每日刷题记录1
Preface
There were some wrong in my previous way of learning.
It’s difficult to consolidate knowledge only by learning knowledge without practice.
So I decide to solve some ctf-subject to consolidate my konwledge.
Why I using English to write this project?
It’s easily to find the reason.
MISC
Title : something_in_image
Source : XCTF
File : click here
The file-name is “badimage”,so drop it into 010editor.
Obvious, so much zero ,and only a little informations are normal.
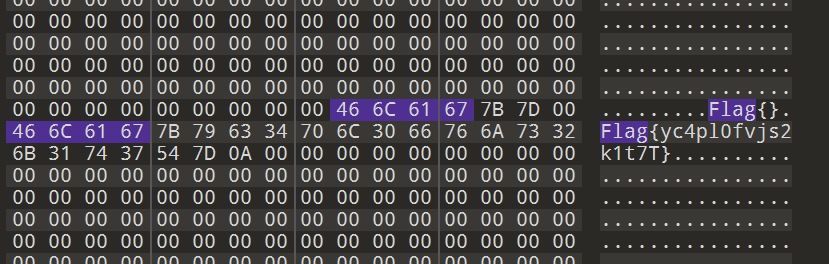
Look up “flag”:
It’s easy ,but i want to know hows it work in the real way;
Look carefully you can find the RAR’s file-header.
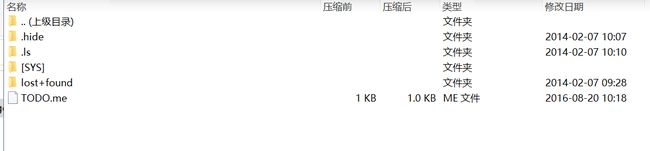
Rename the suffix(后缀名) to RAR ,get these files:
TODO :
Nothing get ,but i solve it .
RE
Title : Hello, CTF
Source : XCTF
File : click me
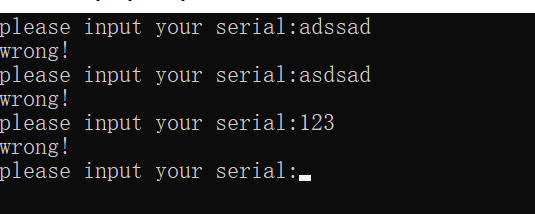
Hint : 菜鸡发现Flag似乎并不一定是明文比较的
Drop in IDA:
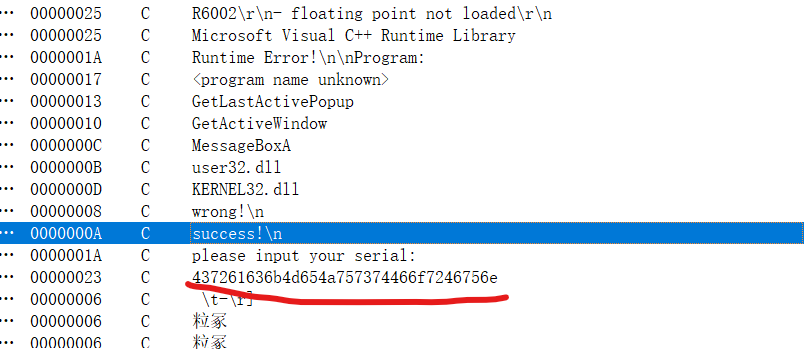
Combined with hint , is compare with the encryoted text .
In addtion, the string is HEX ,decrypt result is “CrackMeJustForFun”
It’s very much like flag.
flag get!!
CRYPTO
Title : flag_in_your_hand
source : XCTF
File : click me
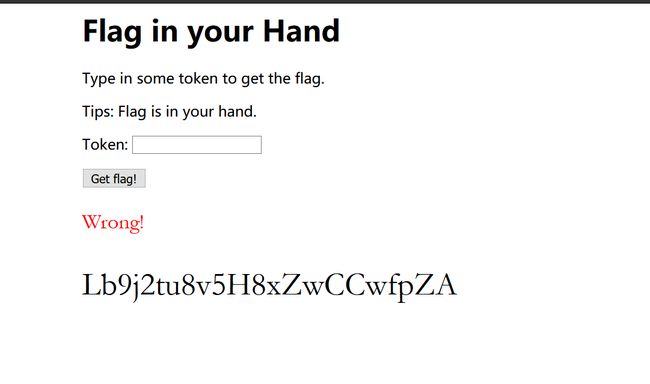
It’s a website :
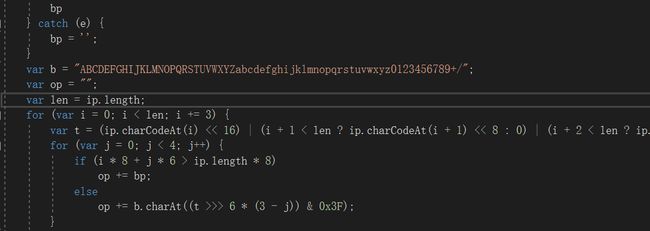
Open the js file with vs ,find this string:
Intuition tells me this is Base64 encrypto , because it’s the same as encrypted tables.
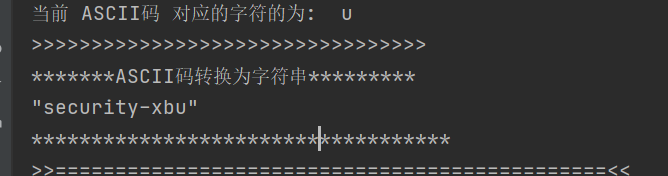
the first part is encrypto by ASCII tables.
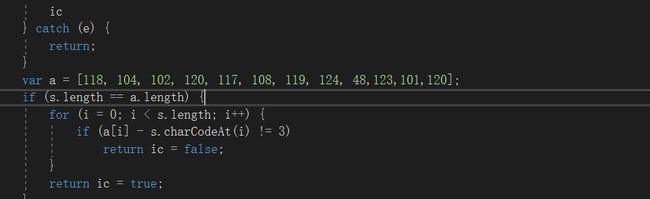
When the number == 3 , the ascii is right ,so the right num is:
[115,101,99,117,114,105,116,121,45,120,98,117]
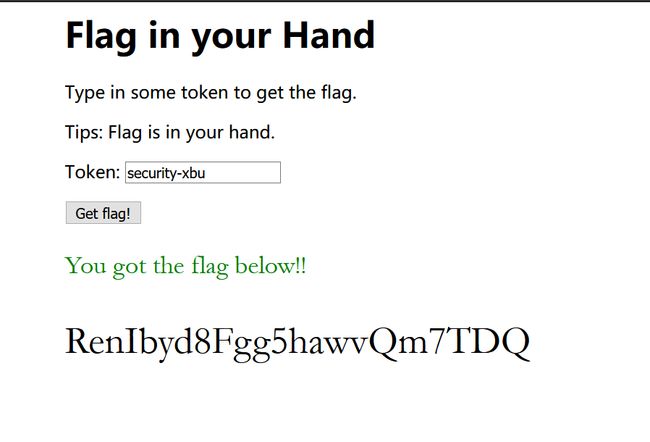
Enter it to the website:
falg get!!!