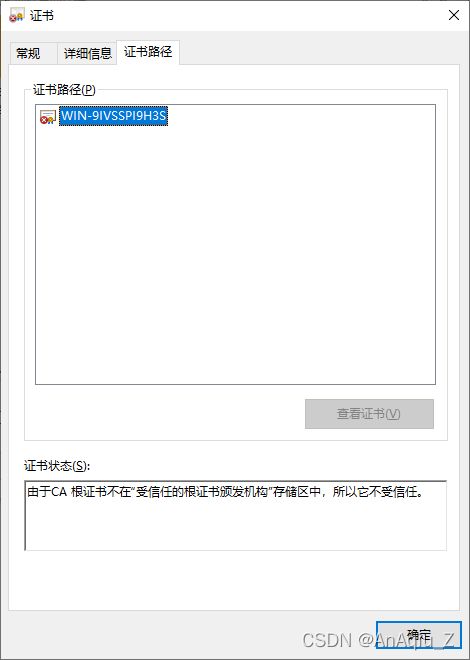
通过测试RDP访问过程验证RDP SSL证书签名算法为SHA1RSA、签名哈希算法为SHA1
搜索或下载证书工具
搜索自有makecert.exe和pvk2pfx.exe或下载我的分享资源
生成证书
将makecert.exe和pvk2pfx.exe拷贝到C:/Windows/System32目录下并在当前目录下启动Windows PowerShell
cd C:\Windows\System32
启动makecert生成证书,指定证书的签名算法SHA256RSA,公钥长度为RSA(2048 Bits)
makecert -r -pe -n "CN=Server" -b 01/01/2015 -e 01/01/2055 -sky exchange -sv ServerPublicKey.pvk ServerPublicKey.cer -a sha256 -len 2048
输入Private Key Password,为满足复杂度要求设置为8位以上数字、字母、特殊字符组合

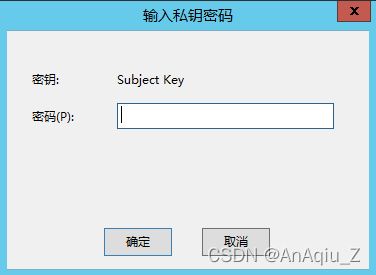
提示信息,成功时提示Succeeded
PS C:\Windows\System32> makecert -r -pe -n "CN=Server" -b 01/01/2015 -e 01/01/2055 -sky exchange -sv ServerPublicKey.pvk ServerPublicKey.cer -a sha256 -len 2048
Succeeded
启动pvk2pfx根据pvk证书导出pfx格式证书,-pi参数后接设置的Private Key Password
pvk2pfx -pvk ServerPublicKey.pvk -spc ServerPublicKey.cer -pfx ServerPrivateKey.pfx -pi password
提示信息,成功时无提示信息
PS C:\Windows\System32> pvk2pfx -pvk ServerPublicKey.pvk -spc ServerPublicKey.cer -pfx ServerPrivateKey.pfx -pi password
导入证书
打开管理控制台
mmc
文件–>添加/删除管理单元–>可用的管理单元–>证书–>添加–>计算机账户–>下一步–>本地计算机–>完成–>确定

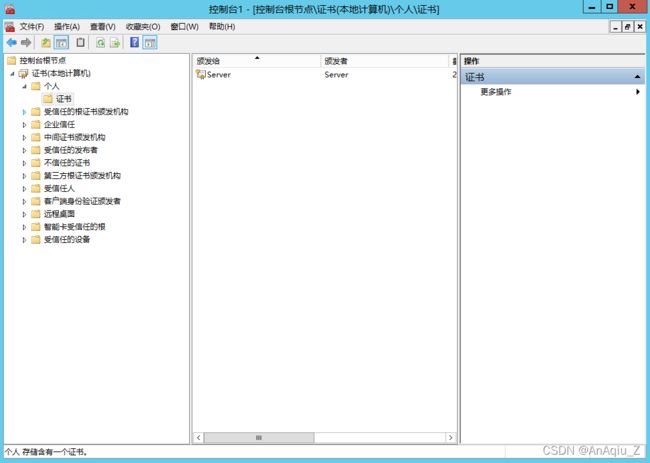
 证书(本地计算机)(中间位置双击)–>个人(右键)–>所有任务–>导入–>本地机计算–>下一步–>浏览–>选择C:\Windows\SysWOW64\ServerPrivateKey.pfx–>下一步–>输入Private Key Password–>确定–>下一步–>完成–>导入成功–>证书(双击)–>出现带私钥的Server证书
证书(本地计算机)(中间位置双击)–>个人(右键)–>所有任务–>导入–>本地机计算–>下一步–>浏览–>选择C:\Windows\SysWOW64\ServerPrivateKey.pfx–>下一步–>输入Private Key Password–>确定–>下一步–>完成–>导入成功–>证书(双击)–>出现带私钥的Server证书
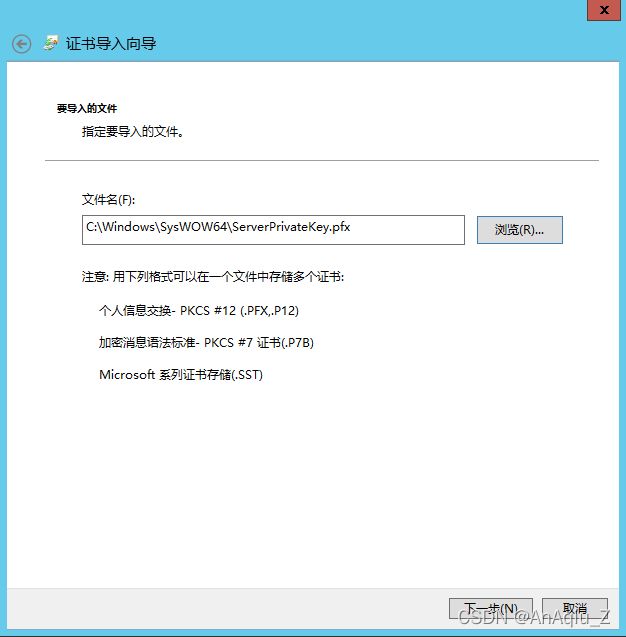



