GP(Global Platform) External authentication and MAC sending APDU
Just implemented a customer requirement of a Windows software development on the GP external authentication and check the card life cycle status, this will need the GP external authentication and the MAC sending APDU.
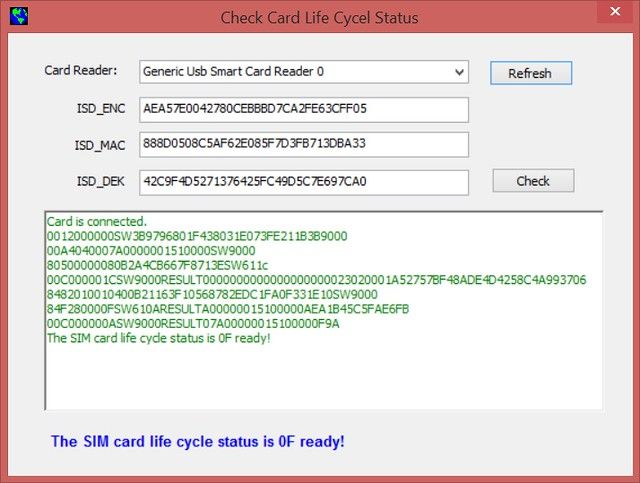
The software screen shot is as following,
The Smart card life cycle status is not as 0F, return error message.
The Smart card life cycle status is 0F ready, showing successful message.
The procedure is first to do the external authentication, then send the life cycle status checking command, the life cycle status command is secured by MAC calculation, as the life cycle status 0F ready required.
Following are the details of how to calculate the external authentication, and calculate the MAC data for the MAC secured APDU. The data is from the screen shot data from the picture previously displayed.
1, external authentication, the following APDUs were happening,
00A4040007A0000001510000SW9000 (Select ISD)
80500000080B2A4CB667F8713ESW611C (Send 8 bytes random data to the Smart Card)
00C000001CSW9000RESULT0000000000000000000023020001A52757BF48ADE4D4258C4A993706 (Smart Card response back challenge and MAC)
8482010010400B21163F10568782EDC1FA0F331E10SW9000 (External authentication APDU sent to Smart Card)
the procedure is quite complicated, the detail analyse as following,
1.1, calculate the session MAC, ENC, DEK key,
the ISD key is as,
ISD_MAC='888D0508C5AF62E085F7D3FB713DBA33';
ISD_ENC='AEA57E0042780CEBBBD7CA2FE63CFF05';
ISD_DEK='42C9F4D5271376425FC49D5C7E697CA0';
The encryption is DES_CBC, the encryption material is as 01820001000000000000000000000000, 0182 is fixed, 0001 is the counter from response data of 00000000000000000000 2302 0001 A52757BF48AD E4D4258C4A993706, and 000000000000000000000000 is the first 10 bytes of response data, the result is as:
Session_ENC=01820001000000000000000000000000 encrypted by AEA57E0042780CEBBBD7CA2FE63CFF05 = DB1B0ECC26F028CED6CEA4242352EA3F
Session_MAC=01010001000000000000000000000000 encrypted by 888D0508C5AF62E085F7D3FB713DBA33 = 8176DCE167EDF989F96403EB86C2943C
Session_DEK=01810001000000000000000000000000 encrypted by 42C9F4D5271376425FC49D5C7E697CA0 = D835DFB5C725B50ADA0AF13448ABCB78
DEK is for encryption, here no use.
1.2 check the Smart card return response MAC correctness(E4D4258C4A993706)
random data(8050 datas): 0B2A4CB667F8713E
Challenge data: A52757BF48AD
random data(8 bytes) + 0001+ Challenge data (6 bytes) = 0B2A4CB667F8713E0001A52757BF48AD
padding 80: 0B2A4CB667F8713E0001A52757BF48AD to 0B2A4CB667F8713E0001A52757BF48AD8000000000000000
0B2A4CB667F8713E0001A52757BF48AD8000000000000000 encrypted by DB1B0ECC26F028CED6CEA4242352EA3F result: 0B9FADA149EFE243085610047322C33AE4D4258C4A993706
last 8 bytes is the matching byte to the last 8 bytes of 00C000001C return.
this is matching 00000000000000000000 2302 0001 A52757BF48AD E4D4258C4A993706 of E4D4258C4A993706
So the Smart card calculated the MAC correctly.
1.3, calculate the external authentication APDU,
The result should be as 8482010010400B21163F10568782EDC1FA0F331E10SW9000
0001+Challenge data(6 bytes) + random data(8 bytes)
0001+A52757BF48AD+0B2A4CB667F8713E encrypted by : DB1B0ECC26F028CED6CEA4242352EA3F
0001A52757BF48AD0B2A4CB667F8713E8000000000000000 encrypted by : DB1B0ECC26F028CED6CEA4242352EA3F result: 7EEAAAC8D76070CFF4A31C6B5DB5D092400B21163F105687
last 8 bytes as the result 400B21163F105687
8482010010400B21163F10568782EDC1FA0F331E10
build the MAC data:
'8482010010400B21163F105687' MAC Key: 8176DCE167EDF989F96403EB86C2943C standar MAC result: 82EDC1FA0F331E10
Get MAC: '82EDC1FA0F331E10'
The final external authentication APDU is as,
8482010010400B21163F10568782EDC1FA0F331E10SW9000
Until now the smart card and terminal finished the mutual authentication.
2, MAC sending check life cycle status APDU buid
2.1 calculate the MAC of APDU 84F280000FA000000151000080000000
calculate the IV
Data as: 82EDC1FA0F331E10(from previous APDU MAC) calculate the MAC by 8176DCE167EDF989F96403EB86C2943C first half as 8176DCE167EDF989 the 8 bytes MAC result as FCAB693D05110CA8 as IV
84F280000FA0000001510000 padding 80 as 84F280000FA000000151000080000000, calculate the MAC by key 8176DCE167EDF989F96403EB86C2943C
the IV is as FCAB693D05110CA8 the result is as: 0AEA1B45C5FAE6FB, this is matching the 84F280000FSW610ARESULTA00000015100000AEA1B45C5FAE6FB
2.2, take it further, if more APDU needs to be sent, so to speak, 84F28000114F07A0000001510000
Data as: 0AEA1B45C5FAE6FB(from previous MAC) calculate the MAC by 8176DCE167EDF989F96403EB86C2943C first half as 8176DCE167EDF989 the 8 bytes MAC result as 35A23577B31DED8C
the IV is as 35A23577B31DED8C the result is as: B5BB6D0CC4F97128, this is matching the 84F28000114F07A0000001510000B5BB6D0CC4F97128
3, Reference:
GP Global Platform Card Specification 2.2