添加证书访问权限
Server证书(右键)–>所有任务–>管理私钥–>添加–>输入对象名称来选择–>NETWORK SERVICE–>检查名称–>确定–>分配NETWORK SERVICE读取权限–>确定
在RDP-tcp中加载证书
通过Windows+R打开运行或在Windows Terminal、Windows PowerShell中打开注册表
regedit
添加注册表项
路径:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
名称: SSLCertificateSHA1Hash
类型: REG_BINARY
值:证书指纹值
验证证书生效情况
遗留问题
因生成证书时采用自签名故仍然会保留SSL Certificate Cannot Be Trusted、SSL Self-Signed Certificate问题,若要解决该问题可在CA中心官方证书网站申请证书,也可搜索免费的证书申请地址,或者由集团单位内部自建统一CA中心颁发证书同时在所有设备导入根证书,目前国密算法正在推行,若自建统一CA中心建议采用国密体系。
SSL Certificate Signed Using Weak Hashing Algorithm in RDP
SSL Certificate Signed Using Weak Hashing Algorithm
Description
The remote service uses an SSL certificate chain that has been signed using a cryptographically weak hashing algorithm (e.g. MD2, MD4, MD5, or SHA1). These signature algorithms are known to be vulnerable to collision attacks. An attacker can exploit this to generate another certificate with the same digital signature, allowing an attacker to masquerade as the affected service.
Note that this plugin reports all SSL certificate chains signed with SHA-1 that expire after January 1, 2017 as vulnerable. This is in accordance with Google’s gradual sunsetting of the SHA-1 cryptographic hash algorithm.
Note that certificates in the chain that are contained in the Nessus CA database (known_CA.inc) have been ignored.
Solution
Contact the Certificate Authority to have the SSL certificate reissued.
See Also
https://tools.ietf.org/html/rfc3279
http://www.nessus.org/u?9bb87bf2
http://www.nessus.org/u?e120eea1
http://www.nessus.org/u?5d894816
http://www.nessus.org/u?51db68aa
http://www.nessus.org/u?9dc7bfba
Output
The following certificates were part of the certificate chain sent by
the remote host, but contain hashes that are considered to be weak.
Subject : CN=SSL_Self_Signed_Fallback
Signature Algorithm : SHA-1 With RSA Encryption
Valid From : Dec 17 19:04:21 2020 GMT
Valid To : Dec 17 19:04:21 2050 GMT
Raw PEM certificate :
-----BEGIN CERTIFICATE-----
MIIB + zCCAWSgAwIBAgIQetsANEKCqoZC74W4Z0idJjANBgkqhkiG9w0BAQUFADA7MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEAbABsAGIAYQBjAGswIBcNMjAxMjE3MTkwNDIxWhgPMjA1MDEyMTcxOTA0MjFaMDsxOTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBsAGwAYgBhAGMAazCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAyYE0CntRczYPDMlxdYUiCLICPQDtzC3qgf3EvS4Gy8YISvhtxZ0GFYBfxwulmPRitOzbs6BU8 / BGKCP7dJ4nwbVx6WFDKEdaHJ3j / WrFKL8KJK0nrOP2hyIwbLqke237QT6d4Hu3C4zVmO4rTAcGdvWs1PTWk7zcnnufUs6COL0CAwEAATANBgkqhkiG9w0BAQUFAAOBgQAHcHkn6n7hDfsqJcmVylQxNcBKqTbW6tYS + IbQi0Hlpd9hcqyKJ / 3NI1hAZi2 + bhlv + Eg2Wx7X11Rg4kwGCaAqGJx4rABKYx7K + H3Xyq8OUzGMcfedY7h + K / QQlbR + 1Z1tPjsmgWpPX6lhcXB0ba18qfMfyRxhEbq8gm7PEXmeHQ ==
-----END CERTIFICATE-----
Risk Information
Risk Factor: Medium
CVSS v3.0 Base Score 7.5
CVSS v3.0 Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N
CVSS v3.0 Temporal Vector: CVSS:3.0/E:P/RL:O/RC:C
CVSS v3.0 Temporal Score: 6.7
CVSS v2.0 Base Score: 5.0
CVSS v2.0 Temporal Score: 3.9
CVSS v2.0 Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
CVSS v2.0 Temporal Vector: CVSS2#E:POC/RL:OF/RC:C
Vulnerability Information
CPE: cpe:/a:ietf:md5 cpe:/a:ietf:x.509_certificate
Exploit Available: true
Exploit Ease: Exploits are available
Vulnerability Pub Date: August 18, 2004
Reference Information
CWE: 310
CERT: 836068
BID: 11849, 33065
CVE: CVE-2004-2761
Software
SQL Server
操作步骤
搜索或下载证书工具
搜索自有makecert.exe和pvk2pfx.exe或下载我的分享资源
生成证书
将makecert.exe和pvk2pfx.exe拷贝到C:/Windows/System32目录下并在当前目录下启动Windows PowerShell
cd C:\Windows\System32
启动makecert生成证书,指定证书的签名算法SHA256RSA,公钥长度为RSA(2048 Bits)
makecert -r -pe -n "CN=Server" -b 01/01/2015 -e 01/01/2055 -sky exchange -sv ServerPublicKey.pvk ServerPublicKey.cer -a sha256 -len 2048
输入Private Key Password,为满足复杂度要求设置为8位以上数字、字母、特殊字符组合


提示信息,成功时提示Succeeded
PS C:\Windows\System32> makecert -r -pe -n "CN=Server" -b 01/01/2015 -e 01/01/2055 -sky exchange -sv ServerPublicKey.pvk ServerPublicKey.cer -a sha256 -len 2048
Succeeded
启动pvk2pfx根据pvk证书导出pfx格式证书,-pi参数后接设置的Private Key Password
pvk2pfx -pvk ServerPublicKey.pvk -spc ServerPublicKey.cer -pfx ServerPrivateKey.pfx -pi password
提示信息,成功时无提示信息
PS C:\Windows\System32> pvk2pfx -pvk ServerPublicKey.pvk -spc ServerPublicKey.cer -pfx ServerPrivateKey.pfx -pi password
导入证书
打开管理控制台
mmc
文件–>添加/删除管理单元–>可用的管理单元–>证书–>添加–>计算机账户–>下一步–>本地计算机–>完成–>确定

 证书(本地计算机)(中间位置双击)–>个人(右键)–>所有任务–>导入–>本地机计算–>下一步–>浏览–>选择C:\Windows\SysWOW64\ServerPrivateKey.pfx–>下一步–>输入Private Key Password–>确定–>下一步–>完成–>导入成功–>证书(双击)–>出现带私钥的Server证书
证书(本地计算机)(中间位置双击)–>个人(右键)–>所有任务–>导入–>本地机计算–>下一步–>浏览–>选择C:\Windows\SysWOW64\ServerPrivateKey.pfx–>下一步–>输入Private Key Password–>确定–>下一步–>完成–>导入成功–>证书(双击)–>出现带私钥的Server证书





添加证书访问权限
Server证书(右键)–>所有任务–>管理私钥–>添加–>输入对象名称来选择–>NETWORK SERVICE–>检查名称–>确定–>分配数据库用户读取权限–>确定

在MSSQLServer中加载证书
通过Windows+R打开运行或在Windows Terminal、Windows PowerShell中打开注册表
regedit
添加注册表项
路径:HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server\MSSQL12.MSSQLSERVER\MSSQLServer\SuperSocketNetLib
名称: Certificate
类型: REG_SZ
值:证书指纹值
参考文档:
https://www.cnblogs.com/huangzelin/p/3645520.html
https://jingyan.baidu.com/article/3aed632e153e9431108091c9.html
https://blog.csdn.net/a549569635/article/details/48831105
https://blog.csdn.net/kufeiyun/article/details/15337097
https://docs.microsoft.com/zh-cn/sql/database-engine/configure-windows/enable-encrypted-connections-to-the-database-engine?redirectedfrom=MSDN&view=sql-server-ver15